2024-9-12 21:2:28 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Mythology surrounding technology is pervasive. Although ideas like Macs can’t get viruses, charging a phone overnight destroys the battery, and private browsing prevents tracking have all been debunked, they continue to inform decisions.
SaaS security has myths of its own. They involve the prowess of CASB, the rarity of SaaS attacks, and the invincible security built into SaaS applications. This post will dive into these myths to see if reality matches the legend, and looks at some of the ways SaaS Security Posture Management (SSPM) counters the myths.
Myth #1: CASB Provides Full SaaS Coverage
When SaaS applications first arrived, security experts believed that Cloud Access Security Brokers (CASB) were the right tool to secure them. CASBs provide visibility into the way companies use the cloud, and can enforce security and governance rules in the SaaS application.
However, CASBs are expensive to implement and take an outside-in view of applications. They lack visibility into most security configurations, and have no visibility into user behavior within the application. The reality is that CASBs only partially protect SaaS apps. Organizations that choose CASBs as their SaaS security tool of choice end up leaving many applications without any coverage at all, and those apps with CASB monitors have significant gaps in their security.
SaaS Security Posture Management (SSPM) tools, in contrast, can connect to and monitor every configuration from every SaaS application, providing a far better understanding of your company’s SaaS stack posture.
CASBs check app access from the outside, while SSPMs secure SaaS applications from within the app. SSPMs have a far deeper understanding of configurations and their impact and are significantly better at assessing and improving a SaaS stack’s security posture.
CONCLUSION: Don’t let CASBs leave your SaaS stack overexposed
Myth #2 SaaS Attacks Are Pretty Rare
Articles covering cyberattacks rarely describe the nature of the attack, only that data was breached. When medical facilities, movie studios, financial institutions, retailers, and others disclose a breach, more often than not it was a SaaS CRM or database that was breached. However, this lack of disclosure has most thinking SaaS attacks are a rarity.
That is starting to change. A recent breach in Snowflake led to over 560 million customer records being put up for sale on the dark web. GitHub repositories were used to steal user login credentials and cryptocurrency, Salesforce Communities leaked information to community sites, and an insider breach at a US telecom exposed data for 63,000 employees.
In a recent 2023-2024 CSA survey of cybersecurity and IT professionals, respondents shared the type of security SaaS security incidents that they had experienced over the past 24 months.
- Data Leakage 58%
- Data Breach 41%
- SaaS Ransomware 40%
- Corporate Espionage 32%
- Insider Attack 11%
The reality is that SaaS attacks are commonplace, and organizations must take every precaution to secure their cloud-based SaaS-apps that contain every top of sensitive corporate data.
CONCLUSION: SaaS attacks happen all the time, and they have a far-reaching effect
Myth #3 SaaS Apps Are Highly Secure Out-of-the-Box
According to legend, SaaS apps are among the most secure pieces of software on the market. SaaS vendors use best practices to secure data, and software is patched and updated immediately to protect itself against the latest threat vectors.
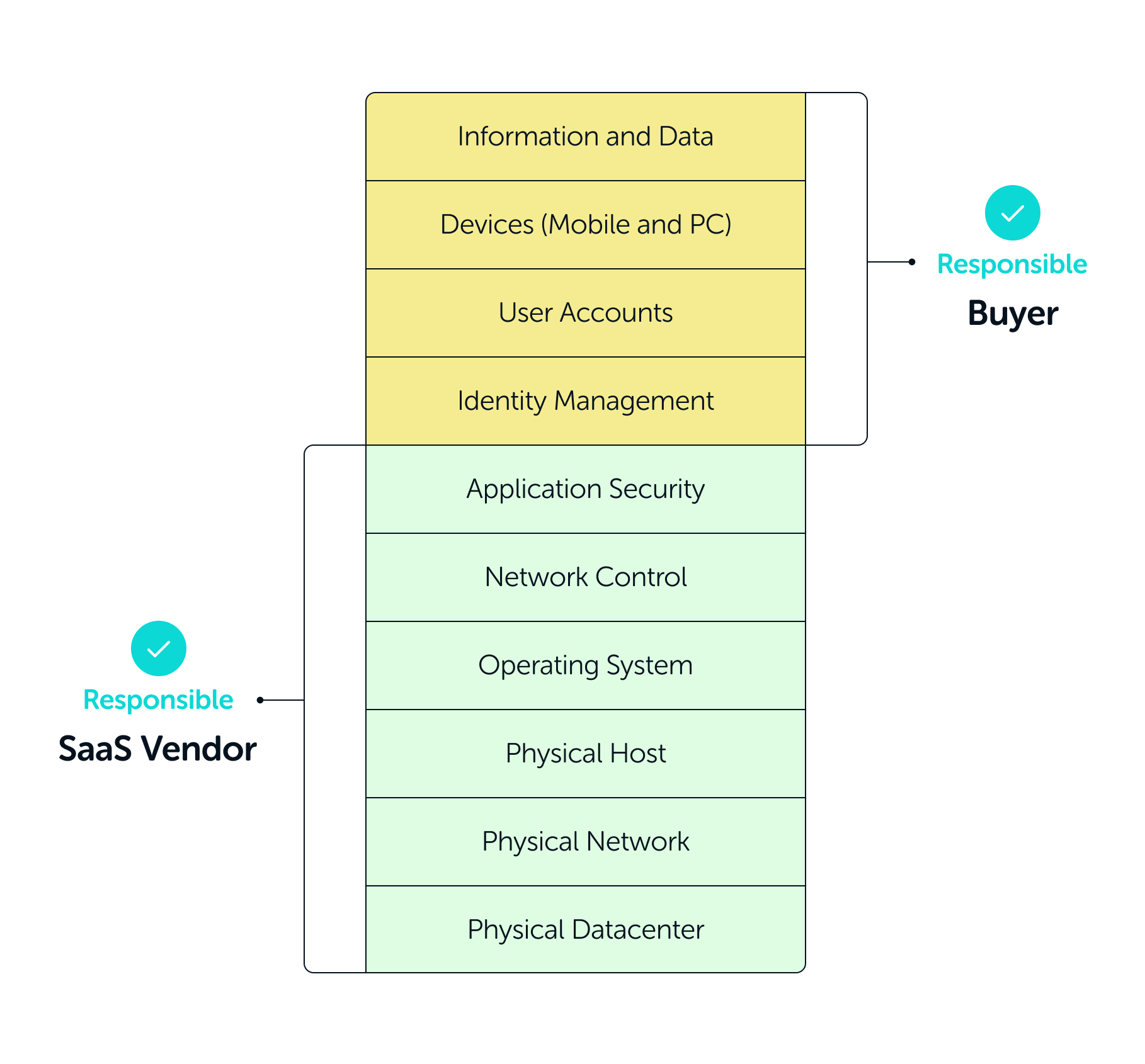
However, data within SaaS applications are often exposed by users who change configurations or grant excessive permissions to third-party applications. Without a tool in place to monitor security settings, businesses are often unaware that the data within their application is exposed.
The responsibility matrix below shows which elements fall under the responsibility of the SaaS vendor, and which areas must be secured by the SaaS user.
Responsibility Matrix

