2024-9-17 23:31:6 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
What if I told you that thousands of companies (30% of the accounts we reviewed) are leaving a backdoor open to their ServiceNow databases for anyone with limited programming skills?
This is a story of how a simple misconfiguration in one of the world’s most used SaaS applications sitting at the core of a company’s infrastructure can lead to password exposures and data leaks, putting data and users at risk.
In this two-part series, we begin by examining the structure of ServiceNow, and the relationship between articles, pages, and widgets. In Part 2, we get inside the misconfiguration and show ServiceNow users how to secure their knowledge bases.
About Service Now
ServiceNow is one of the world’s most popular IT service management (ITSM) platforms, used by about 80% of Fortune 500 companies. Organizations everywhere rely on this SaaS application to automate business processes relating to IT, HR, customer service, and other functions.
The knowledge base is one of the service’s most visible features. It stands as a centralized repository for sharing articles, best practices, and other important information. Employees and customers access knowledge base articles as a form of self service, enabling them to resolve issues without opening a ticket.
Knowledge base articles often contain sensitive information. They may include one-time passwords, personal information, or internal links that aren’t intended for public consumption.
Articles, Pages, and Widgets
When a user opens a ServiceNow knowledge base page, there are three components working in concert to ensure that the information is displayed correctly.
The core of any page is the content. This is the information that the user is seeking, and it is unique to every knowledge base webpage. In the lexicon of ServiceNow, content is called an article.
ServiceNow uses widgets as containers to hold different types of information. In addition to the widget containing the article, there are additional widgets on the page that may allow users to rate the information on the page, leave comments, see breadcrumbs, or add other information. Widgets make it easy to modularize and organize information.
Pages are the third piece of the ServiceNow knowledge base puzzle. They organize and position the layout of the widgets so that there is a logical flow of information. The page ensures that the user can read the article first before being asked to rate the information on the page or leave a comment.
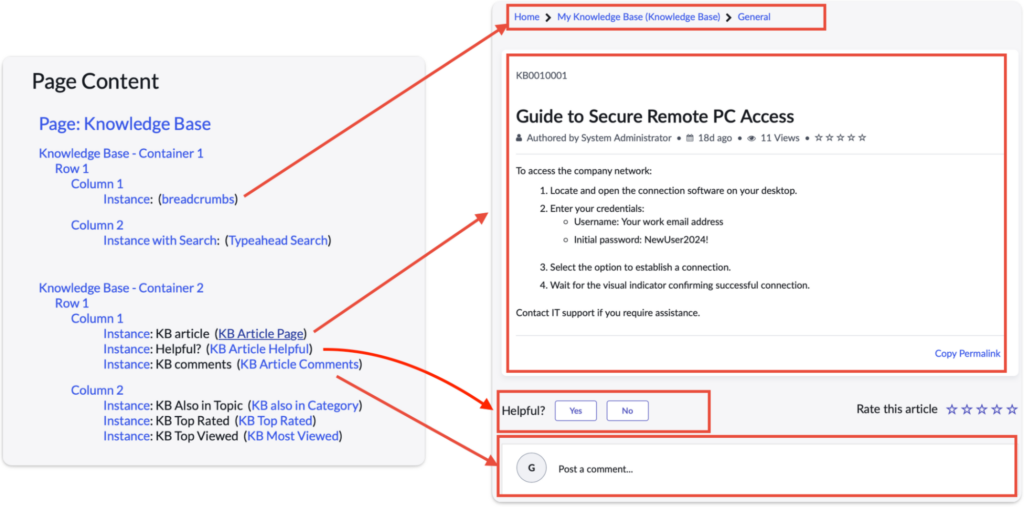
Figure 1 brings these three elements together. The left side of the image shows Page Content. This is the page which contains a number of widgets. The right side of the image shows the user-facing webpage. Each widget corresponds with a displayed piece of content. Users can see the article and engage with the page using elements that are added into place by the widget.

