
Over the past decade, Bitcoin’s value has increased more than 200-fold. Similarly, other cryptocurrencies have also seen significant growth, prompting many individuals to engage in mining for profit. This rise in cryptocurrency mining has led to a substantial increase in the use of cryptominers.
As organizations increasingly migrate their computing workloads to the cloud for various benefits, attackers have shifted their focus to these cloud resources for cryptocurrency mining. For instance, a 29-year-old Ukrainian was recently arrested for cloud mining over $2 million in cryptocurrency using an organization’s cloud resources.
The complexity of cloud infrastructure allows many cryptominers to infect them and remain undetected for extended periods, sometimes months or even years. Organizations often mistakenly believe that cloud service providers will handle the security of workloads running in the cloud. However, cloud service providers operate under a “shared responsibility model”, where the responsibilities of “security in the cloud” and “security of the cloud” are divided.
Hidden Costs: The Damage Caused by Cryptominers
Cloud miners are designed to maximize computational power usage to mine cryptocurrencies. Thus, substantially increasing CPU and GPU consumption and diverting resources from legitimate applications and services. However, attackers are now installing cryptominers with custom configurations that consume fewer resources. This approach allows them to blend in better and avoid raising suspicion. Consequently, enabling the cryptominers to survive longer in the environment.
As a result, organizations may face skyrocketing cloud bills as cryptominers exploit their computational resources. The unexpected surge in resource usage can strain budgets, especially in environments with auto-scaling capabilities, where additional instances are spun up to meet the demand created by cloud miners. However, using cryptominers with reduced resource consumption, attackers can prolong their presence, prolonging the financial impact on organizations.
From Dormancy to Attack: The Lifecycle of a Cryptominer
Cryptominers in cloud-native environments have a lifecycle that begins with a breach and proceeds to dormancy before starting the attack. Understanding the lifecycle is critical for recognizing and managing threats before they cause substantial damage.
Initial Breach Methods
1. Exploitation of unpatched vulnerabilities:
- Cryptominers often enter systems by exploiting unpatched vulnerabilities in software, containers, or orchestration platforms. Attackers scan for known security flaws and use automated tools to infiltrate the environment.
- Example: A vulnerability in a container runtime might allow attackers to escape the container and gain access to the host system, from which they can deploy cloud mining software. The MITRE ATT&CK framework technique T1496 documents these methods.
2. Use of stolen or weak credentials:
- Another common method is to use stolen credentials or weak passwords brute-force to gain unauthorized access to cloud accounts and services.
Example: Attackers may obtain credentials from previous data breaches or use phishing tactics to trick users into revealing their login details. Popular credential stealer malware such as Racoon and RedLine that exfiltrate stored credentials from the victim’s browsers and other sources.
Methods Used to Install Cryptominers in Kubernetes (K8s)
Cloud miners use sophisticated methods to install cryptominers in Kubernetes environments. They often exploit misconfigurations or vulnerabilities in the Kubernetes setup. For example:
- Exploiting Kubernetes API Server: Attackers may exploit exposed Kubernetes API servers that are accessible from the internet, gaining control over the cluster.
- Compromising Container Images: Malicious images with cryptominers pre-installed can be pulled from public repositories if proper image scanning and image signing are not enforced.
- Abusing Kubernetes Secrets: Cloud miners may gain access to sensitive data stored in Kubernetes secrets and use it to deploy cryptominers.
Obfuscation Techniques:
Attackers use various techniques to obfuscate their activities:
- Container Escape: By exploiting vulnerabilities, cloud miners escape from the container to the host system to deploy cryptominers.
- Resource Limits Avoidance: Attackers configure containers to avoid Kubernetes resource limits, ensuring their cloud miner runs uninterrupted.
- Rootkits and Fileless Malware: Attackers use rootkits and fileless malware to hide the cryptominer’s presence and activities, making detection difficult.
How They Stay Hidden (Dormancy)
1. Evasion techniques
- Once inside, cryptominers employ various evasion techniques to avoid detection. They often modify system processes and hide their presence using rootkits, allowing them to run unnoticed in the background.
