Parsing command line invocations is fun, because it’s impossible to do it right (all the time).
Imagine a test DLL that exports a function called foobar. We place this DLL in c:\test directory and name it like this:
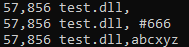
test.dll, #666
We can then use rundll32.exe to execute the foobar function using the following syntax:
rundll32 "c:\test\test.dll, #666", foobar
A different version can use the following name:
test.dll,abcxyz
with the invocation:
rundll32 "test.dll,abcxyz", foobar
We do need quotes, because rundll32.exe does not accept file names with a ‘coma’ in them (for obvious reasons), and the full path is not needed if we are in the same directory, but the gist is that these are all proper DLL file names!:
What your sophisticated regexes extracting DLL name and API’s ordinal number, or API name from this sort of invocations tells you today?
And then here’s another case for your consideration – create a test DLL with the following exports:
- A
- W
- AA
- AW
- WA
- WW
When you run the following invocations:
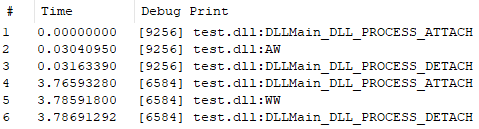
rundll32 c:\test\test.dll, A
rundll32 c:\test\test.dll, W
– which of these 6 exported functions will get executed?
I have provided an answer to this question a few years ago, and here’s the DebugView output:
The bottom line is that you can’t use regexes for parsing command line invocations w/o running into many corner cases.
