2024-9-23 16:39:32 Author: perception-point.io(查看原文) 阅读量:11 收藏
Quishing, or QR code phishing, is quickly advancing as threat actors adapt their tactics to bypass email security QR scanners. Quishing has become one of the fastest growing email threat vectors, by introducing QR codes into phishing campaigns, threat actors added an additional layer of evasion, making it harder for traditional security solutions to detect. But now as many cybersecurity vendors have already followed Perception Point’s lead in implementing QR scanners, “Quishing 2.0” attacks have emerged – and they’re more evasive than ever.
One Not-So-Small Step for Quishing: New Evasion Method
In a new quishing campaign discovered by Perception Point’s security research team, threat actors took QR code phishing to a whole new level. This highly complex attack exploits widely trusted platforms like SharePoint and online QR scanning services, combining them in a way that evades almost every email security solution today (almost).
To fully understand the complexity of Quishing 2.0 attacks, we will first walk through the target’s journey before diving into the innovative evasion tactics adopted by the threat actors.
From Email to Exploit: A Walkthrough of a Quishing 2.0 Attack
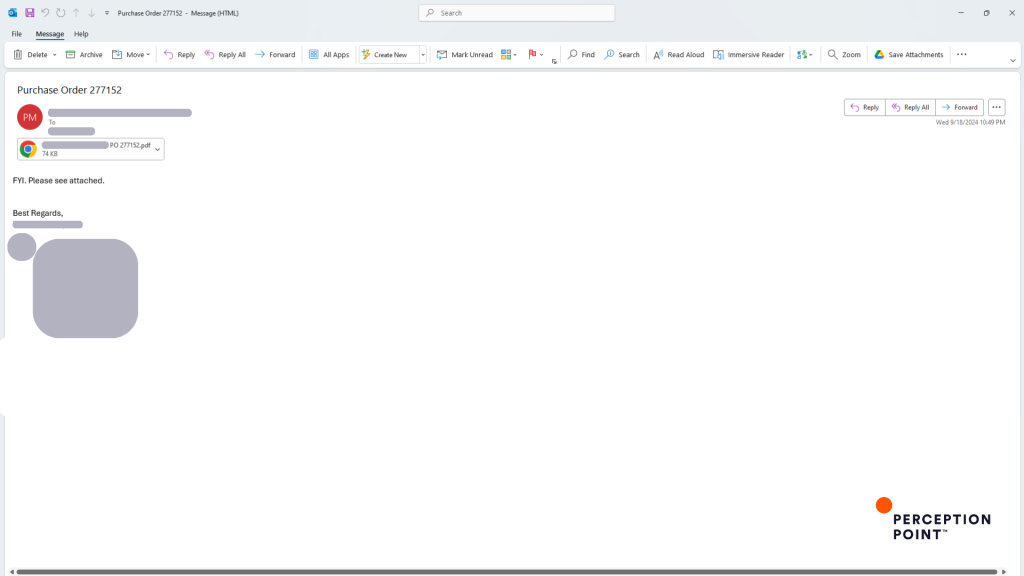
Email Message
The target receives an email appearing to be from a real business in some cases the attacker would even spoof their domain and impersonate a business partner the target is familiar with. The subject line and attached PDF file suggest it’s a Purchase Order (PO).
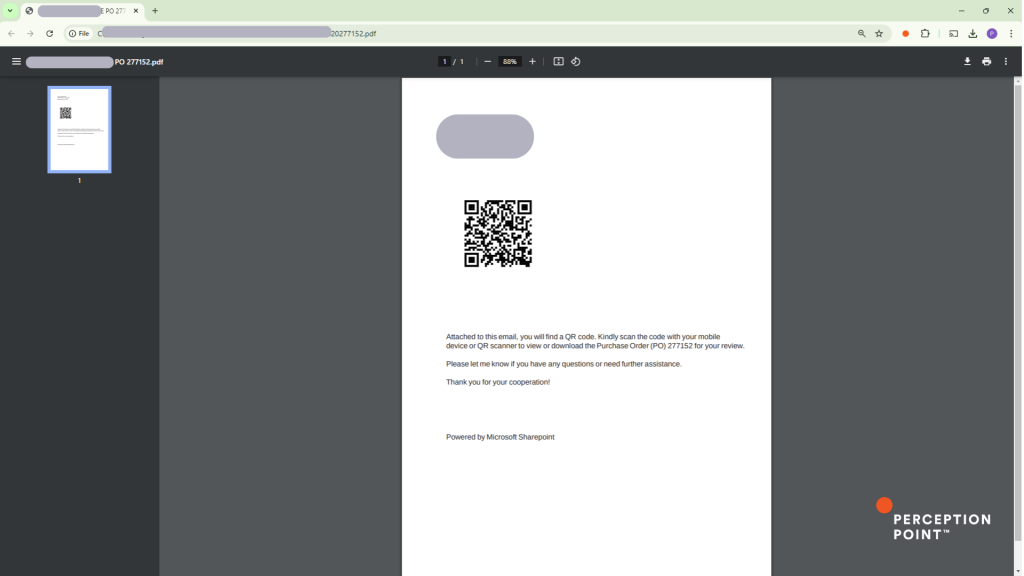
PDF Attachment
Inside the PDF document, the target sees a large QR code along with instructions to scan it in order to view the full purchase order. The PDF includes the physical address of the impersonated business, further reinforcing its credibility.
