2024-9-9 17:44:21 Author: www.vmray.com(查看原文) 阅读量:8 收藏
The Labs team at VMRay actively gathers publicly available data to identify any noteworthy malware developments that demand immediate attention. We complement this effort with our internal tracking and monitor events the security community reports to stay up-to-date with the latest changes in the cybersecurity landscape.
In August 2024, the VMRay Labs team has been focused on the following areas:
1) New VMRay Threat Identifiers addressing:
- Detection of reverse shell attempts via Bash
- Detection of starting a PowerShell process with no command line parameters
2) Configuration Extraction capabilities for:
- Socks5Systemz
3) Smart Link Detonation improvements including new detonation rules for:
- URLs pointing to files hosted using GitHub comments
- The abuse of Microsoft’s forms.microsoft.com service in phishing campaigns
4) New YARA rules for:
- Atomic stealer
- Empyrean stealer
- Monti ransomware
- GrimResource
Now, let’s delve into each topic for a more comprehensive understanding.
In a few last blog posts, we introduced you to the concept of the VMRay Threat Identifiers (VTIs). In short, VTIs identify threatening or unusual behavior of the analyzed sample and rate the maliciousness on a scale of 1 to 5, with 5 being the most malicious. The VTI score, which greatly contributes to the ultimate Verdict of the sample, is presented to you in the VMRay Platform after a completed analysis. Here’s a recap of the new VTIs that we added, or improved in the past month.
1) Detect reverse shell attempts via bash
Category: Persistence
Reverse shell attacks are a concerning method that threat actors use to gain unauthorized access and control over systems. As part of our ongoing commitment to enhancing security, we are introducing our latest VMRay Threat Identifier (VTI), designed to detect reverse shell attempts via Bash—even when the Command & Control (C&C) server is down.
A reverse shell is a type of attack where an infected system initiates a connection back to the attacker’s machine, allowing the attacker to remotely control the compromised system. Once established, the attacker can execute commands, deploy additional malware, and perform various malicious activities, often without detection.
Bash, the default command-line shell found on many Unix-like systems such as Linux and macOS, is crucial in reverse shell attacks due to several key reasons. First, Bash is widely available, being pre-installed on most systems, which makes it a easily accessible tool for attackers. Its ability to execute a broad range of commands gives attackers significant control over a compromised system. Additionally, Bash’s scripting features allow attackers to automate the creation of reverse shells and other malicious activities, enhancing the efficiency of their attacks and making them harder to detect. Finally, because Bash is a legitimate and commonly used tool, its presence during an attack can often go unnoticed by security systems, blending in with normal system operations and reducing the likelihood of detection.
To address this evolving threat, our new VTI goes a step further. It actively monitors and triggers on any attempt to create a reverse shell via Bash, even if the attempt does not result in a successful connection. Additionally, by focusing on persistence attempts, our VTI ensures that even if the initial reverse shell connection fails, any subsequent attempts to re-establish the connection are detected.
2) Detect starting a PowerShell process with no command line parameters
Category: DefenseEvasion
PowerShell is a powerful tool built into Windows that allows users and administrators to automate tasks and manage systems efficiently. However, this same power makes it a convenient tool for cybercriminals as it is preinstalled and can simply be used for malicious activities. In particular, attackers often use PowerShell in a way that hides their true intentions, making it difficult for traditional security tools to detect malicious activity.
Recently, our analysis revealed an unusual pattern: a PowerShell process running without any visible command-line parameters—just “powershell” by itself. While this might not seem alarming at first glance, it turned out to be a red flag. Typically, when PowerShell is used legitimately, it comes with specific commands or scripts. Seeing a PowerShell process with no such commands suggests something unusual is happening behind the scenes.
The hidden danger
Let’s dive into the technical details. In the suspicious cases we observed, the PowerShell process wasn’t receiving its instructions through the usual command-line arguments. Instead, these instructions were being fed directly through what’s known as stdin (standard input), a channel typically used to send data to a program while it runs.
What’s particularly concerning is that this standard input was connected to a pipe—a method that allows two programs to talk to each other quietly. In this scenario, the attacker set up these pipes to secretly send commands to PowerShell. Because this technique doesn’t leave the usual clues that security tools look for, it can easily slip under the radar. As a result, traditional defenses, which often focus on visible command-line activity, might miss this kind of stealthy behavior entirely.
