Recently, our team of analysts discovered a sample of a yet-unknown ransomware that they dubbed Kransom. The malware employed the malicious DLL-sideloading technique to hijack the execution flow of an .exe file belonging to the popular game Honkai: Star Rail. Here is everything we have on the threat so far.
Initial Infection Vector
View the sandbox session for detailed analysis.
The Kransom ransomware attack began with a deceptive archive containing two files: an executable and a DLL (Dynamic Link Library) file.
The executable was signed with a valid certificate from COGNOSPHERE PTE. LTD, the publishing company for Honkai: Star Rail, a popular RPG.
DLL Side-Loading Technique
Kransom employs a technique known as DLL side-loading to evade detection and inject its malicious payload. The method involves loading a malicious DLL into the process of a legitimate application.
Upon launching the legitimate executable named “StarRail.exe”, the user triggers the loading of the malicious DLL (see analysis of StarRailBase.dll), which is responsible for initiating the infection and encrypting the victim’s files.
File Encryption Method
Kransom utilizes a simple XOR encryption algorithm with a weak key (0xaa) to encrypt files on the infected system.
ANY.RUN’s sandbox helps you track all the encrypted files and see their contents.
Ransom Note
Following successful file encryption, Kransom drops a ransom note that instructs the user to contact “hoyoverse” for solutions.
This is a social engineering tactic designed to impersonate the game’s legitimate developer, Hoyoverse, and extort money from victims.
Collecting Threat Intelligence on Kransom Ransomware
To stay updated on the latest Kransom attacks and enrich your investigations to this and other threats, use Threat intelligence Lookup.
The service pulls threat data from thousands of public malware and phishing samples analyzed in the ANY.RUN sandbox on a daily basis.
It lets you search its database using over 40 different parameters, helping you zero in on threat using different details like registry keys, IP addresses, mutexes, and more.
Here is an example of a query you can use to find more samples of Kransom that use the DLL-sideloading technique:
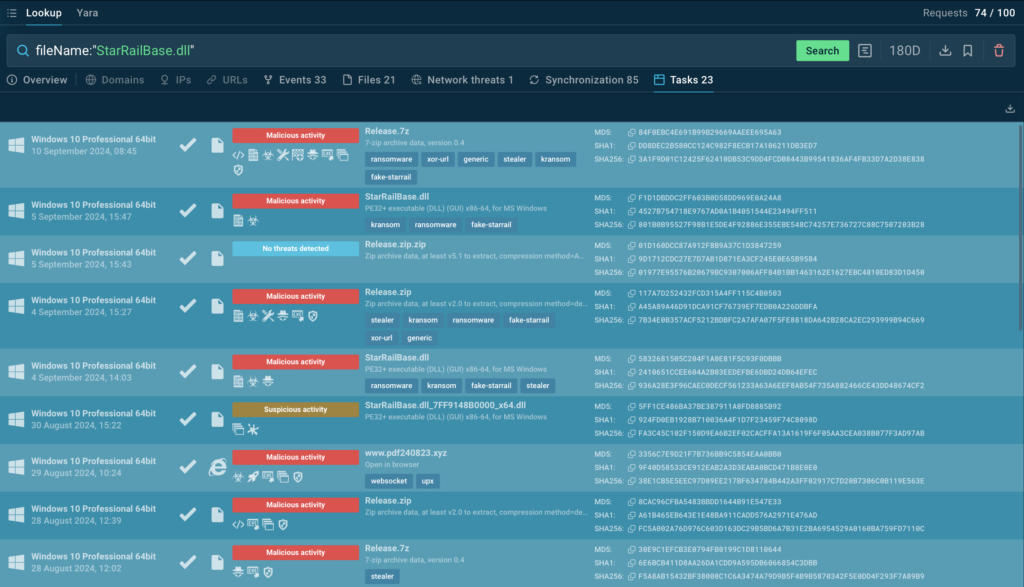
The service returns more than 20 sandbox sessions that you can explore along with synchronization events and files that match the query.
Conclusion
The targeting of games like Honkai: Star Rail in ransomware attacks suggests a potential risk of threat actors using similar methods with other popular software. Organizations need to stay alert and take proactive steps to protect their systems. This includes being careful with downloads from unknown sources, receiving official software updates, and using reliable tools like ANY.RUN’s Interactive Sandbox and Threat Intelligence Lookup as part of a layered security architecture.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
