2024-9-16 23:1:36 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Think of the Digital Operational Resilience Act (DORA) as the EU’s way of making sure that financial institutions can stay strong, even when the digital world gets messy. With cyberattacks becoming smarter and more frequent, and everything from system glitches to natural disasters throwing wrenches in the works, DORA steps in to help organizations stay resilient when things go sideways.
So, what’s the deal with DORA? In simple terms, it’s all about making sure financial institutions can handle whatever’s thrown at them—whether that’s a cyberattack, system meltdown, or even something as unpredictable as a freak storm. Since so much of the financial world relies on digital infrastructure these days, the risks are higher than ever. Enter DORA. With this DORA compliance checklist and clear outline of the DORA compliance requirements, financial entities have a clear roadmap of what they must follow to stay safe and sound.
DORA’s main goals are to:
- Strengthen cybersecurity: DORA lays down the law when it comes to cybersecurity, making sure institutions are protecting their systems and data like pros.
- Standardize compliance: No more guessing games across EU countries. DORA makes sure everyone’s on the same page, regardless of location.
- Improve incident response: When things go wrong, it’s not just about what you do, but how fast you do it. DORA pushes for clear, quick response plans.
- Encourage collaboration: Sharing is caring! DORA wants institutions to share info about cyber threats so everyone benefits.
- Tighten third-party risk management: Many institutions rely on outside vendors for tech services, but DORA makes sure those third parties are held to high standards too.
In short, DORA is here to make sure financial institutions aren’t just playing defense—they’re playing smart. Following DORA regulatory guidelines will help protect not only individual organizations but the entire financial ecosystem from the chaos that digital threats can unleash.

Key Components of DORA
Understanding what DORA’s all about is the first step to staying compliant. Let’s break down the most important pieces of the DORA process, so you know what needs to be covered:
1. ICT Risk Management Framework
At the heart of DORA is the need for every financial institution to have a solid ICT risk management plan in place. Think of it as your roadmap for identifying, assessing, and managing all those pesky risks that come with using Information and Communication Technology (ICT).
- Identify critical assets: Figure out which of your ICT systems are mission-critical.
- Risk assessment: Regularly evaluate where your vulnerabilities lie and how they could impact your operations.
- Mitigation strategies: Once you know your risks, put the right safeguards in place to minimize them.
2. Incident Reporting Obligations
When something goes wrong, you can’t just cross your fingers and hope it goes away. DORA makes sure you’ve got the right reporting protocols set up to handle any significant ICT incidents.
- Timely reporting: If an incident impacts your operations (or those of your clients), you’ve got to report it quickly.
- Incident classification: Create a system to rank incidents by severity so you can prioritize your responses.
- Regulatory communication: Keep open lines with regulators, ensuring transparency and cooperation when things hit the fan.
3. Digital Operational Resilience Testing
What’s the best way to know if you’re prepared for a cyberattack? By testing your systems, of course! DORA requires that institutions test their operational resilience on the regular.
- Threat-led penetration testing (TLPT): You’ll need to simulate real-world cyberattacks at least once every two years to see how well your defenses hold up.
- Scenario-based testing: Test out different disruption scenarios to make sure your team is ready for anything.
4. Third-Party Risk Management
Since many financial institutions depend on third-party tech vendors, DORA makes sure these relationships are closely monitored to keep risks in check.
- Due diligence: Before signing on with a third-party provider, ensure they meet your security standards.
- Ongoing monitoring: Regularly assess third-party risks to stay ahead of any potential vulnerabilities.
5. Information Sharing Mechanisms
DORA encourages institutions to share insights about emerging cyber threats with each other to strengthen the collective defenses of the financial sector.
- Industry collaboration: Join industry forums to stay plugged into the latest threat intel.
- Threat intelligence sharing: Share relevant info with other institutions to boost everyone’s situational awareness.
6. Governance and Accountability
DORA puts a big emphasis on accountability, making sure that governance structures are solid.
- Board responsibilities: Your board needs to stay on top of ICT risk management strategies and align them with the overall business plan.
- Accountability frameworks: Set up clear lines of accountability so that everyone knows their role in keeping things resilient.
