2024-8-31 01:36:37 Author: securityboulevard.com(查看原文) 阅读量:8 收藏
Author:
Kaustubh Jagtap, Product Marketing Director, SafeBreach
On August 29, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Defense Cyber Crime Center (DC3) issued an urgent advisory warning security teams about known RansomHub ransomware IOCs and TTPs identified through FBI threat response activities and third-party reporting as recently as August 2024. Detailed information about this threat and the associated IOCs and TTPs can be seen in the advisory #StopRansomware: RansomHub Ransomware.
This blog will share an overview of the threat and our coverage for these threat actors. As a SafeBreach customer, you will have access to all the attacks listed below and more to validate your organizational security controls against this threat.
US CERT Alert AA24-242A (RansomHub Ransomware)
According to the advisory, RansomHub is a ransomware-as-a-service variant—formerly known as Cyclops and Knight—that has established itself as an efficient and successful service model (recently attracting high-profile affiliates from other prominent variants such as LockBit and ALPHV).
Since its inception in February 2024, RansomHub has encrypted and exfiltrated data from at least 210 victims representing the water and wastewater, information technology, government services and facilities, healthcare and public health, emergency services, food and agriculture, financial services, commercial facilities, critical manufacturing, transportation, and communications critical infrastructure sectors.
The affiliates leverage a double-extortion model by encrypting systems and exfiltrating data to extort victims. It should be noted that data exfiltration methods are dependent on the affiliate conducting the network compromise. The ransom note dropped during encryption does not generally include an initial ransom demand or payment instructions. Instead, the note provides victims with a client ID and instructs them to contact the ransomware group via a unique .onion URL (reachable through the Tor browser). The ransom note typically gives victims between three and 90 days to pay the ransom (depending on the affiliate) before the ransomware group publishes their data on the RansomHub Tor data leak site.
Technical Details
- Initial Access – According to the information available, RansomHub affiliates typically compromise internet-facing systems and user endpoints by using methods such as phishing emails, exploitation of known vulnerabilities, and password spraying. These include exploiting several CVEs, including CVE-2023-3519, CVE-2023-27997, CVE-2023-46604, CVE-2023-22515, CVE-2023-46747, CVE-2023-48788, CVE-2020-1472, and CVE-2020-0787.
- Discovery – RansomHub affiliates conduct network scanning with tools such as AngryIPScanner, Nmap, and PowerShell-based living off the land methods with PowerShell to conduct network scanning.
- Defense Evasion – Cybersecurity researchers have observed affiliates renaming the ransomware executable with innocuous file names, such as Windows.exe, left on the user’s desktop (C:\Users\%USERNAME%\Desktop) or downloads (C:\Users\%USERNAME%\Downloads). The affiliates have also cleared Windows and Linux system logs to inhibit any potential incident response. Affiliates used Windows Management Instrumentation to disable antivirus products. In some instances, RansomHub-specific tools were deployed to disable endpoint detection and response (EDR) tooling.
- Privilege Escalation and Lateral Movement – Following initial access, RansomHub affiliates created user accounts for persistence, reenabled disabled accounts, and used Mimikatz on Windows systems to gather credentials and escalate privileges to SYSTEM. Affiliates then moved laterally inside the network through methods including Remote Desktop Protocol (RDP), PsExec, Anydesk, Connectwise, N-Able, Cobalt Strike, Metasploit, or other widely used command-and-control (C2) methods.
- Data Exfiltration – Data exfiltration methods depend heavily on the affiliate conducting the network compromise. The ransomware binary does not normally include any mechanism for data exfiltration. Data exfiltration has been observed through the usage of tools such as PuTTY, Amazon AWS S3 buckets/tools, HTTP POST requests, WinSCP, Rclone, Cobalt Strike, Metasploit, and other methods.
