2024-9-5 23:37:49 Author: www.malwarebytes.com(查看原文) 阅读量:3 收藏
In mid-August, we identified a malvertising campaign targeting Lowes employees via Google ads. Like many large corporations, Lowe’s has their own employe portal called MyLowesLife, for all matters related to schedule, pay stubs, or benefits.
Lowe’s employees who searched for “myloweslife” during that time, may have seen one or multiple fraudulent ads. The threat actor, who does not strictly limit themselves to Lowe’s but also targets other institutions, aims to gain access to the login credentials of current and former employees.
My Lowe’s Life ads
Combining ads with a phishing page is a proven recipe for success. Indeed, unsuspecting users often rely on Google Search to take them to the site they are looking for, rather than manually entering its full URL in the browser’s address bar. It is somewhat suspicious to see ads for an internal HR portal, but then again it could be easy to overlook that oddity.
We found two different advertiser accounts impersonating MyLowesLife, and in one instance, we even saw 3 malicious ads from both accounts one after the other. The URL listed for each ad is different, and does not match the legitimate one (myloweslife.com), a well-known technique of lookalikes criminals often employ.
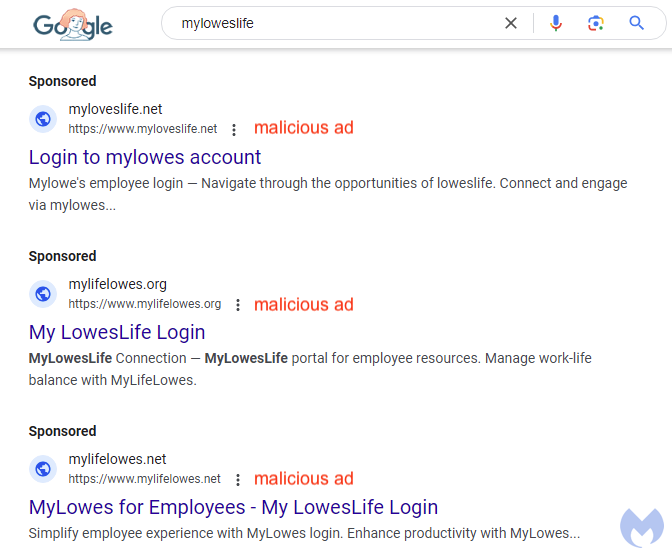
Phishing site built with AI
The threat actor registered several similarly looking domain names in order to trick their victims:
myloveslife[.]net
mylifelowes[.]org
mylifelowes[.]net
myliveloves[.]net
myloveslive[.]net
mylofeslive[.]net
myloweslove[.]com
What’s interesting is how the home page for each of those is not what you’d expect. In fact, what we see is a generic ‘retail store’ template which appears to have been built using AI.
