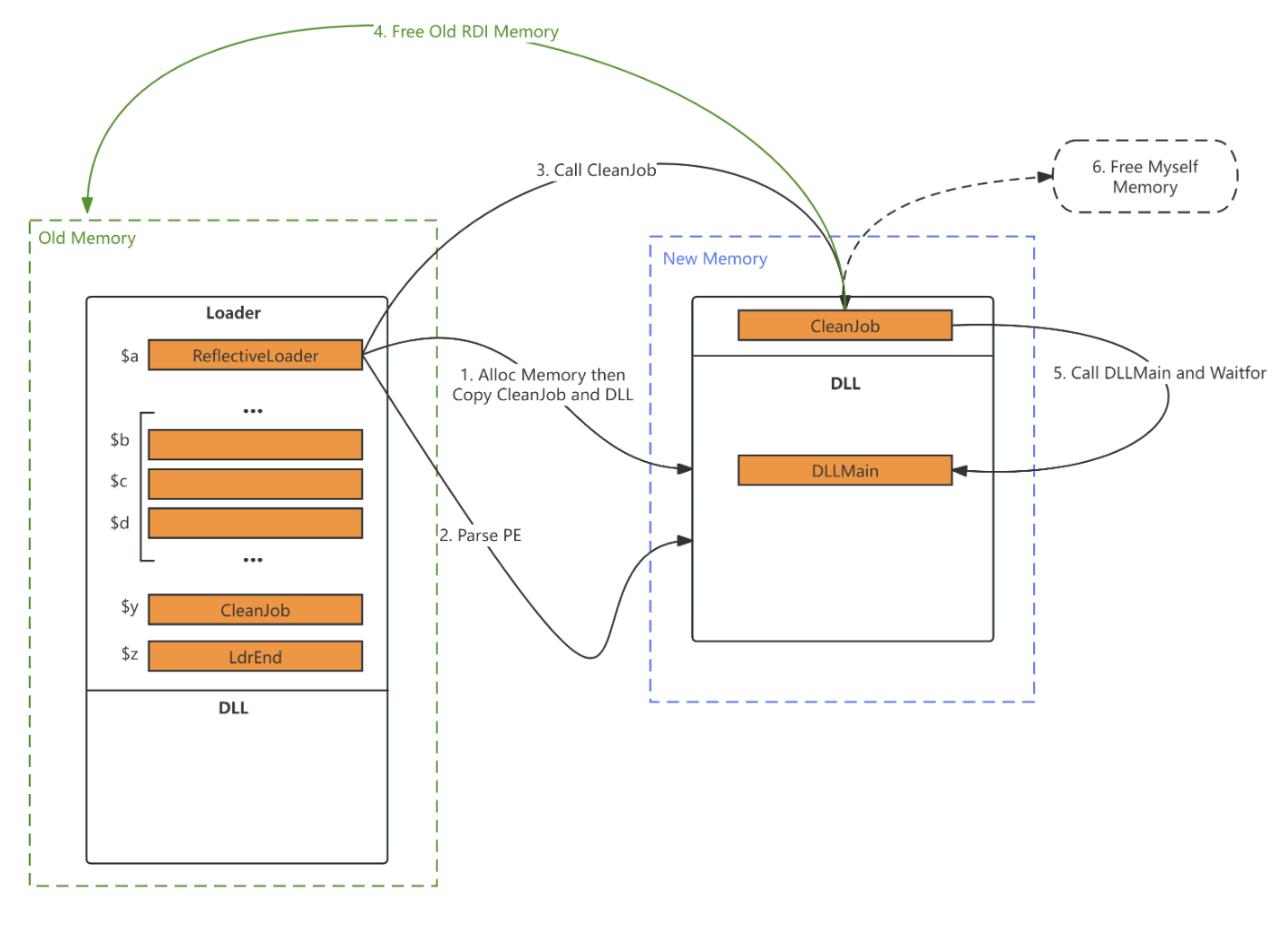
Self Cleanup in post-ex job, suit for CobaltStrike
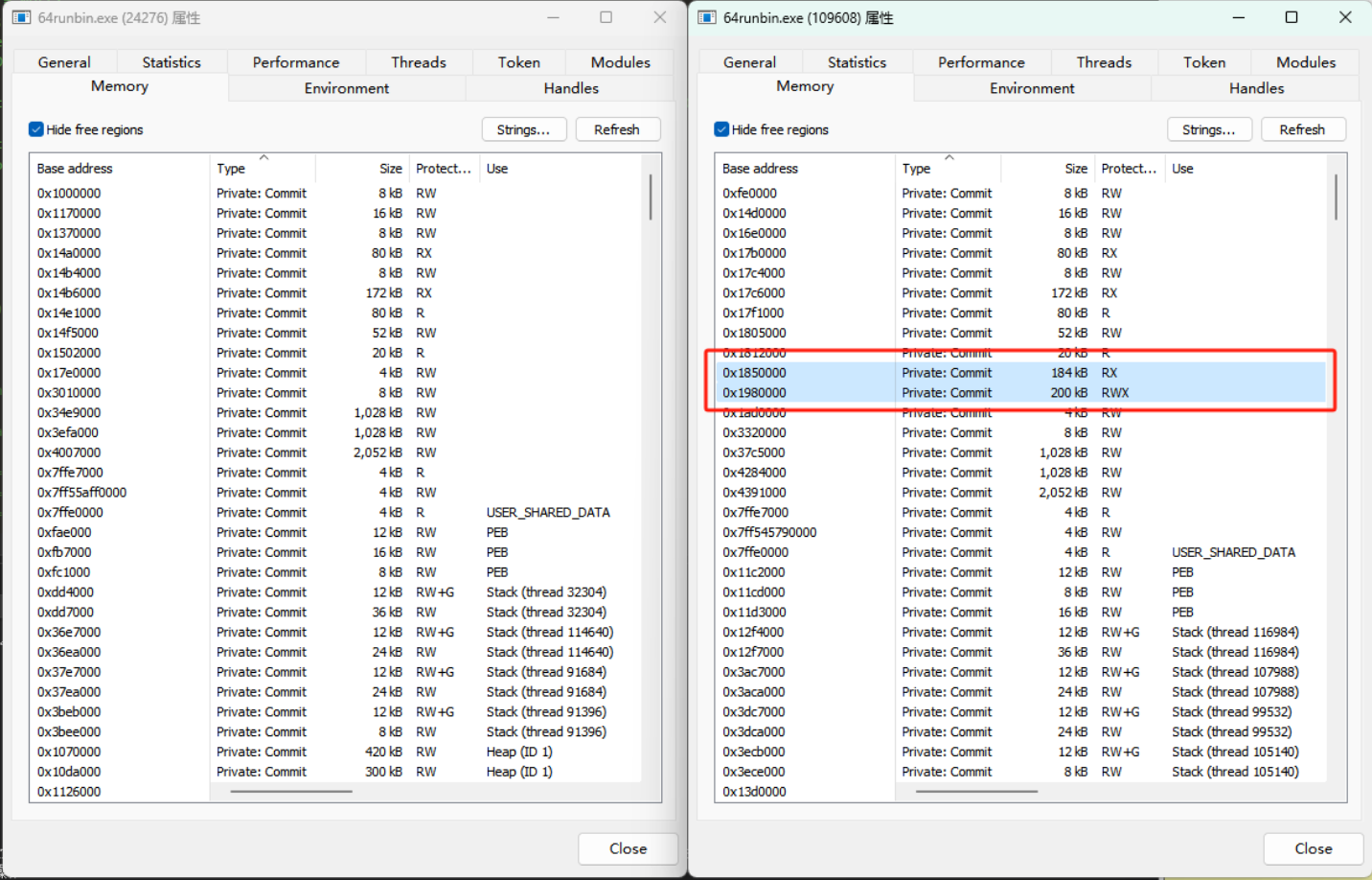
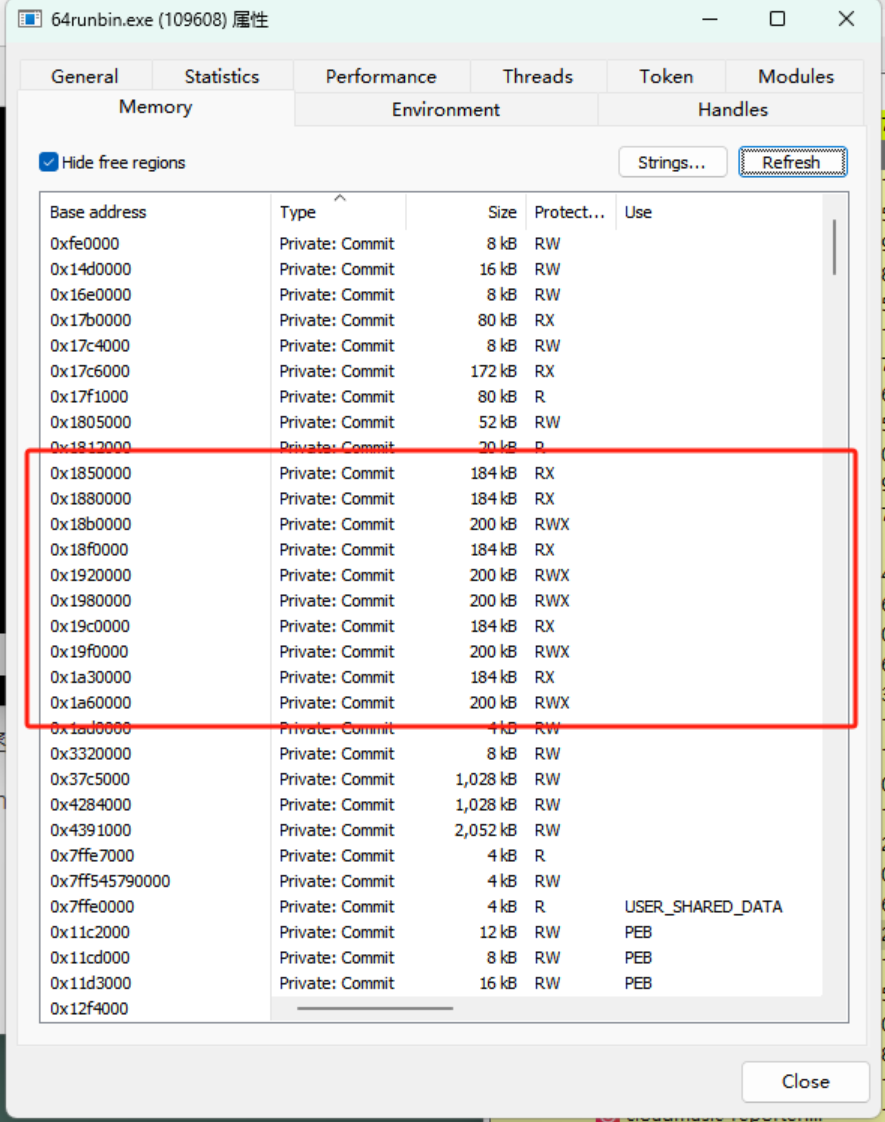
When the target of process injection is the current process, and when the post-ex job is executed and the thread exits, the memory will look like this
Then, perform 5 screenshots:
So, we use the RDI itself to clean up itself and the memory area which the post-ex job is executed.
This is also a general memory execution plugin
The code is not beautiful, and many IOCs are not evasioned. Please modify it according to OPSEC principles. This code only shows the self clean technology.