CONCLUSION: SaaS apps really are secure, but the data and access must be secured using a SSPM
SSPM Increases SaaS Security From Day 1
One thing you can count on is that your SSPM tools identify misconfigurations and high-risk third-party applications immediately upon deployment. On the day of the integration, it provides visibility and actionable measures for improvement to increase the SaaS security posture.
Posture is measured based on application settings, connected third-party applications, user settings, and device posture. High-risk settings have a higher weighted impact on posture, to provide a true assessment of SaaS security.
The following chart shows the average starting posture of applications that are monitored by Adaptive Shield and the subsequent improvements in posture over the first year.

Over time, configurations often drift, weakening the security posture. SSPMs recognize when those settings change, identify the user who made the change, and alert app owners and security teams so they can re-secure the applications.
There are three main reasons why configurations drift:
- An admin made a temporary change and forgot to change it back.
- Large companies have thousands of non-security employees with access to configurations who don’t realize the impact their actions have on their company’s security posture.
- Operational changes trigger security warnings when static thresholds are crossed. For example, a company may have a policy allowing 10% of high privilege users of an app to be dormant. If they cross the threshold, the security check will change from pass to fail.
In addition, drifts can be caused by malicious users, who may turn off MFA to provide a threat actor with access using a username and password alone.
Tracking drifts on applications with a high security posture ensures that accidental changes to configurations are addressed immediately. The following chart shows the most frequently changed configurations by Adaptive Shield customers.

Secure Your SaaS Applications
With all the myths surrounding SaaS apps, there are two truths you can count. The first is that threat actors are increasing their focus on accessing SaaS applications. With online access potentially just a phished user credential away, many view it as the low-hanging fruit.
The second is that SSPM platforms are a game changer in SaaS security. From improving posture immediately to detecting configuration drifts as they happen, it is the security tool of choice for organizations that want to truly secure their applications.
The post Two Lies, One Truth in Securing Your SaaS Stack appeared first on Adaptive Shield.
*** This is a Security Bloggers Network syndicated blog from Adaptive Shield authored by Arye Zacks. Read the original post at: https://www.adaptive-shield.com/blog/two-lies-one-truth-in-securing-your-saas-stack/
如有侵权请联系:admin#unsafe.sh
