2024-9-7 01:39:7 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Author:
Kaustubh Jagtap, Product Marketing Director, SafeBreach
On September 5th, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and National Security Agency (NSA) issued an urgent advisory warning security teams about efforts undertaken by threat actors affiliated with Russia’s General Staff Main Intelligence Directorate (GRU) 161st Specialist Training Center (Unit 29155). Detailed information about this threat and the associated IOCs and TTPs can be seen on Russian Military Cyber Actors Target US and Global Critical Infrastructure.
This blog will share an overview of the threat and our coverage for these threat actors. As a SafeBreach customer, you will have access to all the attacks listed below and more to validate your organizational security controls against these state-sponsored threat actors.
US CERT Alert AA24-249A (GRU Unit 29155)
GRU Unit 29155 is well known for carrying out cyber attacks with the sole purpose of espionage, sabotage, and reputational harm from at least 2020. In early 2022, they began deploying the destructive WhisperGate malware against Ukrainian organizations in an attempt to disable critical infrastructure at the start of the regional conflict. This group operates independently of other known GRU units 26165 and 74455. This advisory is intended to warn organizations and entities across United States and its international partners against the potential threat from Unit 29155 which has been previously responsible for attempted coups, sabotage and influence operations, and assassination attempts throughout Europe. Additionally, this group is known to collect data for espionage purposes, causing reputational harm (via data leaks), and sabotage (via destruction of stolen data). The FBI believes that Unit 29155 threat actors also rely on non-GRU threat groups to conduct their malicious operations.
GRU Unit 29155 is also known by the following names:
- Cadet Blizzard (formerly known as DEV-0586 by Microsoft)
- Ember Bear (also known as Bleeding Bear by CrowdStrike)
- Frozenvista
- UNC2589
- UAC-0056
The group has continually targeted several NATO and non-NATO members in Europe and North America, in addition to other countries in Latin America, and Central Asia. These attacks include website defacements, infrastructure scanning, data exfiltration, and data leak operations. Since the beginning of the Ukrainian conflict in 2022, Unit 29155 has been responsible for disrupting efforts to provide aid to Ukraine by targeting critical infrastructure sectors including government services, financial services, transportation systems, energy, and healthcare.
Technical Details
Reconnaissance – According to the information available, Unit 29155 leverages several publicly available tools (see below) to scan victim networks for IP addresses that can potentially grant them access into the network:
- Acunetix
- Amass
- Droopescan
- JoomScan
- MASSCAN
- Netcat
- Nmap
- Shodan
- VirusTotal
- WPScan
They typically enumerate the victims’ Active Directory (AD), looking for active devices and searching for vulnerabilities on these devices to further their goals. Unit 29155 also leverages common red teaming techniques and publicly available tools to conduct cyber operations.
Initial Access – VPNs are typically used to anonymize their presence and Unit 29155 constantly attempt to exploit weaknesses in internet-facing systems by targeting the unpatched vulnerabilities, including:
- CVE-2021-33044 (Dahua Security)
- CVE-2021-33045 (Dahua Security)
- CVE-2022-26134 (Atlassian Confluence Server and Data Center)
- CVE-2022-26138 (Atlassian Confluence Server and Data Center)
- CVE-2022-3236 (Sophos: Firewall)
Lateral Movement – Unit 29155 uses the Shodan search engine to scan for vulnerable IoT devices and leverages exploitation scripts to authenticate to IP Cameras with default usernames and passwords and exfiltrate image files. Additionally, they attempt to perform remote command execution (RCE) on vulnerable IP cameras to extract and dump configuration settings and credentials.
Command and Control (C&C) – Unit 29155 uses Virtual Private Servers (VPSs) to hide their location and host operational tools that enable the threat group to perform recon, exploit victim infrastructure, and exfiltrate stolen data. Once an exploit is successful on a victim network, a Meterpeter payload is used to initiate communication with C&C infrastructure.
Exfiltration of Stolen Data – Stolen data from the victims is compressed and exfiltrated using the command line utility, Rclone and sent to the threat actors’ remote storage location. Unit 29155 have been observed exfiltrated Windows processes and artifacts, such as Local Security Authority Subsystem Service (LSASS) memory dumps, Security Accounts Manager (SAM) files, and SECURITY and SYSTEM event log files.
