2024-9-10 16:17:1 Author: www.cleafy.com(查看原文) 阅读量:2 收藏
Key Points
- In June, the Cleafy Threat Intelligence team identified an unclassified Android banking Trojan. Subsequent analyses revealed that the malware was a variant of TrickMo, albeit with newly incorporated anti-analysis mechanisms.
- The mechanisms include using malformed ZIP files in combination with JSONPacker. In addition, the application is installed through a Dropper app that shares the same anti-analysis mechanisms. These features are designed to evade detection and hinder cybersecurity professionals' efforts to analyse and mitigate the malware.
- The sample analysis allowed us to trace the structure of the command-and-control (C2) server and the organisation of exfiltrated data, highlighting critical endpoints used to store and manage stolen information. By gaining access to these endpoints, we uncovered sensitive files, including credentials and pictures, exfiltrated from infected devices.
- The new findings underscore an enhancement in the Threat Actor’s capabilities. Although TrickMo retains the typical functionalities of an Android banking Trojan, the data collected from infected devices could enable the attacker to undertake additional actions, compromising the victim on multiple levels.
Stay ahead of emerging threats with Cleafy Prevent - advanced mobile threat detection.
Don't let sophisticated threats like TrickMo compromise your mobile app. Cleafy Prevent, powered by Cleafy LABS' globally renowned malware experts, delivers cutting-edge malware detection and device integrity monitoring to safeguard high-risk environments. Deploy robust, real-time protection with our lightweight SDK, designed for swift and seamless integration:
- Advanced malware detection: Protect your app with state-of-the-art malware detection.
- Device integrity monitoring: Ensure only secure, uncompromised devices interact with your app.
- Easy integration: Quickly deploy with a lightweight SDK for immediate, seamless protection.
Explore how Cleafy Prevent can fortify your mobile ecosystem with tailored, real-time security, backed by leading malware experts.
Introduction
Cleafy’s Threat Intelligence team observed an interesting Android malware sample in early June, initially classified as unknown. Further analyses revealed that the malware was a variant of the banking Trojan TrickMo, but with newly integrated anti-analysis features that complicated its classification.
TrickMo has a well-documented history of targeting Android devices. It emerged as part of TrickBot’s evolution, enabling TAs (Threat Actors) to expand the infection to the Android environment. The introduced anti-analysis mechanisms, which consist of a combination of different techniques known as malformed ZIP, JSONPacker, and dropper apps, highlight the malware's ever-evolving nature. The malware's purpose is to evade detection and hinder the efforts of cybersecurity professionals to analyse and mitigate this threat.
Nevertheless, the sample analysis also allowed us to trace the structure of the command-and-control (C2) server and the management of exfiltrated data, highlighting critical endpoints used to store the stolen information. We uncovered sensitive files, including credentials and pictures, exfiltrated from infected devices by gaining access to these endpoints.
What makes this discovery particularly noteworthy is the potential impact of the compromise on a victim user. A TA's actions with the exfiltrated data extend beyond banking fraud, potentially triggering identity theft scenarios. Moreover, as highlighted in this document, the exfiltrated data could be accessible to third parties without authentication, exposing the user to multiple attackers.