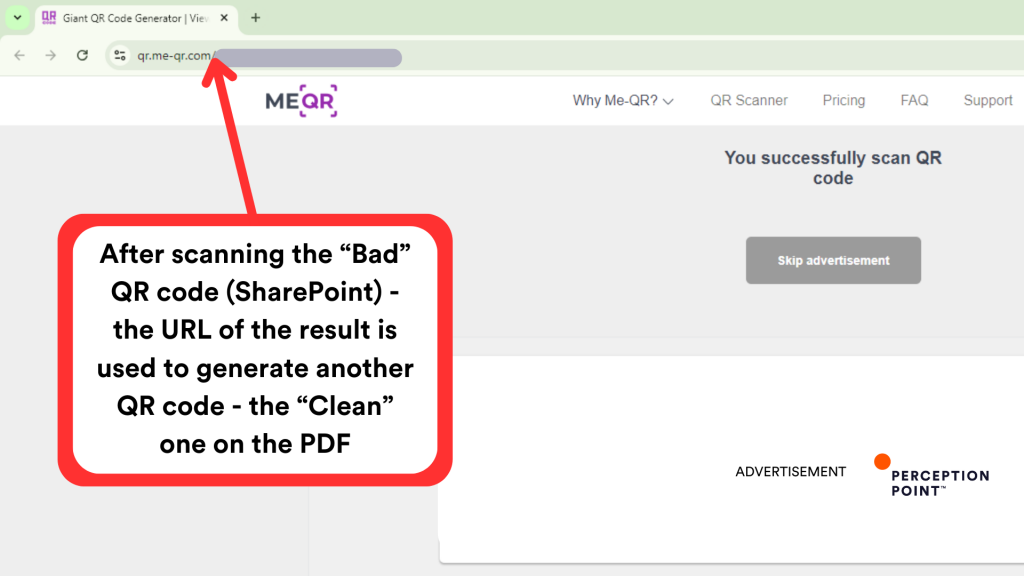
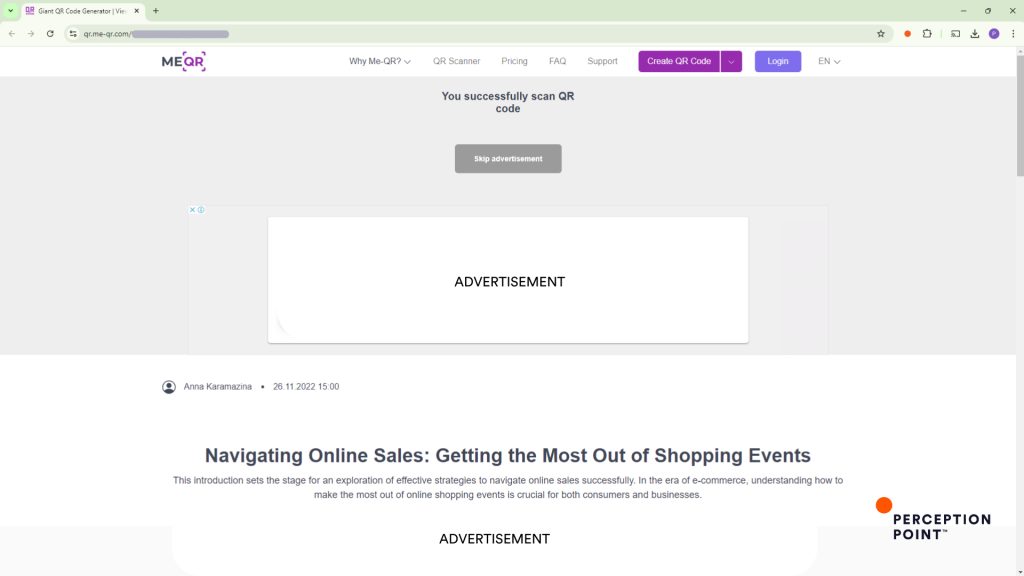
QR Scanning Service (Me-QR)
When the target scans the QR code, they are redirected to me-qr.com, a legitimate QR code creation and scanning service. The page indicates that the QR code was successfully scanned, with a button labeled “Skip Advertisement.” This step adds another layer of authenticity, as it uses a trusted service. We’ll touch on this step more when discussing the attackers’ tactics.
