
关于BBOT
BBOT是一款递归型互联网OSINT资源情报工具,该工具深受Spiderfoot项目的启发,旨在自动化侦察、漏洞奖励项目和ASM。

功能介绍
1、支持多个目标
2、网页截图
3、 Web安全测试模块套件
4、由 NLP 提供支持的子域名变异
5、Neo4j 的本机输出(以及更多)
6、使用 Ansible 自动安装依赖项
7、使用自定义 YARA 规则搜索完整攻击面
8、Python API + 开发人员文档
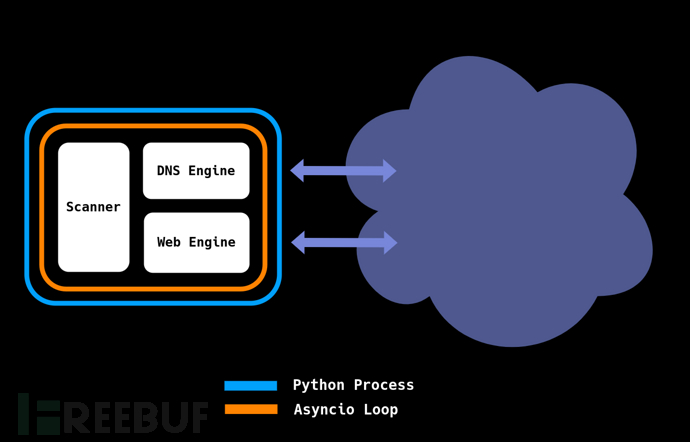
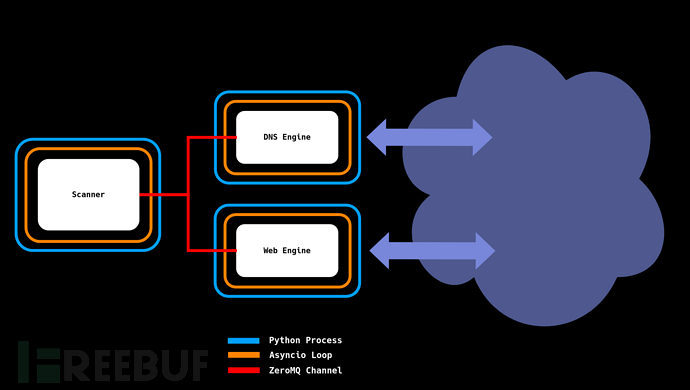
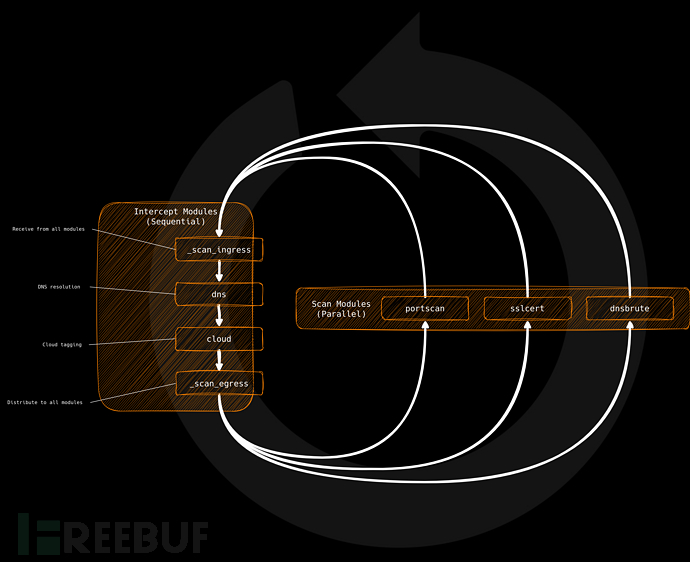
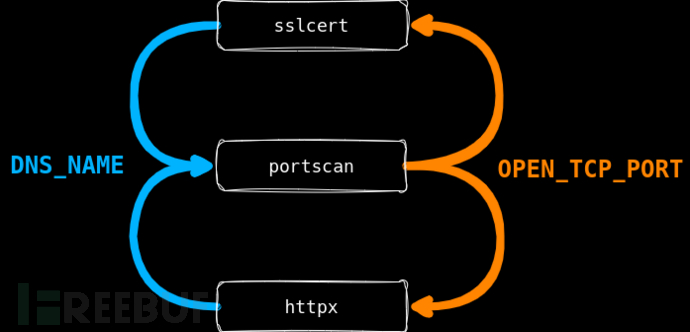
工具架构
工具安装
由于该工具基于Python 3开发,因此我们首先需要在本地设备上安装并配置好最新版本的Python 3环境。
接下来,广大研究人员可以直接使用下列命令将该项目源码克隆至本地:
https://github.com/blacklanternsecurity/bbot.git
除此之外,我们也可以直接使用pip安装稳定版本:
pipx install bbot
工具使用
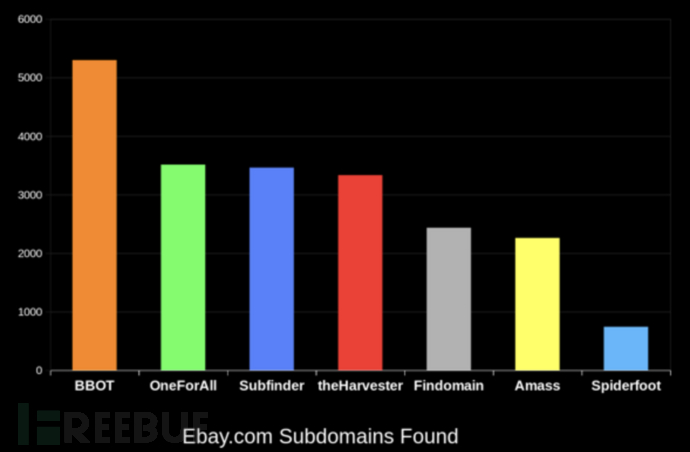
子域名查找器
被动 API 源加上针对目标特定子域名变异的递归 DNS 暴力破解:
bbot -t evilcorp.com -p subdomain-enum bbot -t evilcorp.com -p subdomain-enum -rf passive
subdomain-enum.yml:
description: Enumerate subdomains via APIs, brute-force flags: # enable every module with the subdomain-enum flag - subdomain-enum output_modules: # output unique subdomains to TXT file - subdomains config: dns: threads: 25 brute_threads: 1000 # put your API keys here modules: github: api_key: "" chaos: api_key: "" securitytrails: api_key: ""
网络爬虫
bbot -t evilcorp.com -p spider
spider.yml:
description: Recursive web spider modules: - httpx config: web: # how many links to follow in a row spider_distance: 2 # don't follow links whose directory depth is higher than 4 spider_depth: 4 # maximum number of links to follow per page spider_links_per_page: 25
电子邮件收集器
bbot -t evilcorp.com -p email-enum bbot -t evilcorp.com -p email-enum subdomain-enum spider
email-enum.yml:
