2024-8-29 14:32:5 Author: cyble.com(查看原文) 阅读量:16 收藏
Executive Summary
The geopolitical situation surrounding Ukraine in 2024 showcases a complicated interaction of changing international alliances and the difficulties the Ukrainian government faces in sustaining this support as global priorities shift.
While Ukraine continues to receive significant international support, the landscape in 2024 indicates a potential decline in the international community’s patience and commitment. The combination of reduced U.S. aid, significant gaps in European allocations, and the distraction of global conflicts poses serious challenges for Ukraine.
However, on August 6, 2024, after its longtime defensive posture since the beginning of the conflict in February 2022, Ukraine threw caution to the wind by launching a significant mechanized lean-on, spanning 25 miles on the borders adjoining Russia’s Kursk Oblast region. Within 21 days, the Ukrainian forces claimed to occupy more than 450 miles of territory in the Kursk region.

While this may seem like a surprise attack to most of the world, Cyble analyzed certain incidents that indicate Ukraine’s top military brass had been in a preparatory phase since the beginning of 2023.
Preparatory Events
Chronological Analysis of Cross-border Incursions
Based on information gathered from various Russian and Ukrainian sources, Ukraine’s initial actions included reconnaissance of the border areas using volunteer units and possibly special reconnaissance and sabotage groups.
We observed that Ukrainian volunteer organizations were quite active on Telegram channels to gain stealthy intelligence about Russian force deployments in the border regions of Kursk and Belgorod to plan raids, drone strikes, and, in some cases, even capturing border villages to create footholds in Russian territory.
A chronological analysis of Ukrainian incursions from 2023 is highlighted to understand the weak Russian defenses and strategic failure of Russian military commanders to preempt and contain the ‘Kursk Offensive’.
2023
- February 2023: Ukrainian Grad missiles target the industrial base and public areas in the city of Shebekino. Intermittent shelling and drone attacks continued targeting the city throughout February.
- March 2023: Drone Attack on Transneft-Druzhba oil pipeline, Tuapse oil depot, and Electric Utilities in Belgorod Oblast. Freedom of Russia Legion, the Siberian Battalion, and the Russian Volunteer Corps conducted several raids into the Belgorod and Bryansk regions to disrupt public facilities.
- August 2023: More drone attacks in the village of Lavy and government buildings, including Kursk Railway Station.
- September 2023: Artillery barrages fired by Ukrainian forces on the village of Tyotkino. Drone strikes on government buildings and other villages alongside the border in the Kursk region.
- October 2023: Ukrainian Drones strike electrical facilities in the towns of Sudzha, Lyubimovka, and Glushkovo in the Kursk region, leading to blackouts in several localities.
- December 2023: Ukrainian drones attacked public areas and Electrical utilities in the Dmitrievsky and Zheleznogorsk districts in the Kursk Region.
2024
- February 2024: The Ukrainian paramilitary unit Legion of Freedom of Russia posted on its Telegram channel that it needed assistance locating Russian military establishments and moving troops in the Bryansk, Kursk, and Belgorod border regions.

