
2024-9-3 13:30:59 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
WordPress is the most widely used content management system globally, with over 478 million of all websites are built on its platform, according to its developers. However, this widespread popularity also makes WordPress a prime target for malicious actors. Because of this, cybersecurity researchers closely examine WordPress and frequently identify and report various security issues within the content management system (CMS).
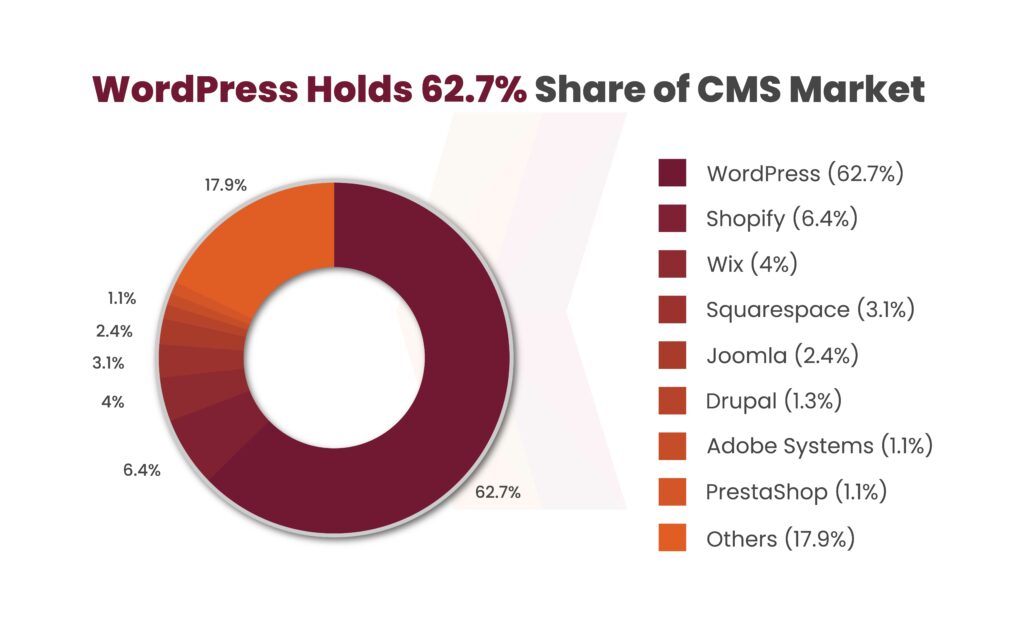
Shopify and Wix, WordPress’s closest competitors, lag far behind with market shares of 6.4% and 4%, respectively, emphasizing WordPress’s dominant position. Additionally, it’s noteworthy that 30.6% of websites operate without a recognized CMS, reflecting diverse web development methods.
However, among sites that do use a CMS, WordPress’s dominance is unmistakable. Its continuous innovation and adaptability to the changing demands of the web have firmly established its leading position in the CMS market.
Consequently, WordPress is often perceived as having numerous security issues. This increased scrutiny is beneficial: it means that most vulnerabilities and their solutions are well understood, simplifying the process of securing your WordPress site. In this blog, we will discuss about WPML flaw and also we will explore the methods of keeping your WordPress site safe.
Brief of WPML Plugin Vulnerability (CVE-2024-6386)
A critical vulnerability (CVE-2024-6386) was discovered in the WPML WordPress multilingual plugin, affecting versions below 4.6.13. This flaw, which scored a 9.9 on the CVSS scale, allows authenticated users with Contributor-level access or higher to execute arbitrary code remotely via server-side template injection (SSTI). The vulnerability arises from improper input validation within the plugin’s use of Twig templates for rendering shortcodes. With over one million installations, this flaw is critical, so admins must update to the latest version immediately to avoid exploitation. The WPML team has since released a patch (version 4.6.13) to address the issue, urging all users to apply the update without delay to secure their websites.
In simpler terms, attackers can inject malicious code into what appears to be harmless content, such as a shortcode. When the plugin processes this code, it executes on the server, giving the attacker unauthorized access and control. This could enable them to steal sensitive data, install malware, redirect website traffic, or even deface the website entirely.