- Encryption – RansomHub ransomware has typically leveraged an Elliptic Curve Encryption algorithm called Curve 25519 to encrypt user accessible files on the system. Curve 25519 uses a public/private key that is unique to each victim organization. To successfully encrypt files that are currently in use, the ransomware binary will typically attempt to stop multiple processes. The ransomware binary will attempt to encrypt any files that the user has access to, including user files and networked shares. RansomHub implements intermittent encryption, encrypting files in 0x100000 byte chunks and skipping every 0x200000 bytes of data in between encrypted chunks. Files smaller than 0x100000 bytes in size are completely encrypted. Files are appended with 58 (0x3A) bytes of data at the end. This data contains a value which is likely part of an encryption/decryption key. The structure of the appended 0x3A bytes is listed in the alert with images from three different encrypted files. The ransomware executable does not typically encrypt executable files. A random file extension is added to file names and a ransom note generally titled How To Restore Your Files.txt is left on the compromised system. To further inhibit system recovery, the ransomware executable typically leverages the vssadmin.exe program to delete volume shadow copies.
Important Note for SafeBreach Customers – Coverage for AA24-242A (RansomHub Ransomware)
As soon as details were made available, the SafeBreach Labs teams added attacks based on the advisory and mapped existing attacks in the Hacker’s Playbook to these US-CERT alerts immediately. It is important to note that existing SafeBreach customers already had a good level of coverage against tactics and techniques previously leveraged by the ransomware group identified in the advisory. Please run/re-run the attacks listed below to ensure your environments are protected against these TTPs.
New IOC-Based Playbook Attacks Related to AA24-242A (RansomHub Ransomware)
- #10448 – Transfer of RansomHub (454292) ransomware over HTTP/S (INFILTRATION) – Automation
- #10449 – Email RansomHub (454292) ransomware as a compressed attachment (LATERAL_MOVEMENT) – Automation
- #10450 – Email RansomHub (454292) ransomware as a compressed attachment (INFILTRATION) – Automation
- #10445 – Write RansomHub (454292) ransomware to disk (HOST_LEVEL) – Automation
- #10446 – Pre-execution phase of RansomHub (454292) ransomware (Windows) (HOST_LEVEL) – Automation
- #10447 – Transfer of RansomHub (454292) ransomware over HTTP/S (LATERAL_MOVEMENT) – Automation
Existing Behavioral Playbook Attacks Related to AA24-242A (RansomHub Ransomware)
- #3830 Extract credentials using PwDump through PowerShell
- #5487 Exploit CVE-2020-1472 ZeroLogon
- #5833 Extract Login Information using MimiKatz DCSync
- #6246 Exploit ZeroLogon (CVE-2020-1472) (Windows)
- #6372 Modify Volume Shadow Copy (VSS)
- #6473 Agentless lateral movement via RDP
- #6513 Agentless lateral movement via SMB and RCE, using Mimikatz
- #6581 Discover domain computers using LDAP method
- #6909 RDP Connection Between 2 Simulators
- #6910 RDP Tunneling
- #7043 Disable Cortex XDR using its default password (Windows)
- #7044 Disable Cortex XDR using its default password (Linux)
- #7144 Unregister anti malware scanning interface providers
- #7170 Add a local administrator (Windows)
- #7222 Password Spraying
- #7554 Clear Windows Event Logs
- #7827 Impair Powershell command history logging
- #7834 Add Exclusions to Windows Defender
- #7835 Disable Windows Defender From Registry
- #794 Extract Login Information using MimiKatz
- #8018 Web application port scanning
- #8019 Port scanning target simulator
- #8020 Port scanning of local subnet network
- #8023 EDR evasion by overriding `ntdll` .text section
- #8024 EDR evasion by overriding `ntdll` hooked functions
- #8357 Clear RDP connections history (Windows)
- #8857 Add Mimikatz as exclusion to Windows Defender and execute Mimikatz
- #8867 Pre-execution phase of chisel (767b) hacktool (Windows)
- #9577 Disable Cortex Rules to Execute Mimikatz
- #3829 Run obfuscated Mimikatz on host
- #286 Brute force attack over the LDAP protocol
- #2273 Pass the Hash over SMB using Mimikatz
- #2267 Add an exclusion to Windows Defender using PowerShell
- #2251 Network Share Connection Removal
- #2244 Windows Management Instrumentation Event Subscription
- #2245 Indicator Removal on Host (Windows)
- #2244 Windows Management Instrumentation Event Subscription
- #199 Brute force attack over FTP
- #192 Brute force attack over RDP protocol
- #173 Brute force attack over SSH protocol
- #172 Brute force attack over SMB protocol
- #1339 Remote command execution by PSExec
- #1220 Inject Mimikatz using PowerShell to Extract Credentials
What You Should Do Now
SafeBreach customers can now validate their security controls against these TTPs in multiple ways.
