An emerging threat is a new or evolving cybersecurity risk that is particularly challenging to defend against due to the lack of intelligence on its attack methods, strategies, and techniques.
These threats can take various forms, from sophisticated malware to unconventional attack vectors. They also often exploit new vulnerabilities or technologies that can bypass current security measures.
Characteristics of Emerging Threats
Unlike persistent threats, which are well-known and have existing defenses, emerging threats:
- Involve new techniques, tools, or exploits that have not been widely seen before.
- Evolve continuously, with attackers continually refining their methods to evade detection and countermeasures.
- Can be difficult to predict, making them challenging to defend against.
- May have much more serious implications for victims.
Why Organizations Need to Monitor Emerging Threats
Many organizations are not equipped to handle emerging threats due to a lack of awareness, resources, or expertise. Such threats can disrupt their operations, lead to data breaches, and cause financial losses. They can also damage a company’s reputation and have a negative impact on customer trust.
To protect their assets, businesses need to stay informed about emerging threats and take proactive measures.
How Threat Intelligence Lookup Helps Collect Information on Emerging Threats
One of the services that help organizations learn about new threats is Threat Intelligence (TI) Lookup from ANY.RUN.
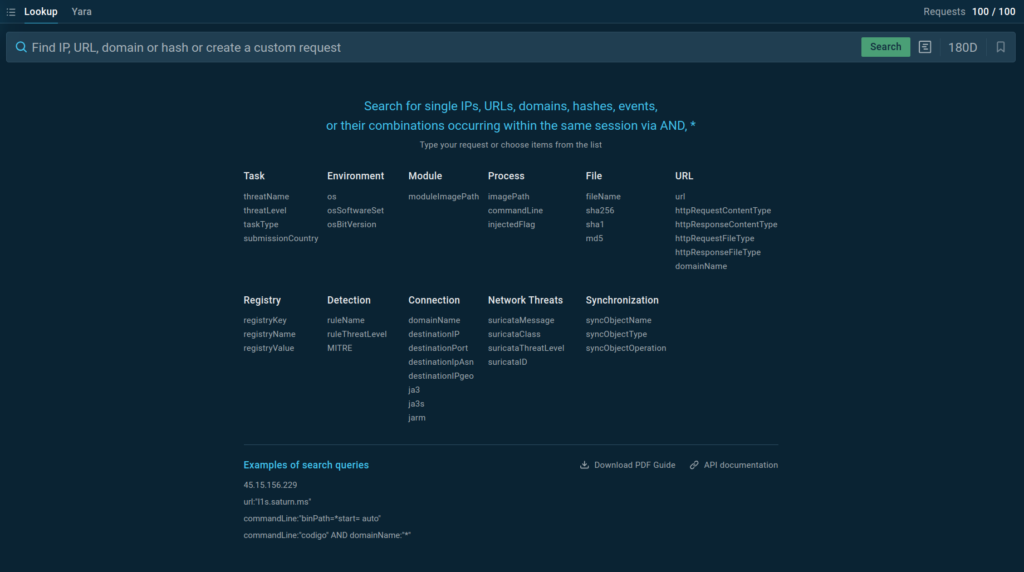
The service is powered by a global community of 400,000 security experts who submit thousands of samples to the ANY.RUN sandbox for analysis every day.
Through this process, large volumes of indicators of compromise (IOCs) and other threat data are extracted and sent to Threat Intelligence Lookup, making it accessible to users for searching and gathering fresh info on malware and phishing threats.
TI Lookup allows users to:
- Search through 2TB of the latest malware and phishing threat data
- Refine your searches using over 40 different search parameters and combinations, including wildcards
- Get quick results, each with a corresponding sandbox session
- Use YARA Search with a built-in rule editor
- Integrate with your security systems using API
Examples of Emerging Threats and How to Investigate Them with TI Lookup
1. New Phishing Threats
Attackers are constantly finding new ways to make their phishing attempts convincing.