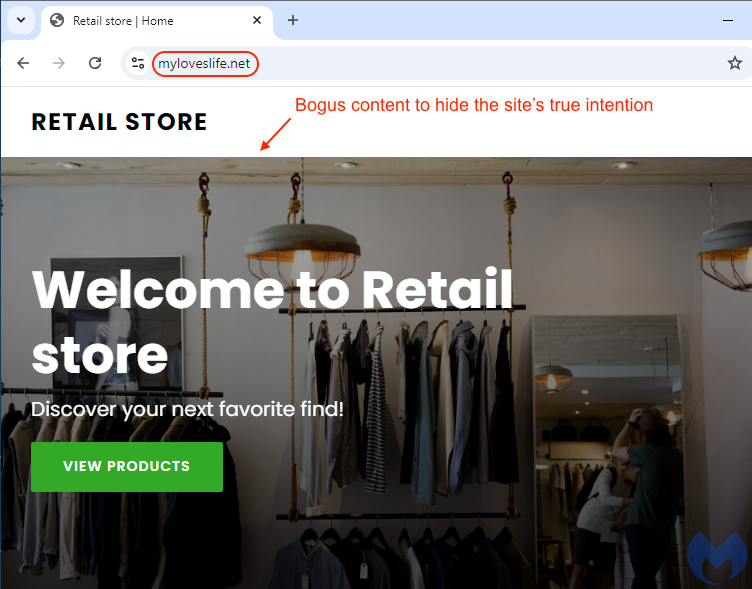
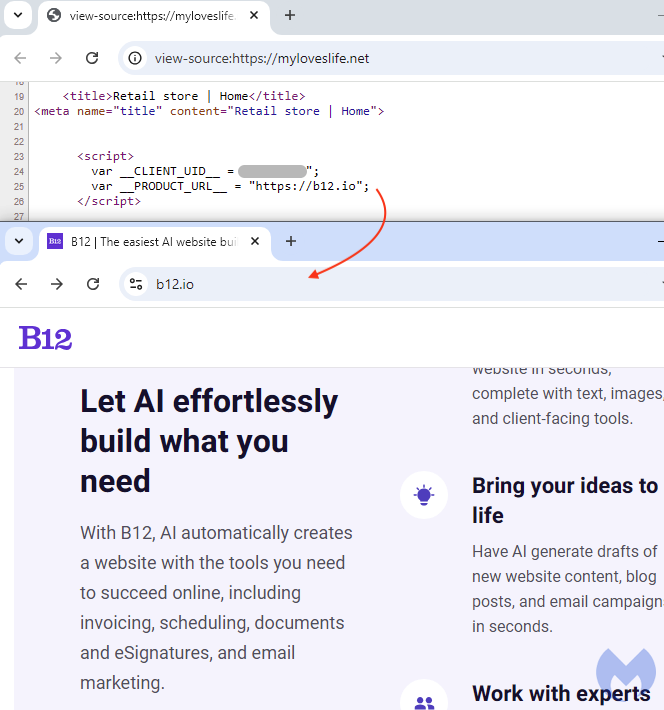
There is a simple reason for this: if anyone was to investigate those potentially fraudulent websites, they would not see anything malicious. As a result, it will be difficult to convince a domain registrar or hosting provider to take any action such as suspending the site.
Phishing page
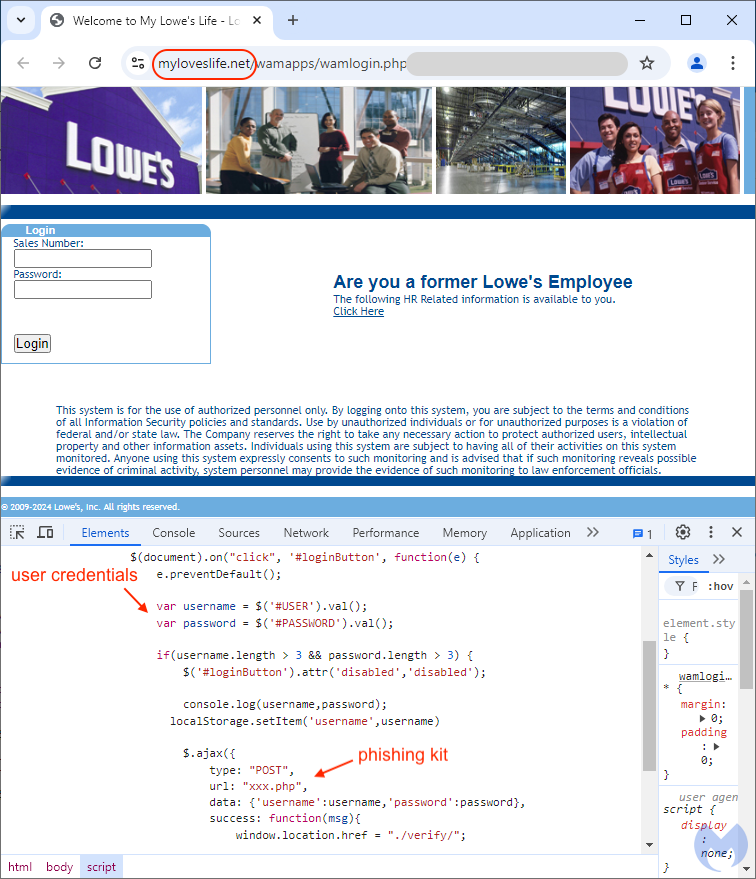
When victims click on the Google ad, they are taken directly to the phishing page, contained within a directory named ‘wamapps’, which interestingly matches the structure of the real Mylowe’s Life website:
https://lius.myloweslife.com/wamapps/wamlogin
This an exact replica of the real Lowe’s portal that prompts users for their Sales Number and Password:

Looking at the page’s source code, we can see how these two fields are being sent back to the threat actor using a POST request via xxx.php, the phishing kit. After collecting this data, a second page asks users for their security question. This is presumably a feature used by Lowe’s to secure accounts if they detect unusual login activity:
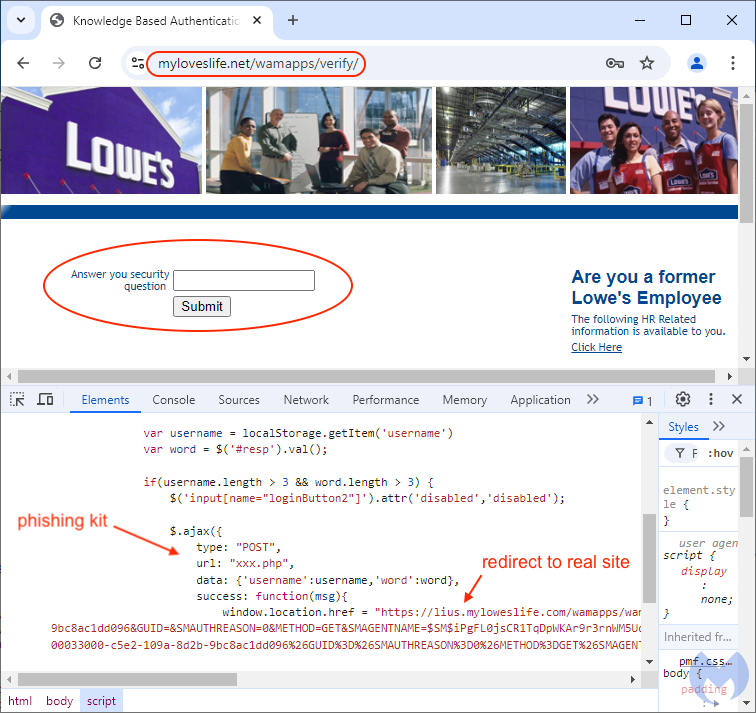
Finally, after providing those details, victims are redirected to the real MyLowesLife website where they will be asked for their login details again. While that could raise suspicion, it’s possible many users will think it’s simply a glitch with the system and won’t look back again.
It’s unclear what the threat actor does with the stolen credentials, but likely they are a broker reselling them to other criminals.
Mitigations
Brand impersonation via Google ads is a very popular technique leveraged by threat actors of all kind. They know people will open up their default browser, do a quick search and that’s exactly where they can target them.
To avoid many of the phishing campaigns that abuse Google ads, we strongly recommend against clicking on sponsored results. You are better off scrolling down further and visiting the official websites directly.
For an online portal you regularly visit (bank, grocery store, etc.) it’s a good idea to bookmark the website into your browser’s favorites: it’s quicker and safer to visit a site that you trust in that manner.
We reported these malicious ads to Google and to our knowledge this ad campaign is no longer running. Malwarebytes customers were protected on day 1 via both the Malwarebytes Browser Guard and Malwarebytes Premium Security. If you suspect you have been a victim of identity theft, feel free to check out Malwarebytes Identity Theft Protection (also available to customers via our premium security products).

如有侵权请联系:admin#unsafe.sh