Securing Knowledge Base Content
Knowledge bases are organized within ServiceNow following a hierarchical structure. Organizations may have multiple knowledge bases, each catering to different users or populations. For example, a company may have a self-service knowledge base for employees to deal with IT issues and a separate knowledge base to help customers use their product. Each knowledge base must be configured independently, and administrators have the option of setting the knowledge base to public or private.
Additionally, pages can be set to private. This provides flexibility to organizations who want to keep some pages private in a publicly accessible knowledge base. When an unauthorized user attempts to access a private page, they are prompted to log in before any information is displayed.
This system seems to work well. Sensitive information is limited to authorized personnel, and organizations are protected against data leaks.
Finding Misconfigurations in ServiceNow
Adaptive Shield systematically researches SaaS configurations to secure the application. This research is critical, and without it our SaaS security platform wouldn’t understand the ramifications inherent in each misconfigured setting.
Our story began while researching ServiceNow configurations to find optimum ways to secure the application. As part of our process, we systematically look at settings from within the application and try to access data from outside the application.
Our mission is to identify and mitigate misconfigurations in public-facing digital assets that could lead to leaks and breaches of confidential data, intellectual property, or personally identifiable information. Our goal during this research is to stay ahead of emerging threats and deliver industry-leading solutions for our customers.
Initially, we found a number of publicly accessible pages that externalized knowledge base articles. Many of these articles contained sensitive information, including detailed information about the tenant’s IT infrastructure, personal details such as user names, email addresses, and passwords. The clearly unintended revelation of critical information pointed to a security oversight that demanded immediate attention. Those articles were accessible via specific URL patterns, which varied slightly between old and newer ServiceNow deployments.
Older Instances
-
- *.service-now.com/kb_home.do
- *.service-now.com/kb_find.do
- *.service-now.com/kb_list.do
- *.service-now.com/kb_view.do
Newer Instances
-
- *.service-now.com/kb?id=kb_home
- *.service-now.com/kb?id=kb_search
- *.service-now.com/kb?id=kb_article
- *.service-now.com/kb?id=kb_article_view
- *.service-now.com/kb?id=kb_view
Pulling Information Out of ServiceNow
We looked at the kb_home page and landed on this screen for organizations that had a publicly-facing knowledge base. The page allows users to search for articles that have been shared publicly.

Next, we went to a kb_article page. As shown in the following screenshot, if public pages are enabled and the knowledge base is exposed, the article’s content can be viewed without the need for authentication. In this article, anyone can see the initial username and password to secure remote PC access.

This anonymized example represents many that we came across that shared highly sensitive information from across various domains, including IT operations, human resources, and R&D. Clearly, a large number of companies are unintentionally sharing knowledge base articles.
To this point, the issues we found were misconfigurations on the part of the company. Pages that shouldn’t have been publicly shared allowed guest access to anyone who could find the link.
Misconfigurations and the Shared Responsibility Model
ServiceNow security is jointly shared between the company and its customers. ServiceNow, like most SaaS applications, is responsible for ensuring the security of the application. That includes the platform design, physical security of its data centers, network security, and vulnerabilities, as well as other elements.
ServiceNow customers are responsible for securing access to the data within their ServiceNow tenants. That means using the security settings, such as MFA or privacy configurations, that limit access to authorized users.
In effect, that means that ServiceNow must build an app that is secure, while its customers must take care to lock the door. In the misconfiguration described here, customers did not use the privacy tools included to prevent outsiders from accessing their knowledge base articles. SaaS Security Posture Management (SSPM) is designed to detect misconfigurations and enable security teams to secure their applications.
Widgets: The ServiceNow Achilles Heel
To this point, our research detected misconfigurations that could be found by any user. However, the next step in our investigation led us to examine the role of widgets within the ServiceNow environment. We identified widgets as a potential pathway to download sensitive data that appeared to be secure.
The findings of this stage in our investigation will be detailed in the second part of this blog.
About Adaptive Shield
Adaptive Shield is a SaaS Security Posture Management (SSPM) & Identity Threat Detection and Response (ITDR) company, dedicated to enabling organizations to be on top of their SaaS security. Our research team reviews all application configurations to better understand the implications of each setting and the potential risk exposed by misconfigurations. We work with SaaS developers to make SaaS safer.
Our SSPM & ITDR platform integrates with over 160 applications out of the box including ServiceNow security, covering misconfiguration management, human and non-human identity security, and any suspicious behavior in the ecosystem. For more information visit adaptive-shield.com
The post Part 1: Can Just Anyone Access Your ServiceNow Articles? appeared first on Adaptive Shield.
*** This is a Security Bloggers Network syndicated blog from Adaptive Shield authored by Dan Meged. Read the original post at: https://www.adaptive-shield.com/blog/part-1-can-just-anyone-access-your-servicenow-articles/
如有侵权请联系:admin#unsafe.sh