Important Note for SafeBreach Customers – Coverage for AA24-249A (Unit 29155)
As soon as details were made available, the SafeBreach Labs team mapped existing attacks in the Hacker’s Playbook to this US-CERT alerts immediately. It is important to note that existing SafeBreach customers already had a comprehensive level of coverage against the tactics and techniques leveraged by the Fox Kitten threat group identified in the advisory. Please run/re-run the attacks listed below to ensure your environments are protected against these TTPs.
New IOC-Based Playbook Attacks Related to AA24-249A (Unit 29155)
- WhisperGate Payload:
- #10462 – Write WhisperGate_payload (2a25b2) ransomware to disk
- #10463 – Transfer of WhisperGate_payload (2a25b2) ransomware over HTTP/S
- #10464 – Transfer of WhisperGate_payload (2a25b2) ransomware over HTTP/S
- #10465 – Email WhisperGate_payload (2a25b2) ransomware as a compressed attachment
- #10466 – Email WhisperGate_payload (2a25b2) ransomware as a compressed attachment
- #10467 – Write WhisperGate_payload (6d892d) ransomware to disk
- #10468 – Transfer of WhisperGate_payload (6d892d) ransomware over HTTP/S
- #10469 – Transfer of WhisperGate_payload (6d892d) ransomware over HTTP/S
- #10470 – Email WhisperGate_payload (6d892d) ransomware as a compressed attachment
Existing IOC-Based Playbook Attacks Related to AA24-249A (Unit 29155)
- WhisperGate:
- #6880 – Pre-execution phase of WhisperGate_stage1 ransomware
- #6881 – Write WhisperGate_stage1 ransomware to disk
- #6882 – Transfer of WhisperGate_stage1 ransomware over HTTP/S
- #6883 – Transfer of WhisperGate_stage1 ransomware over HTTP/S
- #6884 – Email WhisperGate_stage1 ransomware as a compressed attachment
- #6885 – Email WhisperGate_stage1 ransomware as a compressed attachment
- #6886 – Pre-execution phase of WhisperGate_stage2 ransomware
- #6887 – Write WhisperGate_stage2 ransomware to disk
- #6888 – Transfer of WhisperGate_stage2 ransomware over HTTP/S
- #6889 – Transfer of WhisperGate_stage2 ransomware over HTTP/S
- #6890 – Email WhisperGate_stage2 ransomware as a compressed attachment
- #6891 – Email WhisperGate_stage2 ransomware as a compressed attachment
- Raspberry Robin:
- #7968 – Write Raspberry Robin worm to disk
- #7969 – Transfer of Raspberry Robin worm over HTTP/S
- #7970 – Transfer of Raspberry Robin worm over HTTP/S
- #7971 – Email Raspberry Robin worm as a compressed attachment
- #7972 – Email Raspberry Robin worm as a compressed attachment
Existing Behavioral Playbook Attacks Related to AA24-249A (Unit 29155)
- #264 – Remote Control using Meterpreter to Execute File Commands
- #806 – Collect Files using ZIP
- #1263 – Data asset exfiltration over TCP
- #2267 – Add an exclusion to Windows Defender using PowerShell
- #2273 – Pass the Hash over SMB using Mimikatz
- #2389 – Modify Firewall Rules using netsh.exe
- #2208 – Extract Credentials using Get-GPPPassword (PowerShell)
- #3828 – Credentials collection using PwDump
- #5107 – Stop a service using net stop command
- #6127 – Extract LSASS memory dump using Rundll32
- #6584 – File download from a DNSlivery server
- #6988 – Video capture (Windows)
- #7046 – Communication via TOR (Windows)
- #7144 – Unregister anti malware scanning interface providers
- #7167 – Covert data asset exfiltration over TOR (Windows)
- #7169 – Dump the SAM database from the registry (Windows)
- #7222 – Password Spraying
- #7834 – Add Exclusions to Windows Defender
- #7835 – Disable Windows Defender From Registry
- #8018 – Web application port scanning
- #8019 – Port scanning target simulator
- #8020 – Port scanning of local subnet network
- #8370 – In memory credential extraction via MiniDumpWriteDump
- #8371 – In memory credential extraction via MiniDumpWriteDump and handle hijacking
- #8372 – Credential extraction via Pypykatz
- #9456 – Extract SAM credentials from registry
- #10142 – Create port proxy using netsh.exe
What You Should Do Now
SafeBreach customers can now validate their security controls against these TTPs in multiple ways.