- Example: A cryptominer may rename their processes to mimic legitimate system processes, making it difficult for administrators to spot them during routine checks.
2. Stealth mechanisms
- Cloud miners also use stealth mechanisms such as delaying their activity or operating only during off-peak hours to avoid raising suspicion.
- Example: A cryptominer might remain inactive during business hours and activate only at night or during weekends when system monitoring is less intensive.
When and How They Attack
1. Activation during high resource availability
- Cryptominers are often programmed to activate when there is high resource availability, such as during off-peak hours or when the system detects low usage. This strategy ensures that their activity goes unnoticed while maximizing cloud mining output.
- Example: A cryptominer might start its operations late at night when legitimate workloads are minimal, reducing the chances of detection.
2. Execution of attacks
- Once activated, cloud miners consume significant computational resources to mine cryptocurrency. This can lead to noticeable performance degradation and increased operational costs.
- Example: A cloud miner might use the majority of a cloud instance’s CPU and GPU resources, causing legitimate applications to slow down or crash.
Lurking in the Shadows: Hidden Threats
Cryptominers often employ sophisticated techniques to persist and evade detection, making them formidable threats in cloud environments. Their ability to stay hidden while exploiting resources underscores the need for continuous monitoring and advanced runtime threat detection.
Persistence and Evasion Techniques
1. Persistence mechanisms
- Cloud miners use various methods to ensure they remain active in the system even after initial detection attempts. They often deploy cron jobs, scheduled tasks, or scripts that re-execute the malicious software if it is removed.
- Example: A cloud miner may install a cron job that checks for the presence of the mining software every few minutes and reinstalls it if it has been deleted.
2. Rootkits and fileless malware
- Cryptominers may use rootkits or fileless malware to avoid detection by traditional security tools. Rootkits allow cloud miners to hide their files, processes, and network connections, while fileless malware operates in memory without leaving traces on the disk.
- Example: A rootkit might intercept system calls to conceal the presence of cloud mining processes, making them invisible to standard monitoring tools.
3. Network and process hiding:
- Cryptominers often camouflage their network traffic and processes to blend in with legitimate activities. They may encrypt their communications or use non-standard ports to avoid detection by network security devices.
- This depends on the cryptominer and the techniques the attacker is willing to use since the attacker may even decide to use well-known application ports to blend in with the existing workloads of the organization.
The Need for Continuous Monitoring and Runtime Threat Detection
1. Real-Time Threat Detection
- Continuous monitoring and runtime threat detection are essential to effectively identifying and responding to cloud miners. Unlike periodic scans, real-time monitoring can detect suspicious activities as they happen, allowing for immediate intervention.
- Example: A runtime security tool might detect abnormal CPU usage patterns indicative of cloud mining and alert administrators instantly.
2. Behavioral Analysis
- Advanced threat detection tools employ behavioral analysis to identify deviations from normal activity. By analyzing patterns of behavior, these tools can detect cloud miners based on their operational characteristics rather than relying solely on known signatures.
- Example: A behavioral analysis system might flag a process that suddenly consumes excessive CPU resources or accesses unusual network endpoints.
3. Hash-Based Detection
Hash-based detection can identify known cryptominer malware by comparing file hashes against a database of malicious hashes. This method can quickly flag known threats.
Example: Using a security tool that checks the hash of a file against a list of known cryptominer hashes can help in detecting and blocking the miner before it can cause damage.
4. Byte Pattern Scanning
Byte pattern scanning involves searching for specific sequences of bytes that are unique to cloud mining malware. This method can detect both known and new variants of cryptominers.
Example: Implementing Yara rules to scan for byte patterns associated with cloud mining software can help in early detection.
5. Automated Response Mechanisms
- Implementing automated response mechanisms can help mitigate the impact of cryptominers by isolating affected resources and removing malicious software promptly. Automation reduces the time to respond and limits the potential damage.