By abusing legitimate services, mimicking popular websites, and crafting believable lures, criminals attempt to trick users into engaging in the target activity like revealing their credentials or installing malware on their systems.
Example: Abuse of SES Accounts by Tycoon 2FA Phish-kit
Recently, ANY.RUN researchers spotted a phishing campaign exploiting compromised Amazon Simple Email Service (SES) accounts to distribute phishing emails.
The attack chain began with an email from Amazon SES, which then redirected the victim through various domains, including social networks and news outlets like India Times, to the final page requesting their credentials.
Using a TI Lookup query featuring a string used in phishing URLs combined with the abused domain, we can find more samples and relevant threat data on the campaign:
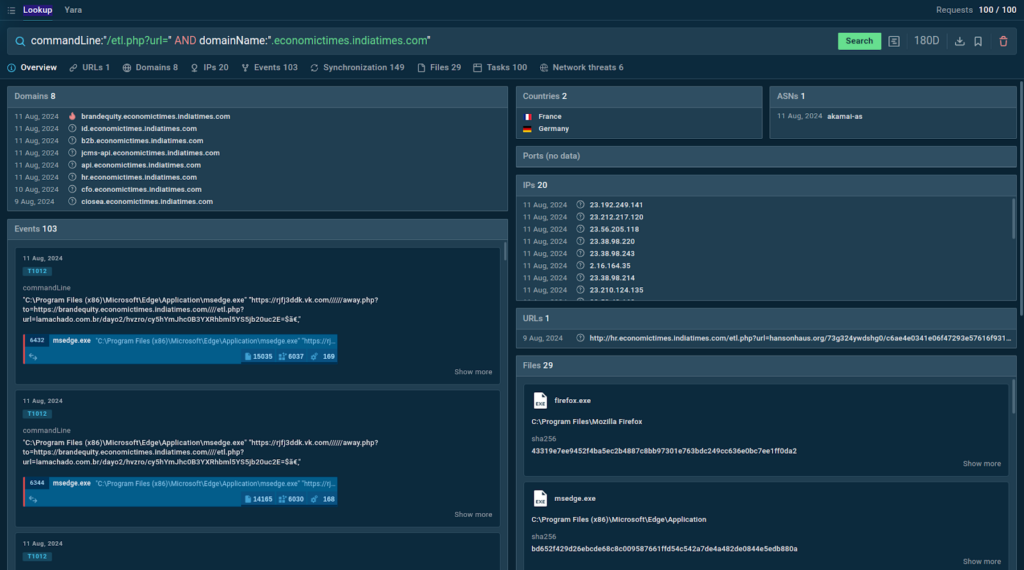
Threat Intelligence Lookup returns 8 domains, 20 IPs, 29 files, and other details found across a hundred viewable sandbox sessions that match our search query.
2. New and Evolving Malware Families
New strains of malware appear daily with some of them going on to become serious security challenges on the global stage. These can include ransomware, trojans, and other types of malicious software.
Often, they use advanced methods to avoid detection and attack systems, such as running only in memory or using legitimate tools to blend in with normal activities.
Example: DeerStealer Malware
DeerStealer is a new malware family discovered by ANY.RUN in July 2024. This malicious program was distributed as part of a phishing campaign mimicking Google Authenticator website.
With Threat Intelligence Lookup, we can quickly gather information on the latest samples of this malware, by using YARA Search. This tool lets us use custom YARA rules to find samples that match their contents.
Let’s borrow a rule for DeerStealer from ANY.RUN’s public collection of YARA rules.
