2024-9-11 16:51:9 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Managing identities online has become a critical aspect of business operations. Whether you’re a start-up or a large enterprise, having a reliable identity management solution can make or break your security infrastructure. While in-house solutions offer excellent support for specific industries and offer a high level of customization, third-party providers excel in enhanced security, cost efficiency, faster deployment and scalability. Choosing the right identity provider is crucial, as it requires architectural changes that can make switching later difficult and costly.
As a product architect, I’ve worked on numerous projects where selecting the right identity provider was crucial. In one instance, we initially used an existing identity management solution, only to realize it wasn’t scalable as our needs grew. The increasing complexities forced us to adopt off-the-shelf solutions, resulting in a challenging migration process. This experience inspired us to develop a selection checklist. We based this checklist on an in-depth study of AWS Cognito, Okta, Keycloak and Auth0, and it revolves around the following six questions to guide decision-making.
How Complex is my MFA requirement?
Organizations should consider several critical factors before defining their MFA requirements, as data security is a priority in sectors like healthcare, military, and finance. These include robust password policies, token expiry provisions, stolen password detection and resistance to brute-force attacks. Implementing multi-factor authentication (MFA) significantly enhances security, although there are trade-offs between convenience and security levels. For instance, while SMS codes offer convenience, they are less secure than hardware tokens.
Advanced MFA methods, such as biometric authentication, may cost more. Auth0 is a better choice for features as it offers a wide range. Okta, however, is more compatible with existing systems. Keycloak provides native support for various MFA methods, including TOTP (Time-based One-Time Password) and WebAuthn.
All four comply with regulatory standards. We found Okta to have the best MFA support. However, examining each use case is crucial. Factors like industry-specific regulations, device reliance, and backup methods affect MFA’s effectiveness and adoption.
- What Single Sign-On Standard Protocols Will I Use?
Adopting Security Assertion Markup Language (SAML), Lightweight Directory Access Protocol (LDAP), Kerberos, or OpenID Connect depends on the organization’s requirements, infrastructure and security needs. SAML and OpenID offer good interoperability, with OpenID being decentralized. Kerberos provides strong encryption and minimizes data transmission across the network. LDAP is ideal for large-scale directory management.
All four identity providers, AWS Cognito, Okta, Keycloak and Auth0, support SAML and OpenID Connect. AWS Cognito suits AWS-centric environments. Auth0 is good for configuring and customizing SAML integration for diverse use cases. Okta is a better option for enterprises as it offers enterprise-grade features for SAML integration, like advanced policy management, adaptive authentication and support for complex federation scenarios.
AWS Cognito does not provide LDAP or Kerberos support, whereas Auth0 is more user-friendly for LDAP. It provides comprehensive documentation and support resources for its integration.
Okta is scalable and reliable, offering monitoring and alert features for proactive directory management, making it ideal for mission-critical LDAP environments.
Keycloak guarantees robust support and flexibility but requires significant setup and configuration efforts for complex use cases and performance optimization.
What are my Multi-Tenancy Model Requirements?
The choice relies on backend customization, cost, scale and maintainability. AWS Cognito allows easy integration with the AWS system. It is cost-effective, secure, and designed to scale automatically as needed. However, it offers limited customization and is less responsive than Okta or Auth0. Initial learning and configuration might also need some maintenance effort.
Auth0 is perfect for handling large volumes of authentication requests. It also has a user-friendly interface and extensive documentation suitable for growing businesses. But the cost can increase significantly.
This cost factor is also true for Okta. Deploying it with a small, inexperienced team can also be difficult as complex customizations may require additional expertise. However, Okta has robust enterprise-grade features, including advanced user management, security policies and integrations. Keycloak’s multi-realm support handles large numbers of tenants and users well, but customization can be time-consuming. Maintenance overhead is significant, as managing multiple realms, updates and security increases administrative workload.
Is UI Customization Possible?
UI customization is crucial for its impact on branding, user experience and security. AWS Cognito and Okta provide customization scope in hosted UI. Auth0 has an edge as it allows for opportunities on the UI portal itself. Keycloak’s realm-specific branding can make the product more customized.