DORA Compliance Checklist
Here’s where the rubber meets the road. To get in line with DORA, you’ll need to follow a structured plan. Let’s walk through the DORA compliance checklist, a must-have tool for staying on track:
1. Scope Determination
First things first: Does DORA apply to you? Use Article 2 to assess if your organization falls under its scope. This involves looking at factors like the size of your business, the type of services you offer, and your presence in the EU.
2. Gap Analysis
Take a good, hard look at your current ICT systems and compare them to DORA cybersecurity regulations. Where do you fall short? This gap analysis will help pinpoint what needs to be addressed.
3. Remediation Plan
Now that you know where the gaps are, it’s time to build a roadmap to fill them. Prioritize actions based on risk and resources, making sure your plan is realistic and achievable.
4. Critical Third-Party ICT Providers
If you’re working with third-party ICT providers, especially those classified as critical under Article 31, make sure they’re fully compliant with DORA. Perform due diligence and stay on top of ongoing monitoring.
5. Threat-Led Penetration Testing (TLPT)
Article 26 requires you to implement TLPT using approved frameworks and conduct tests on live production systems at least once every two years. Get ready for some stress-testing!
6. Incident Response Plan
Set up a clear process for managing ICT incidents, including procedures for identifying, tracking, and classifying issues. You’ll also need a strong communication plan to keep everyone in the loop—both internally and with regulators.
7. Continuous ICT Monitoring
Keep your finger on the pulse of your ICT systems. Article 8 specifies that you need to regularly monitor and assess risks, keeping an updated inventory of your information assets.
8. Board Responsibilities
Make sure your board is fulfilling its duties under Article 5 by overseeing security policies and approving your digital resilience strategies. Top-down buy-in is key to success.
9. Documentation Practices
Keep thorough records of everything related to your compliance efforts—risk assessments, incident reports, testing results, you name it. Good documentation is your best friend when it comes to audits.
10. Training and Awareness Programs
Build training programs to raise awareness about cybersecurity risks among your employees, from top execs to the most junior staff.
Implementation Steps for DORA Compliance
Now that you’ve got a handle on the checklist, let’s talk about how to actually put DORA into practice. Here’s a step-by-step guide to DORA implementation:
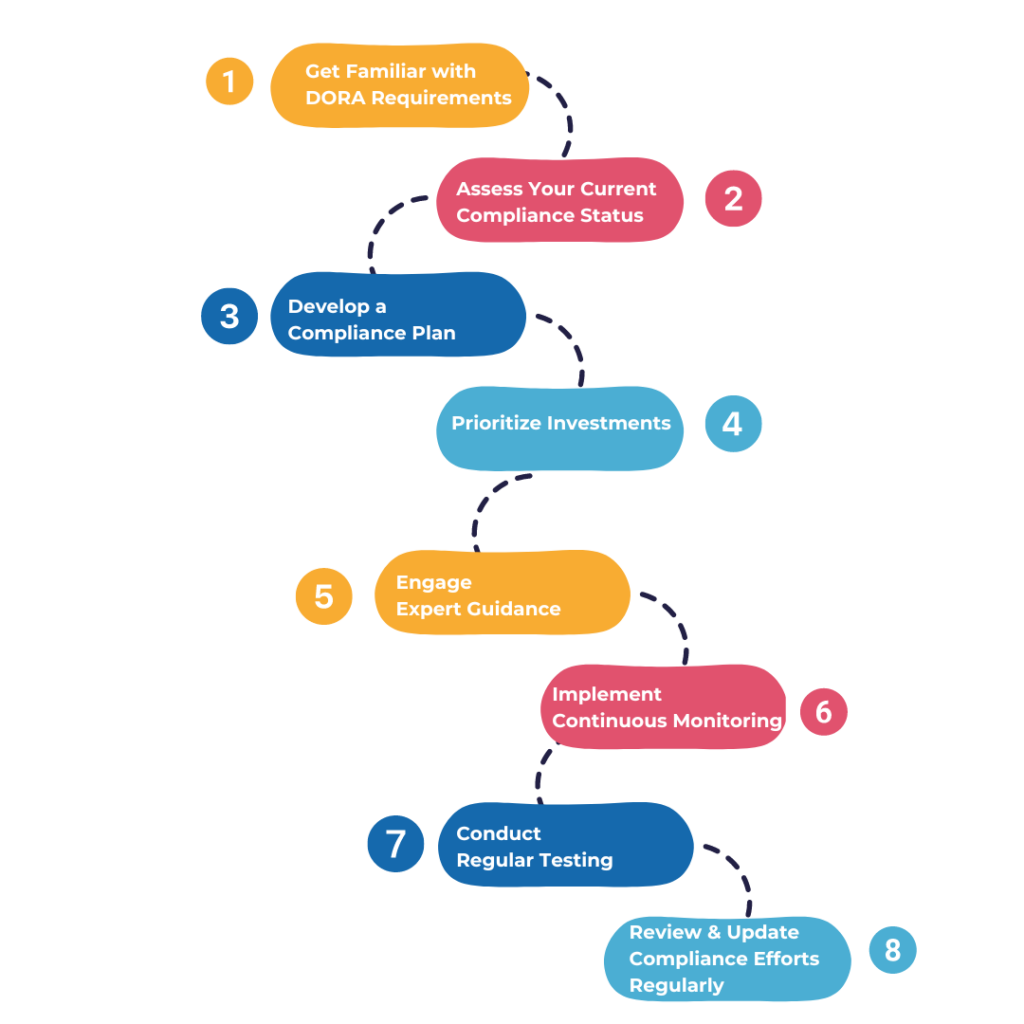
Step 1: Get Familiar with DORA Requirements
Before diving in, make sure you’ve read through the DORA regulatory text and all the accompanying guidelines from the European Supervisory Authorities (ESAs). Knowing the ins and outs of the regulation will make everything else smoother.
Step 2: Assess Your Current Compliance Status
Time for a self-assessment. Take stock of your current policies and practices, focusing on ICT risk management, incident response, and third-party risk management. Identify any gaps between where you are now and where you need to be under DORA.
