2024-9-24 18:37:22 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
Last month, a threat actor used stolen credentials in an unsuccessful attempt to access a client’s One Drive account. On the surface, this was just another threat actor attempting an account takeover attack that was detected by Adaptive Shield’s ITDR capabilities and denied access by our customer’s security team. However, a deeper investigation revealed that this attack was part of a much larger campaign targeting many other customers and global companies.
Sophisticated Spear Phishing Attack
The SaaS attack’s roots were found in a Spear Phishing attack. Spear Phishing is a phishing technique that uses social engineering to target specific individuals.
In this case, executives and high-privileged users received an email alerting them that someone had shared a document with them. The user was asked to log in to download the file.
This is a fairly common phishing technique. However, this phishing email had some major differences which made it much more effective. Most phishing emails try to trick the user by using a similar URL name to that which they are looking for. They might spell microsoft.com with a “0” instead of the “o,” or spell google.com with an extra “g” so it says googgle.com. Alternatively, they might create a URL with an extra word, such as microsoft-security.com. Users looking carefully at these URLs can often identify them as fakes, and most email security solutions catch these types of phishing attempts before they ever make it into the user’s inbox.
Threat actors used a relatively new obfuscation technique that uses Google Accelerated Mobile Pages (AMP). In an AMP, the initial link is a page hosted on Google.com, which allows the initial phishing email to slip past Secure Email Gateways (SEG). Once the user clicks on the link, the user is redirected to the target page.
In this attack, users were redirected up to 20 times through a series of Google URLs, tinyurl links, bit.ly links, and an attacker relay infrastructure. Many of the redirects used decoded URLs to make it more difficult to see where the user was being redirected. At the end of the redirects, users found themselves on a Microsoft or Docusign brand impersonation page.

Figure 1: The string of redirected URLs that included the name of the targeted company
Once the user arrived on the Microsoft or Docusign branded page, they were shown the name of the file, which was personalized to them or their company, and prompted to log in. After entering their credentials, they received the document, while the threat actors gained credentials to access the application.
When the user entered their information, it was relayed to the attacker. Unlike other more advanced adversary-in-the-middle (AiTM) attacks that we have seen, these attackers did not use the victim’s user agent. Instead, they used different user agents, which was one of the anomalies that helped us detect the threat.
Next, the threat actor captured the token and used it in their attempt to log into their victim’s account via VPN. While there are many things a threat actor can do once they have accessed the app, we believe that this threat actor was targeting email accounts to perform typical BEC activities.