To tackle this sophisticated technique, we developed a new VTI designed specifically for Windows systems. The trigger logic behind this VTI is straightforward yet powerful: it tracks PowerShell processes that are started with stdin connected to a pipe, signaling potential malicious activity. Our new VTI ensures that even these hidden attacks won’t go unnoticed.
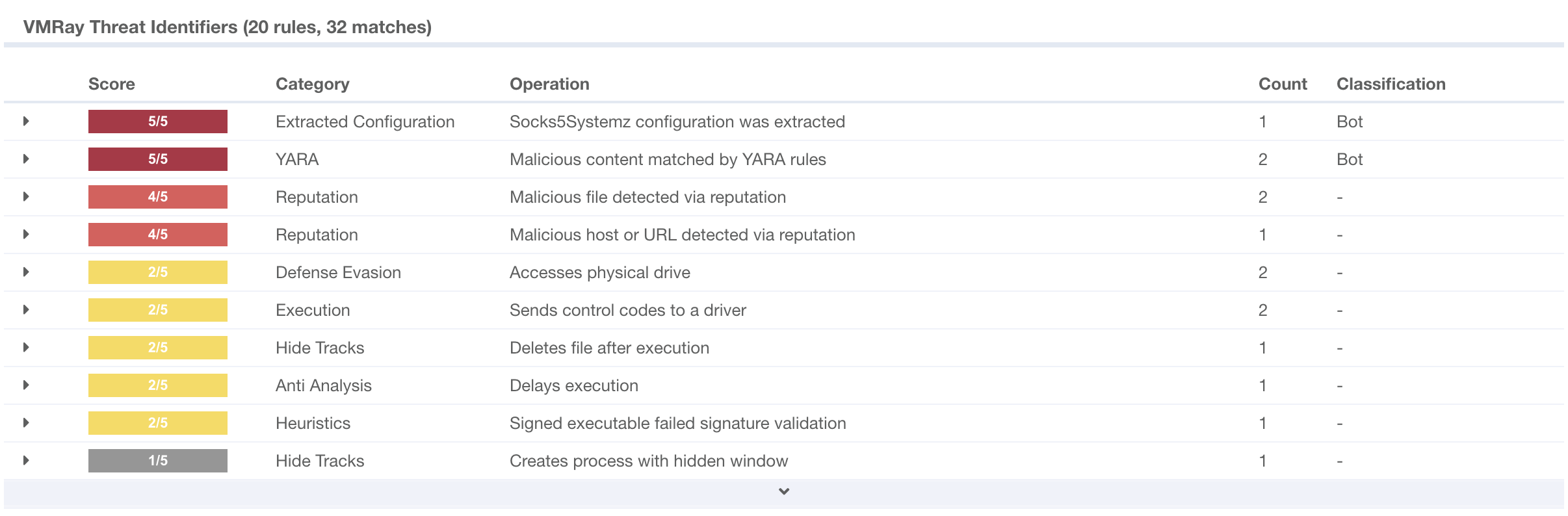
Last month, we introduced powerful new YARA rules specifically designed to detect Socks5Systemz, a malicious proxy-for-hire software. Building on this foundation, we’re excited to introduce Configuration Extraction as an additional vector for detection in this malware family.
What is Configuration Extraction?