Step 3: Develop a Compliance Plan
With the results of your assessment in hand, craft a compliance plan that lays out specific actions for each department. Assign clear responsibilities, set deadlines, and make sure you have the resources needed to get the job done.
Step 4: Prioritize Investments
Focus on where you’re most vulnerable first. Whether it’s shoring up your cybersecurity infrastructure or enhancing your threat intelligence capabilities, make sure your investments are targeted where they’ll have the biggest impact.
Step 5: Engage Expert Guidance
You don’t have to go it alone. Bring in specialists who know the ins and outs of ICT risk management to help guide your efforts and ensure you’re staying on track.
Step 6: Implement Continuous Monitoring
Set up systems to continuously monitor your ICT environment for any potential risks. Keep a close eye on your assets and regularly assess legacy systems for vulnerabilities.
Step 7: Conduct Regular Testing
Put your resilience to the test with TLPT and other testing frameworks. Simulate different types of disruptions to make sure your defenses are up to par.
Step 8: Review and Update Compliance Efforts Regularly
DORA isn’t a one-and-done deal. As the regulations evolve, your compliance efforts need to evolve too. Set regular reviews to assess your progress and make updates where needed.
By following this approach, not only will you meet your DORA compliance requirements, but you’ll also be in a strong position to weather any digital storms that come your way. Compliance isn’t just about avoiding penalties—it’s about building a resilient, future-proof organization
Conclusion
By following this approach, not only will you meet your DORA compliance requirements, but you’ll also be in a strong position to weather any digital storms that come your way. Compliance isn’t just about avoiding penalties—it’s about building a resilient, future-proof organization.
Think of DORA as your safety net in an unpredictable digital landscape. The benefits go beyond ticking boxes on a regulatory checklist. You’re fortifying your business against potential disruptions, ensuring seamless operations even in the face of crises. By having robust processes in place, you’ll gain trust from clients and partners who’ll appreciate your commitment to security and operational resilience. And let’s face it, a resilient business is one that thrives long term.
Take it one step at a time, and remember: compliance doesn’t have to be a headache. With the right tools, mindset, and support, navigating DORA can actually give you the upper hand. So, buckle up, embrace the process, and turn this challenge into an opportunity to future-proof your business.
The post DORA Compliance Checklist: From Preparation to Implementation appeared first on Scytale.
*** This is a Security Bloggers Network syndicated blog from Blog | Scytale authored by Wesley Van Zyl, Senior Compliance Success Manager, Scytale. Read the original post at: https://scytale.ai/resources/dora-compliance-checklist-from-preparation-to-implementation/
如有侵权请联系:admin#unsafe.sh
