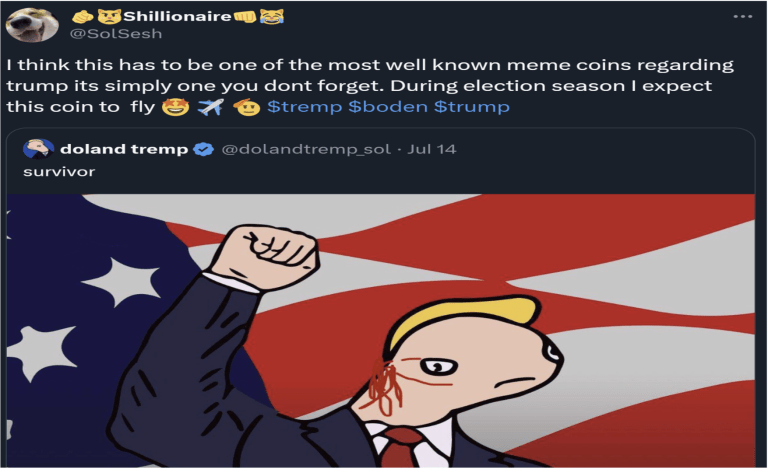
2024 US Elections Infrastructure Attack Report
The US elections are set to be held on November 5, 2024, and there have been numerous global threats revolving around this significant event. Cybercriminals have extensively relied on candidate names to make their campaigns impactful and believable. Most of these campaigns serve the purposes of financial fraud or misinformation regarding elections and voting. Researchers at BforeAI analyzed a set of PreCrime threats, including newly registered domains (NRDs), acquired over months to uncover interesting methods used in conducting malicious attacks, discussed briefly in this report.
Most phishing campaigns related to this year’s election event were focused on presidential candidates. The domains primarily used the strings of ‘harris’, ‘kamala’, ‘trump’, and ‘biden’, followed by state and local candidates participating in down-ballot elections as a secondary choice.
Using the candidate keywords can bring more credibility to fake domains and can easily mislead the public. Election integrity and voting can be manipulated using strong emotional sentiments through patriotism, fear, or anger, to elicit desired actions.
Domains having ‘vote’ and ‘election’ keywords are generic in nature, but offer the broad appeal necessary to attract a large audience, making them useful for future campaigns. As the domain ages, its reputation and trustworthiness rise and multiple future election campaigns can be hosted around these events.
Domains with candidate names can create believable phishing sites, misleading supporters into providing personal information or making donations to fake campaign funds. Such funding pages can attempt to steal personally identifiable information (PII) and steal credit card information and funds from unsuspecting supporters. The PII can be further leveraged to run misleading election information and spam irrelevant content to potential voters under the guise of political support.
Multiple websites were attempting to suppress voter’s turnout by providing misinformation about voting dates, locations, and requirements. News articles such as promoting specific propaganda against candidates and fake facts through whistleblowing websites were disseminated to manipulate voter opinions and behaviors, with the goal of impacting the election outcome.
Common indicators of maliciousness were seen on multiple domain names where they were registered with typographical errors, or redirecting to phishing websites. Others included mimicking official candidate names, election-related trademarks, or even recent registrations, particularly close to the election period. Such domains can be set up and abandoned quickly for specific election-related attacks
URL: https[:]//vote-no-sunnybailey[.]com
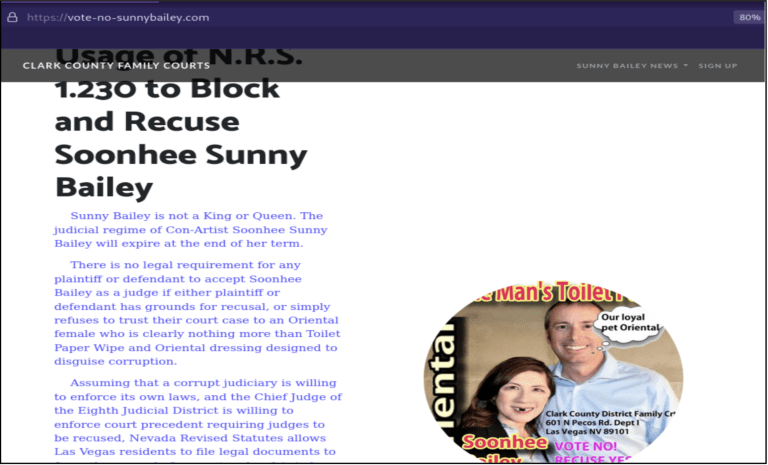
Figure: Web pages manipulating visitors by stating unverified facts about eminent personalities
Various ecommerce stores were set up to capitalize on the excitement surrounding the event and spread propaganda. The sample messages found on T-shirts sold by these ecommerce websites are to promote a candidate’s favorability. Malicious shops aiming to gain financially through this method are designed to steal personal information like name, email, address, contact details, credit card numbers, expiration dates, and CVC codes from unsuspecting users. This stolen data is then sold on the dark web or used for future financial fraud and social engineering attacks.