- March 2024: The Ukrainian far-right para-military group, Russian Volunteer Corps, along with other groups like ‘Freedom of Russia’ and ‘Siberian Battalion’ carried out several raids in Bryansk, Belgorod, and Kursk, capturing the border village of Novaya Tavolzhanka.
- April 2024: Drone attacks in Fatezhsky district of the Kursk region.
- May 2024: Ukrainian drones strike in the villages of Uspenovka and Gordeyevka in the Korenevsky district, Zarya in the Glushkovsky district, and the Sudzha checkpoint.
- June 2024: Drone raids on Village Gorodishche in the Kursk Region.
- In July 2024: Multiple drone attacks disrupted the Electricity & Water supplies in the Kursk and Belgorod regions.
Cyber Sabotage
Ukraine’s cyber sabotage activities played a crucial role in shaping the battlefield dynamics leading up to the Kursk Offensive. As the conflict evolved, Ukrainian cyber units, particularly under the auspices of military intelligence (HUR), executed a series of strategic cyber operations aimed at disrupting Russian military capabilities.
Besides these, Ukrainian activists, by and large, independently operating with their frail-looking operations, were able to support the larger cause. The highlights of the cyber sabotage tactics adopted by Ukrainian cyber teams encompassed:
Disrupting Critical Infrastructure & Military Logistics: Many of these cyber-attacks focused on critical infrastructure, including electrical and water utilities (Rosvodokana), internet infrastructure, industrial plants, and military-industrial complexes.
Intelligence Gathering & Data Destruction: Various threat groups, such as PhantomCore, Twelve, and BlackJack, employed malwares, including data wipers, ransomware, and RATs such as Rhadamanthys Stealer and Ozone RAT to obtain intelligence on Russian military installations and then destruct their data to sabotage Russian operations.
Escalation and Retaliation: The timing of certain attacks, such as BlackJack’s retaliation against Russian ISP M9 Com Ltd following an attack on Ukrainian telco Kyivstar, indicates that these campaigns are not isolated incidents but part of a larger tit-for-tat escalation in the cyber domain.
September 2023: From September 2023 to June 2024, the pro-Ukrainian hacking group Lifting Zmiy launched a series of attacks on the IT infrastructure of the Russian government and private organizations by leveraging Operational Technology (OT). The group was reported to have infiltrated the PLC systems of Tekon-Avtomatika, a company involved in industrial automation, deploying a command and control (C2) server that could manipulate critical infrastructure, including elevators.
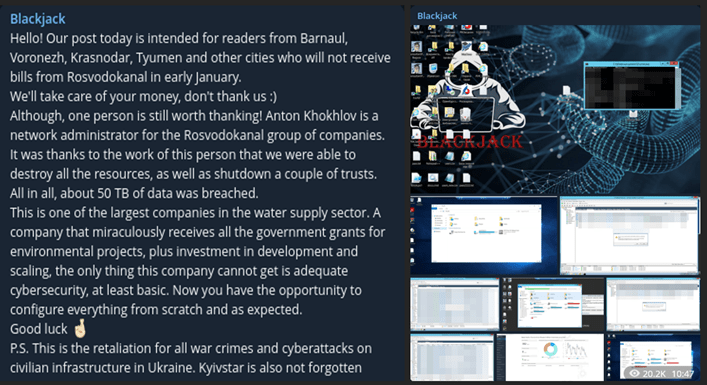
December 2023: Pro-Ukrainian threat group BlackJack, possibly affiliated with the Ukrainian intelligence services, was reported to have employed ransomware and wiper to destroy information within the infrastructure network of Rosvodokanal, a company specializing in water utilities and water management. The attack impacted regions including Barnaul, Voronezh (near Kursk), Krasnodar, Tyumen, and other unspecified cities. BlackJack later claimed responsibility for the attack via their Telegram channel in December, while they may have gained access to the network in August 2023.
January 2024: A newly emerged pro-Ukraine threat group, PhantomCore, with its custom PhantomRAT, launched several supply chain attacks by spreading and expanding the attack print of its malware through earlier compromised Russian entities. The group targeted several critical manufacturing complexes, energy companies, and IT organizations in Russia.
Parallelly, Ukrainian hacktivists BlackJack targeted Russian internet service provider (ISP) M9 Com Ltd in January with several consistent and disrupting Distributed Denial of Service (DDoS) attacks in retaliation to the December 2023 cyberattack on Ukrainian Telecom, Kyivstar. BlackJack also stole 10 GB of data from the company, later leaking it in public and deleting over 20 TB of data from the company.


March 2024: The PhantomCore threat group continuing their activities in March was observed to be using high-quality bait documents to target the Russian military-industrial complex.
Another pro-Ukraine threat group, Core Wolfes, has actively targeted Russian defense-related organizations since its first appearance in August 2021, attacked the Russian Military Research Institute developing weapons in March, followed by an attack on a Russian Military Manufacturing Plant in early April 2024, using UltraVNC remote-access tool in their campaigns.
April 2024: Threat group BlackJack was attributed to a major attack on the Russian Critical Infrastructure Monitoring company Moscollector with Fuxnet malware in June 2023. The group claimed to have compromised 2,659 sensor gateways, with approximately 1,700 successfully attacked, which allegedly severely disrupted emergency detection and response capabilities in Moscow. BlackJack later leaked screenshots and data dumps from the attack, including password information and operational details. Their post revealed access to Russia’s 112 emergency service number, hacking and disabling about 500 critical infrastructure sensors, disabling network appliances, wiping 30 TB of data, invalidating office keycards, and dumping passwords from internal services.

