2024-8-31 06:49:23 Author: bfore.ai(查看原文) 阅读量:9 收藏
%20(8).jpeg)
Security analysts have a problem, and it isn’t their fault. Due to a lack of context regarding emerging threats, they are understandably confused about how to strategically prioritize remediations in an impactful way. On a daily basis, analysts can see thousands of newly registered domains (NRD) stacking up on the internet and a significant portion of them will turn out to be malicious, suspicious, or not safe for work. According to APWG’s Phishing Trends Summary for 2023, approximately five million phishing websites were recorded inlays year alone, breaking previous records. With about 250,000 average NRDs detected on a daily basis, the volume and level of detection efficiency can greatly impact the takedown capabilities of any company.
But it doesn’t start here. Unbeknownst to the average person, there’s a whole world of cybercriminal activity occurring in the deep and dark webs, where these malicious campaigns are built, bought, and sold. Whenever an adversarial campaign launches its operations to target industries, employees, or even consumers, domains are the key element to their mass targeting and propagation.
As a defensive tactic, many organizations deploy takedowns to tackle cybercrime and threats operating on the surface web. However, traditional takedown methodologies are obsolete in the era of advancing cybercriminal tactics. Many takedown attempts yield poor results due to lagged responses, delayed actions, and lack of sufficient proof to claim maliciousness. We will touch on these pain points more a little later in the article.
Also, we know that doing just one takedown won’t eliminate the lurking threats. Traditional takedowns essentially only skim off the superficial level of threats when observed from an DNS (Domain Name System) adversarial perspective. It will not disrupt the root of the malicious operations, unless the detection systems and takedowns are collectively stronger and swifter than before. Today we’ll compare key points to consider when discussing the difference between domain adversary disruption and takedowns.
Why is it still worth discussing takedowns today? According to threat intelligence and malicious domains expert, Abu Qureshi, there’s been a developing pattern of DNS abuse showing the potential to become a defining term for website-based adversarial campaigns.
There are several typical ways DNS adversaries try to target victims. Generally, one of the following methods is used in social engineering campaigns:
- Phishing campaigns using fake “look alike” websites trick users or customers by asking them to visit a fraudulent website where they give up their credentials, personally identifiable information (PII), financial information, or download trojanized files.
- Parking a domain but enabling their subdomains is an emerging malicious domain trend that is not only harmful, but also a hassle to take down. Normally, the subdomain titled ‘pay.’ results in a payment page while the root domains point to monetized links, or are simply registered without any content on it (also known as parked domains).
- Using email addresses to target customers or C-suite level executives through phishing, whaling, or spear phishing. It might contain malware embedded files that are circulated to emails, likely made available from the internet, which can result in compromised devices and access to sensitive information. In such cases, legitimate domains are obtained only to activate the mail records and avoid suspicion.
Smart cybercriminals mean effective techniques are getting deployed across the internet all the time. But how do they get a domain in the first place? Here are some emerging trends Qureshi recently compiled:
Cybercriminals portraying as legal entities
In this novel practice cybercriminals set up legal companies using fraudulent documents. When a takedown is requested on a domain hosted by a legally-owned company, the domain owner can request a reversal of locks if the proof provided by the threat analyst is insufficient, even if the site is proliferating illegal activity. This can make it difficult for researchers to verify the company’s legitimate existence and execute a takedown.
Anonymity maintained by the domain registrars and hosting providers
Many hosting providers and registrars hide domain ownership information. With ownership information hidden, identifying people running destructive cyber campaigns can be extremely challenging. Attribution for adversarial disruption purposes is still a common pain point for most researchers.
Exploitation of free registrars and geographical distribution
With this method, cybercriminals use fixed, short-term campaigns using reputable, secure registrars offering enhanced identity protection features. Adversaries leverage free trials offered by domain registration services or obtain vouchers for greatly-reduced fees via dark web marketplaces.
Additionally, the takedown process can be greatly affected by geographical distribution. Varied time zones, inconsistent business hours, workloads, language barriers, response times, and acts of nature can all cause significant time lags on a takedown request.
What is a “dark web” marketplace?
Adversarial campaigns generally begin in dark web marketplaces: forums that offer assorted tools, services, and hosting providers to cybercriminals on a subscription basis. These marketplaces harbor a collaborative environment and offer dedicated forums devoted to “the tricks of the trade” for proliferating fraudulent websites, like gathering traffic, search engine optimization, and which hosting solutions are best for evading legal notices for takedowns.