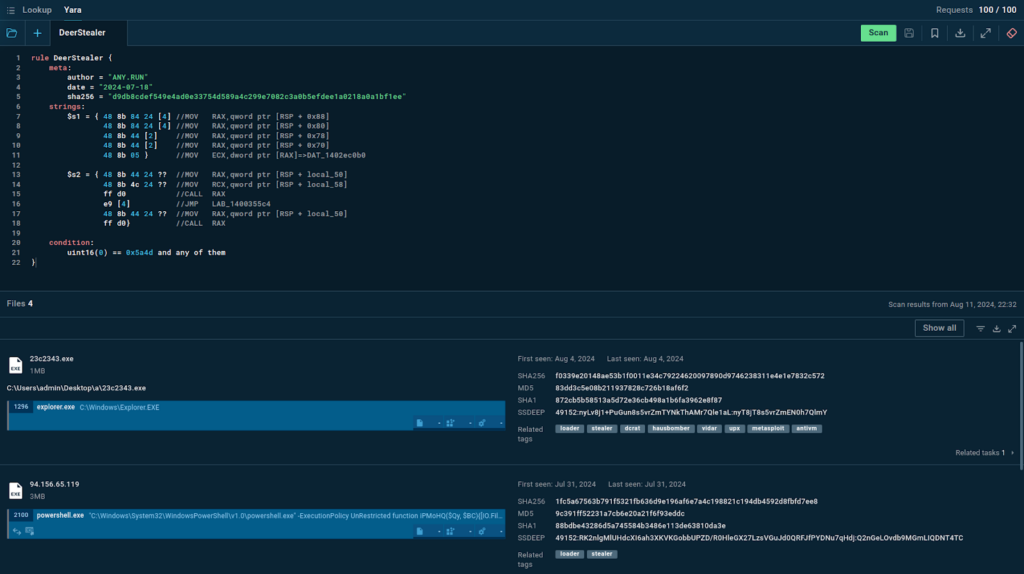
In response to our query, the service provides four samples with their corresponding sandbox sessions, allowing us to take a closer look at how the threat operates and collect valuable intelligence.
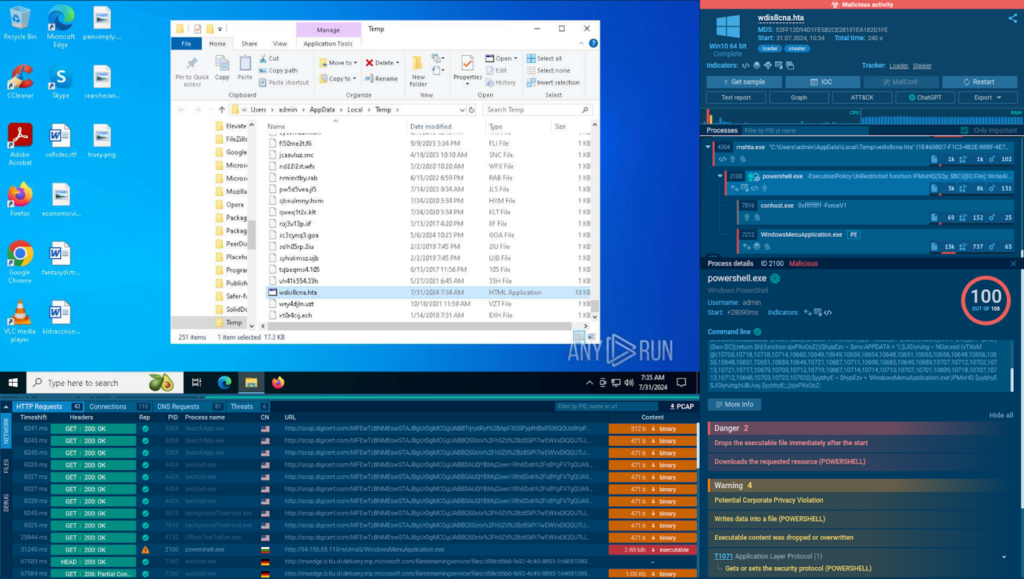
We can easily navigate to each of the samples to view a detailed sandbox report on their execution and even rerun the analysis sessions using our custom VM setup.
3. TTPs (Tactics, Techniques, and Procedures)
TTPs, or Tactics, Techniques, and Procedures, are the methods used by attackers to carry out their operations. Evolving malware families often introduce new ways to exploit vulnerabilities, avoid detection, and steal data with each new version. These tactics can be strong indicators of the latest malware samples.