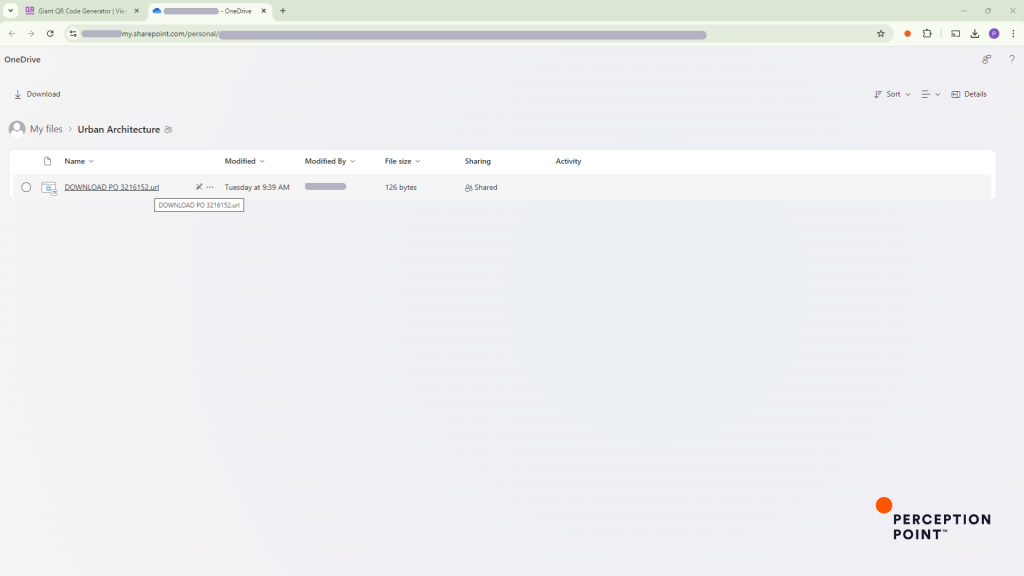
SharePoint Folder
Clicking the “Skip advertisement” button leads the recipient to a real SharePoint page, seemingly connected to the impersonated business – based on the URL we believe this Microsoft account was created using the spoofed domain that was used to deliver the email. This is where the attack takes full advantage of trusted services to mask malicious intent.
The recipient sees what appears to be a .url file (basically a link in the form of a file) with the name of the PO. The file was uploaded to SharePoint by a user with the same name as the one who emailed the target.
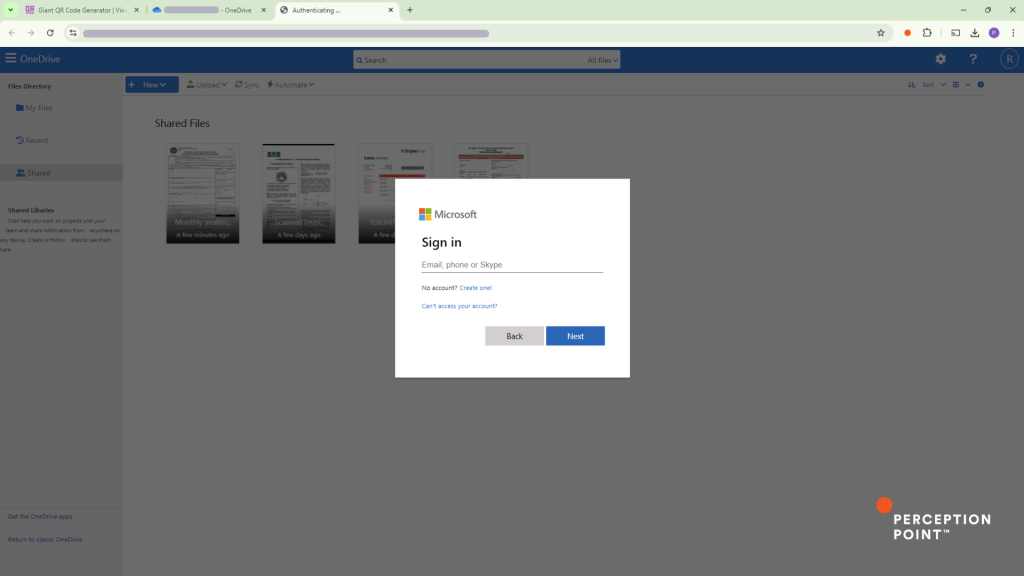
.url File and M365 Phishing Page
If the recipient clicks on the file in SharePoint, they are redirected to the final payload and the first real malicious one: a fake OneDrive page. The Microsoft 365 login form, designed to steal the victim’s credentials, appears over what cosmetically seems to be files of scanned invoices from the PO in the background.