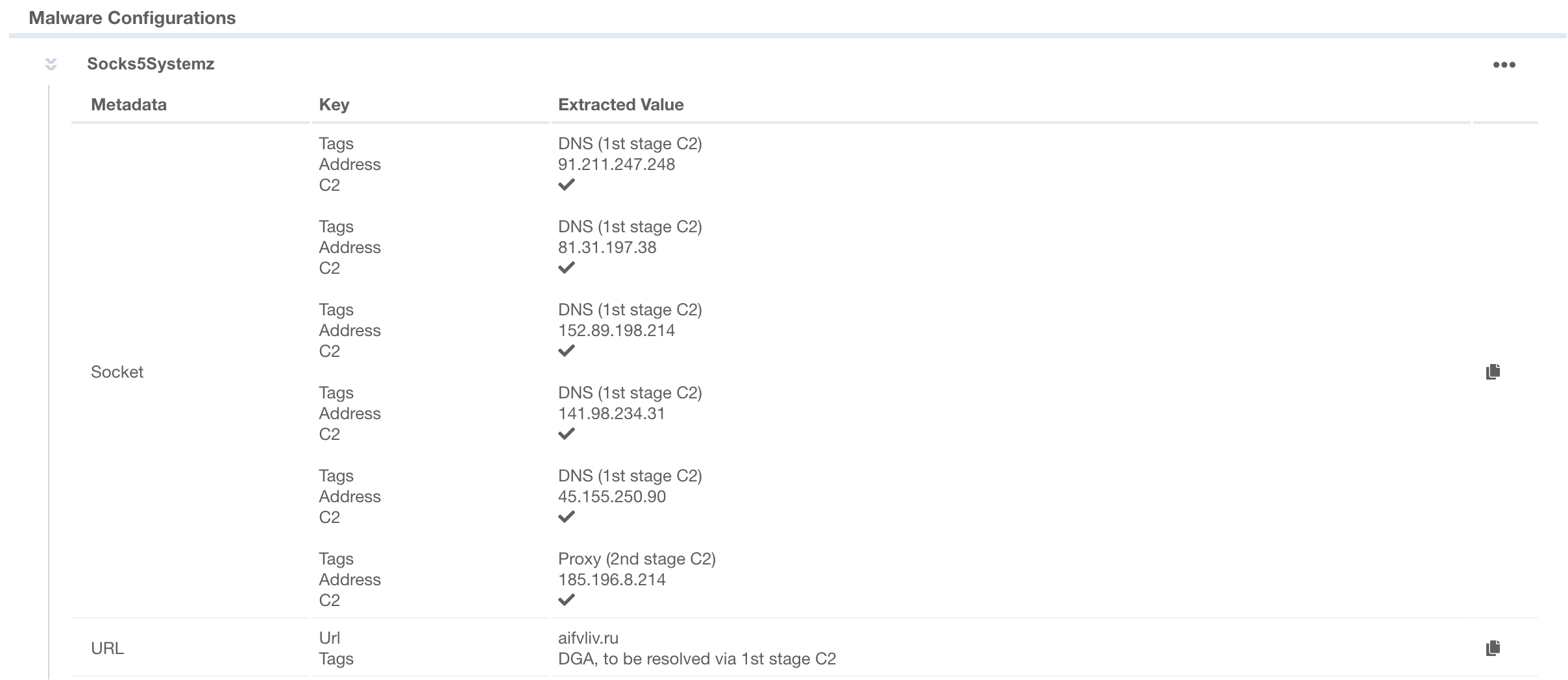
Configuration Extraction is a crucial technology in the fight against cyber threats. It involves identifying and extracting the key details embedded within malware that dictate its behavior, such as command-and-control (C2) server addresses, encryption keys, and other critical parameters. By uncovering these configurations, we can classify and attribute ongoing attacks with greater precision, even when the C2 server is unresponsive.
How it works?
All of our Platform products are equipped with automated Configuration Extraction capabilities. This feature enables the VMRay Platform to automatically capture and extract malware configurations based on the specific malware family. The entire process is automated, delivering actionable insights that can be immediately applied in threat response. The extracted configurations are included in the Analysis Report and are available for download in the standard MWCP JSON format. Additionally, these configurations enhance the generated Indicators of Compromise (IOCs), such as C2 server domains and IP addresses.
With our latest updates, we’ve expanded our capabilities to include configuration extraction for Socks5Systemz. We now offer comprehensive coverage for this active malware family, combining both YARA-based detection and in-depth configuration extraction.
In August 2024, we’ve made several improvements to the Smart Link Detonation (SLD) mechanism in our Platform products. If you haven’t read about it yet – SLD is a feature that enables the automatic evaluation and detonation of appropriate hyperlinks in document and email samples. This time, we’ve added new detonation rule, which allows for even greater capability of this feature to capture malicious URLs.
New SLD rule for URLs pointing to files hosted using GitHub comments
As cyber threats continue to evolve, malicious actors are increasingly exploiting trusted platforms like GitHub to spread malware. An alarming trend has emerged: the use of GitHub comments to distribute malicious content. In response, we introduced a new Smart Link Detonation (SLD) rule designed to detect and neutralize URLs pointing to files hosted in GitHub comments.