Figure 1: Cybercrime forums advertising hosting providers that evade takedown ‘bullets’, a.k.a., “bulletproof”.
Courtesy: Breachforums
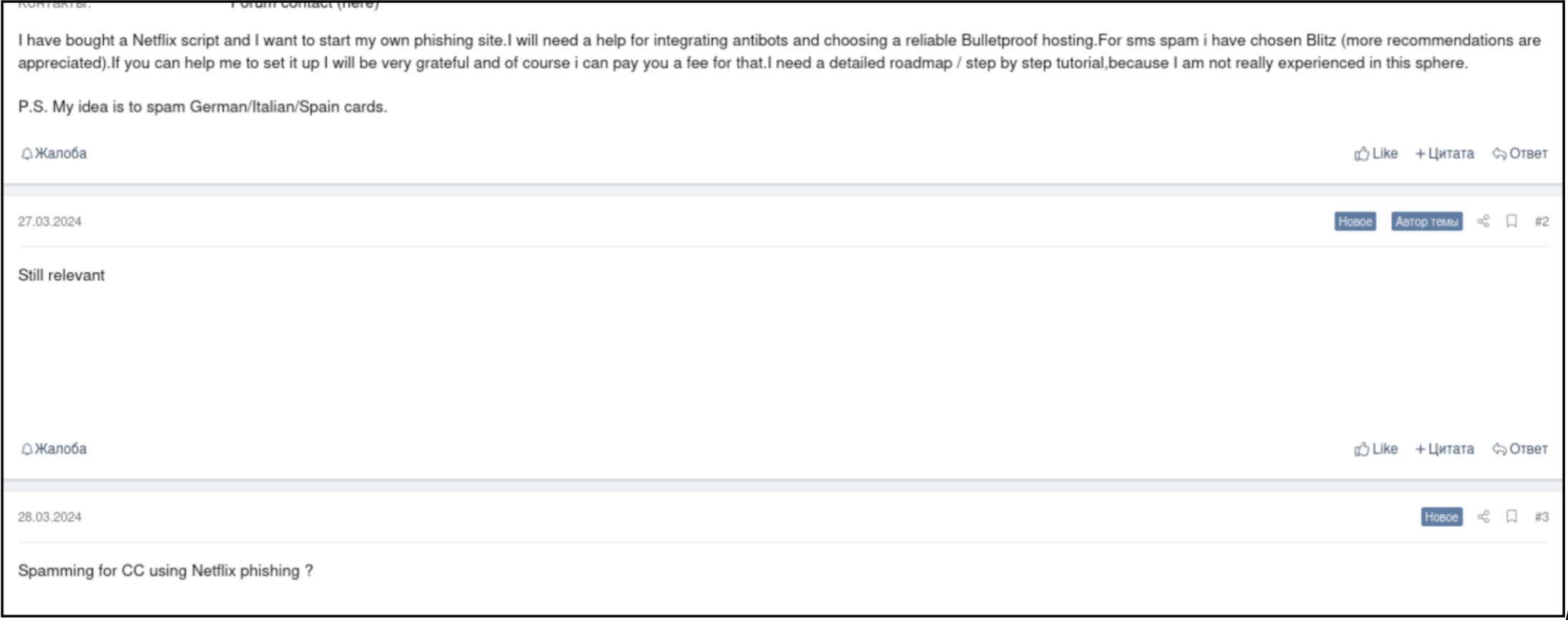 Figure 2: Cybercrime forums hosting discussions on different tools and methods to create a malicious campaign.
Figure 2: Cybercrime forums hosting discussions on different tools and methods to create a malicious campaign.
Courtesy: XSS
Traditional takedown methods are not likely to impact the cybercrime trends mentioned above.
In the case of all these methods, it’s very possible that, by the time a campaign or a pattern is identified and the takedown is completed, the damage has already been done and the malicious operation has achieved its desired result. Then, once the campaign is completed, infrastructure such as domains, emails, and IPs are left dormant or removed from hosting by the cybercriminals.
This raises a couple questions: On what scale should you prioritize a takedown? Should you engage experienced experts to help manage the problem of malicious domains?
It is cybercriminals’ standard operating procedures to target well-known companies that may not address security issues promptly and regularly. Large, familiar business-to-consumer (B2C) organizations with high web traffic and user engagement tend to be default targets. These companies must rely on a combination of an in-house security team with an external vendor with expertise in executing takedowns at scale.
