
2024-8-31 06:49:17 Author: bfore.ai(查看原文) 阅读量:11 收藏
2024 Paris Olympic Games Infrastructure Attack Report

The Paris Olympic Games, which officially started on 26 July, 2024, has been swirling with malicious and cybercriminal activities for months before the event. Adversaries were found to have set up social media accounts, stores, ticketing systems, and cryptocurrencies amidst the popularity and commotion of the Olympics. Researchers at BforeAI analyzed the set of NRDs (Newly Registered Domains) acquired two weeks prior to the event and analyzed the rise in malicious activities, discussed briefly in this report.
During the analysis, a total of 166 unique domains were discovered that leveraged on the common signs of DNS abuse such as keyword stuffing, typosquatting, and known top-level domains (TLDs) often used for phishing. Through these means, the threat actors attempted to conduct financial scams by replicating the existing brands relevant to this event.
These sets of malignant domains use unconventional or suspicious TLDs such as .xyz, .win, .stream, .mobi, .shop, .store, and .info, often preferred because they are cheaper and less regulated. In addition, common misspellings or variations of “Olympics” (e.g., “olymplics”, “olymppics”, “olympicpepe”, “olympicgold”). This is a tactic to catch users who mistype the domain name.
A significant use of keywords related to the Olympics and specific years or events (e.g., “paris2024”, “olympics2024”, “slc2034”, “winterolympics2034”) were found. This is an attempt to attract traffic and appear relevant to search engines. By doing so, the domains in this cybercriminal infrastructure gain an advantage of ‘domain age’ which can influence their future search engine rankings and search engine optimization (SEO). A good domain age can benefit the success of email delivery rates and increase public trust to improve malicious campaign performance.
Counterfeit Olympic shop domains appeared to be increasingly prevalent in the lead-up to the Paris Olympics, potentially resulting in significant financial losses for fans and enthusiasts looking to purchase official merchandise and experiences. These fraudulent sites take advantage of the excitement surrounding the event, misleading consumers and undermining the integrity of legitimate vendors. Some notable examples included:
- parisolympics2024[.]store
- shop-olympics[.]shop
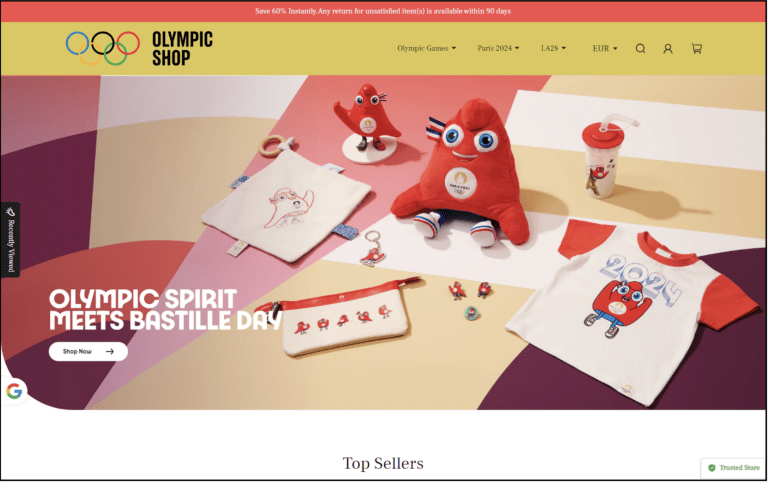
Figure: Fake shops set up prior to the Paris Olympics attempt to commit financial fraud and collect personal information.
Cybercriminals exploited the popularity of the Paris Olympics to sell counterfeit tickets. These fraudulent websites, often deceptively named things like, “Paris Olympics 2024 Tickets,” aimed to steal personal information such as name, email, address, and contact details from unsuspecting users redirected to these sites. Further, the same website can also persuade visitors to buy the fake ticket, capturing their payment information such as credit card numbers, expiry dates, and CVC codes. Such data often lands up on the dark web for sale or exploited for future financial frauds.
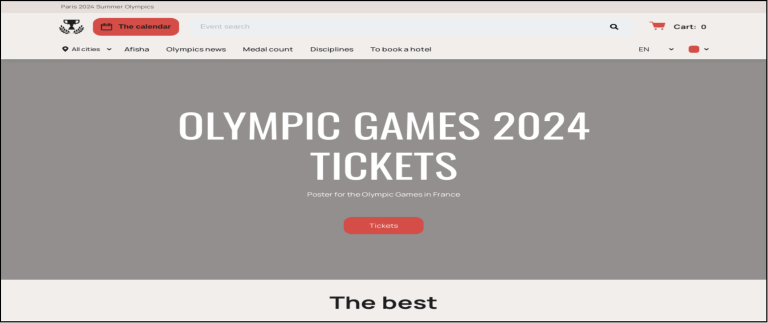
Figure: Olympic ticket sales are done through fake websites for financial gain and/or information harvesting.