GitHub is a cornerstone of the global development community, widely trusted by developers, organizations, and enterprises for its secure, open-source platform. However, this very trust is being manipulated by cybercriminals who embed malicious URLs within GitHub comments, leveraging the platform’s credibility to bypass traditional security filters. These URLs, often unnoticed, can lead to the download and execution of malware, posing a significant risk to users.
The recent distribution of the Lua malware loader illustrates the severity of this threat. Attackers cleverly used GitHub comments within a Microsoft repository to upload malicious files as attachments. The links to these harmful files were then distributed through various channels, such as emails, chat messages, or other mediums. Because these links appeared to lead to a legitimate Microsoft repository on GitHub, users were more likely to trust the content and download the files. Once executed, these files could compromise the integrity of the targeted systems.
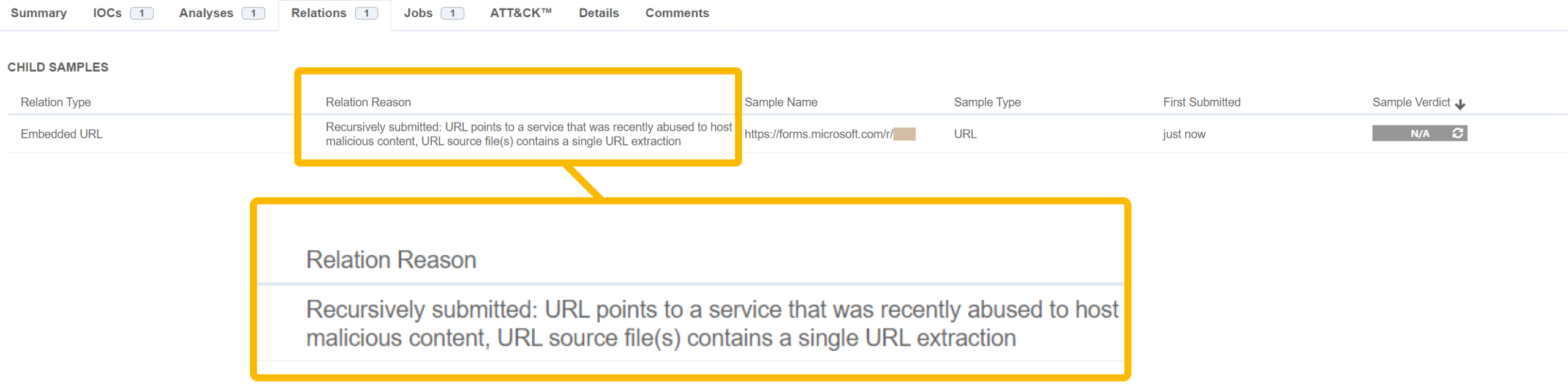
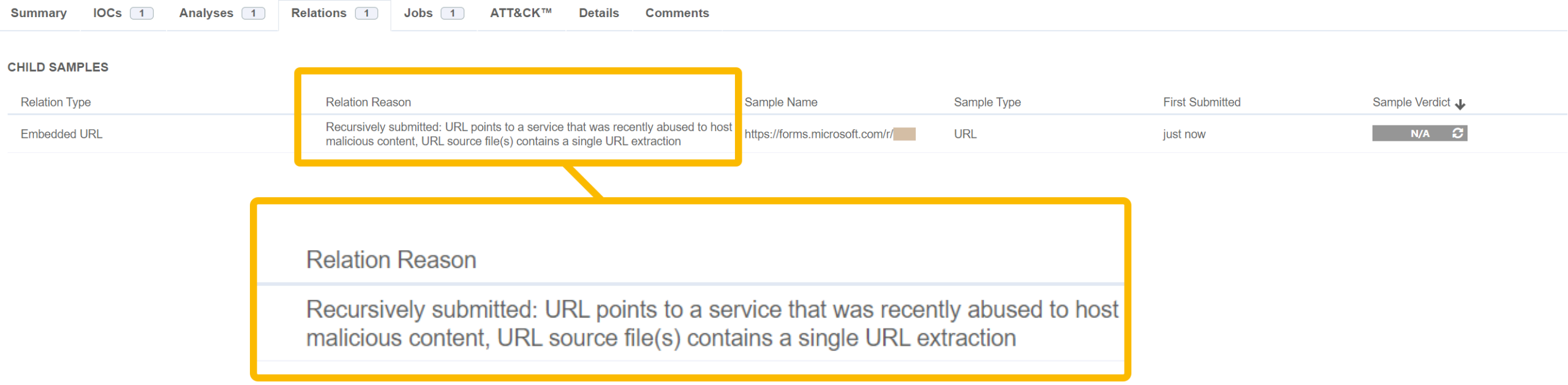
New SLD rule targets Phishing threats from forms.microsoft.com
In August, we’ve addressed a concerning trend involving the abuse of Microsoft’s forms.microsoft.com service in phishing campaigns. To counter this threat, we’ve enhanced our SLD mechanism with a new detonation rule that specifically targets URLs from this service, enhancing our ability to detect and neutralize phishing attempts before they reach users.
