2024-9-16 21:16:26 Author: cyble.com(查看原文) 阅读量:13 收藏
Overview
The Cyble Global Sensor Intelligence Network, or CGSI, has been actively monitoring and capturing real-time attack data through various Honeypot sensors. Last week’s research reveals the top cyber threats of the week including multiple exploit attempts, malware intrusions, financial fraud, and brute-force attacks. Multiple CVE attempts and targeted malware cases were observed from September 4, 2024, to September 10, 2024.
CGSI’s recent research highlights a range of vulnerabilities impacting various IoT devices and software systems. A significant issue identified is the arbitrary code execution vulnerability in SPIP’s Porte Plume plugin, tracked as CVE-2024-7954. This flaw affects versions before 4.30-alpha2, 4.2.13, and 4.1.16, allowing attackers to execute arbitrary PHP code via specially crafted HTTP requests. Users are advised to upgrade to the latest patched versions to mitigate this risk.
Another critical vulnerability is CVE-2024-4577, which involves PHP CGI configurations. This flaw permits attackers to execute arbitrary commands through malicious URL parameters. GeoServer versions prior to 2.23.6, 2.24.4, and 2.25.2 are affected by CVE-2024-36401, a remote code execution vulnerability due to unsafe XPath evaluation of OGC request parameters. Users should either apply the available patches or remove the vulnerable gt-complex library to secure their systems.
CVE-2024-32113, a path traversal vulnerability in Apache OFBiz affecting versions before 18.12.13, was also a highlight of this week’s research. This flaw allows unauthorized access to restricted directories, making it essential for users to upgrade to version 18.12.13 to close this security gap. In SolarWinds Web Help Desk, CVE-2024-28987 exposes a hardcoded credential vulnerability that enables remote attackers to gain internal access and manipulate data.
Brute Force Attacks and Malware Infections
Brute-force attacks targeting IT automation software and databases have surged. These attacks are characterized by relentless attempts to decipher passwords and gain unauthorized access. They are particularly concerning due to their focus on critical infrastructure, which can lead to substantial disruptions and data breaches.
These attacks have been significant, involving systematic attempts to guess passwords for unauthorized access. Notable volumes of these attacks have been observed, particularly against IT automation software and databases. Brute-force attacks consist of an attacker submitting many passwords or passphrases with the hope of eventually guessing a combination correctly.
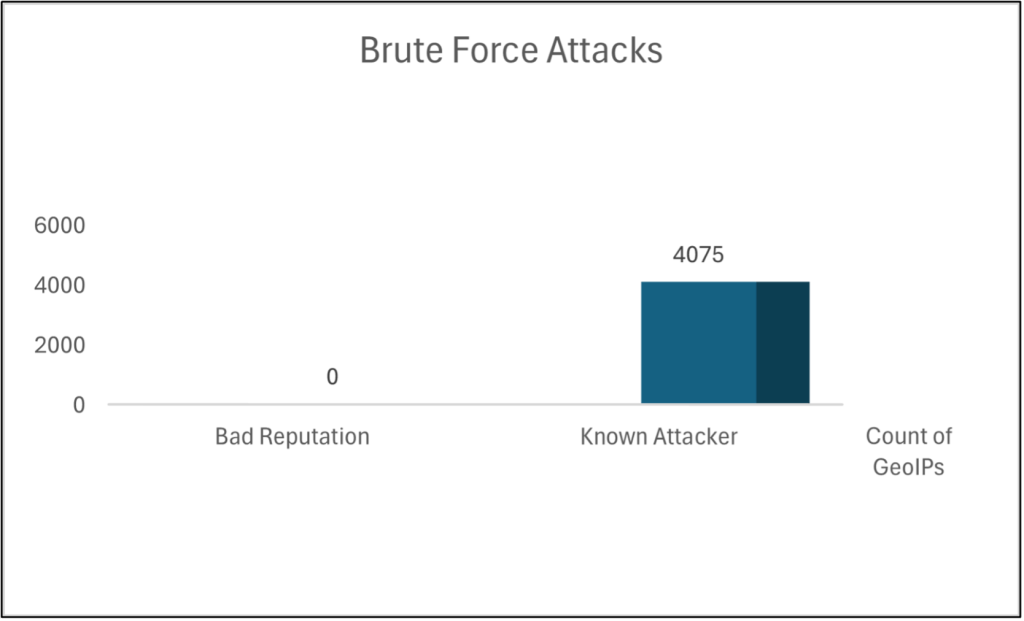
The attacker employs a systematic trial-and-error approach to test every possible password and passphrase until the correct one is discovered. This brute force attack method involves iteratively guessing login credentials or encryption keys and potentially accessing hidden web pages. Hackers methodically work through all possible combinations in hopes of success. Last week, Cyble recorded numerous such attacks, and the statistics related to specific source IPs are illustrated below (Figure 1).