The MITRE ATT&CK matrix is a detailed framework for understanding different TTPs. Each type of behavior is categorized and given its own identifier. For example, “T1059.003” refers to the abuse of the Windows Command Shell.
Example: Samples of New HijackLoader Version
Let’s consider HijackLoader, which received an update earlier in 2024.
One of the core features of the new version is User Account Control (UAC) bypass (TT1548.002) that lets the malware execute on the computer by slipping past Windows security controls.
To find samples of the new HijackLoader version, we can use the following query in TI Lookup:
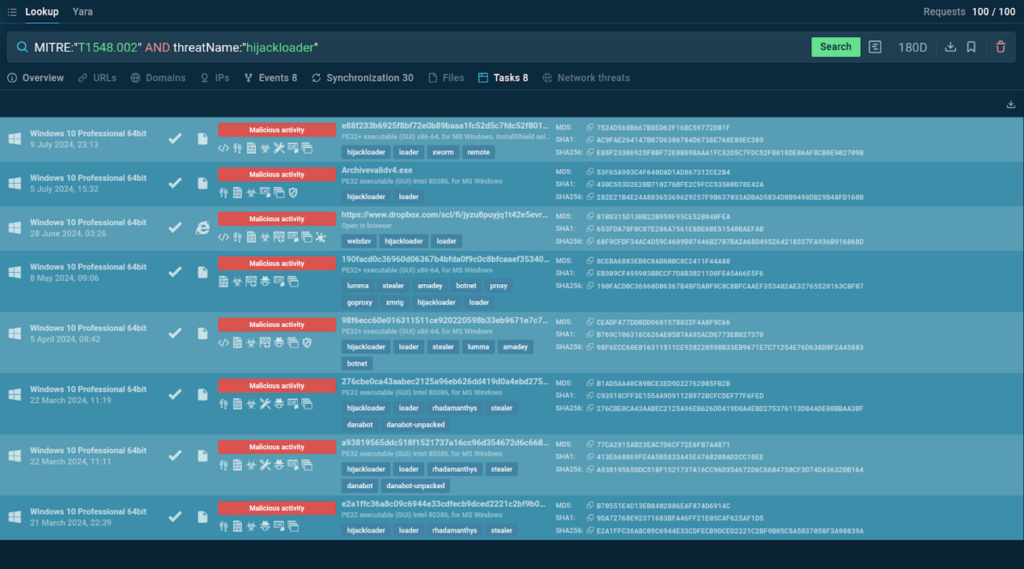
The service returns 8 sandbox sessions with the analysis of the newest variants of HijackLoader.
4. Exploitation of World Events
World events, such as natural disasters, political crises, or global health emergencies, can be exploited by attackers to launch cyber threats.
During the COVID-19 pandemic, there was a surge in phishing emails and malicious websites claiming to offer information or assistance related to the virus.
Attackers take advantage of the heightened interest and concern surrounding these events to trick users into clicking on malicious links or downloading malware.
Example: CrowdStrike Incident
One of the recent events used by threat actors to spread malware and phishing was the CrowdStrike outage.
After the cybersecurity company pushed a bad update, millions of PCs around the world received a blue screen of death. This sent attackers on a race to exploit the confusion, launching a wave of phishing emails and malicious websites offering fake recovery guides.
ANY.RUN analysts were among the first to uncover the threats abusing this event and TI Lookup played a significant role in this investigation.