description: Enumerate email addresses from APIs, web crawling, etc. flags: - email-enum output_modules: - emails
网络扫描仪
bbot -t www.evilcorp.com -p web-basic bbot -t www.evilcorp.com -p web-thorough
web-basic.yml:
description: Quick web scan include: - iis-shortnames flags: - web-basic web-thorough.yml: description: Aggressive web scan include: # include the web-basic preset - web-basic flags: - web-thorough
一次性从多个源获取全部数据
bbot -t evilcorp.com -p kitchen-sink bbot -t evilcorp.com -p subdomain-enum cloud-enum code-enum email-enum spider web-basic paramminer dirbust-light web-screenshots
kitchen-sink.yml:
description: Everything everywhere all at once include: - subdomain-enum - cloud-enum - code-enum - email-enum - spider - web-basic - paramminer - dirbust-light - web-screenshots config: modules: baddns: enable_references: True
Python库使用
同步
from bbot.scanner import Scanner
if __name__ == "__main__":
scan = Scanner("evilcorp.com", presets=["subdomain-enum"])
for event in scan.start():
print(event)异步
from bbot.scanner import Scanner
async def main():
scan = Scanner("evilcorp.com", presets=["subdomain-enum"])
async for event in scan.async_start():
print(event.json())
if __name__ == "__main__":
import asyncio
asyncio.run(main())工具运行演示
演示视频:【点我观看】
许可证协议
本项目的开发与发布遵循GPL-3.0开源许可协议。
项目地址
BBOT:【GitHub传送门】
参考资料
https://www.blacklanternsecurity.com/bbot/
https://github.com/smicallef/spiderfoot
https://github.com/blacklanternsecurity/bbot-vivagraphjs
文章来源: https://www.freebuf.com/sectool/410448.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh