
漏洞背景
3月23日,微软发布公告ADV200006称Adobe Type Manager Library中存在2个未修补的漏洞,当Windows Adobe Type Manager Library处理Adobe Type 1 PostScript 格式字体时存在两个远程执行代码漏洞。攻击者利用漏洞可在多个场景实施攻击,比如说服受害者在Windows的预览中访问一个特殊构造的文档。
4月15日,微软正式发布CVE-2020-1020/CVE-2020-0938漏洞补丁。
腾讯安全团队已对漏洞进行分析,该漏洞可稳定利用:
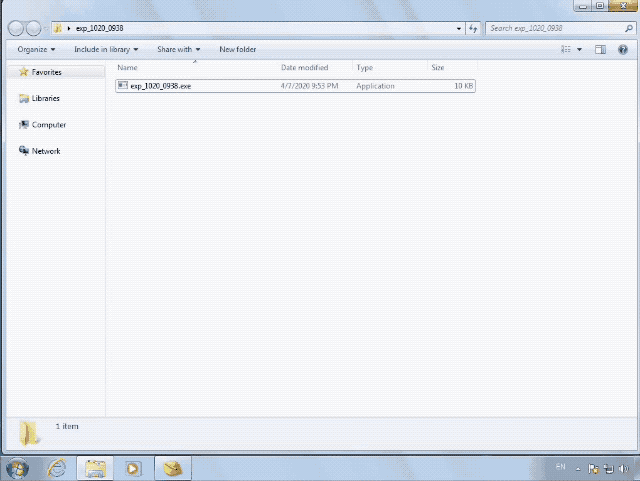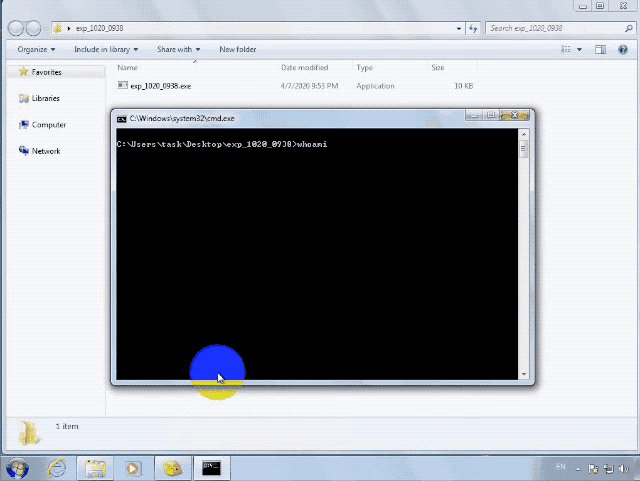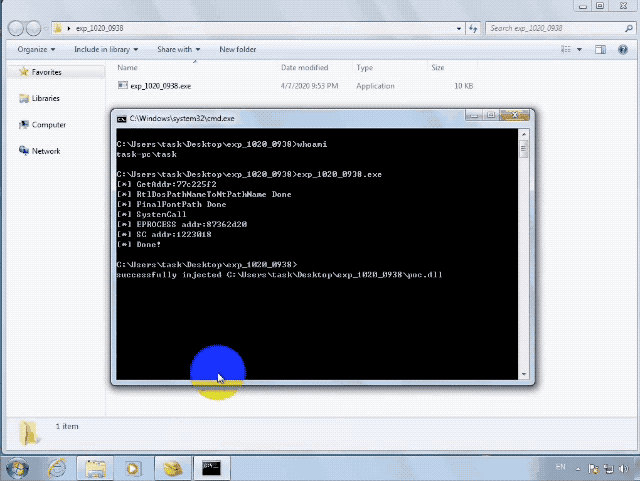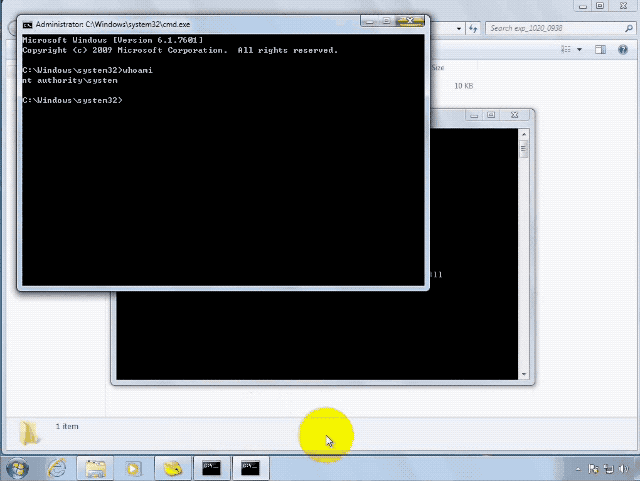
漏洞版本
· Windows 10 for 32-bit Systems
· Windows 10 for x64-based Systems Windows 10 Version 1607 for 32-bit Systems
· Windows 10 Version 1607 for x64-based Systems
· Windows 10 Version 1709 for 32-bit Systems
· Windows 10 Version 1709 for ARM64-based Systems
· Windows 10 Version 1709 for x64-based Systems
· Windows 10 Version 1803 for 32-bit Systems
· Windows 10 Version 1803 for ARM64-based Systems
· Windows 10 Version 1803 for x64-based Systems
· Windows 10 Version 1809 for 32-bit Systems
· Windows 10 Version 1809 for ARM64-based Systems
· Windows 10 Version 1809 for x64-based Systems
· Windows 10 Version 1903 for 32-bit Systems
· Windows 10 Version 1903 for ARM64-based Systems
· Windows 10 Version 1903 for x64-based Systems
· Windows 10 Version 1909 for 32-bit Systems
· Windows 10 Version 1909 for ARM64-based Systems
· Windows 10 Version 1909 for x64-based Systems
· Windows 7 for 32-bit Systems Service Pack 1
· Windows 7 for x64-based Systems Service Pack 1
· Windows 8.1 for 32-bit systems
· Windows 8.1 for x64-based systems
· Windows RT 8.1
· Windows Server 2008 for 32-bit Systems Service Pack 2
· Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
· Windows Server 2008 for Itanium-Based Systems Service Pack 2
· Windows Server 2008 for x64-based Systems Service Pack 2
· Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
· Windows Server 2008 R2 for Itanium-Based Systems Service Pack 1
· Windows Server 2008 R2 for x64-based Systems Service Pack 1
· Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
· Windows Server 2012
· Windows Server 2012 (Server Core installation)
· Windows Server 2012 R2
· Windows Server 2012 R2 (Server Core installation)
· Windows Server 2016
· Windows Server 2016 (Server Core installation)
· Windows Server 2019
· Windows Server 2019 (Server Core installation)
· Windows Server, version 1803 (Server Core Installation)
· Windows Server, version 1903 (Server Core installation)
· Windows Server, version 1909 (Server Core installation)
漏洞分析
漏洞模块为atmfd.sys(Windows 10 1703后是fontdrvhost.exe),成因在于Windows解析PostScript字体中的BlendDesignPositions或BlendVToHOrigin时,没有经过安全检查,导致处理模块可能引发越界写,栈溢出的问题。
SetBlendDesignPositions:
BlendDesignPositions格式如下:

Win7 x86环境下,atmfd!SetBlendDesignPositions在解析BlendDesignPositions array时,会将内容全部保存到栈上,缓冲区的大小是960(0x3C0),因此最多存放16个sub-array,当sub-array数量大于16时,会引发溢出:
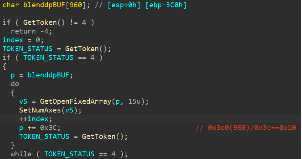
ParseBlendVToHOrigin:
atmfd!ParseBlendVToHOrigin在处理数组BlendVToHOrigin时存在两处溢出。
Win7x86下由于定义的int v12[2]仅有8个字节,当NumMasters大于2时,引发缓冲区溢出:
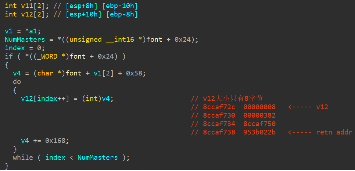
NumMasters大小可以在字体文件中通过构造特殊的BlendDesignPositions或WeightVector控制:
第二处溢出发生在atmfd.sys读取BlendVToHOrigin时,首先获取当前NumMasters并根据其大小将BlendVToHOrigin的数据复制到栈中的V11,由于NumMasters可控,当NumMasters过大时会对栈中的v11造成溢出,V11同样也是8字节:
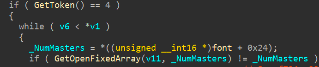
第二次溢出时,由于V12在V11的高地址方向,所以当V11溢出时会覆写V12中保存的指针。
补丁分析
由于win7已停止更新,win10 1703后微软把atmfd.sys模块的功能移植到fontdrvhost.exe中,补丁前后漏洞模块共做了2处修改,2个函数均存在栈溢出漏洞:
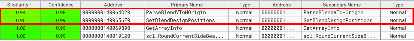
补丁后SetBlendDesignPositions中增加了条件判断,sub-array数量超过16时返回错误,避免溢出:
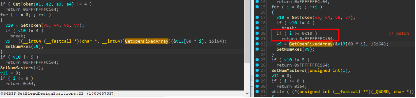
补丁后ParseBlendVToHOrigin中启用了GS保护栈的完整性,并在读取BlendVToHOrigin数组前,限制了NumMasters大小;
时间线:
1. 3月23日,微软发布通告ADV200006称Adobe Type Manager Library中存在2个未修补的漏洞
2. 3月24日,腾讯安全发布漏洞通告
3. 4月15日,微软官方发布CVE-2020-1020/CVE-2020-0938漏洞通告及补丁
参考链接:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1020
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0938
如若转载,请注明原文地址
如有侵权请联系:admin#unsafe.sh