
2024-9-10 18:40:3 Author: securityboulevard.com(查看原文) 阅读量:1 收藏

Are you confident that shifting security left in your software development lifecycle is enough to protect your organization? Over the last few years, many CISOs and AppSec professionals have embraced the "shift-left" philosophy, integrating security earlier in the development process. But is this approach truly comprehensive, or has it become a buzzword that oversimplifies the complexities of modern software security?
In this article, we will share insights from cybersecurity expert Chris Romeo and how he challenges the sufficiency of shift-left, urging security leaders to rethink their strategies. We'll challenge Chris' perspective and provide insights into why a more holistic approach to security might be necessary to truly secure your applications. Dive right in!
💡
This article is based on our conversation with Chris on the Elephant in AppSec - the podcast that explores, challenges, and boldly faces the AppSec Elephants in the room.
Chris Romeo's Background
Chris has 26 years of experience in cybersecurity, having worked for 11 years at Cisco, founded his own security education company, Security Journey, and now Devici, an AI-infused threat modeling tool for development teams.
Chris is a sought-after speaker at numerous global application security conferences. He is also the author of a weekly newsletter, The Reasonable AppSec, where he shares the top 5 security articles worth your time.
Chris hosts not one but three security podcasts: the Threat Modeling Podcast, SecTablePodcast, and my personal favorite, Application Security Podcast. He is never afraid to freely express his opinions, sometimes quite strong ones, like "DAST is dead".
Watch the full podcast below:
The Origins and Evolution of ‘Shift-Left’
The shift-left approach was born out of a simple yet powerful idea: by addressing security earlier in the development process, organizations could prevent vulnerabilities from being baked into the final product.
This philosophy quickly gained traction, transforming into a widely accepted best practice across the industry. Over time, however, shift-left evolved from a practical strategy into a marketing buzzword, often touted as a cure-all solution for software security. Chris, with his decades of experience, cautions against this oversimplification, reminding us that shift-left is only one piece of a much larger puzzle.
Chris’s Critique: The Marketing Trap
Chris Romeo is particularly critical of how the term "shift-left" has been co-opted by vendors and marketers.
"Shifting left has just become a marketing term. It doesn't actually mean anything anymore." – Chris Romeo
He points out that some companies have gone so far as to push the concept of "shifting everywhere," a term that, in his view, dilutes the original intent of the shift-left philosophy to the point of meaninglessness. This marketing-driven approach, he warns, risks creating a false sense of security among organizations that might believe they’ve addressed all their security needs simply by adopting shift-left practices.
DAST: Dead or Alive?
In the podcast, Chris Romeo shares his perspective on Dynamic Application Security Testing (DAST). He acknowledges the challenges and limitations of DAST tools, particularly in modern, API-driven applications with JavaScript front-ends. Romeo critiques DAST for often failing to provide meaningful insights, especially when the applications are slimmed down and designed with minimal attack surfaces.
He recounts a personal experience where his company was required to use a DAST tool to scan an application. Despite the simplicity and security measures already in place, the DAST tools he tried struggled to find significant issues, often reporting trivial findings like the lack of a secure cookie flag on a GDPR consent cookie. This experience led Chris to question the return on investment of DAST tools, especially when they cannot efficiently scan modern applications or integrate seamlessly into DevOps pipelines.
"There's not a DAST tool around that can run inside of a pipeline at scale, at speed, without slowing things down." – Chris Romeo
However, Romeo is not entirely dismissive of the concept behind DAST.
When we challenged him on the podcast, he suggested that for DAST to be more effective, it would need to be faster, capable of running within a pipeline without slowing it down, and more focused on scanning specific changes rather than entire applications.
"For me, what is the perfect DAST? It's something that can run in the pipeline, that can run at speed and scale, that can pinpoint a single change and basically be the technology behind IAST." – Chris Romeo
He highlights that Interactive Application Security Testing (IAST) might be a path forward, as it offers the capability to monitor the data flow within an application, identifying vulnerabilities as they occur.
"API security tools are kind of taking the place of what DAST was supposed to do." – Chris Romeo
The Limitations of Shift-Left
While shifting security left is undoubtedly beneficial, Chris argues that it’s not a panacea. One of the major limitations of the shift-left approach is its focus on the early stages of development, often neglecting security concerns that arise post-deployment.
💡
Many security threats only emerge once the software is in the wild, interacting with real-world users and environments.
These runtime issues require ongoing vigilance and tools designed to monitor and address threats that weren’t apparent during development. While runtime protection is often cited as a solution, it's not the only answer.
"What threat modeling can do though is it can help you to eliminate rework or at least cut it down significantly because you’re finding those security and privacy challenges while you’re doing the design." – Chris Romeo
Another efficient approach is to ensure robust security measures that extend beyond deployment without relying on traffic monitoring. Escape provides such a solution, offering continuous protection even after deploying code. By integrating security at every stage of the development lifecycle, Escape ensures vulnerabilities are managed effectively post-deployment without the need for real-time traffic analysis.
