2024-9-4 04:2:21 Author: lab.wallarm.com(查看原文) 阅读量:4 收藏
Managing an organization’s attack surface is a complex problem involving asset discovery, vulnerability analysis, and continuous monitoring. There are multiple well-defined solutions to secure the attack surface, such as extended detection and response (EDR or XDR), security information & event management (SIEM), and security orchestration, automation & response (SOAR); despite that, these tools often do not prioritize APIs. At the same time, today APIs are indispensable for integrating various software systems; however, this integration broadens the attack surface, making APIs primary targets for cybercriminals.
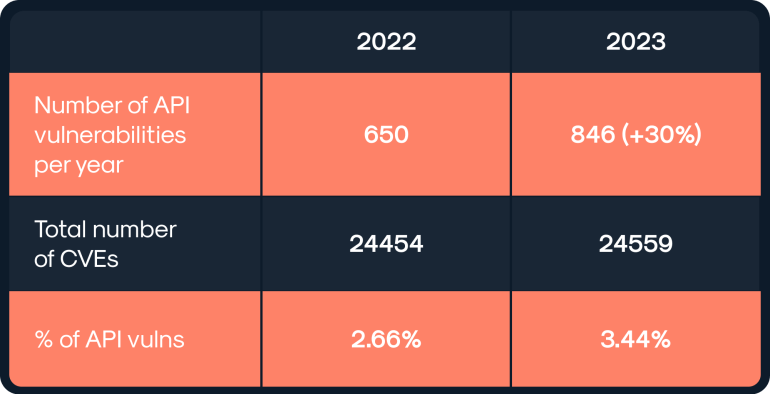
30% Increase in API vulnerabilities among CVEs in 2023
According to the Wallarm API ThreatStats™ Reports from 2022 to 2023, API vulnerabilities experienced a substantial 30% increase, rising from 650 to 846 instances. This growth reflects the expanding landscape of API security challenges, even as the total number of Common Vulnerabilities and Exposures (CVEs) saw a marginal rise from 24,454 to 24,559. More significantly, the share of API vulnerabilities within the entire CVE spectrum surged from 2.66% to 3.44%. This notable increase underscores the expanding focus on API security, highlighting it as a crucial and growing concern within the cybersecurity field. In other words, each 29th CVE was API-related in 2023, to compare with each 37th CVE in 2022.

Market Observations
API discovery involves cataloging all internal and third-party APIs within an organization. This process helps developers find existing APIs to avoid redundant work and integrate them into new applications. It also helps security teams to build secured infrastructure and services. However, after dozens of interviews with security professionals, the majority said that they don’t have a clear picture of the number of APIs used in the organization and they are not sure if they have up-to-date documentation. The challenge occurs as it is often a semi-manual process and involves proper security processes that even large organizations don’t always properly follow. Keeping track of APIs is challenging as projects scale with new endpoints, parameters, and functionalities being added. This growth can make it difficult to keep the API documentation up-to-date. At the same time, modern enterprises have about 100+ APIs on average which are great targets for security breaches. For example, just API Leaks themselves have become a new Top-5 threat with the recent examples of leaked API keys from MailChimp, Mailgun, and SendGrid, put 54 million users at risk.

API Discovery options you might have
- Understand API Specifications
- Examine API Documentation: Conduct a detailed review of the API documentation, understanding all aspects of its functionality and potential use cases. Pay particular attention to the security practices outlined in the documentation. Identify how authentication, authorization, data encryption, and other security measures are implemented.
- Authentication: Ensure the API uses robust authentication methods, such as OAuth, API keys, or JWT (JSON Web Tokens). Verify that these methods are well-documented and properly implemented.
- Community and Support: Engage with developer communities, forums, or official support channels to gather additional insights and clarifications on undocumented or poorly documented aspects of the API.
- Code Reviews: If available, review the source code of the API or its client libraries. This can provide deeper insights into how security mechanisms are implemented and identify any discrepancies between the documentation and actual implementation.
- Test the API: Conduct hands-on testing by interacting with the API endpoints. This helps in identifying undocumented behaviors, and potential security flaws, and understanding the practical implementation of security measures.
- Conduct API Audits
- API auditing systematically reviews and analyzes APIs to ensure they are secure, efficient, and compliant with relevant standards and policies. This process involves a thorough examination of the API’s design, implementation, and documentation. Regular audits can uncover performance issues, inefficiencies in API designs, and potential security vulnerabilities.