- Example: Upon detecting a cryptominer, an automated system could quarantine the compromised instance, terminate suspicious processes, and initiate a forensic investigation.
Once Detected, What is the Next Step?
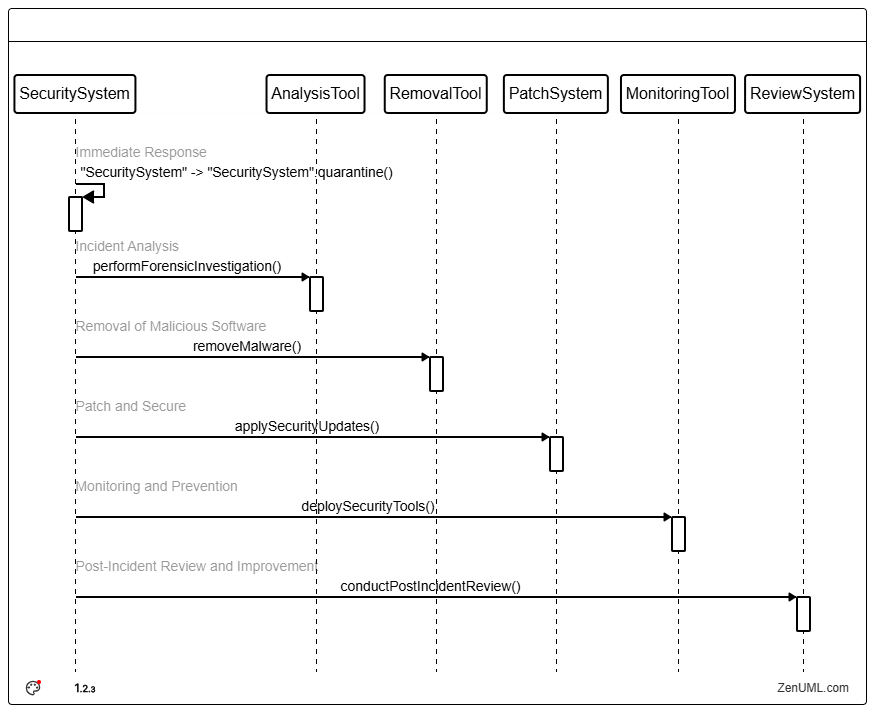
1. Immediate Response: Upon detecting a cryptominer, it is crucial to take immediate action to prevent further damage and resource consumption. The first step is to isolate the affected system or instance from the network to contain the threat.
Example: Quarantining the compromised instance prevents the cryptominer from communicating with its command-and-control server and spreading to other systems.
2. Incident Analysis: Conduct a thorough analysis to understand the extent of the compromise. This includes identifying how the cloud miner entered the system, what vulnerabilities were exploited, and whether any other malicious activities are ongoing.
Example: Performing a forensic investigation to trace the attack vector and analyzing logs to determine the scope of the breach.
3. Removal of Malicious Software: Remove the cloud mining software and any associated malware from the affected systems. This may involve using specialized tools to detect and clean rootkits or fileless malware that standard antivirus solutions might miss.
Example: Utilizing advanced malware removal tools to ensure complete eradication of the cryptominer and related threats.
4. Patch and Secure: Patch any vulnerabilities that were exploited by the cryptominer to prevent future attacks. This includes updating software, applying security patches, and hardening system configurations.
Example: Applying security updates to the container runtime, strengthening access controls, and implementing network segmentation to limit the impact of potential future breaches.
5. Monitoring and Prevention: Enhance monitoring and prevention measures to detect and respond to similar threats in the future. Implement continuous monitoring, runtime threat detection, and automated response mechanisms to improve your security posture.
Example: Deploying advanced security tools that provide real-time monitoring and automated threat response to catch and mitigate cloud miners and other threats promptly.
6. Post-Incident Review and Improvement: After resolving the incident, conduct a post-incident review to identify lessons learned and improve your security practices. This involves analyzing the incident response process, identifying gaps, and implementing measures to strengthen your defenses.
