2024-8-31 06:49:22 Author: bfore.ai(查看原文) 阅读量:11 收藏
Over the past couple blog articles, we have discussed how malicious domain takedowns remain a relevant cybersecurity tactic, particularly for midsize to large organizations, to minimize attack surface and protect customers. What is often misunderstood about this process and cybersecurity in general, is the critical importance of domain registrars to the security equation.
Domain registrars can play a significant role in safeguarding websites by providing various security features, assuming they are reputable. But there are also ‘bad’ registrars; ones that are not only harmful for a company’s website and its users, but also for their lack of compliance in handling takedown requests resulting in threats to other organizations. These registrars are often referred to as ‘bulletproof’ – hinting at the way they shield cybercriminals from takedowns.
Non-cooperative registrars have attracted many cybercriminals over the years thanks to this “bulletproof” feature, and remain popular for carrying out DNS (Domain Name System) abuse through phishing, botnets, malware C2s, and spam. Most domains that are hosted on such registrars are difficult to take down since the registrars either refuse to understand the case of maliciousness or they want to promote and benefit from criminal activity.
These registrars are a threat to both organizations and the general public, since they act as a safe harbor for cybercriminal infrastructure. Different cybercriminals have different motives for the crimes they perpetrate, but the crimes themselves can range from targeted phishing, mass spamming, defamation, hacktivism, and brand impersonation.
Registrars have an inherent responsibility to address takedown requests for malicious or criminal domains and aid in adversarial disruption. However, when Domain Name Registrar (DNR) services turn a blind eye to the grievances raised, they tend to attract more criminals. This in turn increases the difficulty in categorizing certain types of registrars – whether they’re non-cooperative for operational reasons or because they are sheltering cybercrime.
How does a domain registrar work?
Virtually every modern organization and/or business uses the internet to gain an audience and establish a brand, via a web address or URL (Uniform Resource Locator) of their choice. The URL (the web address by which the brand wishes to be identified) is obtained through a registrar that specializes in issuing domain names within their selected top level domain (TLD), such as “.com”, “.edu”, “.gov”, etc., provided that the domain name is available.
The registrar also assigns nameservers and DNS servers, which are like lookup tables used to translate the text URLs into their numerical IP addresses. All of these steps are important in setting up a website, and registrars offer these services on an annual subscription basis.
A registrar can keep the registrant’s details private on request. However, when legal notices come into the picture, compliant registrars will provide these hidden details, whereas bulletproof or private domains not under ICANNs jurisdiction generally will not. It is worth noting that anyone can find information about a domain by running a Whois query, which highlights the registrar and registrant details, even if the registrar does not comply. There can be many factors that term a registrar noncompliant, one of them is when a registrar service is established to promote cybercriminal activities and openly refuses takedowns of malicious domains. Other reasons can be as simple as registering company location, workforce issues, an inconsistent takedown request process, lengthy response times, or an overwhelming volume of takedown requests.
Noncompliant Registrars Promoting Cybercrime
Cybercriminals primarily engage in DNS abuse for phishing or brand infringement activities, and seek registrars that are lenient or negligent regarding takedowns. Such services are formed by criminals for criminals, meaning that even consistent follow-up on a takedown request might not yield the desired outcome. Such services can be openly identified on cybercrime marketplaces, and their reputation defaults to noncompliance, as they exist to service cybercriminals under the guise of legitimate domain registrars.
The domains found on these registrars’ servers are often associated with activities like:
- Blackhat SEO
- Botnets for “command and control” and malware deployment
- Pharming
- Spamming
- Mass registrations for brand abuse of any entity
- Fake shops and services
- Fraudulent servicing of legitimate companies
- Domain hijacking
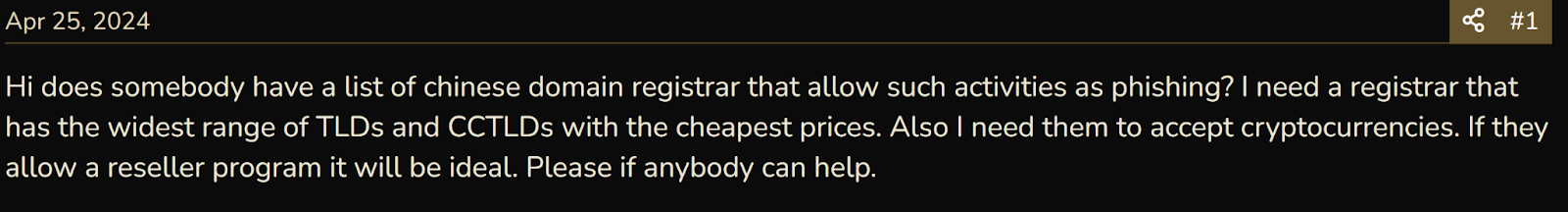
Below are examples of chat threads from cybercrime forums using “registrar” as the search term. There are open discussions regarding identifying domain registrars that will support legal noncompliance, allowing the criminals to remain anonymous and protect the websites that are a part of their malicious infrastructure.
By understanding and flagging the sources of malicious domains, we ensure the bad registrars earn the reputation they deserve. The reason is simple – when malicious websites are consistently flagged from a single DNR server, they are termed as noncompliant for takedowns, leading to gradual building of evidence against them to support their noncompliant designation.
Registrars noncompliant due to jurisdiction
Registrars are responsible for being compliant based on a set of regulations established by ICANN (Internet Corporation for Assigned Names and Numbers). ICANN also maintains a list of their accredited registrars who can resell domain name registrations and governs their activities.
