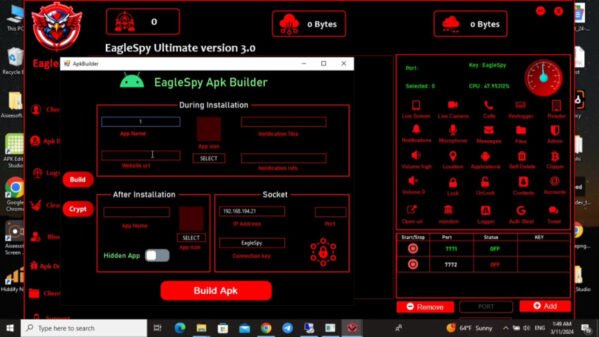
On March 21st, SOCRadar identified in the Dark Web(in a hacker forum under their surveillance) the distribution of a recently updated malicious software named EagleSpy v3.0 Android RAT (Remote Access Trojan).
This tool represents a major cybersecurity threat as it allows for unauthorized remote access and control over infected Android devices.
EagleSpy v3.0 Trojan Features
Ever since more and more people started using their mobile devices to purchase goods or access financial info, it was a matter of time before a comprehensive malicious software like EagleSpy arrived at our ‘doorstep’.
This trojan with its wide array of features, can be compared to a Swiss Army knife in the context of cyber threats.
Crypto Injections
The feature targets popular cryptocurrency wallets and exchanges, including Trustwallet, Metamask, Coinbase, Kraken and others. Typically, RATs like EagleSpy are capable of keylogging, screen capturing, and accessing files stored on the infected device. For example, if a user enters a private key, or if the private key is stored in a readable format on the device, the malware could potentially capture this information.
Show Scam Page
Continuously monitors the victim’s device activities, with a focus on web browsing habits. Upon detecting an attempt to navigate to a financial website, the malware then intervenes, redirecting the user to a counterfeit web page, mimicking legitimate banking or financial services. These pages are designed to deceive the user into entering personal, acting like a tipical web phising method. The entered information is then transmitted to the attackers.
Injection
Injection is a capability that ensures the scam pages are a recurring event. Every time the user attempts to access their cryptocurrency wallet for example, the fake page is shown again. And again, increasing its chances of capturing critical data.
PIN & Pattern Lock Grabs
EagleSpy 3.0’s code contains various techniques used to record the device’s PINs, passwords, or unlocking patterns. Again, like a keylogger.
Real-time Data Transmission
Captured data is sent to a specified Telegram bot controlled by the attackers. This is really bad, because attackers can take advantage immediately upon receiving the stolen data.
Screen Manipulation
With each mentioned feature I feel like I need to take a pause, to reset passwords, scan my devices and uninstall unused apps. The malware can alter the device’s display and show custom messages or even a blank screen, effectively locking the user out or distracting them. This is truly effective and the shivers on my spine are still going strong.
Custom Injection & Ransomware
Attackers are provided with the capability to customize add their own scripts to the malware. Or even implement custom ransomware.
Permission Manager
Ensures that the malware retains its full capabilities without prompting user alerts for permission requests that could lead to its detection. Horrifying!
Google 2FA Stealer
Saving the worst for last. This feature is referring to stealing Google’s two-factor authentication codes. By obtaining these codes, the attackers can bypass even well-protected accounts.
How is this Trojan Spreading?
The activation of malware like EagleSpy typically involves a few common methods that trick or compel the user into installing the Trojan on their device. While specific details about EagleSpy’s activation mechanisms aren’t provided in the sources, here are some common practices observed with Android RATs and Trojans:
Firstly is the phishing attack. Users might receive emails, SMS, or messages in apps that contain links or attachments. These are designed to look legitimate but contain the malicious attachments. This attachment can be hidden as a polyglot. We discussed about those in the StrelaStealer article. Once it’s executed, the malware is up and running on the device.
Another way of spreading EagleSpy is through malicious apps. These apps could be made available on third-party app stores or even, in some cases with free VPN apps, slip through checks and appear in Google Play Store.
How to Protect Against It
Regular scans
Make use of built-in tools like Google Play Protect and, if available, device-specific security features like Samsung’s Device protection to scan for and remove malware. Also consider third-party antivirus apps for additional protection, Bitdefender is still king!
Avoid installing apps from unknown sources
Be cautious with apps from outside the Google Play Store. Android has security settings that block installations from unknown sources by default. If you need to install an app from outside the Play Store, ensure it’s from a trusted source and remember to re-enable the protection afterwards.
Apply good security habits
Develop safe habits such as avoiding suspicious websites, links, and attachments, especially from unsolicited emails or messages. Use strong, unique passwords and consider a password manager to keep them secure.
Stay safe!