How forms.microsoft.com is being abused?
Forms.microsoft.com is a legitimate service provided by Microsoft that allows users to create forms, surveys, and quizzes. Unfortunately, cybercriminals have recognized the potential of this service as a phishing tool. By embedding malicious links within forms created on this platform, attackers can craft highly convincing phishing campaigns. These phishing forms often mimic legitimate login pages, tricking unsuspecting users into entering their credentials, which are then captured and used for unauthorized access to sensitive accounts and data.
Additionally, the forms.microsoft.com platform is designed to be user-friendly, allowing anyone to create and distribute forms quickly. This ease of use extends to attackers, who can create phishing forms with minimal effort.
New SLD rule for moengage.com redirects
Recently, we’ve addressed a tactic in which attackers abuse open redirects on trusted domains like moengage.com to facilitate phishing campaigns. In response to a customer report and a thorough investigation, we’ve enhanced our VMRay Platform by introducing a new Smart Link Detonation rule specifically designed to detect and analyze URLs containing redirects from moengage.com.
Moengage.com is a legitimate platform known for customer engagement and marketing automation. However, like many trusted services, it can be exploited by attackers. In this case, cybercriminals have taken advantage of an open redirect vulnerability within the moengage.com domain. By embedding phishing URLs within legitimate-looking moengage.com links, attackers can trick users into clicking on these links, believing they are being redirected to a safe and familiar site. Instead, the redirection leads to a malicious site designed to steal credentials or deploy malware.
To counter this emerging threat, we’ve developed a new SLD rule. This rule is specifically designed to analyze URLs from moengage.com that contain redirects, ensuring that any hidden threats are promptly neutralized.
Atomic stealer
We are happy to announce the latest addition to our security arsenal: a new YARA rule designed specifically to detect and neutralize AtomicStealer, a dangerous and evolving malware family that targets macOS users.
AtomicStealer, also known as AMOS Stealer, is a particularly sophisticated strain of malware that embeds itself within installers using the .dmg extension, the standard disk image format for macOS. This allows it to disguise itself as a legitimate application, leading unsuspecting users to download and execute it, thereby compromising their systems.
What makes AtomicStealer especially concerning is a recent update released by its developers in late 2023. This update introduced advanced payload encryption techniques, enabling the malware to bypass traditional detection methods and making it significantly harder to identify and eliminate.
Why macOS users should take notice?
For many years, macOS has been viewed as a relatively secure operating system, with a lower incidence of malware compared to other platforms. However, AtomicStealer serves as a stark reminder that no system is immune to attack. The AMOS stealer’s ability to evade conventional detection methods and its specific focus on macOS users marks a significant shift in the cyber threat landscape, underscoring the importance of maintaining up-to-date security measures.
A tailored YARA rule for AtomicStealer
To combat this emerging threat, we’ve integrated a new YARA rule into our VMRay Platform. This rule is crafted to detect and classify AtomicStealer, ensuring that our users are safeguarded against this malware. Here’s how the new rule enhances our security offerings:
- Accurate detection – the YARA rule is optimized to identify AtomicStealer variants, even those employing the latest encryption tactics.