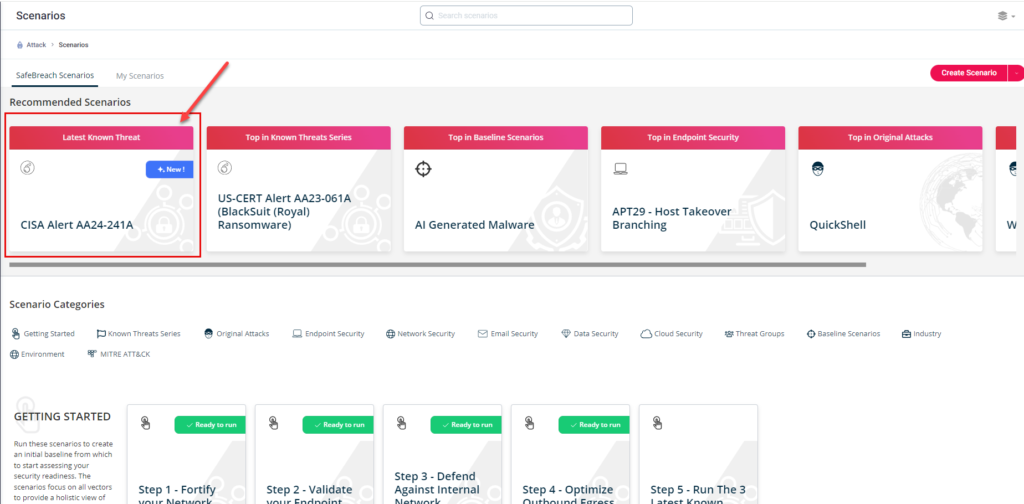
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA24-242A (RansomHub Ransomware)
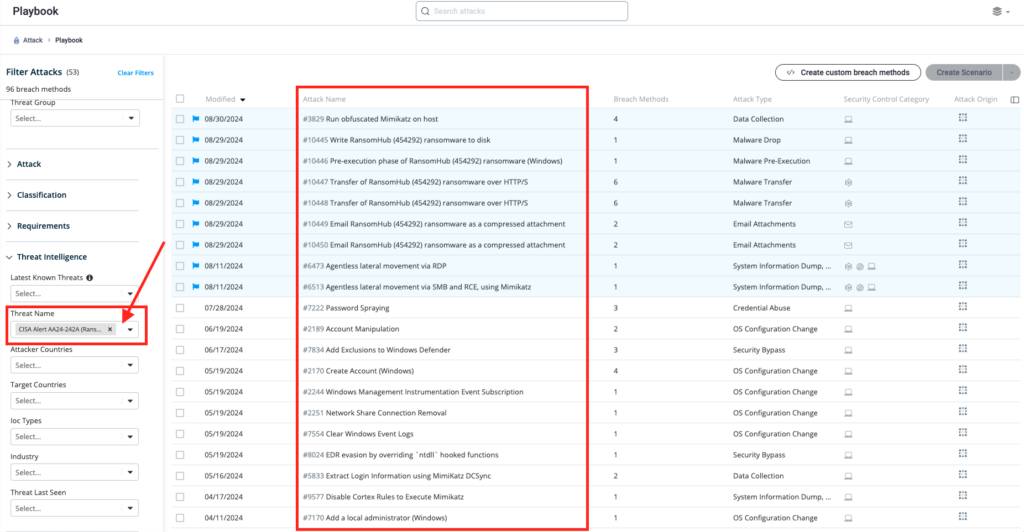
Method 2 – From the Attack Playbook, select and filter attacks related to AA24-242A (RansomHub Ransomware). Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
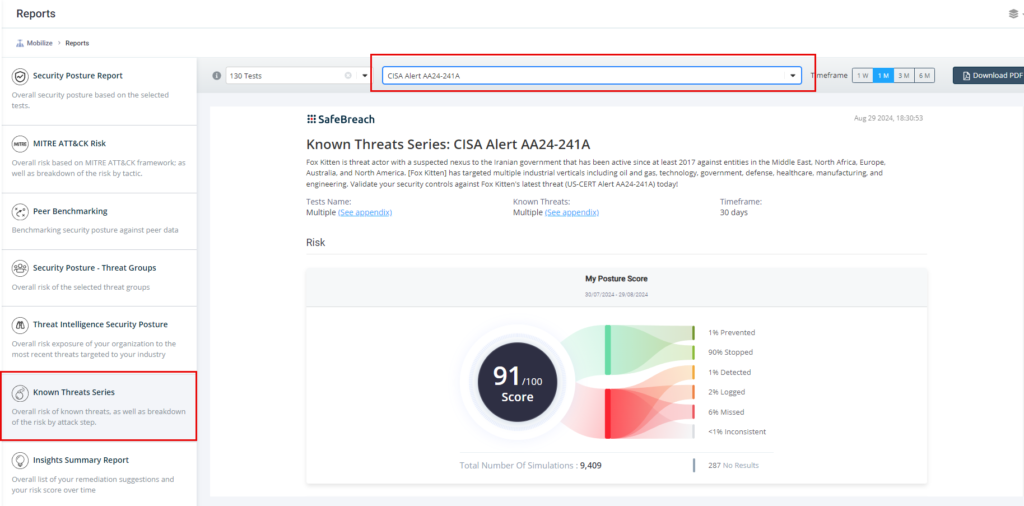
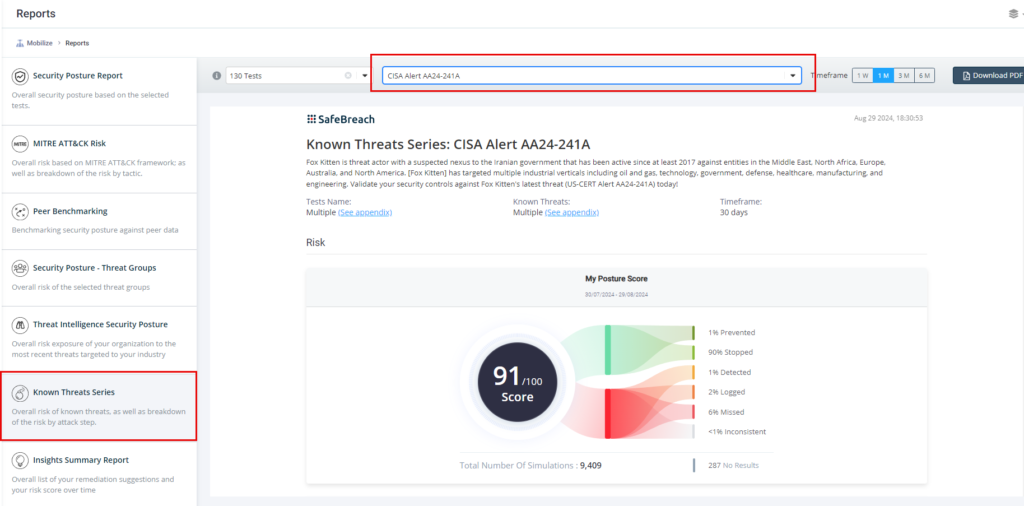
Method 3 – From the Known Attack Series report, select the US-CERT Alert AA24-242A (RansomHub Ransomware) report and select Run Simulations, which will run all attack methods.
NOTE – FBI and CISA recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against growing threat of advanced cyber threats. Additional recommendations can be seen in the advisory (linked below):
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location. Promptly patch all internet exposed devices and services, including web servers, web applications, and remote access gateways.
- Require all accounts with password logins.
- Disable unused or unnecessary network services, ports and protocols.
- Keep all operating systems, software, and firmware up to date.
- Require Phishing-Resistant multifactor authentication to administrator accounts.
- Identify, detect, and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool.
- For additional recommendations, please review the advisory in detail.
You Might Also Be Interested In
Get the latest
research and news
The post US CERT Alert AA24-242A (RansomHub Ransomware) appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by Kaustubh Jagtap. Read the original post at: https://www.safebreach.com/blog/safebreach-coverage-for-us-cert-alert-aa24-242a-ransomhub-ransomware/
如有侵权请联系:admin#unsafe.sh
