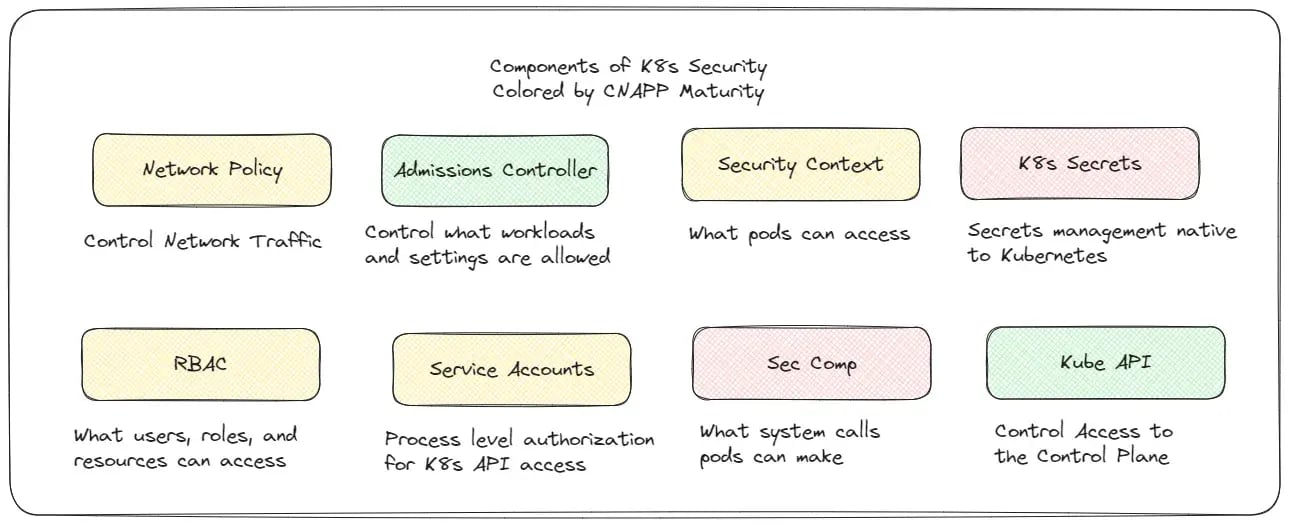
Today, we’re delighted to share Uptycs Kubernetes Risk Insights—our latest enhancement to elevate your security posture. This new feature correlates runtime security findings, like cryptominers, exploitable vulnerabilities, and more, directly to misconfigurations in your cloud and Kubernetes control plane, such as internet exposure and excessive permissions. Organizations have long taken a siloed approach to addressing Kubernetes security risks in their environment through static compliance and misconfiguration scanning or image vulnerability scanning. However, Uptycs intelligently combines insights and presents attack paths to crown jewel assets and presents a unified risk score for every container. This enables security teams to triage and prioritize the most critical risks based on runtime and Kubernetes context that assesses the likelihood of a breach and the potential severity of a breach for every container workload. The move to Kubernetes across enterprises has been massive, with a recent CNCF survey showing over 95% of organizations using Kubernetes or planning to do so. Kubernetes has its superpowers when it comes to fault-tolerant orchestration and in-built controls inside the cluster for RBAC, governance, networking, and more. Kubernetes security is crucial as the platform’s complexity presents a wide attack surface, often exploited by recent breaches including cryptomining attacks and privilege escalation. However, with greater control comes greater risk and the complexity of Kubernetes security presents a wide attack surface which has shown to be wildly exploited by recent breaches including the following: With these types of attacks, the following is clear: Your CNAPP needs to go a level deeper than traditional agentless/image scanning for Kubernetes security: Fellow analyst James Berhoty summarizes this nicely in terms of Kubernetes security maturity in the CNAPP Market: As seen above, factoring all these insights in isolation is extremely hard and creates a siloed approach where key attack paths and critical risks are missed. Uptycs takes the heavy lifting by correlating insights from runtime, Kubernetes control plane, audit logs, and cloud control plane. These are mapped to breach likelihood and severity and turned into a single risk assessment score, which significantly enhances Kubernetes security. These include the following: Breach Likelihood: Runtime Threat Detections: such as reverse shells, cryptominers and more with correlation to potentially malicious Kubernetes control plane activity and code commits in the developer pipeline. Internet Exposure: While many CNAPP solutions look at Kubernetes load balancers, node ports, and services as well as cloud security groups, NACLs, the missing ingredient is looking at Network Policies which act as means of defense against exposure and lateral movements. If your risk engine is not telling you if a network policy is active, you’re missing key context. Uptycs not only provides visibility into the full internet exposure path and attack path to crown jewels in the cloud, but integrates with Cilium network policies to show you which network policy is active and whether it is causing internet exposure risk or not. Pod Security Context/Misconfigurations: If a pod is running as root or has host network access, it has the ability to escalate into the cloud and get access to crown jewels such as S3 buckets with data. Vulnerabilities: Exploitable vulnerabilities with packages that are in-use by running processes. Malware: Images detected with cryptominers and ransomware that are deployed. Impact severity: RBAC: With identity being a key attack vector for escalation of privileges and lateral movements, it is extremely important to understand excessive permissions in the cluster. Many clusters also come with default service accounts which are great for dev/test but in production are very risky and when exploited can lead to loss of data and open attack paths. Exposed Secrets: Credentials that are exposed are more likely to be exploited to access sensitive information and data. With this unified risk calculation, security teams can prioritize the most critical risks on a daily basis across their container and Kubernetes inventory. While this blog focuses on risk prioritization, here is a glimpse of what Uptycs can enable for security teams to mitigate risks in real-time and prevent future threats and risks from happening: Why Uptycs For Kubernetes Risk Prioritization
 Source: The Kubernetes Gap in CNAPP
Source: The Kubernetes Gap in CNAPPUptycs Kubernetes Risk Prioritization
Step 1: Risk Calculation






Step 2: Risk Prioritization

Step 3: Risk Remediation and Prevention

Kubernetes Security with Unified Risk Insights | Uptycs Blog
2024-9-10 21:21:14 Author: www.uptycs.com(查看原文) 阅读量:7 收藏
2024-9-10 21:21:14 Author: www.uptycs.com(查看原文) 阅读量:7 收藏
文章来源: https://www.uptycs.com/blog/kubernetes-security-with-uptycs
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh