
2024-9-2 23:19:22 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
This article provides a comprehensive overview of SOC2 compliance for technology startups, particularly those with fewer than 10 employees. It aims to demystify the SOC2 certification process, highlight its benefits, and offer cost-effective strategies for achieving compliance.
The article emphasizes practical, actionable steps that startups can take to prepare for and implement SOC2 policies without significant financial burden.
What is SOC2?
SOC2 (Service Organization Control 2) is a auditing procedure developed by the American Institute of CPAs (AICPA) to ensure that service providers securely manage data to protect the interests of their organization and the privacy of their clients.
SOC2 defines criteria for managing customer data based on five "trust service principles"—security, availability, processing integrity, confidentiality, and privacy.
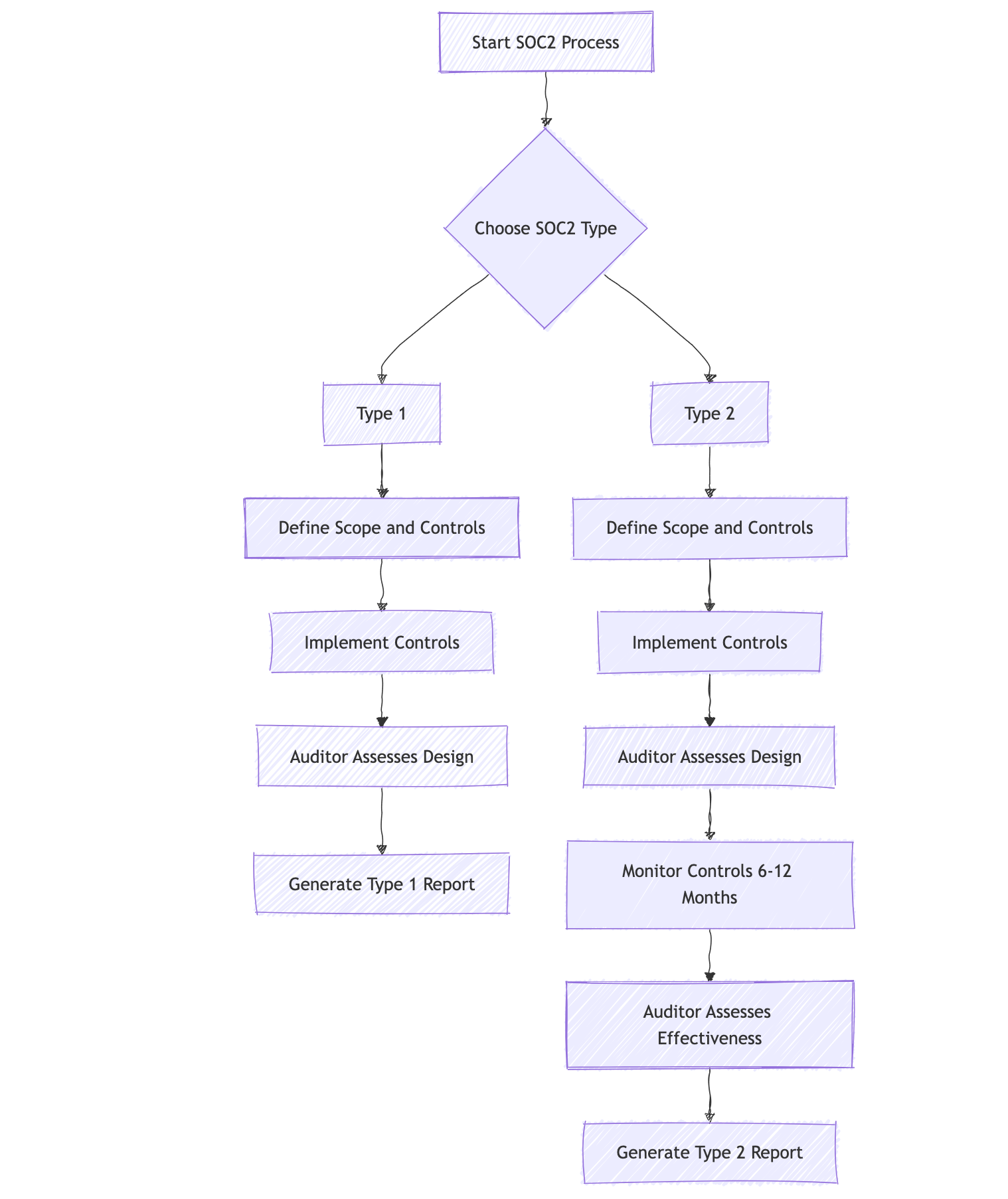
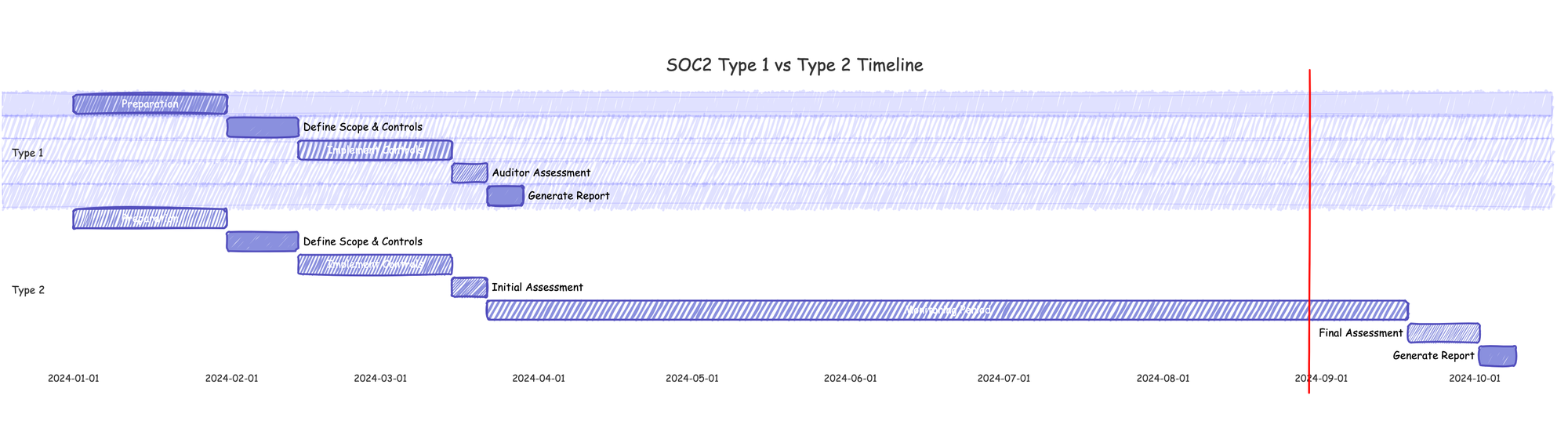
SOC2 Type 1 vs Type 2
Understanding the difference between SOC2 Type 1 and Type 2 reports is crucial for organizations pursuing SOC2 compliance. Both types of reports assess an organization's internal controls, but they differ in scope and duration of examination.
SOC2 Type 1:
- Assesses the design of controls at a specific point in time
- Provides a snapshot of the organization's security posture
- Typically faster and less expensive to obtain
- Useful for organizations just starting their compliance journey
SOC2 Type 2:
- Assesses both the design and operating effectiveness of controls over a period of time (usually 6-12 months)
- Provides a more comprehensive view of the organization's security practices