- Effective classification – by accurately classifying the AtomicStealer family, we provide detailed insights that enable more targeted and effective mitigation strategies.
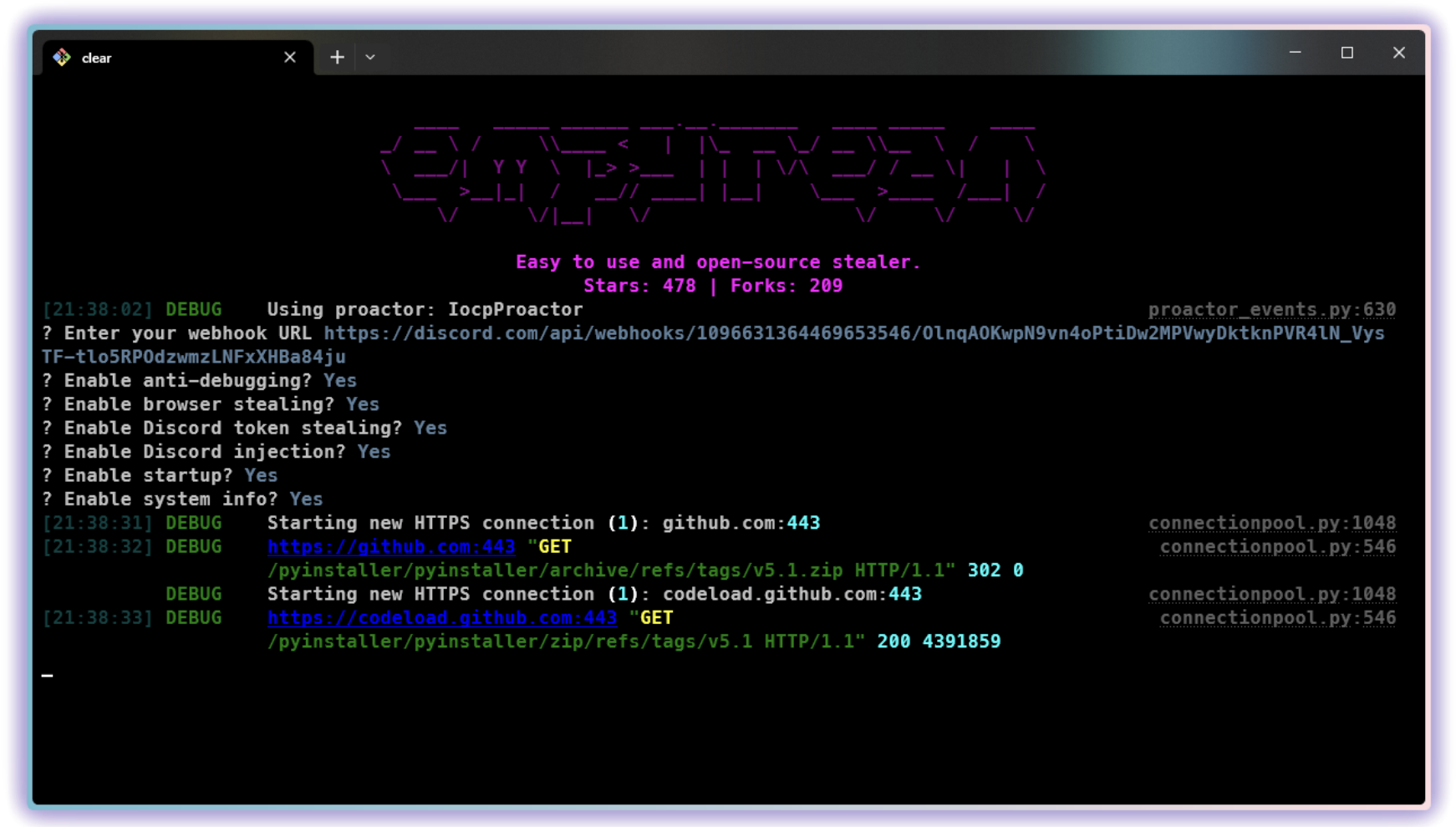
Empyrean stealer
Empyrean stealer, an open-source tool written in Python and readily available on GitHub. This stealer poses a significant risk, particularly due to its versatile feature set and ease of customization, making it an appealing choice for cybercriminals.
