![]()
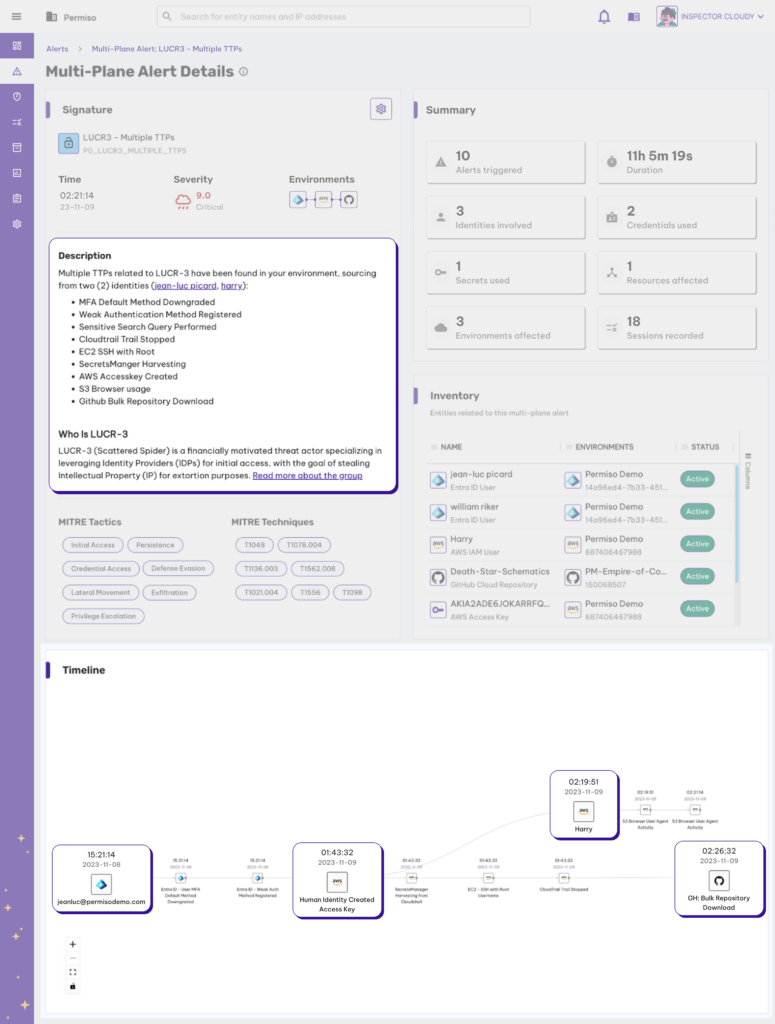
Permiso today added a Universal Identity Graph engine that makes it simpler for cybersecurity teams to visually map the relationship between individuals, applications and systems to better enforce zero-trust IT policies.
Company Co-CEO Jason Martin said this latest offering combines multiple entity and runtime graph technologies to map an IT environment without requiring organizations to deploy and manage a graph database. Queries can then be launched using the GraphQL query language to discover the overall security posture of the organization, he added.
That approach enables cybersecurity teams to discover the relationship between human and non-human identities associated with, for example, a specific software component, noted Martin.
Permiso’s Universal Identity Graph tracks activity back to the identity that initiated it, even when shared credentials are being used. By monitoring access patterns and behavioral anomalies, the Universal Identity Graph makes it simpler to surface suspicious activity indicative of, for example, a stolen set of credentials being unusually used to access applications or services.
Previously, Permiso has developed a security posture management platform that uses machine learning algorithms to baseline behaviors and apply more than 1,000 rules for detecting anomalous behavior. Those capabilities are critical because cybercriminals are increasingly using stolen credentials to access applications and services for long periods as part of an effort to avoid detection. The goal is to make it appear they are a legitimate user of those applications and services before they start to exfiltrate data or inject malware into the IT environment. Otherwise known as “living off the land,” that approach is also often used to steadily escalate privileges in a way that ultimately inflicts the most amount of damage possible.
Last year Permiso uncovered a cyberattack in which cybercriminals were employing text messages to steal credentials that enable them to access Amazon Web Services (AWS) infrastructure.
In an era where many employees now routinely access applications and services from multiple remote locations, it has become more challenging for cybersecurity teams to detect anomalous behavior without the aid of machine learning algorithms, noted Martin.
In addition, as cybersecurity teams assume more responsibility for governance, risk and compliance (GRC) functions, the need for an identity graph to facilitate an audit becomes more apparent, he added.
It’s not clear at what pace organizations are adopting zero-trust principles for managing IT but achieving that goal isn’t possible without an ability to manage identities. Cybersecurity teams need to be able to work closely with IT operations teams to dynamically enforce zero-trust controls at a much more granular level.
Ultimately, it’s only a matter of time before most organizations adopt zero-trust IT principles. The challenge is that making that transition is more of a process than an event. As such, it might take a year or more for an organization to consistently apply these types of controls across the entire organization. However, the more insights an organization has into the relationships between users, machines and applications, the easier that transition becomes.
Recent Articles By Author