2024-9-17 01:35:0 Author: ddanchev.blogspot.com(查看原文) 阅读量:6 收藏
This is from the "correct if I'm wrong but this is publicly accessible information so why shouldn't I take a look at it" department.
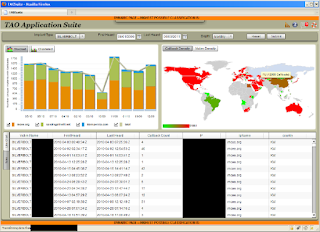
I've been recently going though Snowden's archive and I came across to my favorite presentation which is on the topic of 4th party collection and now that we all know that I've participated in GCHQ's Lovely Horse program with my Twitter account where I was "supposed" to improve the security awareness of the GCHQ with my tweets I came across to several unredacted domain names in NSA's TAO Application Suite and I've decided to look them up while living in the universal world where everyone seems to submit and know everything which is VirusTotal.
The document is also available in the OCR version at the National Security Archive.
Here are the domains:
hxxp://mcee.org - 65.111.254.13
hxxp://sandrogolinelli.net
hxxp://transpersia.com
Here are the results:
http://mcee.org; http://sandrogolinelli.net; http://transpersia.com where we already know that MD5: e5107ff5153547a8d9cc5738289e9f96 is known to have phoned back to mcee.org in specific http://mcee.org/service.php?p=dlfile&a=3574736a716a07016a0201060d0103010615515945595441535a47586a565459595754565e155
354415d50471843061b041b03 and http://mcee.org/service.php?p=pop&url=2160677e657e13157e1615121915171512015920282b0c0c0c0111130e10110e1311101901111
41b14101b1119010c0c0c2b606213641016631014016473736e731b01094f544d4d082b and MD5: adfbc680b21257cc8b2f204de72ec57a is known to have phoned back to sandrogolinelli.net where we also know that the same MD5 is known to have phoned back to pooladimm.com (5.144.130.34)
如有侵权请联系:admin#unsafe.sh