May 2024:
- In May 2024, researchers investigated incidents at two Russian industrial plants where attackers encrypted the infrastructure with Lockbit 3 and damaged ESXi server virtualization. The attacks were part of a series of attacks allegedly carried out by two pro-Ukrainian groups, one tracked as Morbid Trickster and the other remained unidentified.
- Sticky Werewolf has used Rhadamanthys Stealer and Ozone RAT in campaigns targeting the Russian aviation industry, including the AO OKB Kristall, a Moscow-based company involved in aircraft and spacecraft production and maintenance.
- During this period, local sources reported regular disruptions in internet and mobile services in the Kursk Region due to cyber attacks.
June 2024:
- The Twelve hacktivist group, which has been actively targeting Russian entities since April 2023, resurfaced in June to encrypt and destroy Russian companies’ data using several wipers. The Twelve group shares infrastructure and TTPs with the DARKSTAR ransomware group (formerly Shadow and COMET).
- DDoS attacks on the Telecommunication network in the Kursk region continued, disrupting public services such as the extension of healthcare services.
July 2024:
Hacktivist group The IT Army of Ukraine claimed cyber-attacks on several Russian ISPs in border regions, disrupting the services of RegionSet in Kursk; PG19 in Taganrog and Rostov-on-Don, and Yug-Link in Krasnodar. The timing of these disruptions was noted for its strategic impact.

August 2024:
The IT Army of Ukraine continued its cyber offensive against Russian internet service providers (ISP), targeting Iflat and RialCom, which serve the city of Serpukhov. Serpukhov is notable for its machine-building and metalworking industries, the Serpukhov Military Institute of Missile Troops, and the Institute of Engineering Physics.
Just two days after the Kursk Offensive, on August 8, 2024, internet resources in the Kursk region were reported to experience a massive DDoS attack, causing many online services to become temporarily unavailable.
Cyber Retaliation from Russia
On August 12, 2024, Ukraine’s CERT-UA recorded a mass distribution of emails impersonating the Security Service of Ukraine sent by the threat actor UAC-0198. These emails concealed malware capable of gaining unauthorized access to the infected computer. Over 100 affected computers, including those within Ukrainian state bodies and local self-government institutions, were reported to have been identified.
On August 19, CERT-UA reported the distribution of malicious emails titled ‘prisoners of war’, which were originated by threat actor Vermin. These emails contained a link to download an archive named “spysok_kursk.zip”; when unzipped, SPECTR and FIRMACHAAGENT malware were installed on the targeted machine.
Conclusion
The Kursk offensive, launched by Ukraine in early August 2024, marks a pivotal and complex military campaign that integrates active combat and cyber sabotage strategies. It showcases a perfect synthesis of cyber and conventional warfare, utilizing extremely disciplined operation security to maintain the element of surprise.
This successful operation has shifted perceptions of the conflict and revitalized global support for Ukraine. Ukraine’s advance into the Kursk region was motivated by a necessity to regain momentum following several setbacks against Russian forces. Ukraine effectively employed cyber tactics to disrupt Russian logistics and communication systems, which bolstered the efficiency of their ground maneuvers. This involved targeting Russian supply routes and essential infrastructure, complicating the enemy’s response capabilities.
The operation not only resulted in substantial territorial acquisitions but also transformed the strategic dynamics of the war, strengthening Ukraine’s position and boosting troop morale. As developments unfold, the repercussions of the Kursk offensive are expected to impact military strategies and diplomatic discussions in the ongoing conflict.
References
https://www.understandingwar.org/backgrounder/russian-offensive-campaign-assessment-august-27-2024
https://x.com/netblocks/status/1744748014613213215
https://rt-solar.ru/solar-4rays/blog/4506/
https://rt-solar.ru/solar-4rays/blog/4559/
https://claroty.com/team82/research/unpacking-the-blackjack-groups-fuxnet-malware
https://rt-solar.ru/solar-4rays/blog/4615/
https://blog.morphisec.com/sticky-werewolfs-aviation-attacks
https://securelist.ru/twelve-group-unified-kill-chain/110128/
Related
如有侵权请联系:admin#unsafe.sh