2024-9-13 17:1:29 Author: cyble.com(查看原文) 阅读量:11 收藏
Key Takeaways
- Cyble Research and Intelligence Labs (CRIL) identified a campaign targeting individuals connected to the upcoming US-Taiwan Defense Industry Conference, as indicated by the lure document uncovered during the investigation.
- The campaign involves a ZIP archive containing an LNK file that mimics a legitimate PDF registration form for deception.
- When the LNK file is opened, it executes commands to drop a lure PDF and an executable in the startup folder, establishing persistence.
- Upon system reboot, the executable downloads additional content and executes it directly in memory, effectively evading detection by the security products.
- The first-stage loader triggers a second-stage loader, which downloads, decodes, and compiles C# code in memory, avoiding the creation of traceable files on disk.
- Once the compiled code is executed, the malware exfiltrates sensitive data back to the attacker’s server via web requests designed to blend in with normal traffic, making detection more difficult.
Overview
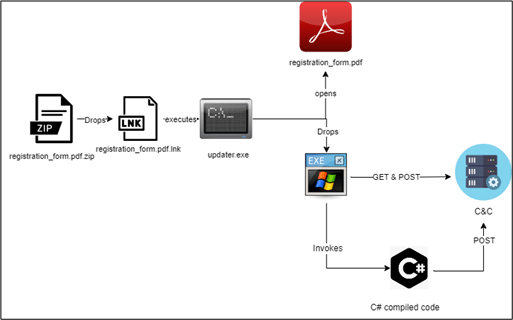
The initial infection vector of this campaign remains unclear; however, based on the lure document analyzed, there are indications that the attack may have been delivered to users via spam emails. The attack commences with a suspicious archive file containing an LNK file disguised as a PDF document. This deception is designed to trick users into executing the malicious LNK file, which in turn triggers a series of covert actions in the background.
Upon execution, the LNK file extracts two components: a base64-encoded executable and the actual lure PDF. The executable is protected using .NET’s Confuser, an obfuscation tool, to evade detection and is placed in the startup folder to ensure persistence on the compromised system. Once the executable runs, it retrieves additional malicious content, specifically a DLL file, from a remote server. This DLL file is Encrypted using XOR operation to further obscure its purpose.
The executable employs .NET’s “Assembly.Load” function to load the decrypted DLL directly into memory, enabling it to bypass traditional security mechanisms that scan files written to disk. After the DLL is loaded, it downloads encrypted C# code from the TA-controlled server, compiles it on the victim’s machine, and then executes it entirely in memory.
During our testing of this malware, we were unable to capture the final payload. However, analysis of the loader’s code suggests that the payload’s ultimate purpose is to exfiltrate sensitive data from the victim’s machine to conduct further malicious activities. Based on the lure document used in this attack, it is likely that the TA behind this campaign is specifically targeting individuals associated with the upcoming US-Taiwan Defense Industry Conference.
The figure below shows the infection chain.

Technical Analysis
CRIL uncovered a campaign targeting users by posing as registration forms for the upcoming Conference and distributed malicious ZIP files under the name “registration_form.pdf.zip”. The ZIP file contains an LNK file disguised as a PDF. When extracted, the archive presents a file named “registration_form.pdf,” but this is actually an LNK file with a dual extension (.pdf.lnk), misleading the user into thinking it is a legitimate PDF document. The malicious LNK file contains an embedded executable and a lure PDF, both encoded in base64 format, further concealing the malicious content, as shown in Figure 2.
When the user opens the LNK file, it triggers several background commands. First, the LNK file searches the base64 embedded content using the “findstr” command and saving them as “1.txt” and “2.txt,” respectively. Next, the “certutil” utility decodes these files, storing the lure PDF as ” registration_form.pdf ” in the Temp directory and the executable as “update.exe” in the “%AppData%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup” folder, ensuring persistence. Finally, the registration_form.pdf is opened with the system’s default PDF viewer. The figure below shows the content of the malicious LNK file.

Lure Document:
The lure document used in this attack suggests that the TA behind the campaign is likely targeting individuals connected to the upcoming US-Taiwan Defense Industry Conference, which is scheduled to take place in the United States from September 22nd to September 24th, 2024.
The potential targets are expected to include key participants such as defense officials, industry executives, government representatives, and other stakeholders involved in or attending the event. The timing and focus of the campaign suggest that the TA aims to exploit the significance of the conference, potentially for gathering sensitive information to conduct further malicious activities. This strategic targeting underscores the sophisticated nature of the campaign and its alignment with geopolitical interests. The figure below shows the Lure document.