All four identity providers share UI Library support to ensure seamless communication with the backend and negate struggles with accessibility, scalability, cross-platform compatibility and design consistency.
AWS Cognito is user-friendly but has limited options. Okta’s out-of-the-box features reduce the need for extensive customization. Users can configure the notification setting via the Okta Admin Console. Auth0 is the most flexible as it supports dynamic variables, localization and advanced formatting options. Personalizing notifications based on user attributes, language preferences and contextual information, enhancing user engagement and relevance is also possible in Auth0.
Maintenance in Keycloak could be labor-intensive. Users may also find the documentation on theme customization lacking in detail for complex scenarios.
Which One is Aligned With My Authorization Requirements?
AWS Cognito supports scalability and easy integration with AWS services like Lambda, API Gateway, and S3 for mobile and web applications. It is user-friendly and provides a fully managed user directory service to speed up the sign-up and sign-in functionalities.
Auth0 and Okta are more flexible. Auth0 excels in authorization with custom access control rules and supports social login and identity federation. Keycloak offers fine-grained authorization policies but can be challenging for new users when it comes to implementation.
Okta specializes in enterprise identity management. It offers seamless access to multiple applications with one set of credentials and integrates easily with systems like HR and LDAP. Okta’s adaptive authentication adjusts dynamically based on user behavior and risk factors, providing robust IAM features for managing user identities, roles, and permissions.
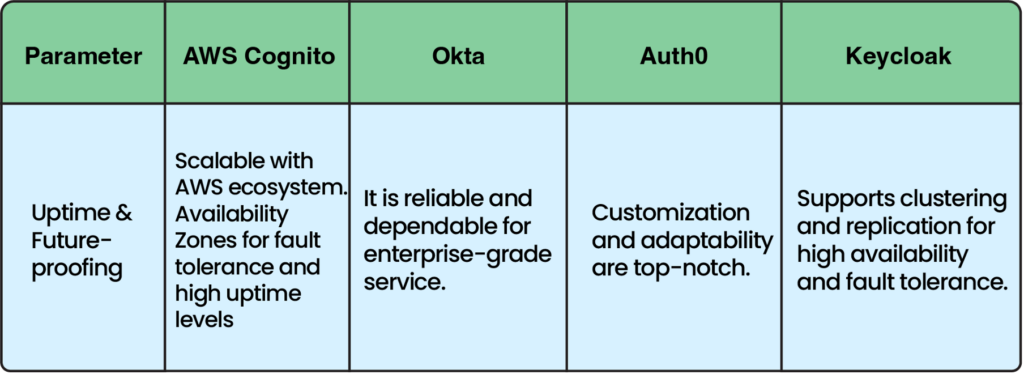
Which is Best for my Uptime Requirements and Future-Proofing?
All three identity providers offer reliable identity management solutions with varying degrees of uptime and future-proofing. Okta stands out for its robust reliability. Its industry-standard SLAs, multiple data centers and redundancy mechanisms make it dependable for enterprise-grade identity management needs.
Auth0 maintains reliability through a distributed architecture and built-in redundancy. It offers high uptime levels (which may vary based on the selected plan). Auth0’s customization and adaptability make it more popular among organizations seeking tailored customer identity solutions.
AWS Cognito benefits from the reliability and scalability of the AWS ecosystem, leveraging multiple availability zones for fault tolerance and high uptime levels. Its integration with other AWS services ensures compatibility with future advancements in cloud computing and identity management.
Keycloak supports clustering and replication for high availability and fault tolerance and can be deployed with load balancers. It is highly extensible through custom providers and scripts, allowing adaptation to future requirements. However, Keycloak is resource-intensive, and managing its dependencies can be burdensome.
Conclusion
AWS Cognito, Okta, Keycloak and Auth0 each offer unique benefits. However, their proper application depends on evaluating them against parameters like security, cost efficiency, scalability and customization. These six questions can be a good approach for making a well-informed decision and staying aligned with long-term strategic goals.
如有侵权请联系:admin#unsafe.sh