For smaller businesses, it’s good practice to stay aware of the latest cybersecurity news and understand whether customers have faced any malicious campaigns or impersonation attacks. If yes, then a dedicated takedown team should be engaged to hunt down the domains and perpetrators or take further legal actions.
However, is executing a takedown enough? Opinions may differ here. Takedowns are useful to remove any internet-facing threats hosted by an adversary, since these remain one of the easiest ways cybercriminals spread malicious campaigns. The main reason why companies should focus on adversarial disruption as part of their cyber defense strategy is to eliminate the cybercriminals’ operational infrastructure right from its roots.
Furthermore, the process of collecting intelligence on the criminal infrastructure provides the analysts with the ability to execute bulk takedowns, without having to do them one at a time. This intelligence can include:
- The adversary’s preferred hosting provider and registrar.
- Communication details acquired from the domain WHOIS details.
- Email addresses tracking to analyze history and pattern of activities.
- Any other associated information that can help tracing the perpetrators and identifying their motives.
- Analysts can correlate or generate indicators of compromise (IOCs) from a domain that allegedly distributes malware or relays commands, known as C2 (Command and Control). Once intel leads identifying domains using operational malware are confirmed, they need to be shared across security teams to trigger alerts in their endpoint detection and response (EDR) tools.
These intelligence leads can be shared with relevant technical consumers and business stakeholders. Once enough adversarial threat intel is gathered, the next best steps for the security teams is to minimize its impact through takedowns.
How to disrupt domain adversaries?
As discussed above, disrupting domain adversaries is slightly more involved than just conducting takedowns. Since simply performing traditional takedown steps, such as sending a notice to the domain registrars and hosting providers with proofs won’t help, here’s what an organization should do: AUTOMATE repeatable process!
The right automation tool can provide busy security teams with many benefits. Automation can quickly, accurately, and preemptively identify and remediate certain repetitive, low-level threats at scale. If the tool is augmented with predictive AI, it will be able to trigger these actions more autonomously and to handle larger data sets, to predict and prioritize threats so that the security team can focus on the ones that require a human touch.
Here are some additional areas where automation can enhance traditional takedowns and have stronger focus on disruption:
Use of existing automation tools
By establishing a seamless and efficient takedown workflow leveraging automated kill switches, APIs, and reporting mechanisms, a company can report malicious domains in a much more scalable manner versus cumbersome traditional templated takedowns and manual outreach.
Incorporate Threat Intelligence
During the takedown process, a lot of attack intelligence (i.e. threat actors, IOCs, etc.) is collected. By automating IOC usage and threat data by feeding it directly into the takedown report, operators will experience a game-changing shift in the amount of time spent investigating and verifying a threat.
Improved Industry Partnerships
When intelligence regarding a specific threat is gathered, most companies share it with business stakeholders, peer companies, and even the general public to raise awareness and minimize the threat’s impact. By automating malicious domain and takedown sharing with your industry peers and partners, a ripple effect is generated; aiding in diminishing the threat and harboring stronger partnerships.
By implementing and enhancing automation in the above areas, security teams in a company can remain focused on other pain points in the organization, and maintain business continuity and scalability.
When automation removes most of the mundane, day-to-day tasks associated with takedowns, security experts can better focus on the more complex intricacies of performing takedowns due to DNS abuse. DNS abuse is broken into different categories including botnets, malware, pharming, phishing, and spam. These categories overlap with slight differences that each require tailored approaches such as prioritization, intent analysis, chaining the threat, identifying affected industries, and more.
AI plays a critical role in addressing the complexities of malicious domain registration and takedowns. By leveraging predictive intelligence indicators, we can accurately assess the potential risk or malicious intent of a domain before it becomes active. This preemptive approach significantly reduces the effectiveness of evasion tactics and loopholes employed by adversaries.DNS adversary disruption definitely deserves additional attention!
While the advantages of having experienced experts to help manage the problem of malicious takedowns can’t be ignored, it doesn’t mean automation shouldn’t be used where appropriate. Certain measures taken towards risk analysis, threat indications, and threat prioritization for every domain can help teams act more effectively. By dividing every step for a domain takedown into smaller, more manageable segments, and identifying the areas where automation can help, security analysis teams can save a lot of time and energy.
Let’s not forget the preemptive element that can help predict the threat before it happens. What can be better to disrupt a cybercriminal infrastructure than before it even begins? The future of takedowns clearly lies in the ability to leverage predictive defenses to predict, preempt, and deter cybercriminals before they start an attack.
如有侵权请联系:admin#unsafe.sh