We’ve uncovered a new campaign delivering DeerStealer malware by exploiting Google’s own advertising platform and other legitimate services.
Read in-depth analysis of DeerStealer.
What’s happening?
Adversaries are impersonating Google Authenticator in Google Ads to deliver the DeerStealer information-stealing malware.
The campaign uses sophisticated techniques to evade detection, allowing it to target users searching for legitimate software. Hackers are likely using a centralized command and control (C2) structure to manage this operation.
The following table shows the key components of this campaign:
| Component | Details |
|---|---|
| Target | Google Authenticator users |
| Platform Exploited | Google Ads |
| Malware | DeerStealer |
| Affected Systems | Windows |
DeerStealer is a modern information stealer capable of extracting credentials, cookies, and other sensitive data from web browsers.
Breaking down the attack chain
The attack begins with malvertising on Google search results, driving victims to fake ads that display legitimate Google domains to increase credibility. When users click these ads, they’re led through a series of redirections, ultimately landing on malicious sites like “chromeweb-authenticators.com”.
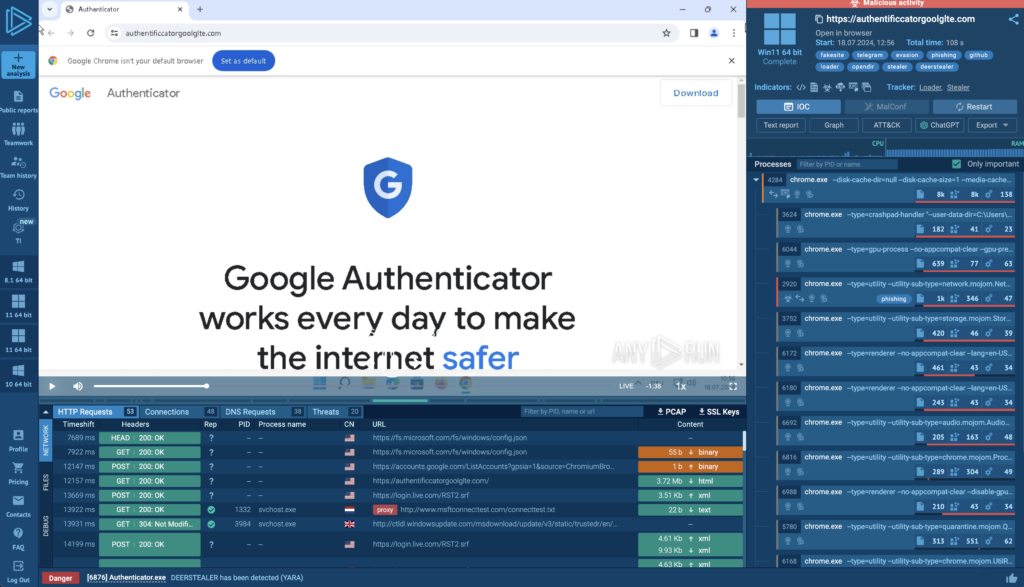
The fake websites prompted users to download a file named “Authenticator.exe,” hosted on a GitHub repository named ‘authgg’ by ‘authe-gogle.’ This file contained the DeerStealer information-stealing malware.
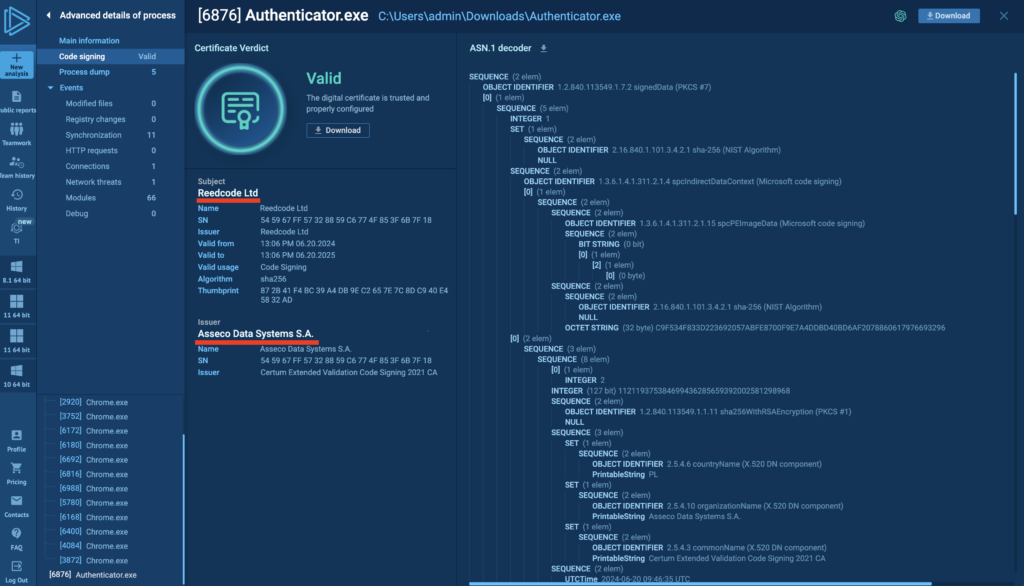
The executable was signed by companies such as Reedcode Ltd., making it appear legitimate and capable of bypassing security systems.
How Google responded
Google, upon being alerted by Malwarebytes, blocked the fake advertiser. The company is working to improve its detection systems by scaling up automated tools and human reviewers to better identify and remove such malicious campaigns. In 2023, these efforts led to the removal of 3.4 billion ads, the restriction of 5.7 billion ads, and the suspension of 5.6 million advertiser accounts.
How to protect yourself
Here are a few things you can do to protect against DeerStealer — and other malware:
- Avoid clicking promoted results in Google Search
- Use an ad blocker
- Bookmark official software project URLs
- Verify download URLs match official domains
- Scan downloads with updated antivirus before executing
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Request 14-day free trial for your entire team →
Stas Gaivoronskii
Stas is a malware analyst at ANY.RUN. He has more than 11 years of experience in the digital forensics field and 4 years in malware analysis.
Stas is a malware analyst at ANY.RUN. He has more than 11 years of experience in the digital forensics field and 4 years in malware analysis.

Jack Zalesskiy
Technology writer at ANY.RUN
Jack Zalesskiy is a technology writer with five years of experience under his belt. He closely follows malware incidents, data breaches, and the way in which cyber threats manifest in our day-to-day lives.