The Empyrean stealer is designed with the primary goal of exfiltrating sensitive information from infected systems. Below are some of the key features highlighted by its developers:
- Discord token information theft – the stealer specifically targets Discord tokens, which can be used to hijack accounts and engage in malicious activities under the guise of the victim.
- Browser data capture – it has the capability to extract a wide range of browser data, including cookies, passwords, bookmarks, and browsing history.
- System information gathering – Empyrean collects comprehensive system details, which can be used to further tailor attacks or evade detection.
- Anti-Debugging measures – to thwart analysis, Empyrean includes checks to determine if it is being executed in a virtualized or sandboxed environment.
- Persistence mechanism – the stealer ensures its persistence on an infected system by adding itself to the startup registry, allowing it to run automatically whenever the system is rebooted.
In response to the growing threat of the Empyrean stealer, we have developed and integrated a new YARA rule specifically designed to detect this malware.
Monti ransomware
In the previous month, we added a new YARA rule, specifically designed to identify and mitigate a new variant of the Monti ransomware, which has recently emerged as a significant threat.
Monti was first discovered in 2022 and initially caught the attention of cybersecurity experts due to its resemblance to the Conti ransomware. By mimicking Conti’s tactics and techniques, Monti quickly became a concern for many organizations. However, in 2023, a new variant of Monti ransomware was detected, and it has taken a different direction from its predecessor.
What’s new in the 2023 Monti variant?
These are just a few key highlights—there’s much more to this new threat!
- Linux targeting – unlike earlier versions, targetting both Windows and Linux, this new variant specifically targets Linux systems.
- Use of
--whitelistoption – one of the more notable features of this variant is the introduction of a--whitelistoption. This option allows the malware to exclude Virtual Machines that are running on the infected system from being encrypted. This could mean that the attackers are becoming more selective, possibly to avoid detection or to focus on specific targets. - Speaking of targets the new variant has shown a particular interest in targeting legal and governmental institutions.
- Divergence from Conti – while the original Monti ransomware showed striking similarities to Conti, the 2023 variant has diverged. The new version no longer mimics Conti, whose source code was leaked, making Monti a distinct threat on its own.
- New techniques for Virtual Machines – the ransomware now uses the
–type=softcommand instead of--type=hardto shut down virtual machines (VMs), indicating an evolution in its approach to disabling systems.
GrimResource
In June 2024, security researchers from Elastic Search identified a new attack vector called GrimResource. This discovery is significant as it reveals a novel malware infection technique that exploits the Microsoft Management Console (MMC) to achieve code execution within the MMC environment.
Hackers used to rely on a technique involving Microsoft Office files to spread their malware. However, when Microsoft made changes to block this method, cybercriminals began looking for new ways to attack. One of the methods they’ve found is using special types of files called MSC files, which work with the Microsoft Management Console (MMC). These files are typically used by system administrators to manage computers, but when altered by hackers, they can become a tool for launching attacks.
GrimResource is a new type of cyber attack that exploits a cross-site scripting (XSS) vulnerability through maliciously altered MSC files. When a victim unknowingly opens one of these compromised files, it triggers the XSS flaw, allowing the attacker to inject and execute arbitrary code on the target system. This exploitation can bypass many existing security measures, making it particularly dangerous. The ability of GrimResource to slip past defenses and potentially compromise entire networks highlights the severe threat it poses to systems with vulnerable configurations.
To counteract this emerging threat, we have developed and integrated a new YARA rule designed to trigger upon detection of an MSC file that abuses the XSS flaw.
We hope our constant research into new malware trends and the features we bring to our products help you confidently navigate the complex landscape of cybersecurity. Our latest updates bring powerful tools to your arsenal, with new YARA rules specifically targeting both established and emerging malware families. We’ve also enhanced Smart Link Detonation rules, giving you an even sharper edge in detecting phishing attempts. Plus, with the addition of two new VTIs, you can now assess the maliciousness of new threats with greater precision.
As we gear up for September, we’re excited to share more innovations in the coming weeks. Until then, stay vigilant, stay secure, and don’t forget to check out the latest Release Notes for Platform v.2024.4.0.
如有侵权请联系:admin#unsafe.sh