International Pizza Chain Domain Spoofing Report

BforeAI researchers uncovered a sophisticated phishing campaign targeting well-known international pizza restaurant chains, resulting in financial losses. The investigation was initiated following a tip-off from a Singaporean police phishing advisory that was referenced in a Yahoo News Singapore article. The initial indicator of compromise (IOC) led to the discovery of a much larger, more elaborate and still active malicious campaign that spans multiple countries and targets various pizza restaurant brands.
Previously known intelligence
Based on the references from the Singapore Police Department, the campaign was first identified through the domain domino-plza[.]com, which resulted in a S$27,000 financial loss for seven victims through Singapore locations of Domino’s Pizza restaurants. This domain was used to mimic legitimate order pages, deceiving customers and stealing their funds.
The threat actor was also involved in paid search engine advertising to ensure that malicious domains were at the top of search engine results, even before the victims could reach the original website. This tactic, often combined with black hat search engine optimization (SEO) techniques makes the victims vulnerable to phishing attacks.
After successful phishing attempts in Singapore, the same threat actor behind this campaign has registered domains targeting multiple large international pizza restaurant chains, including PizzaPizza, Little Caesars Pizza, Blaze Pizza, 241 Pizza, Panago Pizza, and Boston Pizza. These domains often resemble the legitimate ones but include subtle variations designed to mislead unsuspecting customers.
As recently as 5 January 2024, the malicious actor continues to register domains using IP addresses 195[.]123[.]218[.]23 , 38[.]180[.]29[.]124 and 146[.]19[.]106[.]54. The domains associated with these IPs include registering with unusual top level domains (TLDs) such as “.life,” “.top” which are uncommon with legitimate brands.
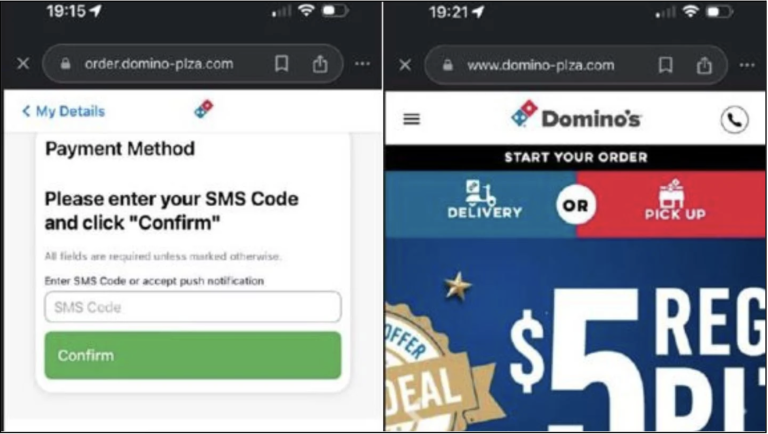
This scam begins with the creation of a typosquatted malicious website that is a near replica of the legitimate pizza delivery chain. These websites also mimic the original website’s features and layout. During the checkout process, users are prompted to enter an One-Time Password (OTP), similar to the reference image below. This OTP verification step is a common security measure to confirm card details. Some pizza brands also have a feature to validate and store the card for easier check out in the future. However, in this scam, the card information is stolen through the attacks enabling the attackers to conduct unauthorized transactions, also known as “carding”. Ultimately, this leads to loss of funds for the victim.
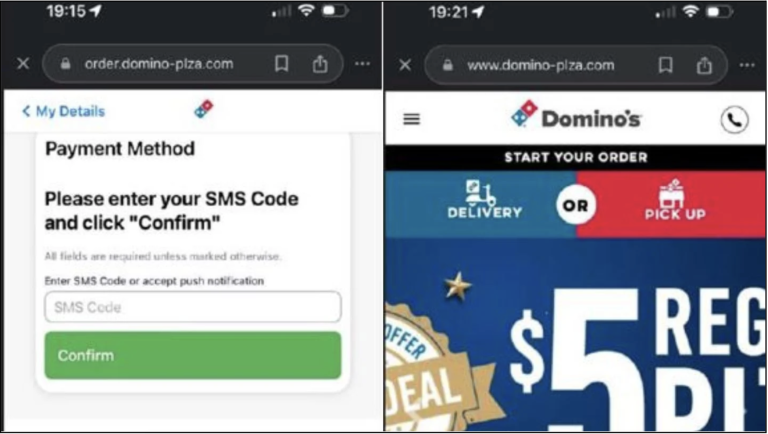
Figure: A malicious website replicating the “Dominos” brand for phishing purposes.