- More rigorous and time-consuming
- Generally considered more valuable by clients and partners
Key Benefits of SOC2 Compliance
- Enhanced Security Posture: Implementing SOC2 controls strengthens overall security practices.
- Competitive Advantage: Compliance can be a differentiator in the market.
- Customer Trust: SOC2 certification builds credibility with clients and partners.
- Risk Management: The process helps identify and mitigate potential security risks.
- Operational Efficiency: Standardized processes often lead to improved operations.
- Regulatory Alignment: SOC2 can help meet requirements for other regulations (e.g., GDPR, HIPAA).
How it works for SaaS companies
For SaaS companies, SOC2 compliance demonstrates a commitment to data security and privacy. It involves:
- Selecting the relevant trust service principles
- Implementing controls and processes to meet these principles
- Undergoing an audit by a certified public accountant
- Receiving a SOC2 report detailing the effectiveness of these controls
Step-by-step Approach
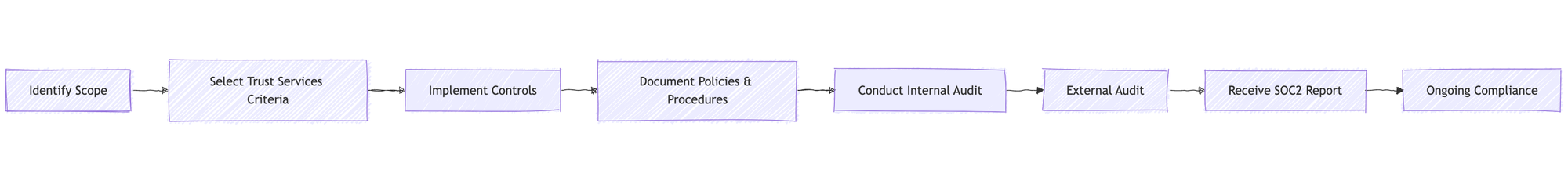
- Identify Scope: Determine which systems, data, and processes will be covered by the SOC2 audit.
- Select Trust Services Criteria: Choose which of the five trust principles (Security, Availability, Processing Integrity, Confidentiality, and Privacy) are relevant to your business.
- Implement Controls: Put in place the necessary technical and organizational measures to meet the selected criteria.
- Document Policies & Procedures: Create and maintain documentation of all relevant security policies and procedures.
- Conduct Internal Audit: Perform a self-assessment to ensure readiness for the external audit.