There was a significant use of similar names mixed with multiple TLDs, possibly to create confusion or redundancy (e.g., “parisolympic2024.live”, “parisolympics2024.live”, “parisolympics2024.store”). This also highlighted the inconsistencies in branding and naming conventions, mixing city names, event names, and event years in a way that is not typical for official websites (e.g., “visitparisolympics2024”, “boysinparis2024”, “parimatch-2024”). Certain subdomains and prefixes were discovered in such domains like “visit”, “teamusa”, “boycott”, “esports”, “api”, which might not be commonly associated with official Olympic content.
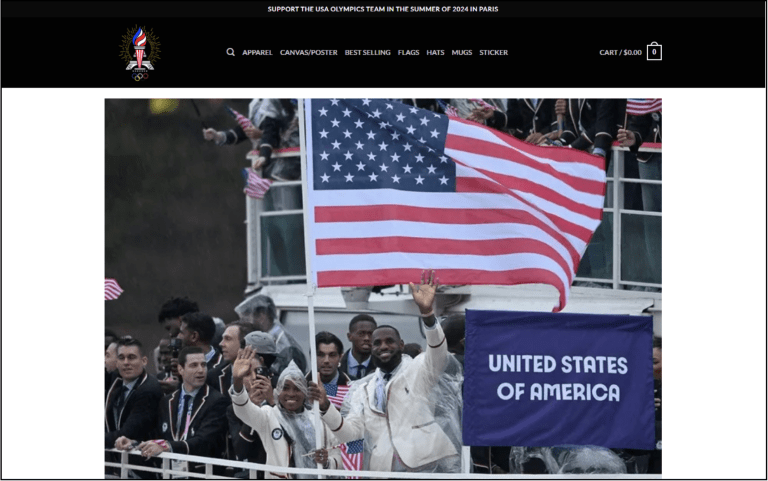
Figure: Different websites were set up to support their respective countries
Also, numerous scam cryptocurrency coins and tokens are being marketed using Olympic-related branding. Similar scams have been seen during previous major events like the FIFA World Cup, and they can lead to substantial financial losses for unsuspecting investors.
Some websites even offered free live streaming, which was obviously unauthorized in nature. This can hurt media broadcasters and advertisers and affect the revenue of the Olympic Games and/or the International Olympic Committee (IOC), who organizes the event. A small group of betting domains was identified attempting to collect financial information from unsuspecting victims interested in placing bets on Olympic sporting events.
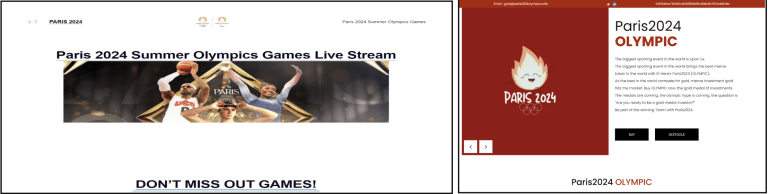
Figure: Unauthorized live streaming websites pose a threat to official broadcasters.
Ways to have a Secure Olympic Experience
Cyberthreats are an inevitable part of any global mega-event and a golden opportunity for scammers trying to defraud the public via various phishing methods. The top suggestion to help ensure a secure Olympic experience as an individual would be to rely solely on official Olympic websites and social media channels. Be wary of unofficial content and avoid clicking on suspicious links. Purchase tickets and watch live streams through authorized platforms only.
A website hosted on an unfamiliar TLD should be verified before entering any personal information. This is further exploited in social engineering campaigns such as phishing attempts on email, messages, and calls (popularly known as vishing).
Any sort of investment around cryptocurrencies created solely for the Olympics event should be strictly avoided, as they are highly volatile and prone to scams. Investments made through unreliable sources such as these can lead to heavy financial losses.
Referring to complaints regarding any fake Olympics-based website on social media and taking the time to report them can help foster a safer online environment for everyone.
With the rise in strikingly similar domains related to the 2024 Paris Olympics, it is essential to enhance adversarial disruption capabilities using predictive analysis with AI. Disrupting or taking malicious infrastructure down completely before it becomes live can halt the campaign in its foundational stage, before it has a wider impact on the general public. Continuous monitoring of the registrars linked to identified malicious domains can help uncover the tactics, techniques and procedures (TTPs) used and inform future activities around globally critical events.
Ready to see BforeAI in action?
Get a personalized demo
Talk to one of our experts and deploy in minutes.
No implementation needed. Works right out of the box!
如有侵权请联系:admin#unsafe.sh