2024-9-19 14:16:25 Author: cyble.com(查看原文) 阅读量:7 收藏
Key Takeaways
- CISA has added vulnerabilities affecting the Microsoft Windows MSHTML Platform (CVE-2024-43461) and Progress WhatsUp Gold network monitoring solution (CVE-2024-6670) to its Known Exploited Vulnerabilities catalog.
- Proofs of Concept and observed exploits of these vulnerabilities mean that users should update affected products as soon as possible.
- Progress WhatsUp Gold was observed under exploit within hours after a Proof of Concept emerged, suggesting an urgent need to patch this 9.8-severity vulnerability.
- Cyble researchers have detected 381 internet-exposed Progress WhatsUp Gold instances; patching these instances is critical.
- Microsoft has patched two high-severity vulnerabilities chained together in Windows MSHTML platform spoofing attacks.
Overview
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added vulnerabilities affecting the Microsoft Windows MSHTML Platform and Progress WhatsUp Gold network monitoring solution to its Known Exploited Vulnerabilities catalog (KEV) after proofs of concept (PoCs) emerged, and security researchers observed active exploits of the vulnerabilities.
We’ll examine the vulnerabilities, the following steps for affected products, and the best practices that all organizations should follow.
CVE-2024-6670: Progress WhatsUp Gold
CVE-2024-6670 is a critical 9.8 severity SQL Injection vulnerability affecting versions of Progress WhatsUp Gold released before 2024.0.0.
The vulnerability in affected versions of the network monitoring software allows an unauthenticated attacker to retrieve the user’s encrypted password if the application is configured with only a single user.
Exploits began within hours after a Proof of Concept for the vulnerability was made available publicly on GitHub, even though a patch had been available for the vulnerability since mid-August, suggesting that some users were slow to update affected versions.
Trend Micro researchers detected remote code execution (RCE) attacks against WhatsUp Gold that exploited the Active Monitor PowerShell Script, leveraging CVE-2024-6670 and CVE-2024-6671, a companion vulnerability also rated 9.8.
Both vulnerabilities are patched starting with version 2024.0.0.
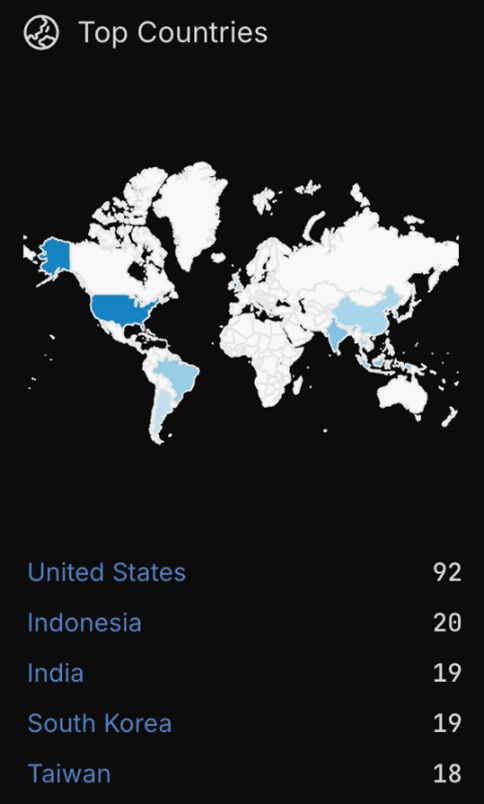
The Cyble ODIN scanner detected 381 internet-exposed Progress WhatsUp Gold instances, as shown in the figure below. Progress WhatsUp Gold is urged to upgrade as soon as possible and check for indicators of compromise in their environments.

CVE-2024-43461: Microsoft Windows MSHTML
CVE-2024-43461 is a high-severity (CVSS: 8.8) vulnerability in the Microsoft Windows MSHTML Internet Explorer browser engine platform containing a UI misrepresentation flaw that allows attackers to spoof web pages. This vulnerability was exploited in conjunction with CVE-2024-38112.
Microsoft has announced the retirement of Internet Explorer 11 and deprecated Microsoft Edge Legacy. However, MSHTML, EdgeHTML, and related scripting platforms remain supported. MSHTML is used in Internet Explorer mode in Microsoft Edge and other applications via WebBrowser control. WebView and some UWP apps utilize EdgeHTML. Updates for vulnerabilities in MSHTML and scripting platforms are included in IE Cumulative Updates, but EdgeHTML and Chakra updates are not.
CVE-2024-43461 was exploited in conjunction with CVE-2024-38112 before July 2024. A fix for CVE-2024-38112, released in July 2024, disrupted this attack chain. To ensure complete protection, customers should install both the July 2024 and September 2024 security updates.
Affected Windows products include:
- Windows Server 2012
- Windows Server 2012 R2
- Windows Server 2008 R2
- Windows Server 2008
- Windows Server 2016
- Windows 10
- Windows Server 2022
- Windows 11
Conclusion
The recent addition of these vulnerabilities to the CISA KEV database underscores their active exploitation. These vulnerabilities can lead to severe security breaches, including unauthorized access to sensitive information and effective spoofing of web pages. Owners of affected products are urged to update their systems with the latest patch released by the official vendor.
Cyble Recommendations
Cyble urges the following best practices:
- Ensure that you install the latest security updates for all affected systems and regularly check for and apply updates to stay protected against known vulnerabilities.
- Implement robust monitoring to detect any unusual activity that could indicate the exploitation of these vulnerabilities. This includes monitoring network traffic, system logs, and user behavior.
- Review and strengthen your security configurations, including access controls and permissions. Ensure that applications are not unnecessarily exposed to the internet and that strong authentication mechanisms are in place.
- Perform regular vulnerability assessments and penetration testing to identify and address potential security weaknesses before they can be exploited.
- Develop a comprehensive patch management strategy that includes inventory management, patch assessment, testing, deployment, and verification.
- Implement proper network segmentation to avoid exposure of critical assets over the internet.
- Maintain an up-to-date inventory of all internal and external assets, including hardware, software, and network components.
Related
如有侵权请联系:admin#unsafe.sh