2024-9-6 03:0:0 Author: securityboulevard.com(查看原文) 阅读量:10 收藏
![]()
Trackers are everywhere and come in many different forms. Some tracking methods are more invasive than others; this post aims to explain what “trackers” are, how they work, and give examples of the data they collect.
Fingerprinting, tracking, and trackers go hand-in-hand. Generally, fingerprinting focuses on reliably identifying unique users – this identity is often then used by tracking mechanisms.
Fingerprinting uses the information found on/sent by your device to identify you and subsequently track you. Identification by unique properties such as browser settings, device information, and connected networks (to include nearest cell towers) are the building blocks of creating a unique user profile.

Fingerprinting takes into account your entire device and factors directly surrounding it – your browser, connected networks, the operating system (exact build and version), browser settings, browser add-ons/extensions, hardware of the device, and more. Fingerprinting is as invasive as it is accurate; for example, the EFF has estimated that only 1 in 286,777 browsers will share the same fingerprint. Naturally, some fingerprinting techniques are more invasive than others.
Fingerprinting has evolved so much so that it is next to impossible to simply “block all fingerprinting” techniques. In fact, it has been demonstrated that on some devices – such as smartphones – some fingerprinting attacks are not possible to block.
Trackers come in many forms. Generally, regardless of what form of tracking is used, trackers are designed to either 1) track you across different websites, web services, and web apps or 2) collect identifying information about you and your device(s). Frequently, they do both.

Many proponents of tracking say that it is beneficial for users because they can get personalized recommendations. While this is true, it comes at the price of the user’s privacy; often times, users don’t understand just what this privacy cost entails even if they are aware of it.
Though as we collectively learn of tracking (and fingerprinting) technologies/methods, what data they can capture, and just who that data is shared with – we should strongly consider: Is the price worth it?
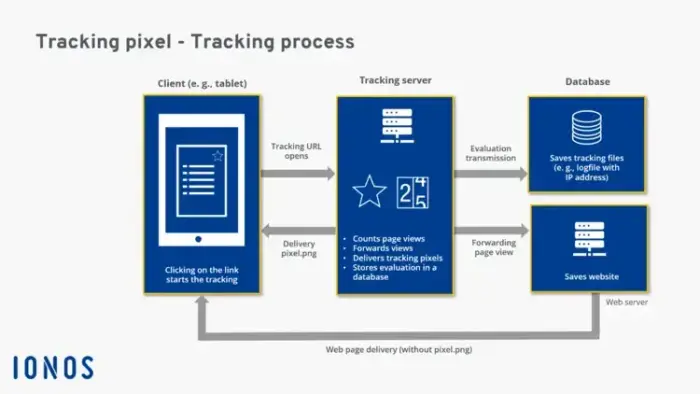
Tracking pixels (also known as web beacons or pixel tags) are 1×1 pixel-sized images typically embedded in web pages, ads, and emails. Though they are images and load like images, they’re so small that they’re invisible to the human eye.
Once loaded, tracking pixels capture data typically about user activity and engagement. For example, tracking pixels are almost ubiquitously used in emails – particularly, marketing emails – to track if and when a recipient opens an email; tracking pixels embedded in emails can report the exact date and time an email was opened, location of the device used to open the email, and in which email client the email was opened.
Source: Ionos
Tracking pixels are also commonly found in advertisements. Tracking pixels embedded in advertisements are often called “ad trackers” – though this term could also include other tracking methods, such as tracking cookies; they can track views, clicks, referral sources, and conversions in displayed advertisements.
Some websites use tracking pixels as well. They’re typically used in combination with analytics software and tracking cookies, though of course this varies immensely between websites. Some may even use multiple tracking pixels, of which are commonly JavaScript code provided by third parties (like the Meta Pixel).
Tracking pixels are versatile and depending on where they are embedded and the entities using them, they can collect many pieces of data such as (but not limited to):
- Browsing history
- Search history
- Location data
- Device information (type, operating system, etc)
- Conversions
- Clicked ads within the ad network
- Data submitted to websites
- Email client information
- Email open data, time
- Information from cookies stored on your device (are you signed into another service?)
- Social media profile information
A rather well-known and infamous tracking pixel is the Meta Pixel (formerly: Facebook Pixel). It is embedded on millions of websites and has shown to be ruthlessly efficient in collecting massive amounts of data – including sensitive data such as tax record information, veteran statuses, addresses, and even health information.
The Meta Pixel in recent times has been the subject of privacy litigation in 2022 and 2023 (and likely going forward), mostly due to it facilitating sensitive data and information sharing – especially where the data was not to be shared with third parties “by law” (think: violating HIPAA) without expressed consent from users.

Cookies are bits of data that get stored on your web browser by websites. You’ve probably heard of first-party and third-party cookies; first-party cookies are placed by the website itself whereas third-party cookies are placed with a different entity that loads on that same website, such as ads served by an ad network.
Some cookies are essential for certain websites to function. Some websites have many cookies that retain many bits of differing information that could get annoying for users to continuously define on subsequent visits. For example, session cookies may be used to reauthenticate you to a website on a subsequent visit – you don’t have to login again. Session cookies may also retain saved preferences (dark mode or light mode?) and other details between visits.
Source: CookieYes
Of course, some cookies in your browser may also be tracking cookies. Note that tracking cookies don’t do the active tracking themselves, but they store information websites interested in tracking your activity can retrieve and read later, often collecting personal information. Tracking cookies can be first-party or third-party, but are commonly third-party.
For collection by calling websites/hosts, tracking cookies can store:
- Browsing history (visited sites)
- Length of stay on a given site
- Interaction data with a site (ex: how many pages you click through)
- Advertisements clicked
- Purchased products
- Information put into web forms (even without pressing the submit button)
- Location data
- Personal information given to a website
Once upon a time, due to Safari and Firefox blocking third party cookies by default and laws such as the EU’s GDPR coming into effect, third-party cookies were seemingly on their way out. Big Tech companies – such as Google and Microsoft – sought to kill the cookie and rolled out plans to do so. Specifically, the initiative to phase out tracking cookies was spearheaded by Google in anticipation of rolling out their Topics API/Privacy Sandbox (which was initially “FloC”).
![]()
However, in July 2024, Google announced it was no longer…
*** This is a Security Bloggers Network syndicated blog from Avoid The Hack! authored by Avoid The Hack!. Read the original post at: https://avoidthehack.com/what-are-trackers
如有侵权请联系:admin#unsafe.sh