This campaign leverages common attack vectors like typosquatting to create domains with slight misspellings of legitimate ones and homograph attacks which use similar-looking characters. Additionally, attackers often utilize freely available page formats or even employ generative AI to create websites and its prominent features within minutes.
The campaign is not limited to a single country but targets international pizza restaurant chains, making it a global threat, with a concentration on some Canadian pizza chain restaurants – the attacker’s ability to register and maintain multiple domains indicates a well-resourced operation aimed at exploiting the popularity and trust associated with these brands.
Despite the initial impact in 2023 in which seven customers lost nearly S$27,000, this phishing campaign remains a potential threat. A recent spike has now been observed using popular Canada-based pizza restaurant chains, PizzaPizza, Little Caesars Pizza, Pizzaiolo, Panago Pizza and Boston Pizza.
This pattern, where there is a shift in server locations and dates of activity from passive DNS records, suggests that these attacks are part of a continuous campaign. The actor used Stark Industries VPS services in both Singapore during the December campaign and Canada for the recent one. The reputation of this VPS provider is quite questionable as it highlights the facilitation of these malicious activities.
Recent research has revealed that some of the associated phishing domains have undergone registration updates in 2024, suggesting ongoing activity. While some of these domains are currently redirecting to non-threatening websites, their recent registration indicates a potential for future malicious use.
The original IP addresses related to the bulk of the identified pizza restaurant chain phishing activities have seen new registrations targeting new entities as recently as April 2024, by the same threat actor. This highlights the persistent nature of phishing campaigns and the need for continued monitoring of newly emerging threats.
Based on the most recent examples targeting Italian horticulture firm Oxyden, it appears that the malicious actors are even expanding their efforts to include other organizations outside the original pizza restaurant chain theme covered in this report.
To stay protected against such attacks, customers of popular pizza chains should watch for red flags in domain names, such as misspellings or unusual characters, signs of a typosquatted domain. Additionally, it is essential to pay attention to the domain’s registration date as a popular brand will not have any recently registered websites with unfamiliar TLDs. Enable multi-factor authentication (MFA) on your accounts to add an extra layer of security. However, if you accidentally share an OTP with a scammer, promptly report suspicious transactions to law enforcement and monitor your account for anomalies.
From an organizational standpoint, this campaign highlights the growing sophistication of phishing attacks targeting the food and beverage industry. Cybercriminals are increasingly using domain spoofing to deceive customers and steal funds. It is crucial for organizations to proactively monitor threats against their brands closely and for customers to be vigilant when placing online orders. The ongoing activity of this threat actor suggests that the campaign is not over, and further vigilance is required to prevent additional losses.
|
Indicators of Future Attack- IP & Domains |
|
| 195.123.218.23 | 38.180.29.124 |
| 146.19.106.54 | |
| busters-pizza[.]top
canadian-pizzas[.]com blazepizza-us[.]com panago-pizzaa[.]com boston-piza[.]com crust[.]life kltchenwarehouse[.]com oxyden[.]top oxyden[.]space domino-plza[.]com pangao[.]org panagoos.top panageca.top panagos.top panaros.top pan-ago.life pizzapanagacas.top ponogaspizzas.com ponaago.com pannaga.top |
phd-hk[.]com
mieete[.]com boston-piza[.]com boston-piza[.]com deeliveroo[.]com crustau[.]net 241piza[.]com callapizzas[.]com blazepizza-us[.]net paanagoo[.]com pizzaplzza.com pizza-iola.com gabrielpiza.com panogoca.com llttlecaesars.com panag-ca.life panagoca.life piza-73.com pl-za-73.life |
Ready to see BforeAI in action?
Get a personalized demo
Talk to one of our experts and deploy in minutes.
No implementation needed. Works right out of the box!
如有侵权请联系:admin#unsafe.sh