Earlier this year, NVISO identified an active cluster of domains likely tied to social engineering. Upon analysis, the domains masqueraded themselves as CAPTCHA verification pages, requesting visitors to press a button to verify they’re human.

While seasoned professionals may immediately recognize the page as fraudulent, less alert users might inadvertently provide their consent to notifications. Shortly after giving consent, the end-user would continuously receive browser-delivered phishing notifications.

As the hunt’s hypothesis assumed breach, we further hunted for traces of both successful social engineering and follow-on abuse. In the following sections we will present which forensic Chromium evidence can be found for initial social engineering (i.e., granted permissions) and follow-on interactions (i.e., delivered notifications, user interactions). Finally, we will cover how this hunt can be performed enterprise-wide through our contributed Velociraptor artifact and provide enterprise hardening recommendations to prevent such abuse.
This article focuses on Chromium-based web-browsers (e.g., Google Chrome, Microsoft Edge) as available telemetry scoped potential victims down to these browsers.
Evidence
In this section we will cover which evidence allowed us to answer if a user had allowed websites to send notifications, had subsequently received notifications and, finally, interacted with the received notifications.
Chromium User Preferences
The Chromium user preferences is a JSON file titled Preferences located within the user’s data directory. The file contains a flurry of settings, of which some pertaining to the notifications. For the two most prominent enterprise Chromium browsers (Google Chrome & Microsoft Edge), the locations are as follows:
| Operating System | Standard Google Chrome Path |
| Windows | *:\Users\*\AppData\Local\Google\Chrome\User Data\*\Preferences |
| MacOS | /Users/*/Library/Application Support/Google/Chrome/*/Preferences |
| Linux | /home/*/.config/google-chrome/*/Preferences |
| Operating System | Standard Microsoft Edge Path |
| Windows | *:\Users\*\AppData\Local\Microsoft\Edge\User Data\*\Preferences |
| MacOS | /Users/*/Library/Application Support/Microsoft/Edge/*/Preferences |
| Linux | /home/*/.config/microsoft-edge/*/Preferences |
Notifications
The $.profile.content_settings.exceptions.notifications dictionary contains the notification permissions attributed to websites. Each website with non-default permissions has its own entry with a last_modified and setting property.
{
"https://bestclevercaptcha.azurewebsites.net:443,*": {
"last_modified": "13349960779269787",
"setting": 1
}
}JSON (Beatified)
The last_modified value is a variation of the Windows’ FILETIME. It represents the number of microsecond intervals since January 1, 1601 UTC (as opposed to Windows’ 100-nanosecond). Conversion to the more common Linux-like timestamp can be achieved through the (last_modified/1000000)-11644473600 formula (i.e., convert last_modified into seconds and remove the number of seconds between Linux’s 1970 and Windows’ 1601 epoch).
The setting property can be mapped to Chromium’s ContentSetting enum. In our case, a setting of value 1 indicates the website has the CONTENT_SETTING_ALLOW permission for notifications.
enum ContentSetting {
CONTENT_SETTING_DEFAULT = 0, // 0
CONTENT_SETTING_ALLOW, // 1
CONTENT_SETTING_BLOCK, // 2
CONTENT_SETTING_ASK, // 3
CONTENT_SETTING_SESSION_ONLY, // 4
CONTENT_SETTING_DETECT_IMPORTANT_CONTENT, // 5
CONTENT_SETTING_NUM_SETTINGS
};C
The $.profile.content_settings.exceptions.notifications object hence provides preliminary evidence on whether a user has set specific website notification permissions, and when this occurred. The object however represents the current permission state; If a user revoked/changed the assigned permissions, the previous states are not available.