Here is one of the search queries used by our team to find domains mimicking the official CrowdStrike domain that emerged right after the incident:
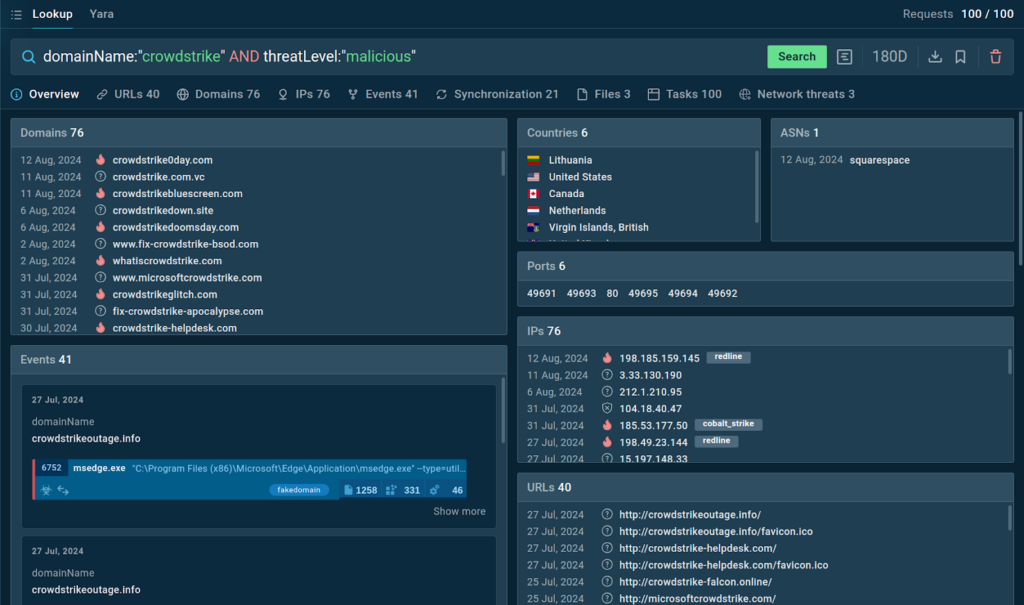
TI Lookup provides 76 domains fitting our description along with IPs, events, and sandbox sessions.
More Ways to Investigate Threats with TI Lookup
Investigating threats requires a systematic and proactive approach.
Here are more ways to effectively conduct investigations with TI Lookup using different types of indicators and artifacts.
1. Check Suspicious Connections
As a security professional, you may receive dozens of security alerts daily. TI Lookup helps you quickly determine if a certain artifact is an actual threat.
Here’s an example query showing how you can check a suspicious destination IP:
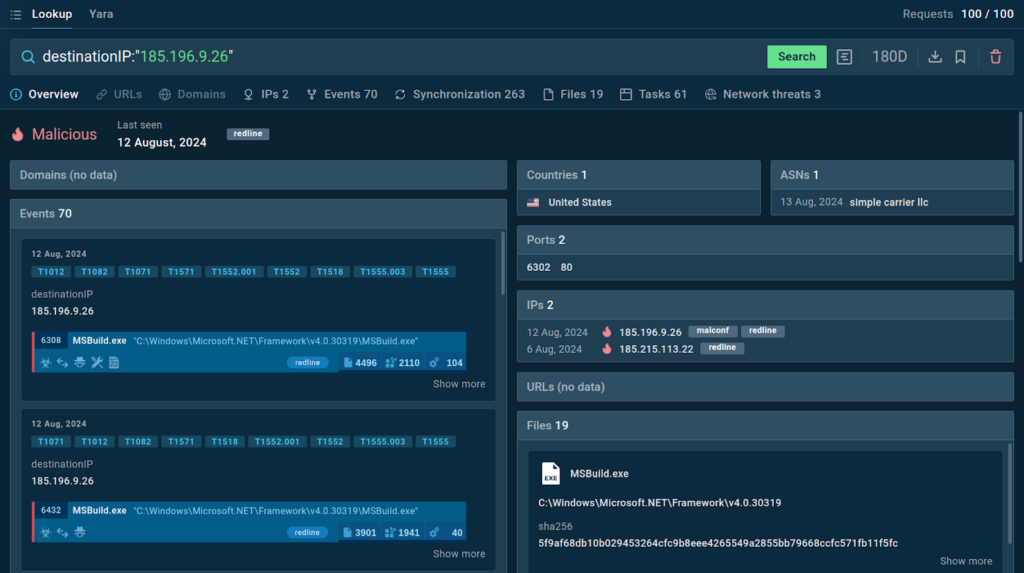
The service instantly shares wider context on the threat and gives a conclusive verdict on the IP.