Example: Organizing a post-incident review meeting to discuss what worked well, what didn’t, and what improvements can be made to enhance your organization’s security posture.
Leading the Charge: Leadership’s Role in Security
Effective cybersecurity starts at the top management, which is no different for cybersecurity in cloud-native environments.
Leadership is crucial in fostering a security culture, ensuring adequate resources are allocated, and staying informed about the latest threats and solutions. Recognizing the importance of proactive measures can significantly enhance an organization’s resilience against cryptominer and other cyber attacks.
Importance of Leadership Awareness
1. Understanding cybersecurity risks
- Leadership must be well-informed about the latest and upcoming cybersecurity risks. This knowledge is essential for making strategic decisions that prioritize security.
- Regular briefings and reports on the latest cybersecurity trends and threats can keep leadership aware and prepared.
2. Promoting a culture of security:
- Creating a security-conscious culture within the organization starts with leadership. By emphasizing the importance of cybersecurity, leaders can encourage employees at all levels to adopt best practices and remain vigilant.
- Incorporating cybersecurity into corporate values and ensuring it is a key component of employee training programs.
Planning, Resource Allocation, and Investment in Security
1. Allocating sufficient budget for security measures
- Adequate funding is essential for implementing and maintaining robust security measures. Leaders must ensure that sufficient resources are allocated to cybersecurity initiatives.
- Example: Budgeting for advanced security tools, continuous monitoring solutions, and regular security audits.
2. Investing in training and advanced security tools:
- Continuous education and training for employees, especially IT and security staff, are vital for staying ahead of evolving threats. Investing in advanced security tools can provide better detection and protection capabilities.
- Example: Providing regular cybersecurity training sessions and certifications for staff and deploying tools like ARMO Platform for runtime threat detection.
3. Strategic planning for security initiatives:
- It is critical to develop and implement a comprehensive security strategy that includes proactive measures, incident response plans, and continuous improvement processes.
- Example: Creating a detailed cybersecurity roadmap that outlines objectives, timelines, and responsibilities for enhancing security posture.
Importance of Incident Response Plan
1. Preparation for potential breaches
- A well-defined incident response plan is crucial for minimizing the impact of a security breach. Leadership must ensure that this plan is regularly updated and tested.
- Example: Conducting regular incident response drills to ensure the team is prepared to handle real-world scenarios effectively.
2. Swift and effective response:
- A prompt and coordinated response can mitigate the damage caused by a security breach. Leadership must empower teams with the authority and tools needed to act quickly.
- Example: Establishing clear communication channels and decision-making processes for rapid response during a security incident.
3. Post incident analysis and improvement:
- After a security incident, it is essential to conduct a thorough analysis to identify weaknesses and implement improvements. Leadership should support a culture of continuous learning and adaptation.
- Example: Organizing post-incident review meetings to discuss what happened, what was done well, and what can be improved for future incidents.
Wrapping Up: Key Takeaways
Cryptominer threats in cloud environments pose significant risks, from resource drain to increased costs, and operational disruptions. Addressing these threats requires a comprehensive approach involving awareness, proactive measures, and advanced detection tools.
Understanding the complexities of cloud-native environments can be the first step to detecting and preventing cloud mining attacks within your organization.
There is no silver bullet to preventing cloud mining attacks within your cloud infrastructure. However, adopting security best practices and staying informed of the latest attacks and security trends will ensure that you give yourself a fighting chance in an ever-changing threat landscape.
Take the next step in securing your cloud infrastructure with ARMO’s Cloud Detection and Response. ARMO offers advanced tools that help you identify cloud miners and other threats before they can cause damage. Try ARMO today and secure your cloud environment against evolving security challenges.
The post Cryptominers in the Cloud appeared first on ARMO.
*** This is a Security Bloggers Network syndicated blog from ARMO authored by Oshrat Nir. Read the original post at: https://www.armosec.io/blog/cloud-mining-security-threats/
如有侵权请联系:admin#unsafe.sh