- Tools like Burp Suite and OWASP ZAP play a crucial role in ensuring APIs are secure and compliant. These tools help identify vulnerabilities, such as injection flaws, broken authentication, and exposure of sensitive data. They also assist in verifying that APIs adhere to security best practices and relevant compliance standards, such as GDPR, HIPAA, and PCI-DSS.
- In addition to security, API auditing focuses on performance optimization. It evaluates response times, error rates, and resource utilization to ensure the API operates efficiently under various conditions. This helps in identifying bottlenecks and areas for improvement, leading to better user experiences and more robust API performance.
- Implement API Gateways
- API gateways are the entry point for managing and securing API traffic. They provide essential functions like authentication, rate limiting, request/response transformation, and collecting analytics. You can manage and secure API traffic with gateways like Kong, Amazon API Gateway, or MuleSoft.
- In addition to these core functions, API gateways also offer several other important features. One such feature is load balancing, which distributes incoming requests across multiple servers to ensure optimal performance and availability. This helps in preventing any single server from becoming a bottleneck or point of failure.
- Another significant feature of API gateways is caching, which stores frequently accessed data temporarily to reduce the load on backend services and improve response times. By caching responses, the gateway can quickly serve repeated requests without having to forward them to the backend each time.
- API gateways also provide capabilities for logging and monitoring, enabling detailed tracking of API usage and performance metrics. This information is crucial for identifying issues, optimizing performance, and ensuring compliance with service-level agreements.
- Furthermore, API gateways support the implementation of security policies such as IP whitelisting, blacklisting, and enforcing HTTPS connections. They can also integrate with identity providers to facilitate OAuth2 and other token-based authentication mechanisms, adding an extra layer of security to the API ecosystem.
- Additionally, many API gateways offer plugins or extensions that allow customization and enhancement of their functionalities. These plugins can add new features, integrate with other systems, or automate specific tasks, providing flexibility to adapt the gateway to specific needs.
- Finally, API gateways often include developer portals that provide documentation, testing tools, and access key management for developers. This helps streamline the process of onboarding new developers and ensuring they have the necessary resources to effectively use the APIs.
- Explore API Marketplaces
- Platforms like Check Point API Reference and APIs.guru provide vetted APIs with community feedback.
- APIs.guru is a community-driven project that aims to create a comprehensive, up-to-date directory of public APIs. It provides a centralized repository of OpenAPI (formerly Swagger) specifications for various APIs, making it easier for developers to discover, compare, and integrate different APIs. APIs.guru helps standardize API specifications and provides tools for browsing, searching, and retrieving API documentation.
- Check Point API Reference provides detailed documentation for the APIs offered by Check Point Software Technologies, a company specializing in cybersecurity. These APIs allow developers to integrate Check Point’s security solutions with other software systems, automate security tasks, and manage Check Point products programmatically. The API reference typically includes information on available endpoints, request and response formats, authentication methods, and examples.
- API Development and Testing tools
- Swagger UI is a tool that automatically generates interactive API documentation from an OpenAPI (formerly Swagger) Specification. It allows developers to visualize and interact with the API’s resources without having to manually create documentation. The interactive interface lets users try out API endpoints, making it easier to understand and test API behavior.
- Apigee is a full-featured API management platform provided by Google Cloud. It offers tools for designing, securing, deploying, monitoring, and scaling APIs. Apigee provides capabilities like traffic management, API security (OAuth, JWT), analytics, and developer portal creation.
- Postman is a popular tool for developing, testing, and documenting APIs. It provides a user-friendly interface for creating and sending HTTP requests, organizing APIs into collections, and automating tests. Postman also offers collaboration features for team-based API development.
- Use API Discovery Tools such as AASM by Wallarm
- No installation, no configuration: API Attack Surface Management (AASM) is an agentless detection solution, so you won’t need to install or configure anything into your infrastructure.
- Designed for APIs: At the same time, it is tailored for the API ecosystem and designed to discover all external hosts with their Web Apps & APIs.
- All API Protocols: It specifies API protocols (REST API, GraphQL, SOAP, XML-RPC, and more)
- Secure: AASM is securing them by identifying if APIs are protected by WAFs and the types of attacks they can protect from. It also searches for API leaks in them such as API keys, authorization tokens, or users’ credentials, etc.
- You can learn more about AASM by Wallarm here.
Summary
By prioritizing these practices, organizations can better manage their API attack surface, enhancing their overall cybersecurity posture and protecting against potential threats. Regular monitoring, auditing, and utilizing advanced tools are key to maintaining a secure and efficient API environment.
To learn how you can quickly discover and protect your API attack surface, sign up for a free trial of AASM by Wallarm here.
如有侵权请联系:admin#unsafe.sh