Chris also highlights the challenge of integrating shift-left practices into complex, modern development workflows.
"We have microservices, continuous deployment, and all these other practices that make it difficult to integrate security early in the process without slowing things down." – Chris Romeo
The complexity of today’s software environments means that early security measures, while crucial, are insufficient on their own.
Going Beyond Shift-Left
"We need to stop treating shift-left as the ultimate solution." – Chris Romeo
As Chris expresses, it is important to expand our view of application security and look at methods that are more comprehensive and secure than just a "shift-left" approach.
Introducing A Comprehensive Security Approach
Romeo advocates for a more holistic approach to software security, one that goes beyond simply shifting left. This comprehensive strategy integrates security from design and coding to testing, deployment, and beyond.
"We need to embrace the concepts of building security and privacy in from the beginning." – Chris Romeo
This can be related to integrating the 5 steps of the Vulnerability Management Lifecycle—Discover & Assess, Prioritize, Remediate & Mitigate, Validate & Monitor, and Report & Improve—across the entire software development process.
This lifecycle approach supports continuous security by identifying and managing vulnerabilities at every stage, even after deployment.
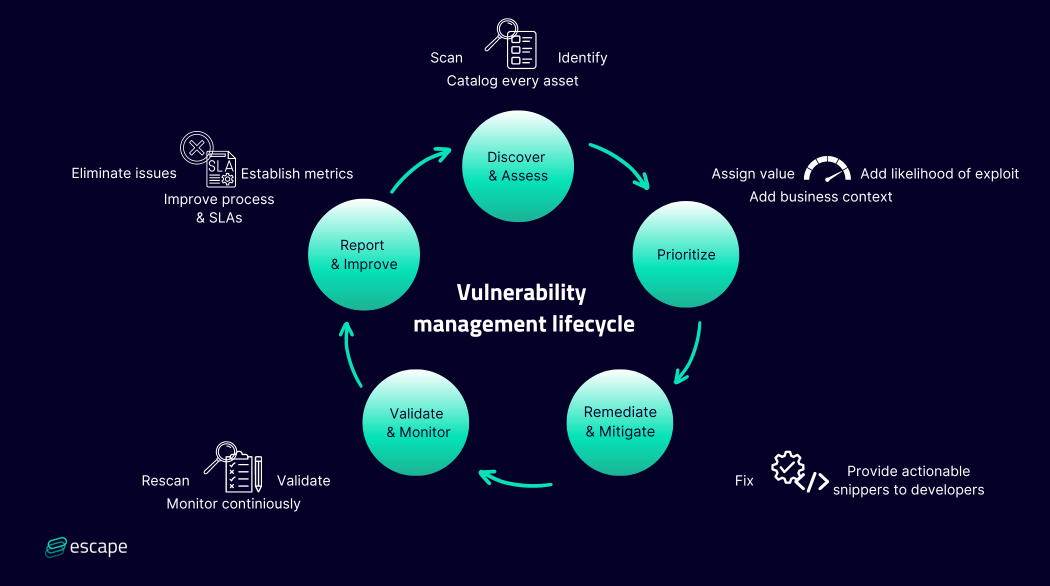
Chris suggests that this approach should also involve close collaboration between development and security teams, ensuring that security is a shared responsibility across the organization.
"What you'll find is a developer knows the system 10 times better than I do as a security person." – Chris Romeo
This is specifically applicable when it comes to threat modeling:
"I think of threat modeling as something that I want developers to be doing when they’re performing design… What threat modeling can do though is it can help you to eliminate that rework or at least cut it down significantly." – Chris Romeo
Best Practices
For organizations looking to adopt a more comprehensive security strategy, Chris Romeo offers several practical recommendations:
- Ensure continuous education for both developers and security professionals.
- Get tools that provide visibility into the entire software lifecycle, not just the development phase.
- Understand the difference between genuine security practices and marketing-driven buzzwords.
"That's what I've always found was missing: the foundational knowledge is just not there." – Chris Romeo
Conclusion
Chris Romeo’s insights serve as a crucial reminder that while shift-left is a valuable approach, it’s not a silver bullet.
Security requires a holistic, lifecycle-wide approach that goes beyond early-stage interventions. By integrating security into every aspect of software development and remaining vigilant against emerging threats, organizations can build more robust and resilient systems.
"I’ve been around for 26 years. […] We’re in a totally different space now. […] We’re in a better place." – Chris Romeo
You may also be interested in:
- Vulnerability Management Lifecycle: A Comprehensive Guide
- DAST is dead, why Business Logic Security Testing takes center stage
- Why does DevOps recommend "Shift left" principles?
- Securing GraphQL Endpoints in the Full Development Lifecycle
*** This is a Security Bloggers Network syndicated blog from Escape - The API Security Blog authored by Alexandra Charikova. Read the original post at: https://escape.tech/blog/why-shift-left-isnt-good-enough-our-conversation-with-chris-romeo/
如有侵权请联系:admin#unsafe.sh