First Stage Loader: updater.exe
The “Updater.exe” file functions as a loader and is protected using the .NET “Confuser protector.” It is placed in the Startup folder, ensuring it executes each time the user logs into the system. Upon execution, the file first verifies if it is running from the “Startup” directory. If it is, the execution proceeds; otherwise, it terminates without further action. When the file runs, it sends a POST request to a compromised site controlled by the TA, transmitting the victim’s machine.
Next, using “WebClient”, it downloads string content from “hxxp://tdea.com.tw/asset/uploads/files/68679813[.]txt” and removes the first character to retrieve the correct base64-encoded content. This reveals the
- machine name: “MSEDGEWIN10″
- URL for the 2nd stage loader: “hxxp://tdea.com.tw/asset/uploads/files/68679815[.]txt“
The first-stage loader downloads a base64-encoded data stream from the above URL, which is first decoded and then further processed by applying an XOR operation using a hardcoded key with a decimal value of 16. This operation results in the extraction of a DLL file. The below shows the decryption loop used for getting the DLL file.

The extracted DLL is then dynamically loaded and executed using the .NET “Assembly.Load” function, allowing the TA to invoke malicious functionality embedded within the DLL. The below figure shows how the “Assembly.Load” function is used to load the decrypted DLL and call a specific method named “MyEntry” with in a class named “ConsoleApp.MyClass”

Second Stage Loader
The “.NET Assembly.Load” function is used to load the second-stage loader, which functions similarly to the initial stage. This DLL loader retrieves additional base64-encoded content from the TA’s controlled server. Once the content is downloaded, it is decoded using base64 and then processed with an XOR operation using a hardcoded key of 48 in decimal, as shown below.

Although the URL “hxxp://tdea.com.tw/asset/uploads/files/68679811[.]txt” currently doesn’t contain any data, code analysis indicates that the decoded content is likely XML data containing C# code and assembly references (DLLs) which utilizes “Compile After Delivery” technique to compile the source code during runtime.

In-memory Execution
The downloaded C# code is compiled in memory using specific compiler parameters such as “GenerateExecutable = false” and “GenerateInMemory = true”. These parameters, along with references to core assemblies like “System.dll”, “System.Data.dll”, and “System.Management.dll”. The “System.Management.dll” is specifically used to interact with Windows Management Instrumentation (WMI), allowing the code to query system properties and interact with system components through WMI queries. This suggests that the TA may use WMI queries to gather system information from the victim.
Additional DLLs may also be included as reference assemblies. The compiled code is executed directly in memory, bypassing the disk entirely, which complicates detection by conventional security tools.
This method is highly effective for evasion. It allows malware or APT groups to dynamically generate and execute payloads at runtime, making detection and mitigation efforts significantly more challenging for defenders. The figure below shows a code snippet responsible for compiling the downloaded C# code and executing it in memory.

Data Exfiltration
After executing the compiled code, the resulting data is sent back to the TA’s server using a web request. A “WebClient” object is utilized to upload the data, where the request’s “ContentType” is set to “application/x-www-form-urlencoded” to simulate standard form data submission, and the “UserAgent” header is modified to mimic a web browser. The “UploadString” method is used to send a POST request to the TA’s specified URL, along with parameters such as a randomly generated filename, a command flag, and the encoded content being transmitted.

Network Communication:
The TA leverages a compromised website to host malicious content and frequently retrieves files stored within an exposed open directory. Moreover, the TA employs CKFinder, a PHP-based file management framework, to upload and manage files sent from the victim machines. This framework allows the TA to store exfiltrated data or additional malicious payloads on the server. The image below illustrates the structure of the open directory on the compromised site, highlighting the ease with which the TA can access and manipulate stored files.