Ultimately, in the following sections, we will delve deeper into how a TrickMo infection can expose the user to multiple levels of risk, including banking fraud, identity theft, and data leakage.
Historical Overview
CERT-Bund identified TrickMo for the first time in 2019. The malware was designed to facilitate financial fraud by intercepting one-time passwords (OTPs) and other two-factor authentication (2FA) mechanisms crucial for secure banking transactions. Its primary targets were banking applications across Europe, particularly in Germany.
The malware represents an evolution of the TrickBot group’s malicious activities for the mobile domain. TrickBot, originally designed to target Windows systems, quickly became famous for its ability to steal banking credentials and other sensitive information. As cybersecurity defences improved, the TrickBot group developed TrickMo to target Android devices, leveraging and adapting the sophisticated techniques that made TrickBot successful. Over time, TrickMo has continually evolved, incorporating advanced obfuscation techniques and anti-analysis mechanisms to thwart detection and analysis efforts by cybersecurity professionals.
The malware’s key features include:
- Interception of One-Time Passwords (OTPs): it can intercept OTPs sent via SMS or generated by authenticator apps, allowing cybercriminals to bypass 2FA and authorise fraudulent transactions.
- Screen Recording and Keylogging: The malware can record the victim's screen and capture keystrokes, providing attackers with sensitive information such as login credentials and PINs.
- Remote Control Capabilities: TrickMo enables remote control of the infected device, allowing attackers to perform various actions, including initiating transactions and modifying account settings without the user's knowledge. With these capabilities, TrickMo can enable TAs to perform the On-Device Fraud (ODF) scenario, one of the most dangerous types of banking fraud.
- Accessibility Service Abuse: By exploiting Android's accessibility services, TrickMo can grant itself elevated permissions, manipulate user inputs, and capture data from other apps, making it particularly effective in targeting banking applications.
- Advanced Obfuscation Techniques: TrickMo continually evolves its obfuscation methods to avoid detection. It uses sophisticated code-hiding techniques to make it difficult for security researchers to analyse the malware.
- Anti-Analysis Mechanisms: TrickMo incorporates sophisticated methods to evade detection, including various techniques to detect and thwart virtualised environments and analysis tools.
The recent discovery of TrickMo's new anti-analysis mechanisms highlights the malware's continuous evolution. The following sections will discuss these techniques in detail, providing deeper insights into how TrickMo operates. Moreover, the analysed sample revealed characteristics of the malware that extend beyond the typical functionalities of a banking Trojan, possibly aligning with those of an infostealer.
Malicious App Overview
The malicious app is distributed via a dropper disguised as the Google Chrome browser. Upon installation, the app displays a warning message prompting users to update Google Play services.
If the user confirms the update, another APK containing the TrickMo malware will be installed. The new app is deceptively named “Google Services” and poses as a legitimate instance of Google Play Services. Upon launching, the app displays a window to ask the user to enable Accessibility services for the app. It guides the users through the process by instructing them to navigate to “Settings” and “Downloaded Services”. This social engineering tactic exploits the user's trust in familiar names and interfaces, thereby granting the malware the elevated permissions to carry out its malicious activities undetected.