2. Enrich Intelligence on Malware’s C2 Infrastructure
Command and Control (C2) infrastructure refers to the servers and communication channels used by attackers to control compromised systems. Attackers regularly update their C2 infrastructure but using TI Lookup you can stay up to date on any changes.
Investigating C2 infrastructure can help identify the source of attacks and the methods used to communicate with infected systems.
Here is a query for finding domains used by the Lumma stealer:
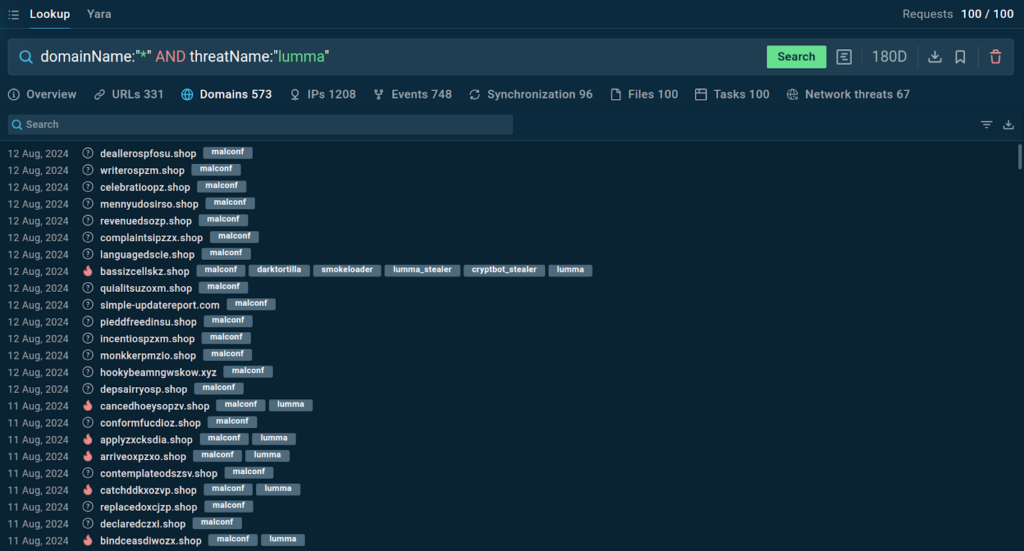
TI Lookup provides a list of domains found in sandbox sessions featuring Lumma. At the top, we can see domains tagged “malconf”, which means that they were extracted directly from the malware’s configuration.
3. Discover Malicious Network Activity Detected by Suricata IDS
Suricata is an open-source Intrusion Detection System (IDS) that can detect suspicious network activity. Investigating network activity detected by Suricata can help identify emerging threats and understand their behavior.
TI Lookup lets us search its database using Suricata rule details like Message, Class, Threat Level, and ID.