URLs:
votefordonaldtrump2024[.]com
trump2024voteforme[.]com
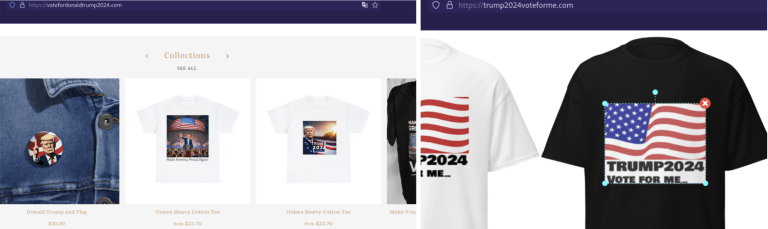
Figure: Ecommerce stores promoting US election candidates and potentially leading to financial fraud
Websites using keywords related to the US elections were discovered to contain inappropriate content originating from China. This is a clear attempt to deceive voters by using misleading tactics. These low-level cybercriminals are using clickbait to lure people to dangerous websites. These malicious redirects can infect devices with harmful software like adware and spyware.
Criminals exploited free website hosting platforms to create multiple websites at no cost. This allowed them to register large numbers of domains quickly and easily. After the election, they could effortlessly remove the harmful content, leaving minimal trace. This approach maximizes their impact while minimizing their risk.
URL: vote2024[.]freeservers[.]com
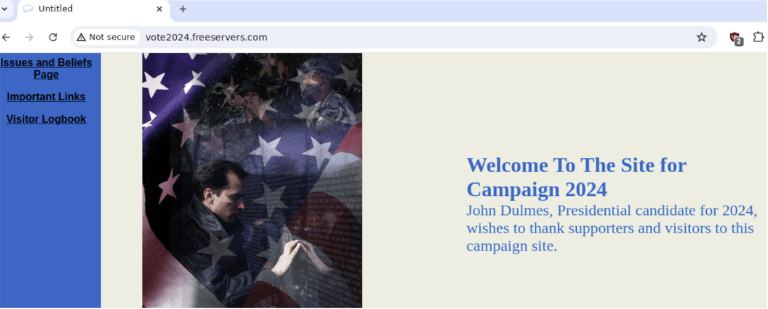
Figure: Adversaries using free web page hosting services to temporarily run campaigns
Additionally, fraudsters were found to be creating digital currencies branded with election-related themes, and promising unrealistic returns to investors. This tactic mirrors similar schemes used during major sporting events like the FIFA World Cup and the 2024 Paris Olympics, which have resulted in significant financial losses for people who fall victim to these schemes.
URLS:
tremp[.]xyz
noooo[.]meme
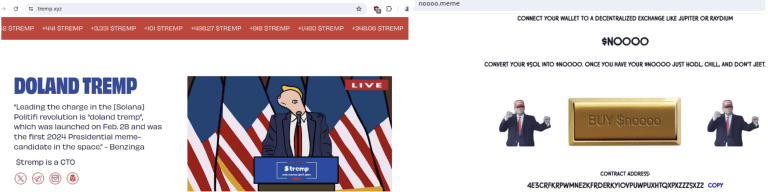
Figure: Meme crypto coins based on US election themes recently surged luring victims to invest in volatile markets
These coins are taken up by the influencing community on Twitter and other social media which mentions whether the value of the coin will rise or fall around the elections. Such attempts to lure users is also a psychological hit to voter’s integrity and clouded judgment on voting.
Figure: Unauthorized live streaming websites pose a threat to official broadcasters.
In addition to the above, many web pages displayed under construction, parked or “coming soon” messages, which is often indicative of future malicious behavior when combined with other elements such as typosquatting or brand infringing.
Safeguarding Your Identity And Your Vote
Amid multiple malicious campaigns attempting to compromise a voter’s identity, financial information, and vote, there are some steps to consider.
The only legitimate website to reference voting information is the usa.gov official website, and voters can register at vote.gov. Information coming from ‘.gov’ TLDs are the only ones that should be considered, since these can only be used by governmental agencies. A legitimate website also uses HTTPS protocol to safely transfer information through encrypted means over the Internet.
Any website that asks for payment should be further verified, since the money provided for donation can disappear without reaching the intended cause. It is advised to visit the original website to verify the legitimacy and avoid clicking on emails and SMS spam through unknown contacts.
Investing in meme coins by being influenced on social media can turn out to be a risky gamble. Such coins are made to gather funds and vanish without a trace, and pivot someone’s favorability in voting. People who are attracted to quick money making methods should carefully consider the volatility of such meme coins.
Cybercriminals use free hostings and typosquatted domain names on a large scale during globally significant events. With the upcoming US elections, a preemptive mitigation approach is crucial to counter potential cyber threats. Even websites that are currently online or those recently registered without content could be the indicators of future attacks. To protect the integrity of the elections, it’s essential to report suspicious websites to authorities and request a takedown before they can be exploited against unsuspecting citizens.
This table represents the most directly relevant US election domains analyzed by our team out of 3882 identified.
|
vote4trumpvance2024.com
|
votekamalakelly2024.com
|
wevotejoebiden2024.com
|
Ready to see BforeAI in action?
Get a personalized demo
Talk to one of our experts and deploy in minutes.
No implementation needed. Works right out of the box!
如有侵权请联系:admin#unsafe.sh