2024-9-19 02:0:56 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Article
An overview of how to investigate workplace violence incidents, make an assessment, and intervene when necessary
By: Dr. Marisa Randazzo, Ph.D.
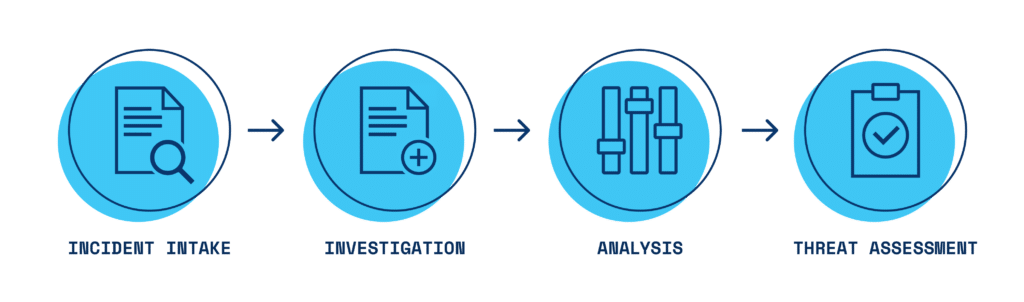
The purpose of the threat management process is to evaluate threatening or alarming behavior, determine whether there is any actual threat or risk, and, if so, figure out how to mitigate it. As depicted in the workflow graphic below, the specific steps in the threat management process are as follows:
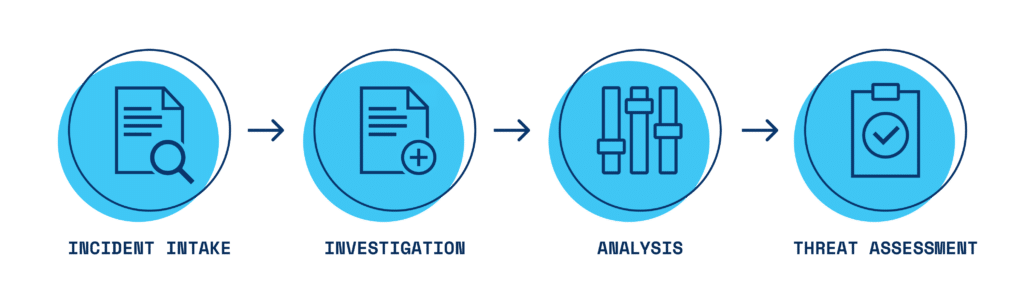
Incident intake and investigation
Intake incident report and answer screening questions to determine if the threat management process is needed. If so, then proceed with the remaining steps.
Investigate the incident, Person of Interest (POI), their behavior, and information about their situation or circumstances
Analysis and assessment
Analyze the information by answering specific investigative questions;
Make an assessment by answering specific assessment questions. If the assessment is that the POI is on a pathway to violence or otherwise poses a threat of violence, suicide, or sabotage, then proceed to threat intervention and protection.
Threat intervention and protection
Implement a threat intervention and protection plan to intervene and reduce the risk from the POI (i.e., a threat management plan); monitor how the intervention is working. If the assessment is that the POI is not on the pathway to violence or does not pose a threat of violence, the threat assessment investigation can be closed and/or referred to another department or agency.
Update the assessment and revise the threat intervention and protection plan if needed; continue to monitor and re-assess until the risk is reduced; and close the case once the threat level is reduced to a level that is acceptable to the organization.
What’s in a name?
One decision that organizations can make when setting up a threat management process is what to call the person they are assessing. Teams vary in which term they use. If your organization already has a database to capture security events or incidents, you may already have a term that you can use to refer to the person you are assessing. If not — or if you want to choose a different term — here are some options to choose from:
- Entity
- Person of Interest (POI)
- Person in Question (PIQ)
- Subject of Concern (SOC)
- Person of Concern (SOC)
- Person Being Assessed (PBA)
- Threatening Person or Situation (TBS)
- Threat Actor (TA)
- Potentially Dangerous Person (PDP)
- Threatening Person (TP)
The specific term that your organization chooses is not critical. What is more important is using the same term throughout the process (whatever term you choose) so that the threat management process is easy to follow and easy to apply to any particular case. Many of the organizations I’ve worked with use either “Person of Interest” or “Entity.” For consistency throughout the remainder of this book, I’ll refer to the subject of a threat assessment investigation as “Person of Interest” or “POI.”
Case example: Incident intake and investigation
In one organization I worked with, a CEO got a threatening email and alerted his executive protection detail. The detail leader created an incident report about the threatening email and forwarded the report to the organization’s Threat Management Team. The threat management team followed the threat management process as detailed below:
Intake incident information and answer screening questions to determine if the threat management process is needed.