Figure 2: Personalized Microsoft OneDrive Page

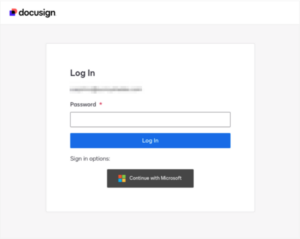
Figure 3. Personalized Docusign Page
A Far Reaching Campaign
After investigating this attack, we wanted to learn more. Adaptive Shield’s ITDR analyzes every IP being used to access the SaaS environment and looks for suspicious anomalies. The first thing that caught our attention about this incident was the IP with a suspicious certificate that had a domain masquerading as Microsoft (*.microsoftonline.aaaloohf.click). We looked for these IPs and similar patterns on URL Scan to gain additional insight into the early stages of this campaign.
We discovered that there were hundreds of DGA-generated domains with a similar structure targeting hundreds of organizations. This dedicated infrastructure was located primarily on Digital Ocean servers and has been used to target international organizations since 2023.
(A Domain Generation Algorithm (DGA) is a technique used by malware to create multiple domain names for command-and-control servers, making it difficult to block and enabling persistent communication with compromised systems.)
A second tool, Virus Total, led our team to a number of threatening IP Addresses (included below). Those IP addresses are on Adaptive Shield’s watchlist, and any attempts to access an app from there will trigger immediate alerts.
Securing SaaS Applications from These Types of Attacks
Phishing attacks that capture user SaaS credentials are remarkably common. Socially engineering users to hand over their usernames and passwords is not all that difficult, which leads to breaches, data leaks, and other threatening acts. However, applications with secure configurations are insulated against these types of unauthorized entry.
A properly configured app has multi-factor authentication (MFA) and Single Sign-on (SSO) turned on. However, adversary-in-the-middle attacks can get around these measures. FIDO2 MFA and automated threat detection monitoring can improve your ability to withstand these attacks.
Allowlisting IP addresses, enforcing role-based access controls (RBAC), and following the principle of least privilege (POLP) are additional measures that shrink the attack surface and limit the damage if a threat actor breaks through.
SaaS Security Posture Management (SSPM) tools, like Adaptive Shield’s platform, monitor configurations, search for drifts, and help security teams harden their access controls to prevent these types of account takeover attacks.
When threat actors are able to enter into an application, Identity Threat Detection & Response (ITDR) tools come into play. They monitor all events, looking for indications of compromise (IOC). In this case, Adaptive Shield’s ITDR used various AiTM detections to detect the attacker’s login. It enriched the available data using publicly available information and recognized the IP as a suspicious launching point for attacks. From there, it classified the login attempt as a threat and instigated an incident response process. Had the threat actor managed to breach the system, other detection in place would have alerted the team if the attacker had touched mailbox rules or registered an additional MFA method.
For organizations concerned about SaaS threats, there is no better tool than SSPM and ITDR working together. Their ability to ensure application configurations are hardened and detection capabilities work in tandem to eliminate threats and keep SaaS applications safe.
If you are concerned about this breach, we recommend searching the logs for all your SaaS applications for the following IOCs.
IOCs:
IP Addresses:
137.184.127.24
24.144.89.3
159.65.208.18
209.38.160.113
209.38.146.44
146.190.168.156
64.23.234.137
167.71.42.27
167.71.20.127
157.230.143.51
94.156.65.137
146.190.57.103
167.71.42.27
137.184.47.61
172.105.151.236
164.90.247.173
24.144.69.26
24.144.68.200
Domains:
{company name}.1637677096.website
{company name}.0297705207.website
{company name}.8401053315.website
{company name}.3070796095.website
{company name}.6131190165.website
{company name}.4724459156.website
{company name}.6633186941.website
{company name}.sdceaqhmfjdn.click
{company name}.6062589717.website
{company name}.6942521000.website
{company name}.7649774662.website
{company name}.3556366653.website
{company name}.9260648617.website
{company name}.7649774662.website
{company name}.0904374097.website
{company name}.2144954650.website
{company name}.2871640980.website
{company name}.5939451783.website
{company name}.5760234463.website
{company name}.1502970144.website
{company name}.2871640980.website
{company name}.7676016287.website
{company name}.8142284163.website
{company name}.7676016287.website
{company name}.6010267449.website
{company name}.hvggcompxauabpc.college
{company name}.edntattxycdw.click
{company name}.rcfhfifsxyqd.click
{company name}.nhealfwoitswkvtr.click
{company name}.pjjeotmtugrqqkyu.click
{company name}.kdnegjalsskdybk.college
{company name}.microsoftonline.yfcyasyuevui.click
{company name}.docusign.wtttvlvzwljherxftdit.com
{company name}.4471844.website
{company name}.13322131.website
{company name}.8142284163.website
{company name}.microsoftonline.hwssyjxgevbgawt.college
{company name}.microsoftonline.myybdhrummltsgn.college
{company name}.microsoftonline.rueramfzfsvl.click
{company name}.microsoftonline.garntnaivpyskvc.college
{company name}.yfcyasyuevui.click
{company name}.microsoftonline.hwssyjxgevbgawt.college
{company name}.microsoftonline.tfgiqsyiewtx.click
{company name}.microsoftonline.ojsiyspovtctkypr.click
{company name}.microsoftonline.ilyrhjuqcxxawrq.college
{company name}.thnoasnnvtidmapu.college
{company name}.feds.kdnegjalsskdybk.college
{company name}.microsoftonline.thnoasnnvtidmapu.college
{company name}.microsoftonline.ilyrhjuqcxxawrq.college
{company name}.microsoftonline.garntnaivpyskvc.college
{company name}.microsoftonline.fqflfpgfcaew.click
{company name}.microsoftonline.sdceaqhmfjdn.click
{company name}.microsoftonline.djwvglbxqhql.click
{company name}.microsoftonline.yfcyasyuevui.click
{company name}.microsoftonline.tfgiqsyiewtx.click
{company name}.microsoftonline.nhealfwoitswkvtr.click
{company name}.microsoftonline.edntattxycdw.click
{company name}.microsoftonline.oeeayfwflnlg.click
{company name}.microsoftonline.mgzannxbgbpc.click
{company name}.microsoftonline.zuqnrqnzqortkpa.college
{company name}.microsoftonline.thnoasnnvtidmapu.college
{company name}.microsoftonline.fbinsmmxehlbwxc.college
{company name}.microsoftonline.thnoasnnvtidmapu.college
{company name}.fqflfpgfcaew.click
{company name}.mgzannxbgbpc.click
{company name}.microsoftonline.znefupvwivbhwitr.click/
{company name}.2871640980.website/app6c7e0d9e6da4d0098ce8966af74e6936/66682b2adeb550c7eeafdb80
{company name}.microsoftonline.ojsiyspovtctkypr.click
{company name}.microsoftonline.ibrdcdmrvgfevahx.college
{company name}.microsoftonline.thnoasnnvtidmapu.college
{company name}.microsoftonline.qgbnegonguoluvyu.college
{company name}.microsoftonline.isszdtaluiyi.click
{company name}.microsoftonline.ojsiyspovtctkypr.click
{company name}.microsoftonline.edcgyoswriqp.click
{company name}.microsoftonline.mgzannxbgbpc.click
{company name}.microsoftonline.ojsiyspovtctkypr.click
{company name}.microsoftonline.oeeayfwflnlg.click
{company name}.microsoftonline.ojsiyspovtctkypr.click
{company name}.microsoftonline.rcfhfifsxyqd.click
{company name}.microsoftonline.rueramfzfsvl.click
{company name}.microsoftonline.edntattxycdw.click
{company name}.microsoftonline.sdceaqhmfjdn.click
{company name}.microsoftonline.thnoasnnvtidmapu.college
{company name}.microsoftonline.lqdwdmjfbzqb.click
{company name}.microsoftonline.lqdwdmjfbzqb.click
The post Sophisticated Spear Phishing Attack Falls Flat Against ITDR appeared first on Adaptive Shield.
*** This is a Security Bloggers Network syndicated blog from Adaptive Shield authored by Yoav Kook. Read the original post at: https://www.adaptive-shield.com/blog/sophisticated-spear-phishing-attack-falls-flat-against-itdr/
如有侵权请联系:admin#unsafe.sh