- External Audit: An independent auditor evaluates your systems and controls against the SOC2 criteria.
- Receive SOC2 Report: Upon successful completion of the audit, receive the official SOC2 report.
- Ongoing Compliance: Continuously monitor and maintain compliance with SOC2 standards.
SOC2 Compliance for Startups
Challenges and Opportunities
Startups face unique challenges in achieving SOC2 compliance:
- Limited resources (both financial and personnel)
- Lack of dedicated security staff
- Rapidly changing business environment
However, they also have opportunities:
- Ability to build security into the core of operations from the start
- Flexibility to implement new processes quickly
- Potential for faster decision-making and implementation
Required vs. Optional Policies
SOC2 is based on the Trust Services Criteria (TSC), which include:
- Security (required)
- Availability (optional)
- Processing Integrity (optional)
- Confidentiality (optional)
- Privacy (optional)
| Principle | Required/Optional | Description |
|---|---|---|
| Security | Required | Protection against unauthorized access |
| Availability | Optional | System availability for operation and use |
| Processing Integrity | Optional | System processing is complete, accurate, timely, and authorized |
| Confidentiality | Optional | Information designated as confidential is protected |
| Privacy | Optional | Personal information is collected, used, retained, and disclosed in conformity with commitments |
For startups, focusing on the required Security principle and selectively adding others based on business needs is often the most practical approach.
Cost-Effective SOC2 Compliance Strategies
Policy Implementation
- Start with a Gap Analysis: Identify what controls you already have in place and what needs to be implemented.
- Prioritize Critical Policies: Focus on essential security policies first.
- Leverage Existing Frameworks: Use established frameworks like NIST or ISO 27001 as a starting point.
- Document as You Go: Integrate documentation into your daily processes to avoid last-minute rushes.
- Automate Where Possible: Use tools to automate policy enforcement and evidence collection.
Free and Open Source Tools
| Category | Tool | Description |
|---|---|---|
| Vulnerability Scanning | OpenVAS | Comprehensive vulnerability scanner |
| Intrusion Detection | Snort | Network intrusion detection system |
| Log Management | ELK Stack (Elasticsearch, Logstash, Kibana) | Log collection, analysis, and visualization |
| Access Control | OpenLDAP | Open-source implementation of LDAP protocol |
| Encryption | VeraCrypt | Disk encryption software |
| Password Management | KeePass | Free, open-source password manager |
| Network Monitoring | Nagios | Network and infrastructure monitoring |
Policy Preparation and Implementation Guide
- Information Security Policy
- Template: NIST Special Publication 800-53
- Implementation: Use NIST guidelines to create a comprehensive security policy. Ensure all employees read and acknowledge the policy.
- Access Control Policy
- Template: CIS Controls v8
- Implementation: Use OpenLDAP for centralized user management. Implement multi-factor authentication using free tools like Google Authenticator.
- Change Management Policy
- Template: ITIL Change Management
- Implementation: Use a free project management tool like Trello or Jira to track and approve changes.
- Incident Response Plan
- Template: SANS Institute Incident Handler's Handbook
- Implementation: Conduct regular tabletop exercises to test the plan. Use a free tool like TheHive for incident response management.
- Risk Assessment Process
- Template: ISO 31000 Risk Management
- Implementation: Conduct annual risk assessments. Use a free tool like SimpleRisk for ongoing risk management.
- Vendor Management Policy
- Template: NIST SP 800-161 Supply Chain Risk Management Practices
- Implementation: Maintain a (google) spreadsheet of vendors with their compliance status. Conduct annual reviews.
- Data Classification Policy
- Template: NIST SP 800-60 Guide for Mapping Types of Information and Information Systems to Security Categories
- Implementation: Use metadata tagging in your document management system to classify data.
- Business Continuity and Disaster Recovery Plan
- Template: Ready.gov Business Continuity Planning Suite
- Implementation: Use cloud backup services for critical data. Conduct annual disaster recovery tests.
Conclusion
Achieving SOC2 compliance is a significant undertaking, but it's not out of reach for small technology startups. By focusing on the essential security principle, leveraging free and open-source tools, and implementing cost-effective strategies, startups can build a robust security posture that meets SOC2 requirements.
Remember, SOC2 compliance is an ongoing process, not a one-time achievement. Regular reviews and updates of your policies and procedures are crucial to maintaining compliance and ensuring the security of your systems and data.
By following the guidelines and using the resources provided in this report, small startups can embark on their SOC2 compliance journey with confidence, enhancing their security posture and building trust with their clients and partners.
*** This is a Security Bloggers Network syndicated blog from Meet the Tech Entrepreneur, Cybersecurity Author, and Researcher authored by Deepak Gupta - Tech Entrepreneur, Cybersecurity Author. Read the original post at: https://guptadeepak.com/demystifying-soc-2-compliance-for-startups-a-simple-guide/
如有侵权请联系:admin#unsafe.sh