Accessibility services are designed to assist users with disabilities by providing alternative ways to interact with their devices. These services can perform various actions, such as reading text aloud, automating repetitive tasks, and simplifying navigation. However, when exploited by malicious apps like TrickMo, these services can grant extensive control over the device.
This elevated permission allows TrickMo to perform various malicious actions, such as intercepting SMS messages, handling notifications to intercept or hide authentication codes, and executing HTML overlay attacks to steal user credentials. Additionally, the malware can dismiss keyguards and auto-accept permissions, enabling it to integrate seamlessly into the device's operations. These capabilities allow TrickMo to conduct financial fraud, making it extremely difficult to detect and remove from the infected device.
Anti-analysis Mechanisms
Dropper
Android droppers are applications used to install additional apps on the device. This type of application contains only one functionality, i.e. the update functionality, that may be abused by TAs. Through this functionality, TAs can deceive the user by proposing an update for the application, allowing the installation of a second, possibly malicious, application.
As noted in the previous paragraph, in this case, the dropper is disguised as a bogus Chrome Browser APK, which includes another APK infected with the TrickMo malware. This malicious APK is stored in one of its resources, specifically the file assets/base.apk.

Droppers can be highly effective in perpetrating attacks. Not only do they disguise themselves as legitimate applications, but they are also developed with minimal fingerprinting (even in terms of permissions requested during installation) to minimise their detection. Moreover, in this specific case, the analysed dropper employs the same anti-analysis protections discussed in the following paragraphs to further minimise detection.
Malformed ZIP
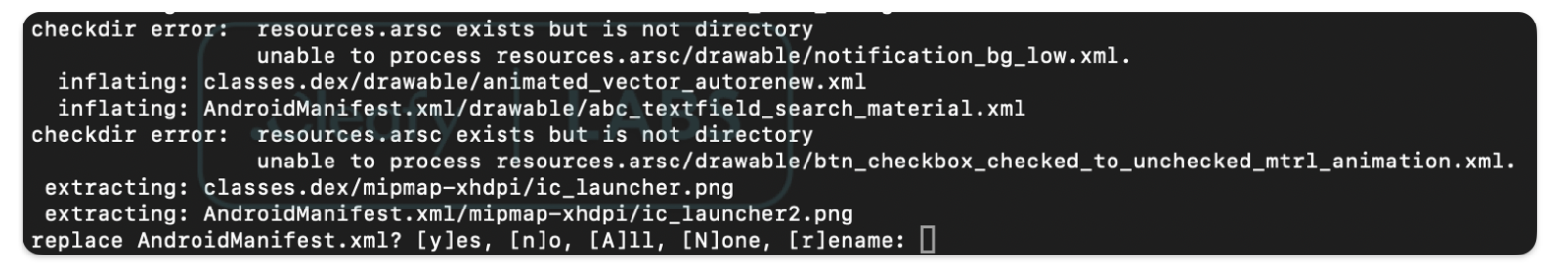
One of the recently introduced anti-analysis mechanisms employed by the latest TrickMo variant involves using malformed ZIP files. In this tactic, the APK file is manipulated by adding directories with the same names as crucial files, such as AndroidManifest.xml and classes.dex.

This clever obfuscation strategy can cause an unzip operation to overwrite these critical files, potentially hindering subsequent analysis. When security researchers or automated analysis tools attempt to extract and examine the contents of the APK, the malformed structure can lead to errors or incomplete extractions, significantly complicating the analysis process and providing TrickMo with an additional layer of evasion.

Despite this hindrance, the AndroidManifest.xml file can still be retrieved using apktool, even though the malformed ZIP technique can obstruct analysis performed by some of the most common tools, such as JADX. Apktool's ability to decompile and decode APK files allows researchers to bypass this obfuscation method and gain critical insights into the malware's structure and behaviour, especially after retrieving the Android Manifest File. The latter reveals a set of suspicious permissions commonly associated with Android banking trojans. These permissions enable the malware to perform various malicious activities, including intercepting communications, accessing sensitive data, and manipulating device settings. Moreover, the file contains several suspicious activities, services, and receivers related to the package dreammes.ross431.in.

Unpacking
Despite multiple references within the application Manifest File to the package dreammes.ross431.in, this package is not present in the original APK. This absence suggests that the application is packed, a tactic commonly employed to conceal malicious components. Specifically, the packer used in this instance is identified as JSONPacker, which effectively hides the malicious DEX file containing critical code for various actions, services, and receivers.
When the app is launched on the device, the payload is unpacked through the class com.turkey.inner.Uactortrust, where the malicious DEX file is retrieved, decrypted, and loaded from the path /data/user/0/dreammes.ross431.in/app_inflict/wF.json.

Malware Features
The unpacked DEX file reveals the app's malicious functionalities. The malware can respond to a series of commands issued by the C2 server, allowing it to perform all the operations necessary to carry out financial fraud and other malicious activities, such as:
- Intercepting SMS messages by changing the default SMS application.
- Retrieves all photos stored on the device.
- Record screen activity and enable remote access and control.
- Perform clicks and gestures on the device.
- The complete list of commands is reported in the Appendix of this document.
Particularly interesting is the functionality of performing HTML Overlay Attacks. The malware retrieves the list of the applications installed on the infected device; then, the C2 server, after receiving the list, will send a command labelled “SaveHtml” accompanied by the package name and an overlay URL. The URL will point to an HTML file later used as an HTML Overlay Injection page.

Command-and-Control (C2) Server Communication
The analysed TrickMo Android banking trojan communicates with its command-and-control (C2) server using the HTTP protocol, specifically through a domain extracted from the malware configuration. This communication channel relays commands from the attackers to the infected device and exfiltrates sensitive data. Through this C2 server, the attackers can manage the malware's activities, receive stolen information, and issue new instructions to the infected devices, ensuring continuous and dynamic control over the compromised systems.