The threat management team reviewed the threatening email sent to the CEO from Derek Davidson. In Davidson’s email, he threatened to kill him and any other employees he could find at their headquarters if he was not given a new job with the organization; he gave the CEO 10 days to respond with a job offer. In the email, he also detailed various locations at the headquarters building and in the surrounding area where he felt he could lay in wait and get a good shot at the CEO and other employees as they walked from the parking area to the building.
The threat management team also ran a search on Davidson’s name and identifiers in the organization’s security database. They found a prior incident report about Davidson when he was still an employee after he sent a series of emails to the organization’s board members criticizing how the organization treated veterans and making recommendations for improvement. That prior incident report had been referred to human resources to address the behavior; no further investigation had been conducted by the security department. The threat management team answered screening questions about Davidson’s threatening email and determined that they needed to use the threat management process to investigate, assess, and mitigate the threat.
The team proceeded to the next step in the threat management process: investigate the incident, the Person of Interest (POI), their behavior, and information about their situation or circumstances.
The threat management team gathered information from multiple sources, including the departments within the organization — including HR, Davidson’s personnel file, Davidson’s former supervisor, and the Employee Assistance Program. They discovered that Davidson had left his job at the organization 6 years prior (to move to a different city with his fiancée) and was eligible for re-hire. He had applied for a new position within the organization but did not get the position. He applied for another position but was turned down for that job as well. It was after he was turned down a second time that Davidson emailed his death threat to the CEO.
They also gathered information from external sources, including running a criminal background check and social media check. They discussed possibly talking with Davidson and decided they would do so if they could identify someone in the organization who still had a positive relationship with Davidson, which they found by reviewing his recent job applications (Davidson listed a current employee at the organization among his references).
Case example: Analysis and threat assessment
After the investigation, the team moved to the next step in the threat management process: Analysis of the information in the investigation. The threat management team analyzed the information it had obtained in order to “connect the dots” — looking for any indications that Davidson was on a pathway to violence, identifying what problems or circumstances might be driving him to see violence as a solution, and, identifying any missing information, to see if further information gathering efforts are necessary.
After the analysis, the team moved to the next step in the threat management process: make an assessment to determine if the POI poses a threat of violence, suicide, or sabotage — or is on a pathway to violence, suicide, or sabotage.
Based on their analysis of the information gathered in the case, the threat management team answered the assessment questions and determined that Davidson was on a pathway to violence – with a plan and possibly at the preparation stage for engaging in violence.
Case example: Threat intervention and protection
As the team assessed Davidson as being on a pathway to violence (meaning, the team felt that Davidson posed a threat of violence to the CEO and other employees), the team needs to proceed to the remaining steps in the threat management process, as follows:
Implement a threat intervention and protection plan to intervene and reduce the risk.
The threat management team focused on the problems and circumstances that they thought were driving Davidson to resort to violence or to see violence as a desirable way to solve his problems.
Update assessment and threat intervention plan if needed.
In Davidson’s case, the threat management team kept a close eye on how the interventions were working and developed a backup plan in case Davidson’s behavior deteriorated, which would have involved bringing Davidson for an emergency psychiatric evaluation to contain an imminent threat.
Once Davidson had been connected with mental health resources for several weeks and had a colleague who was checking in with him on a regular basis, the threat management team updated the assessment by answering the assessment questions again. The team felt at that time that Davidson no longer posed a threat of violence to the CEO or other employees. The team put mechanisms in place to continue to monitor Davidson for several months beyond that.
Close the case once the threat level is reduced to a level that is acceptable to the organization.
After several months of monitoring and multiple updated assessments that showed that Davidson no longer posed a threat of violence, the Threat Management Team closed Davidson’s threat management case. They documented the investigation and intervention in their system of record, so they had a clear history of what worked to reduce Davidson’s risk, in the event he became a concern again.
What’s next?
In the next article of this series, we get into details of the first step in the threat management process: Intake of incident reports and screening them to determine if you need to use the threat management process.

Dr. Marisa Randazzo, Ph.D.
Executive Director of Threat Management
The post Navigating the Workplace Violence Threat Management Process appeared first on Ontic.
*** This is a Security Bloggers Network syndicated blog from Articles - Ontic authored by Dr. Marisa Randazzo, Ph.D.. Read the original post at: https://ontic.co/resources/article/navigating-the-workplace-violence-threat-management-process/
如有侵权请联系:admin#unsafe.sh