Here’s an example of a query featuring a message of Suricata rule that detects potential phishing threats:
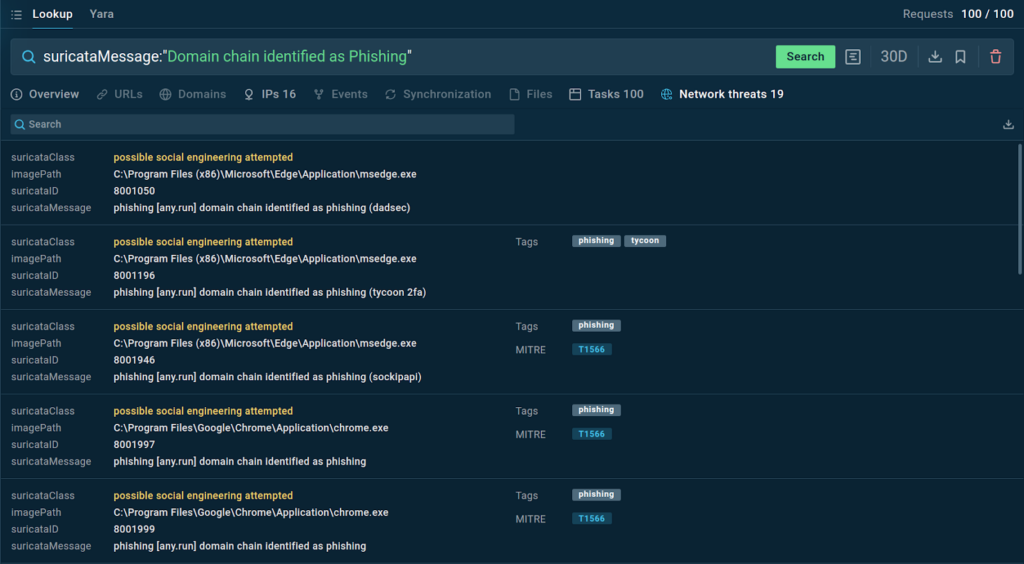
The service gives us a list of matching network threats that we can study further in the sandbox.
Learn more about Suricata search
4. Learn about the Current Threat Landscape
TI Lookup also lets us explore the overall threat landscape specific to a certain country. based on the samples uploaded to the ANY.RUN sandbox by the local users.
Here is a query for finding malicious submissions from Spanish users:
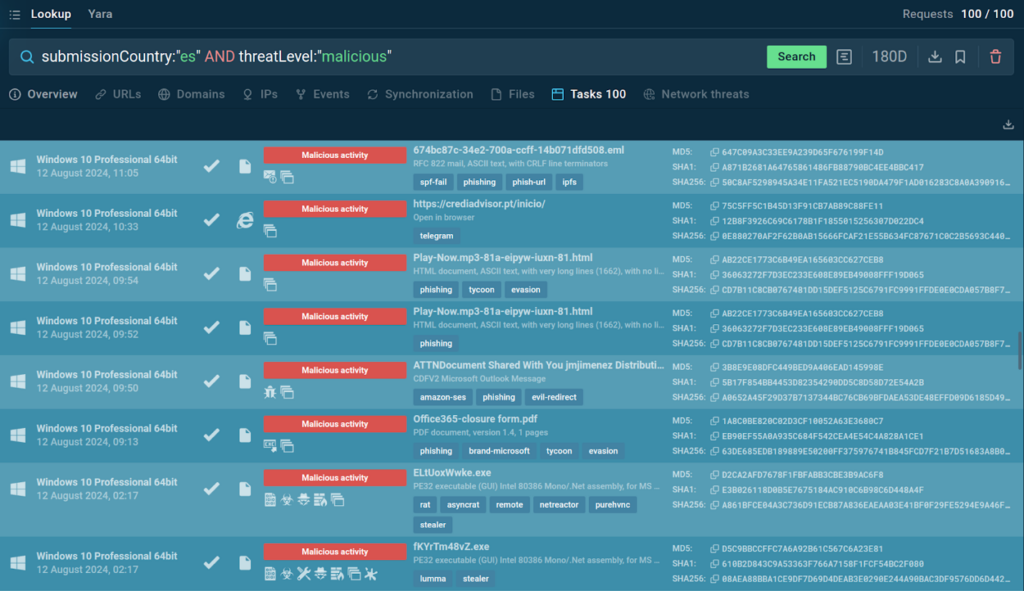
The results can help you get a better understanding of the threats currently active in your location.
Conclusion
Effective investigation of emerging threats relies on comprehensive threat intelligence. TI Lookup provides a wealth of data on C2 infrastructure, network activity, processes, registry changes, and wider threat context. By analyzing these indicators, organizations can better understand and mitigate emerging threats, ensuring the safety and integrity of their systems.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