The initial message sent to the C2 server consists of an HTTP POST request to the endpoint /c. The body of this request contains a JSON file with detailed information about the infected device, including the phone number, model, and a comprehensive list of apps installed on the device. This information enables the attackers to tailor their malicious activities to the specific characteristics of each infected device, enhancing the effectiveness of their campaigns and ensuring continuous and dynamic control over the compromised systems.

Subsequently, the malware transmits another message to the C2 server to request the Clicker configuration.
Clicker configuration
The Clicker configuration showcases a sophisticated method of controlling an infected device via the Accessibility Service. To exploit it, the malware combines a class named Clicker with a clicker.json file saved in the assets directory. The file can also be updated by downloading new versions from the C2 server.

The JSON file contains the package names on which the Accessibility service operates an “auto-click” functionality. For example, one operation that may be performed is automatically accepting permissions for the malware on the device.

This configuration is crucial as it enables the execution of operations that exploit the Accessibility Service, allowing the attackers to perform automated actions on the device. The Clicker configuration targets a mix of system applications and utility services, including settings, package installers, and system managers. This indicates TrickMo's intent to gain profound control over device configurations by disabling security features and enabling permissions without user consent.
The actions defined in the Clicker.json file can be categorised into several types of payloads:
- Blocking system updates (e.g., Samsung Update).
- Disabling security features.
- Preventing the uninstallation of certain apps.
The languages and text filters in the JSON configuration suggest a focus on German and English-speaking users. Phrases like "Aktivieren," "App-info," and "Deinstall" indicate that the malware is designed to interact with devices set to German, hinting at potential victim geolocations in Germany, Austria, or Switzerland. Similarly, English phrases such as "Activate," "App info," and "Uninstall" suggest that the malware also targets devices set to English, indicating potential victims in the United Kingdom and the United States.

Moreover, the same infrastructure leveraged for controlling the botnet and retrieving additional configurations is also employed to store the data exfiltrated from the victim’s device, including logs, credentials, and photos. The following section discusses the specifics of the information that can be extracted in depth. The analysis revealed that the C2 server does not provide an authentication mechanism to access the obtained data, meaning third parties could also access it. Although a login page is provided, the data is accessible by knowing specific endpoints on the server, which are easily guessable, thereby further exposing the victims.
Data leak from C2 Server
This chapter delves into the numerous misconfigurations in the Command and Control (C2) infrastructure leveraged by TrickMo. These misconfigurations, if exploited, provide access to a significant portion of the data exfiltrated from the infected devices of victims targeted by TrickMo distribution campaigns. The data stored within the C2 server encompasses a wide range of sensitive information, including personal photos, documents, connection logs, credentials, and more, totalling 12 GB of files. This analysis underscores the critical security lapses in the C2 setup, which not only jeopardise the privacy of victims but also highlight the operational deficiencies of the TAs behind TrickMo.
Our in-depth analysis of the command-and-control (C2) server unveiled several critical endpoints that play pivotal roles in the malware's operation.
One of the folders contains a list of IP addresses presumably associated with the compromised devices. This list enables the attackers to keep track of infected devices and manage their operations more effectively.

Another folder reveals a list of subdirectories identified by numerical filenames. Each subdirectory contains detailed logs of operations performed on the compromised devices, providing the attackers with a comprehensive record of their malicious activities. These logs can include information on intercepted communications, executed commands, and other actions carried out by the malware, further highlighting the sophisticated level of control the attackers maintain over the infected devices.

Furthermore, the C2 provides HTML files used in HTML overlay attacks. These files include deceptive login pages for various services, including bank accounts such as ATB Mobile and Alpha Bank and cryptocurrency platforms like Binance. By displaying these overlays, TrickMo can effectively phish for user credentials, enabling attackers to gain unauthorised access to sensitive accounts.