Impact of the Vulnerability
The vulnerability is related to the plugin’s handling of shortcodes, which are used to embed content such as media files in posts. WPML relies on Twig templates to render these shortcodes, but it fails to properly sanitize user input, allowing authenticated users to exploit this through server-side template injection (SSTI). This flaw, caused by inadequate input sanitization and template vulnerabilities, provides a pathway for code execution on affected servers.
Response Plan for the Vulnerability
Below is the response plan for the vulnerability:
Identify the Affected Versions
Confirm that your website is running a version of the WPML WordPress multilingual plugin below 4.6.13. These versions are vulnerable to the CVE-2024-6386 flaw.
Update the Plugin
Immediately update the WPML plugin to the latest version (4.6.13 or higher). This version includes patches that address the vulnerability by improving input validation and sanitization, thereby mitigating the risk of server-side template injection (SSTI).
Restrict Access
Limit the number of users with Contributor-level access or higher until the update is applied. Since the vulnerability requires authenticated access at this level to be exploited, reducing the number of users with these privileges lowers the risk of an attack.
Implement Security Monitoring
Deploy or enhance monitoring tools to detect any suspicious activities or unauthorized access attempts. Focus on monitoring the use of shortcodes and template rendering processes, as these are the key areas of exploitation for this vulnerability.
Apply Web Application Firewall (WAF) Rules
Configure your web application firewall (WAF) to block or detect attempts to exploit this vulnerability. This can provide an additional layer of protection by filtering out potentially malicious requests.
How to Patch the Vulnerability?
The WPML team quickly addressed the disclosed vulnerability by releasing a patched version (WPML 4.6.13) on August 20, 2024. It is essential for all WordPress website owners using the WPML plugin to update to this latest version without delay. Failing to apply the patch promptly could leave websites exposed to potential exploitation.
To update the WPML plugin, follow these steps:
- Log in to your WordPress dashboard.
- Go to Plugins > Installed Plugins.
- Find the WPML plugin and click “Update” if a newer version is available.
- After the update is finished, click “Activate” to ensure the latest patched version is in use.
Methods to Keep Your WordPress Site Safe
Below are the steps to keep the WordPress site safe:
- To enhance WordPress security, regularly update core, themes, and plugins, and promptly remove unnecessary ones.
- Enhance WordPress security by enforcing strong password policies, limiting login attempts, enabling two-factor authentication, and recommending the use of a password manager.
- Enhance WordPress security by applying least privilege, reviewing and removing unnecessary accounts, and enforcing strong passwords and two-factor authentication.
- To boost WordPress security, use only essential plugins, review them before installation, remove unused ones, use malware scanners carefully, and consult professionals if malware is suspected.
- To enhance security, disable XML-RPC on your WordPress site if you don’t plan to use it soon; it can easily be re-enabled if needed. If you require XML-RPC, configure restrictions using WordPress plugins.
Book a Free Consultation with our Cyber Security Experts

Conclusion
The WPML vulnerability, CVE-2024-6386, underscores the ongoing importance of maintaining up-to-date WordPress sites and plugins. By promptly updating to the latest version of WPML, website owners can effectively mitigate the risk of exploitation and protect their sites from potential damage. Beyond this specific vulnerability, it’s essential to adopt a comprehensive security approach, including regular updates, strong passwords, two-factor authentication, and careful plugin management. WordPress website owners can safeguard their digital assets by prioritizing cybersecurity and ensuring a secure online presence.
FAQs
- How vulnerable are WordPress sites?
Your WordPress website is vulnerable to threats like bots, brute-force attacks, and backdoor intrusions. These security risks can negatively affect every aspect of your site.
- What is the biggest risk in WordPress site security?
Outdated plugins and themes are among the most frequent security vulnerabilities in WordPress. Cyber attackers often exploit these known weaknesses in outdated software to infiltrate websites.
Ref Link: https://thehackernews.com/2024/08/critical-wpml-plugin-flaw-exposes.html
The post WordPress Sites at Risk from WPML Flaw appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/wordpress-sites-at-risk-from-wpml-flaw/cyber-security/
如有侵权请联系:admin#unsafe.sh