Figure 1 – Statistics of recent brute force attacks
The figure below highlights the most frequently targeted usernames and passwords in brute-force attacks. The analysis shows that these attacks predominantly affect IT automation software and servers, such as “3comcso,” “elasticsearch,” and “hadoop,” as well as databases like “mysql” and “Postgres.” The most commonly used username/password combinations include “root,” “admin,” “password,” and “123456.”

Figure 2 – Most used usernames and passwords
Several case studies highlight ongoing threats in terms of malware attacks. The CoinMiner Linux Trojan targets Linux systems to use their resources for cryptocurrency mining, leading to significant performance degradation.
The Linux Mirai malware attack utilizes the Mirai Botnet to exploit IoT devices and Linux servers for widespread network assaults. The Mirai Botnet is well-known for targeting these devices, converting them into remotely controlled bots that participate in extensive network attacks.
Similarly, the Linux IRCBot attack leverages IRC connections to take control of compromised systems, frequently incorporating them into a botnet. These IRC connections serve as backdoors, enabling attackers to execute a range of actions on the compromised systems. Many of these systems are subsequently used as part of a botnet controlled through IRC.
The Rise of Phishing Emails and Other Scams
Phishing email attacks have been notably prevalent, with several new types of scams emerging recently, leveraging phishing and social engineering. One prevalent type of fraud is the Delivery Scam, where scammers impersonate courier officials to deceive victims into believing they have a package awaiting delivery. Victims are instructed to send sensitive personal details to a specified email address to receive the supposed delivery. These fraudulent emails often come from typo-squatted domains mimicking legitimate courier services.
Another common phishing attack vector is the Project Funding Scam. In this scam, fraudsters promise victims a large sum of money for a project, tricking them into providing sensitive financial information under the pretense of transferring funds. An example seen in this scam involved an email purporting to be from the “World Bank Group”.
The Relief Fund Scam is also prevalent. Scammers promise victims a substantial amount of money in exchange for a small upfront payment. The scam often masquerades as an email from a reputable organization, such as the “United Nations Compensation Committee Office,” using similar-looking email addresses.
In 2024, QR code phishing attacks have surged, reflecting a growing trend among cybercriminals to exploit QR codes for malicious purposes. The rise in QR code phishing can be attributed to several factors.
The widespread adoption of QR codes, particularly during the COVID-19 pandemic, has made them a convenient target for cybercriminals. Users are now more accustomed to scanning QR codes, which creates a false sense of security. QR codes also obscure the destination URL, making it difficult for users to verify the legitimacy of the site they are directed to.
Previously, Cyble Research and Intelligence Labs (CRIL) identified a campaign targeting individuals in China. This campaign used Microsoft Word documents containing QR codes, which were distributed via spam email attachments and pretended to be from the Ministry of Human Resources and Social Security of China. The documents falsely offered labor subsidies and directed users to scan QR codes for authentication. These QR codes led to phishing sites designed to collect financial information, including credit card details and passwords.
The phishing sites associated with this campaign used domains generated by a Domain Generation Algorithm (DGA) and were linked to a series of subdomains and IP addresses. The phishing sites prompted users to enter personal and financial information under the guise of claiming labor subsidies, ultimately aiming to facilitate unauthorized transactions.
Conclusion
The data gathered by the Cyble Global Sensor Intelligence (CGSI) network highlights a surge in cyber threats, including intensified brute-force attacks, critical vulnerabilities, and phishing scams. Key issues include vulnerabilities in SPIP’s Porte Plume plugin and PHP configurations, alongside malware attacks like CoinMiner and Mirai Botnet. Phishing scams, including QR code-based attacks, are increasingly targeting users.
To mitigate these threats, organizations should promptly address vulnerabilities, implement strong passwords, block malicious IPs, and stay vigilant against phishing tactics. Regular updates and proactive security measures are crucial for protecting systems and data.
Mitigations and Recommendations
- Ensure that your security systems block the hashes, URLs, and email addresses provided in the IoC list attachment.
- Address all listed vulnerabilities promptly and maintain vigilance by regularly monitoring top Suricata alerts within your internal networks.
- Consistently review the real-time attack table for any malicious ASNs and IP addresses.
- Implement measures to block IP addresses associated with brute-force attacks and secure the specific ports outlined in the IoC table.
- Immediately update default usernames and passwords to defend against brute-force attacks and establish a policy for regular password changes.
- Configure servers with complex, hard-to-guess passwords to enhance security.
Related
如有侵权请联系:admin#unsafe.sh