Notification Interactions
The $.profile.content_settings.exceptions.notification_interactions dictionary contains metrics on issued and interacted notifications. As soon as a notification is issued or interacted with, the daily metrics are updated.
As was the case for the previously covered notifications object, the notification_interactions object contains per-URL keys as well as a last_modified property. The setting property is however a dictionary where the keys represent Linux-like timestamps (rounded to the day) and the display_count alongside click_count properties provide daily counters on the respective amount of displayed notifications and optional user-interacted notifications.
{
"https://bestclevercaptcha.azurewebsites.net:443,*": {
"last_modified": "13349960822063286",
"setting": {
"1704672000": {
"click_count": 1,
"display_count": 3
},
"1705449600": {
"display_count": 1
}
}
}
}JSON (Beatified)
Together, the notifications and notification_interactions preferences provide sufficient visibility to identify:
- If, and when, a user has set current custom notification permissions.
- When, and how often, said website issued notifications.
- When, and how often, the user interacted with the website-issued notifications.
The above visibility enables threat hunters to identify which users are likely to have been socially engineered and at which frequency. However, for affected users, these artifacts do not permit to scope the incident’s post-notification activity.
Chromium Platform Notifications
While the Chromium user preferences provide insights into the current permissions and associated metrics, the Chromium Platform Notifications database provides visibility into the issued notifications. The Chromium Platform Notifications folder is located alongside the Preferences file and leverages the LevelDB format.
Within this LevelDB store, keys are encoded and values serialized using Protocol Buffers. Commercial forensic tooling such as Axiom supports its parsing out of the box. Alternatively, open source solutions such as LevelDBDumper can assist in recovering the Protocol Buffer data which can, in theory, be de-serialized through ProtoBufEditor if provided with the definitions.
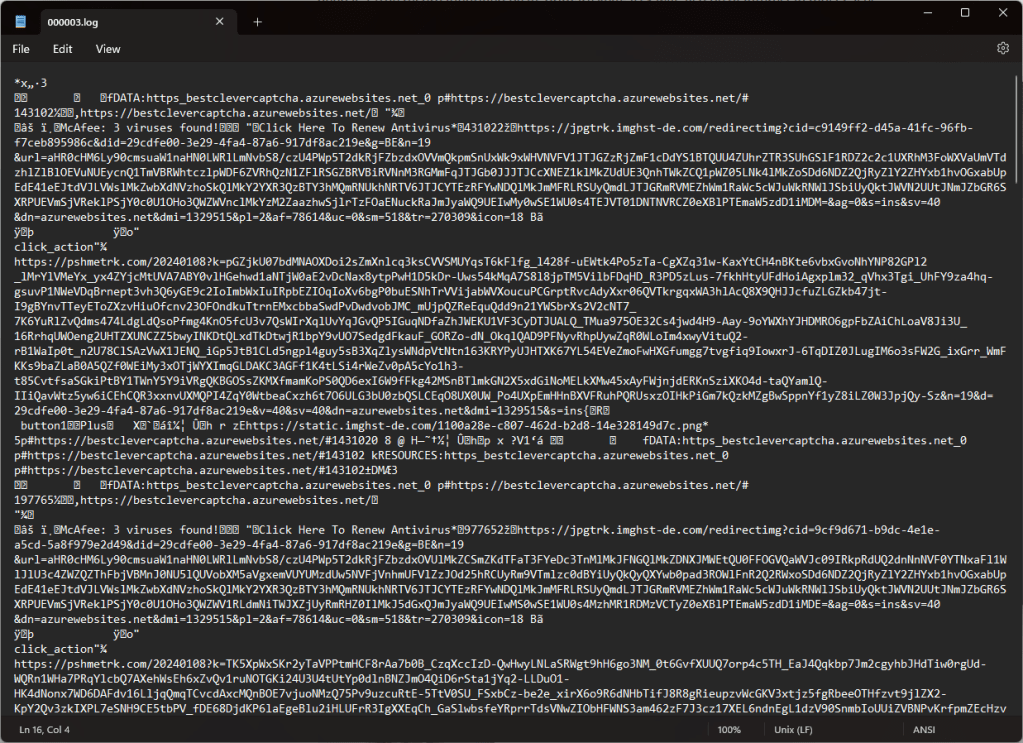
Alternatively, any regular editor is sufficient to extract IoCs (Indicators of Compromise). As shown below, the Platform Notifications\*.log log file contains

Hunting
Endpoint security solutions rarely provide visibility into application-level settings. To empower organizations to hunt for potential traces of browser notification abuse, we extended Velociraptor’s SQLiteHunter. Through the forensic collector’s Generic.Forensic.SQLiteHunter artifact, investigators can now collect and parse notification-related settings on Chromium browsers.

Recommendations
Abusing browser notifications is not a new technique, which luckily also means that preemptive security controls do exist. Organizations are recommended to enforce and harden web browser settings. Specific to this attack pattern, organizations can leverage Chromium’s DefaultNotificationsSetting and NotificationsAllowedForUrls settings as well as FireFox’s Permissions policy to deny notification requests while having organization-approved exceptions.

Maxime Thiebaut
Maxime Thiebaut is a GCFA-certified Incident Response & Digital Forensics Analyst within NVISO CSIRT. He spends most of his time performing defensive research and responding to incidents. Previously, Maxime worked on the SANS SEC699 course. Besides his coding capabilities, Maxime enjoys reverse engineering samples observed in the wild.
如有侵权请联系:admin#unsafe.sh