Cybercriminals are constantly developing new methods to bypass country-specific cyber laws. They understand that different countries have different cyber laws and the severity of the criminal penalties can vary accordingly. This generally means that domains that fall into malicious categories such as brand infringement or phishing are usually registered out of the victim’s country. Regions that fall outside of the victim’s legal jurisdiction are far less likely to result in punishment.
All registrars offer optional privacy features for domain owners to protect registrant details that can be quite stringent. When a request to know the identity of the registrant is evaded, it will flag the registrar as “non-compliant” and will likely cause them to end up on a ‘bad registrars’ list. DNR services not accredited by ICANN, lie outside of ICANNs jurisdiction zones and don’t entertain requests regarding identity disclosure or cybercrime disruption. There is a growing trend of cybercriminals using private domain providers in combination with bulletproof hosting to ensure their websites remain “takedown-proof”.
Most legal authorities or domain protection organizations invest a lot of time and effort to make registrants’ details available. However, due to the delays caused by non-cooperative registrars, the malicious domains in question are able to continue perpetrating the intended crimes.
Miscellaneous registrar-based barriers
While at times the registrar itself can be malicious, there are certain other miscellaneous factors that can put them in non-cooperation. For example, a days-long delay to complete a takedown due to a registrar’s slow initial response can result in non-cooperative. Based on recent statistics that analyzed average takedown time, the minimum time for a registrar to respond to a takedown request is four days. However, this response can extend up to 117 days in particularly bad cases, causing the mean time to takedown across 35 different registrars to average 76.35 days.
Even a registrar with a good reputation can, at times, also become noncompliant due to factors such as the size of their operational workforce. Based on the quarterly analysis of the Cybercrime Information Center that reported malware activity for the first quarter of 2024, 986 registrars were responsible for hosting domains that were involved in DNS abuse. As compared to the previous quarter, one registrar notorious for its malicious activities showed an increase of 38400% in DNS abuse. These numbers provide significant evidence showing the rising exploitation of DNR services and the necessity of a steady workforce that can work round-the-clock to address takedown requests.
To inadvertently address these issues before malicious domains can cause trouble, registrars highlight the kind of evidence that is sufficient to immediately initiate the removal of a website. Many website removal requests are sent without a standardized format, which can result in much back-and-forth communication to gather sufficient evidence of the website’s malicious activities. For the same reason, certain registrars like Cloudflare have created a web form to organize the offending website into different threat categories and gather the evidence necessary to trigger a takedown request. Strategically, this is a good method, as it standardizes the process and reduces delays.
The future of takedowns in light of registrar noncompliance and increasing DNS abuse
Takedowns, which remain an essential cybersecurity tactic, heavily rely on registrar cooperation. Artificial intelligence (AI) systems supporting traditional takedowns can assure managed threat detections and alerting, while addressing scalability. Millions of newly registered domains (NRDs) intended for DNS abuse are detected on a daily basis, so having an ecosystem that maps takedowns and registrar compliance to evaluate their intentions would prove to be helpful.
According to a report by M3AAWG registrars are required to evaluate the intent of registrants and lock suspicious accounts, along with sinkholing the registered domains. Through domain sinkholing, any user visiting a confirmed suspicious website will be redirected to a controlled IP to block traffic to such sites.
Trends indicate the promise of registrars and hosting providers embedding a system that leverages AI to analyze and detect a malicious domain in registration and preemptively prevent it going live. Additionally, the domain registrant’s activities can be tracked and analyzed using behavioral AI to identify suspicious activities, in the case of account takeovers or domain hijacking, to significantly reduce campaigns based on compromised registrant accounts or fraudulent domain registrations.
Best practices for navigating non-cooperative registrars to ensure near takedown results
While there is no guaranteed outcome, there are some best practices that can help push noncooperative registrars to take action. It doesn’t always have to be a takedown, but to collectively halt the operations of the reported domain or alert the visitors of its maliciousness is critical.
Organizations that are victims of DNS abuse can reach out directly to the hosting provider and registry regarding the malicious domain, or engage with their security vendors to do so on their behalf. This will most likely result in removal of the content hosted on the website, leading to default pages and no links for visitors to engage. Additionally, partnering with other security vendors to flag these domains on popular Threat Intelligence Platforms (TIPs) can build significant pressure on the targeted registrar to actuate takedown requests.
Moreover, it is recommended to accumulate strong evidence of fraudulent activity to avoid any delays or other issues with takedowns. Having a standardized reporting template that fits well with most registrars can help yield timely results. To stress the urgency of a threat, one best practice is to connect with the offending registrars, including via social media accounts, to try to get a prompt response. This includes having a list of connections such as upstream providers, escalation contacts, or other relevant DNS abuse operators to hasten the takedown process with DNRs.
In the event of consistent non-cooperation by the DNR to take a domain down, security analysts can submit or share malicious ratings and report the domain to platforms such as Google Security Operations, VirusTotal, Quad9, and others. Once a malicious score is set by various vendors, search engines such as Google, Bing, and Brave will add a red flag to alert the visitors visiting the domain in order to reduce its traffic, even if the website is still active.
While dealing with non-cooperative registrars may require persistent effort, their obstructions can be circumvented by taking a nuanced approach. Additionally, with AI-enabled techniques to handle registrar engagement and takedowns at scale, navigating non-cooperative registrars can be strategically addressed. By adopting AI-based, preemptive security, following disruption principles, and using emerging predictive attack detection methods to scale the takedown requests, organizations can overcome resistant registrars and achieve the early responses that lead to early action.
如有侵权请联系:admin#unsafe.sh