The Good, the Bad and the SharePoint: Quishing Inception
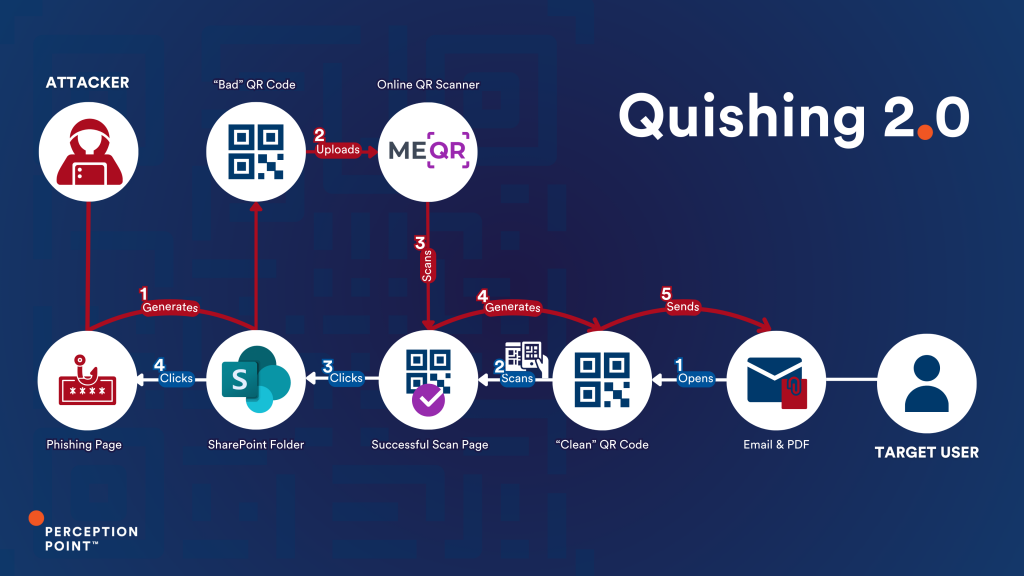
Before delivering the email to the target, the threat actors came up with an innovative and unique evasion technique that hides the malicious payload behind multiple layers of legitimacy. Quishing 2.0 actually involves two QR codes!
Let’s break it down.
The first QR code, to be used in the “back-end” of the attack, leads to the legitimate SharePoint page (associated with a compromised or spoofed business account) that will lead to the malicious phishing page. For the sake of simplicity let’s call this one the “Bad” QR code. We can see so far this is pretty much the average quishing scheme but instead of pointing it directly to the phishing page the threat actors add a “legitimate” hop (SharePoint).
The attacker then takes the “Bad” QR code and uploads it to an online QR scanning service, like me-qr.com, this kind of services allow users to submit an image (JPEG/PNG) with a QR code and extract the URL for them.
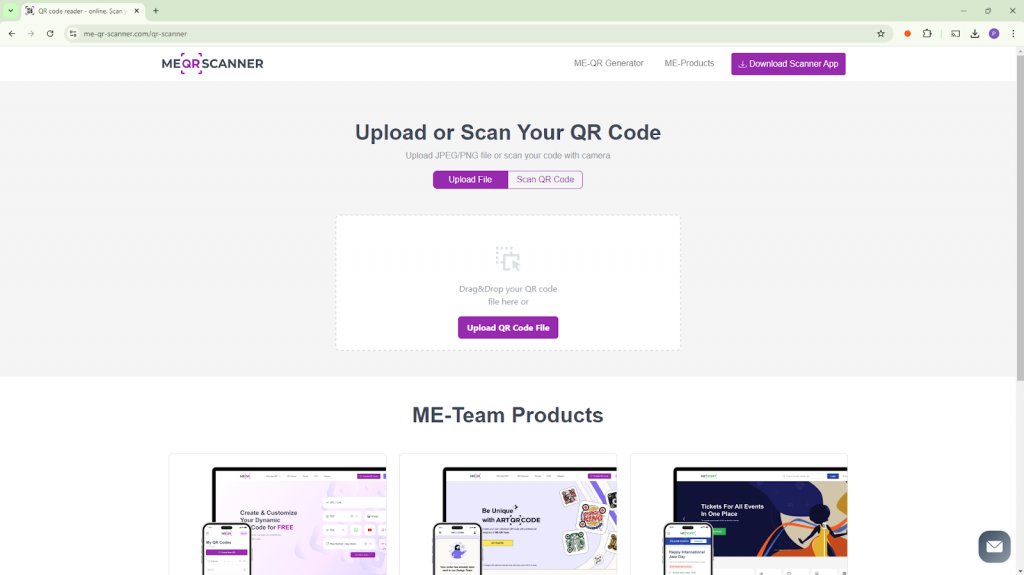
Before taking the user to the destined URL the scanner service first shows an advertisement and a prompt saying the QR code was scanned successfully, clicking a button to skip the ad will redirect the user to the URL behind the QR code.