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA24-249A (Unit 29155), customize scenario, and run it.

Method 2 – From the Attack Playbook, select and filter attacks related to AA24-249A (Unit 29155). Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.

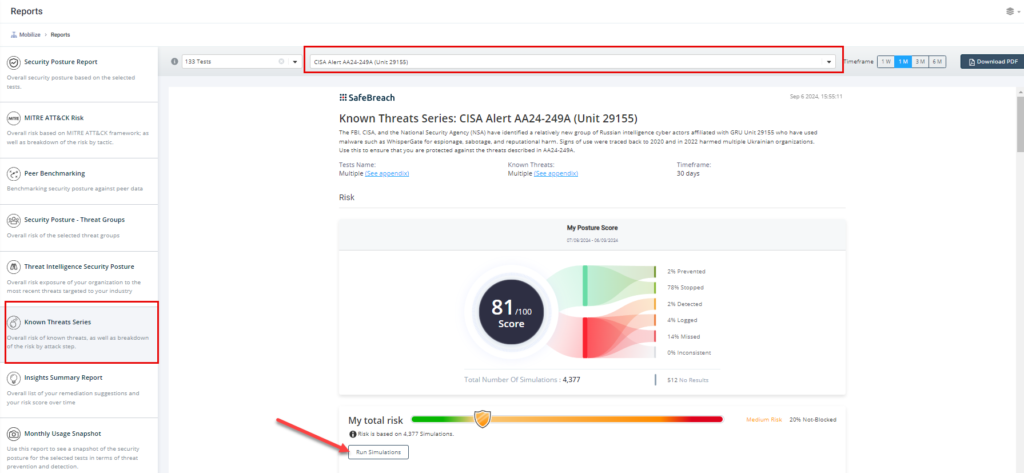
Method 3 – From the Known Attack Series report, select the US-CERT Alert AA24-249A (Unit 29155) report and select Run Simulations, which will run all attack methods.

NOTE – FBI, CISA, and NSA recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against growing threat of advanced cyber threats. Additional recommendations can be seen in the advisory (linked below):
- Limit adversarial use of common vulnerabilities.
- Deploy protective controls and security architecture.
- For additional recommendations, please review the advisory in detail.
Additional References:
- Microsoft Threat Intelligence Center: Destructive Malware Targeting Ukrainian Organizations
- Microsoft Threat Intelligence Center: Cadet Blizzard Emerges as a Novel and Distinct Russian Threat Actor
- CrowdStrike: EMBER BEAR Threat Actor Profile
- Mandiant Threat Intelligence: Responses to Russia’s Invasion of Ukraine Likely to Spur Retaliation
- SentinelOne: Threat Actor UAC-0056 Targeting Ukraine with Fake Translation Software
- Introduction to Acunetix
- GitHub: OWASP Amass
- Kali Linux Tutorials: Droopescan
- GitHub: OWASP JoomScan
- Kali.org: MASSCAN
- DigitalOcean: How To Use Netcat to Establish and Test TCP and UDP Connections
- Shodan: What is Shodan?
- VirusTotal: How it Works
- GitHub: Through the Wire
- Confluence Security Advisory: Confluence Server and Data Center – CVE-2022-26134
- Microsoft: Security Bulletin MS17-010
- Avast: What is EternalBlue and Why is the MS17-010 Exploit Still Relevant?
- Palo Alto Networks Unit 42: Threat Brief – Ongoing Russia and Ukraine Cyber Activity
- CERT-UA#3799 Report
- Bellingcat: Attack on Ukrainian Government Websites Linked to GRU Hackers
- Trend Micro: Cyberattacks are Prominent in the Russia-Ukraine Conflict
如有侵权请联系:admin#unsafe.sh