Threat Attribution
Chinese threat actors have a well-documented history of targeting Taiwan, particularly around significant political events. For instance, during the period leading up to Taiwan’s presidential election earlier in 2024, there was a marked increase in cyberattacks within the 24 hours preceding the election, as reported by Trellix. This surge underscores China’s ongoing efforts in cyber espionage aimed at Taiwan’s political and military sectors. Despite this pattern, the specific TA behind the current campaign remains unidentified, and we have not been able to link these tactics, techniques, and procedures (TTPs) to any known threat actor or advanced persistent threat (APT) group at this time.
Conclusion
This sophisticated attack employs social engineering and advanced in-memory execution techniques to avoid detection. By disguising the LNK file as a legitimate conference registration PDF and executing payloads dynamically in memory, the TAs can conduct malicious activities to steal sensitive information without leaving traces on the disk. Given the timing and context of the US-Taiwan Defense Industry Conference, this campaign is likely intended to conduct malicious operations targeting valuable information related to defense collaborations.
Our Recommendations
- Deploy advanced email filtering solutions to block phishing emails and suspicious attachments before they reach the end users. Anti-phishing solutions that use machine learning or behavior analysis can also identify and block malicious campaigns at an early stage.
- Implement security solutions with advanced threat detection that can monitor in-memory execution of code or PowerShell commands. Tools like EDR (Endpoint Detection and Response) should be used to detect unusual behavior, such as programs compiling and running C# code in memory.
- Ensure that users have the least privileges required for their roles, reducing the risk of malware being able to execute in privileged areas.
- Application whitelisting or blocking untrusted applications from executing in certain directories can also minimize the risk.
- Monitor outbound network traffic for signs of exfiltration and communication with command-and-control (C2) servers, especially encrypted and base64-encoded traffic. Use firewalls, IDS/IPS (Intrusion Detection and Prevention Systems), and network analysis tools to detect suspicious web traffic patterns.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Initial Access (TA0001) | Spearphishing Attachment (T1566.001) | The ZIP archive containing the LNK file may be delivered via phishing or spam emails |
| Persistence (TA0003) | Registry Run Keys / Startup Folder (T1547.001) | update.exe added into the Startup folder |
| Execution (TA0002) | User Execution: Malicious File (T1204.002) | Malicious LNK file executed by the user after extracted from archive file |
| Defence Evasion (TA0005) | Obfuscated Files or Information: LNK Icon Smuggling (T1027.012) | The LNK file uses a PDF file icon, leveraging the “IconEnviromentDataBlock” to appear as a harmless PDF document. |
| Defence Evasion (TA0005) | Deobfuscate/Decode Files or Information (T1140) | Certutil is used to decode base64 content. |
| Defence Evasion (TA0005) | Obfuscated Files or Information: Compile After Delivery (T1027.004) | CSharp code is compiled and executed in memory |
| Command and Control (TA0011) | Data Encoding: Non-Standard Encoding (T1132.002) | Encrypted file is downloaded from TA controlled server. |
| Exfiltration (TA0010) | Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol (T1048.003) | Exfiltrated data is transmitted using standard protocol. |
Indicators of Compromise (IOCs)
| Indicator | Indicator Type | Comments |
| 6b1af6be189e31168b8f4eff84cd475eb5d0cbd08e646760fb352165a30cb269 | SHA-256 | registration_form.pdf.zip |
| 4989882339d745692eabe0a375d8cecd6e7e3af534cd1173d94867b8d069cd7f | SHA-256 | registration_form.pdf.lnk |
| 0e07b96c508dfc0e11f119071cca4ec628dae635771532dae7f034ed369591d7 | SHA-256 | updater.exe |
| df92e2c56f53c9139da70c5a813b6512df616abd56dc10dc80a625c4512cb7f2 | SHA-256 | updater.exe |
| e0174968064b45d1b0c255bec351de94bb59852cb7f2e6ac694debbac59acb7a | SHA-256 | d.dll |
| 5aaa5a7ef2eaa13e6e4274ccdb3c80251c868043fa51c2ca1e5b556a65d5166c | SHA-256 | 68679815.txt |
| 531db819d928243bda43997165da1fa3ebda3412e7d9928cb6bd2a8c898a85ae | SHA-256 | 68679813.txt |
| hxxp://tdea.com.tw/asset/uploads/files/68679813[.]txt | URL | URL used to get the DLL link |
| hxxp://tdea.com.tw/asset/uploads/files/68679815[.]txt | URL | URL used to get the DLL file |
| hxxp://tdea[.]com[.]tw/ckeditor/ckfinder/core/connector/php/connector[.]php?command=SaveFile&type=Files¤tFolder=%2F&langCode=en&hash=f92a86fd96382c5a | URL | POST request to send exfiltrated data |
| hxxp://tdea.com.tw/asset/uploads/files/68679811[.]txt | URL | URL used to get the CSharp (C#) code |
Related
如有侵权请联系:admin#unsafe.sh