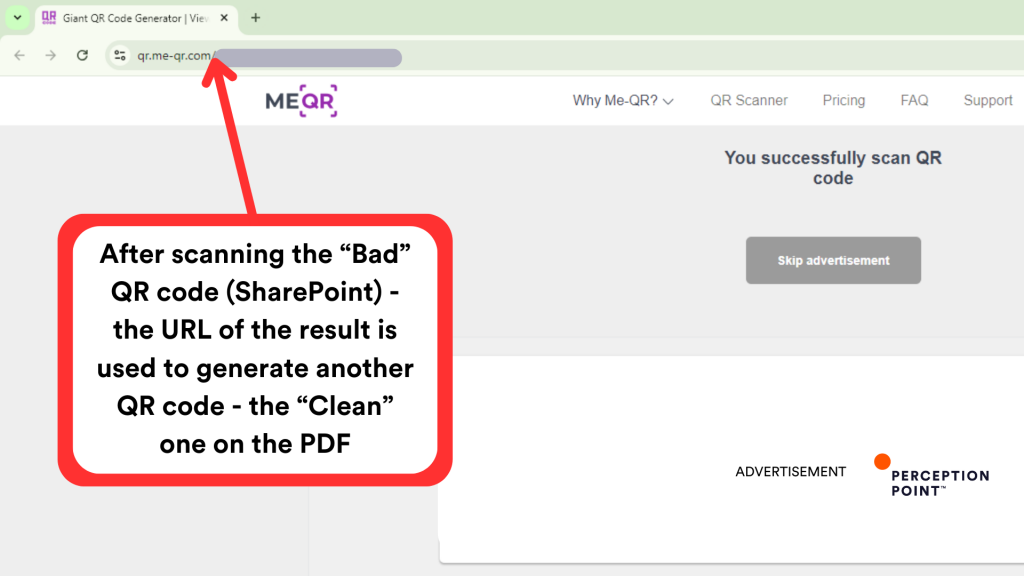
The threat actors took the very URL from this result/ad page and generated a second QR code from it – the “Clean” QR code. This is the “front-end” QR code, the one that targets will ultimately see and interact with on the PDF attachment.
The “Clean” QR code links to the result on me-qr.com and together with the prompt about the successful scan, appearing completely legitimate to the target and bypassing almost any initial email security scans.
The sophistication of Quishing 2.0 attacks lies in the multiple evasion tactics employed by the threat actors. Using 2 QR codes, a legitimate scanning service, and a real SharePoint account, they create multiple layers of legitimacy that most email security systems would not follow through. Each element – the clean QR code that appears harmless, the trusted QR scanning service that adds a layer of authenticity, and the use of a widely trusted platform – combines to make the email appear credible to both users and security solutions. However, Perception Point’s Advanced Email Security still was to prevent it before any harm was done – but how?
Decoding Quishing 2.0 with Dynamic URL Analysis and Computer Vision
Dynamic URL Analysis plays a crucial role in breaking down the layers of Quishing 2.0 and identifying the actual malicious content, even when the target is sent through legitimate services like QR scanners and SharePoint. Perception Point goes beyond surface-level inspection by tracking the journey and scanning every destination URL in real time before the email gets to the user.
But what truly sets Advanced Email Security apart is our Advanced Object Detection Model, designed to combat evasive, two-step phishing techniques like this. Using computer vision, the model analyzes the content of webpages just as a user would see them, detecting clickable elements such as buttons (“skip advertisement”) or login forms. Paired with the Recursive Unpacker, Perception Point automatically clicks through these elements to trace the full path of the attack, uncovering the malicious payloads hidden beneath layers of seemingly legitimate services and QR codes.
Using this multi-layered detection stack, Perception Point provides the most robust, real-time protection against quishing attacks of all types.
如有侵权请联系:admin#unsafe.sh
