 Joe Ariganello VP of Product Marketing
Joe Ariganello VP of Product Marketing
Joe is the VP of Product Marketing at MixMode. He has led product marketing for multiple cybersecurity companies, with stops at Anomali, FireEye, Neustar and Nextel, as well as various start-ups. Originally from NY, Joe resides outside Washington DC and has a BA from Iona University.
A recent joint advisory from the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) has highlighted a significant threat to critical infrastructure sectors across the United States: RansomHub ransomware. This variant, previously known as Cyclops and Knight, has been steadily gaining traction and has successfully compromised a wide range of organizations.
RansomHub: A Growing Threat in the RaaS Landscape
Ransomware-as-a-Service (RaaS) has become a significant concern in the cybersecurity landscape. RaaS providers develop and maintain ransomware tools, then “rent” them out to affiliates who handle deployment and extortion. RansomHub operates under this model, attracting seasoned affiliates with experience in deploying other notorious RaaS variants like LockBit and ALPHV.
Here’s what makes RansomHub particularly worrisome:
- Target-Rich Environment: Since its emergence in February 2024, RansomHub has managed to encrypt and steal data from at least 210 victims. These victims span a diverse range of critical infrastructure sectors, including:
- Water and Wastewater
- Information Technology
- Government Services
- Healthcare
- Emergency Services
- Food and Agriculture
- Financial Services
- Commercial Facilities
- Critical Manufacturing
- Transportation
- Communications
- High-Profile Affiliates: The involvement of experienced affiliates from prominent RaaS groups suggests a well-coordinated and potentially sophisticated operation.
- Rapid Evolution: The RaaS model allows for continuous development and adaptation, making it challenging for traditional security solutions to keep pace.
Recommendations in Light of the RansomHub Threat
The CISA-FBI advisory emphasizes the importance of preparedness in the face of the RansomHub threat. Here are some critical recommendations for organizations:
- Stay Informed: Regularly review advisories from CISA, FBI, and other reputable sources to stay updated on the latest cyber threats.
- Patch Systems Promptly: Apply security patches to close vulnerabilities that attackers might exploit.
- Implement Multi-Factor Authentication (MFA): Enforce MFA across all access points to add an extra layer of security.
- Educate Employees: Train your staff on cybersecurity best practices, including phishing awareness and secure password management.
- Backup Regularly: Maintain regular backups of critical data to facilitate recovery in case of a ransomware attack.
- Consider Advanced Security Solutions: Explore advanced security solutions like MixMode that offer proactive detection and protection against evolving ransomware threats.
By implementing these measures, organizations can significantly reduce their risk of falling victim to ransomware attacks like RansomHub and enhance their overall cybersecurity posture.
Why Traditional Security Solutions Struggle Against RansomHub

Legacy security solutions cannot often detect and effectively prevent modern ransomware attacks like RansomHub. Here’s why:
- Signature-Based Detection: Traditional methods rely on identifying known malware signatures. However, RaaS operators frequently update their code, rendering signature-based detection ineffective.
- Static Analysis: Static analysis tools examine malware code for malicious patterns. But RaaS can utilize obfuscation techniques to mask their true nature, bypassing static analysis.
- Limited Visibility: Legacy solutions might not have complete visibility across all network endpoints, allowing attackers to exploit vulnerabilities undetected.
These limitations leave organizations vulnerable to sophisticated ransomware like RansomHub.
How MixMode Can Help Organizations Combat RansomHub
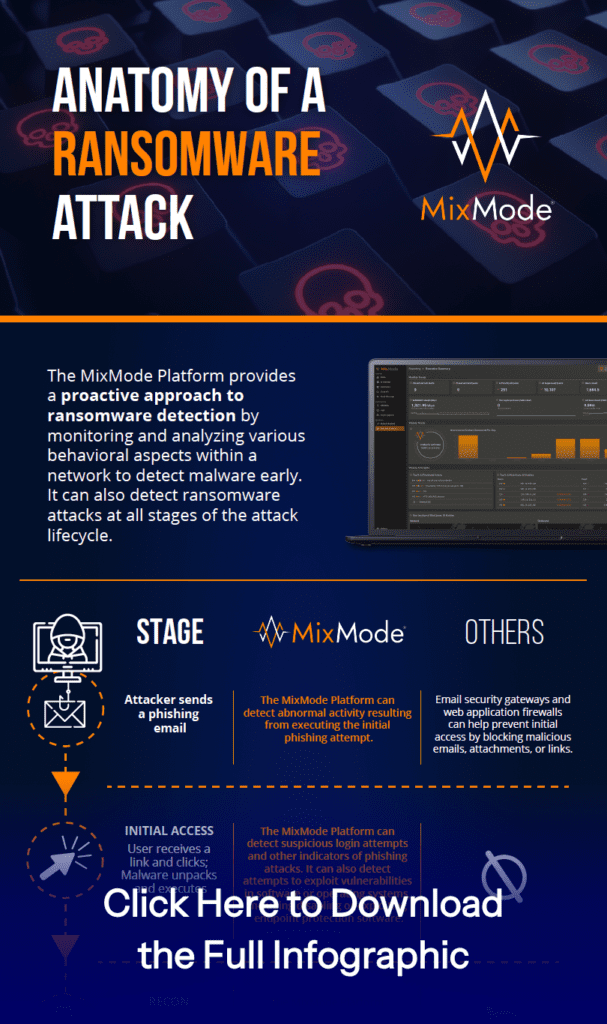
MixMode offers an AI-powered cybersecurity solution that goes beyond traditional methods to empower organizations to combat ransomware by:
- Advanced Threat Detection:
- Real-time behavioral analytics to identify anomalous activities indicative of ransomware attacks.
- Correlation of disparate data sources to uncover hidden threats, including those missed by traditional methods.
- Advanced AI that continuously adapts to the evolving threat landscape.
- Incident Response Acceleration:
- Rapid investigation and containment of ransomware incidents through automated incident response workflows.
- Prioritization of critical alerts based on potential impact.
- Integration with existing security tools for streamlined incident management.
- Threat Hunting and Proactive Defense:
- Identification of vulnerabilities and weaknesses in the network infrastructure.
- Proactive threat hunting to uncover dormant threats.
- Continuous monitoring of the attack surface for complete visibility of emerging risks.
The rise of RansomHub exemplifies the need for continuous vigilance and adaptation in the fight against advanced threats. Reach out to learn how MixMode can help you defend against today’s sophisticated threats.
Other MixMode Articles You Might Like
The Imperative of Explainability in AI-Driven Cybersecurity
Alarming Intrusion: Chinese Government Hackers Target US Internet Providers
Black Hat 2024 and the Rise of AI-Driven Cyber Defense
The Alert Avalanche: Why Prioritizing Security Alerts is a Matter of Survival
Gartner’s 2024 Hype Cycle for Zero Trust: Spotlight on Network Detection and Response
*** This is a Security Bloggers Network syndicated blog from MixMode authored by Joe Ariganello. Read the original post at: https://mixmode.ai/blog/ransomhub-ransomware-targets-critical-infrastructure-a-detailed-look-at-the-cisa-fbi-advisory/