A third endpoint is responsible for storing CSV files that contain captured username and password combinations. This endpoint serves as a centralised repository for the stolen credentials, allowing attackers to access a wealth of sensitive login information. This organised storage facilitates using these credentials in further fraudulent activities, such as unauthorised access to financial accounts and identity theft.

Finally, a specific folder is dedicated to storing ZIP files containing all the images extracted from the compromised devices. These images include potentially sensitive personal pictures, identification documents, and financial information. Attackers can use this data to gather further intelligence about the victims, significantly compromising their privacy and increasing security risks for the affected individuals.

Hence, the data leak from TrickMo's Command and Control (C2) infrastructure exposes a wealth of sensitive information. This breach amplifies the threat of further exploitation by TAs or third parties. When a TA gains access to credentials and sensitive photos, the range of potential malicious activities expands significantly. With user credentials, including usernames and passwords, the TA can easily infiltrate various online accounts, such as banking, email, social media, and other personal services. This access enables direct financial theft, unauthorised money transfers, and fraudulent purchases. Compromised email accounts can also be leveraged to reset passwords for other services, further extending the attacker's reach.
Sensitive photos, such as images of passports, credit cards, and personal identification documents, can be used to commit identity theft. The TA can create fake identities or verify stolen accounts to bypass security checks. These photos can also be exploited for Social Engineering attacks, blackmail, or extortion. For instance, personal or compromising pictures can be used to coerce victims into paying ransom or performing actions beneficial to the attacker.
Furthermore, combining credentials and sensitive photos enhances the TA's ability to perform highly targeted phishing attacks. Using personal information and images, the attacker can craft convincing messages that trick victims into divulging even more information or executing malicious actions. Exploiting such comprehensive personal data results in immediate financial and reputational damage and long-term consequences for the victims, making recovery a complex and prolonged process.
Conclusions
The analysed TrickMo sample and its ability to intercept communications, manipulate device settings, and access sensitive data underscore the advanced nature of this sample and the persistent efforts of its creators to evade detection (e.g., malformed ZIP and JSONPacker) and enhance its capabilities. However, this analysis also gave us more insights about the C2 server, which revealed the structure and organisation of exfiltrated data, highlighting critical endpoints that store and manage stolen information.
Moreover, the TAs behind TrickMo made multiple OPSEC mistakes, publicly exposing part of the exfiltrated data (including pictures exfiltrated from infected devices by gaining access to these endpoints). These images contained valuable information such as passports, credit card details, and other personal documents, demonstrating the extent of data compromise and the level of control the attackers have over the infected devices.
This shallowness, leaving leaked data publicly available, should not be undertaken because it exposes victims to multiple threats that span from identity theft, fraud, extortion, etc. However, it's worth mentioning that the impact of that information is not limited to cyberspace but could also involve a physical threat, with even more risks. Moreover, it's crucial to highlight that the exposed information can be exploited by various TAs who may access the leaked data for purposes entirely different from the original intent (banking fraud in the case of TrickMo). These bad actors can leverage the information for various malicious activities, each potentially more damaging than the last.
Under these circumstances, it is crucial to re-evaluate the risks associated with such threats, emphasising the consequences of these actions in the medium and long term rather than focusing on the near future. This comprehensive assessment underscores the importance of robust data protection and systems with enhanced predictive capabilities to prevent malicious actions arising from such threats.
Appendix 1: Malware Commands
| ID | Command | Description |
|---|---|---|
| 1 | Server | Configures the C&C (Command and Control) server details. |
| 2 | Interval | Sets the frequency at which the malware communicates with the C&C server. |
| 3 | DeleteAll | Deletes all data or traces of the malware from the infected device. |
| 4 | SelfDestroy | Triggers the self-destruction of the malware to remove itself from the device. |
| 6 | SetSmsApp | Changes the default SMS application on the infected device. |
| 7 | SetPhone | Modifies phone settings or configurations. |
| 8 | SendSms | Sends SMS messages to specified numbers. |
| 9 | ShowPopup | Displays a popup message on the infected device. |
| 10 | ActiveInterval | Sets the active time interval for the malware's operations. |
| 11 | RequestInfo | Requests specific information from the infected device, such as contacts or messages. |
| 12 | GetAllPhotos | Retrieves all photos stored on the infected device. |
| 13 | GetPhoto | Retrieves a specific photo from the infected device. |
| 14 | VNC | Enables remote access and control of the infected device using Virtual Network Computing (VNC) technology. |
| 15 | ScreenRecord | Records the screen activity of the infected device. |
| 16 | LoadModule | Downloads and executes additional modules or payloads. |
| 17 | StartOrInstall | Starts a specific application or installs a new one on the infected device. |
| 18 | SetClickerConfig | Configures the clicker settings for automated clicking actions. |
| 19 | ShowDialog | Displays a dialog box on the infected device. |
| 20 | ShowNotification | Shows a notification on the infected device. |
| 21 | SetVars | Sets variables or parameters for the malware's operation. |
| 22 | ReadSms | Reads SMS messages from the infected device. |
| 23 | RequestIgnoreBatteryOptimizations | Requests the device to ignore battery optimization settings for the malware. |
| 24 | ShowCover | Displays a full-screen cover to hide malicious activities. |
| 25 | UnlockScreen | Attempts to unlock the device's screen. |
| 26 | DisableNotifications | Disables notifications to prevent the user from seeing alerts about the malware. |
| 27 | PressHome | Simulates pressing the home button. |
| 28 | PressBack | Simulates pressing the back button. |
| 29 | OpenSetNewPasswordSettings | Opens the settings to set a new password on the device. |
| 30 | SaveHtml | Saves HTML content to the device. |
| 31 | PressRecents | Simulates pressing the recents button to show recent apps. |
| 32 | OpenPowerDialog | Opens the power dialog for options like shutdown or restart. |
| 33 | KillBackgroundProcesses | Terminates background processes running on the device. |
| 34 | RequestOverlayPermission | Requests permission to draw over other apps. |
| 35 | RequestPermissions | Requests additional permissions from the user. |
| 36 | OpenGoogleProtectSettings | Opens the settings for Google Play Protect. |
| 37 | TakeScreenshot | Captures a screenshot of the device's display. |
| 38 | Update | Updates the malware to a newer version. |
| 39 | OpenAccessibilitySettings | Opens the accessibility settings menu. |
| 40 | GetAllVideos | Retrieves all video files stored on the infected device. |
| 41 | GetVideo | Retrieves a specific video from the infected device. |
| 42 | OpenNotificationSettings | Opens the notification settings menu. |
| 43 | OpenAppSettings | Opens the settings for a specific application. |
| 44 | SendUssd | Sends a USSD code (Unstructured Supplementary Service Data) to perform actions like balance checks or top-ups. |
| 45 | ReadCalls | Reads the call logs from the infected device. |
| 46 | ChangeIcon | Changes the icon of the malware to disguise its presence on the device. |
Appendix 2: Indicator of Compromise (IOCs) / TLP-AMBER
We have identified several Indicators of Compromise (IOCs) that provide critical insights into the TA infrastructure and behaviour. However, we have decided to keep these IOCs confidential due to significant misconfigurations within the Command and Control (C2) infrastructure leveraged by TrickMo. This decision stems from the potential risk that additional malicious actors could exploit these vulnerabilities to harvest a substantial amount of sensitive information from the compromised victims within the botnet.
While we acknowledge that withholding IOCs might not be well-received within the cybersecurity community, we prioritise the privacy and security of affected individuals. Consequently, we will disseminate these IOCs under a TLP-AMBER protocol exclusively to trusted entities such as law enforcement agencies, reputable CERTs, and banking institutions.
Researchers and analysts recognised as trusted entities within the community can request access to the IOCs by contacting us at [email protected]. By adopting this cautious approach, we aim to mitigate further exploitation risks while ensuring that critical threat intelligence is shared responsibly with those who can act upon it effectively.
如有侵权请联系:admin#unsafe.sh