David Carmiel, CEO, KELA
In today’s digital landscape, ransomware and extortion attacks are a pervasive threat that can bring enterprises to a standstill. These attacks, where malicious actors encrypt and steal critical data and demand ransom for its release and for not leaking it publicly, can cost organizations millions, not just in ransom payments, but also in lost productivity, data recovery efforts, and damage to reputation. However, with KELA’s cyber intelligence platform, enterprises can significantly mitigate these risks, block ransomware attacks, and drive substantial returns on investment (ROI).
The Rising Threat of Ransomware
Ransomware attacks have evolved from crude attempts to extort money into sophisticated, well-coordinated operations that leverage not only data encryption but fear of releasing victims’ sensitive data. During the past year (May 2023-May 2024), KELA has tracked more than 5000 victims of ransomware and extortion actors, the majority of which are from the US, the UK, Canada, Germany and France, accounting for 70% of all claimed victims. This is just a minimal amount as many victims are never getting on the radar.
These attacks are often facilitated by initial access brokers (IABs) and infostealer infections who provide ransomware attackers with a foothold into a target organization. Understanding these primary attack vectors is crucial for developing effective defensive strategies.
For example, in December 2023, after a disclosure of a security incident by the Australian and New Zealand Nissan Corporation and Financial Services, the operators of Akira ransomware claimed to have compromised Nissan Australia, stealing 100GB of data, as seen in an update from Akira’s blog, below.

Akira claims Nissan Australia as a victim
In March 2024, Nissan released a statement on their website, confirming that approximately 100,000 individuals have been impacted by the cyber breach, with as many as 10,000 having had some form of government identification compromised: “The data set includes approximately 4,000 Medicare cards, 7,500 driver’s licenses, 220 passports and 1,300 tax file numbers.”
Based on KELA research, Akira is known to use the cybercrime ecosystem to purchase initial access, usually via compromised VPN credentials, claiming to each compromised victim who paid a ransom that the access to their network was “purchased on the dark web”. It is fair to assume the initial access vector for Nissan may be the same. This access can be bought from initial access brokers, or could be obtained from platforms and cybercrime markets that sell and distribute compromised accounts sourced by information-stealing malware.
Initial Access Brokers: The Gatekeepers of Cybercrime
Initial access brokers specialize in breaching networks and selling access to the highest bidder, often ransomware affiliates. These brokers exploit vulnerabilities, use stolen credentials, or deploy phishing campaigns to infiltrate corporate networks. Once inside, they sell access to ransomware gangs who then execute the final, devastating attack.
For instance, Black Basta’s attack against an Australian technology company, ZircoDATA, in February 2024 was likely facilitated by an Initial Access Broker. In January 2024, KELA noted that Remote Desktop Protocol access to the company was offered for sale by a threat actor who may have then sold the access details to Black Basta. 200 Australian companies were impacted by the breach of this popular document storage business, with tens of thousands of documents leaked. In their blog posts, Black Basta was seen boasting about stealing 395GB of ZircoDATA archives.
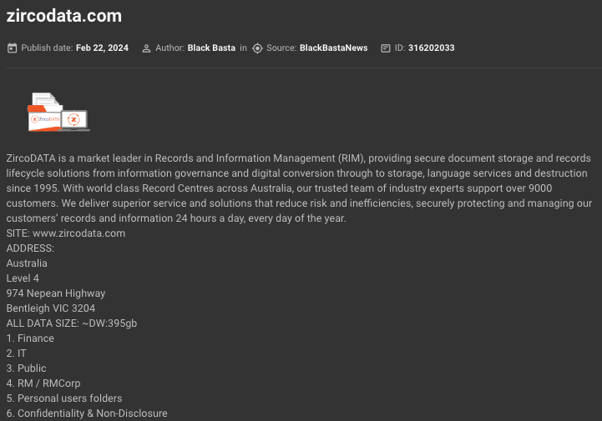
Black Basta claims ZircoDATA as a victim
In May 2024, it was revealed that data included 4,000 documents from Monash Medical Center, including records related to family violence and sexual support clinics, and 60,000 documents related to students of Melbourne Polytechnic.
Infostealer Infections: The Silent Threat
Infostealers are another critical component of the ransomware ecosystem. These malicious programs quietly harvest sensitive information from infected systems, including login credentials, financial data, and proprietary business information. This stolen data facilitates further attacks for ransomware gangs that may obtain login credentials and more on cybercrime platforms.
For instance, UnitedHealth’s CEO confirmed that in a ransomware attack the company experienced in February 2024, the cybercriminals utilized stolen credentials to remotely access Change Healthcare’s Citrix portal, a remote access service that did not have a multi-factor authentication (MFA). The attackers moved laterally through the compromised network and used the access to steal data during 9 days before deploying the ransomware. KELA has seen several instances where compromised credentials to Change Healthcare-owned resources, gained through information stealing malware, were offered for sale or leaked on cybercrime platforms, with some of them appearing only a few days before the attack. While it is not clear if the actor used these credentials to attack the company, it is a possible vector that could be used.
The attack had a devastating effect since multiple cybercriminals ended up involved in the incident. While the data was originally stolen by an affiliate of Alphv (also known as BlackCat), just weeks later, and despite Change Healthcare likely paying a $22M ransom, RansomHub had claimed that they have 4TB of Change Healthcare and United Health’s data, and demanded a new ransom. The victim company has confirmed that it paid a ransom to cybercriminals to protect sensitive data, though it did not specify to whom they paid the ransom: to Alphv (BlackCat), or to RansomHub, which was the second actor to demand a ransom and threaten to leak the data. Per KELA’s check, a post on RansomHub titled “Change HealthCare – OPTUM Group – United HealthCare Group” was no longer available on the site starting the end of April, suggesting that RansomHub could have received the ransom payment and taken down the post. As for the full cost of the attack, one indication is that UnitedHealth advanced nearly $4.7 billion to care providers impacted by the cyberattack!
Leveraging KELA's Cyber Intelligence to Combat Ransomware
KELA’s cyber intelligence platform offers a robust suite of tools designed to collect and analyze information about potential and active cyber threats, empowering organizations to make informed security decisions. Here’s how KELA can change the game in the fight against ransomware:
-
Proactive Threat Detection
KELA’s platform enables organizations to identify and respond to threats before they cause harm. By monitoring cybercrime sources, threat actor communications, and other intelligence sources, KELA provides real-time insights into potential ransomware activities. This proactive stance allows enterprises to strengthen defenses and mitigate vulnerabilities that IABs might exploit.
-
Understanding Attack Vectors
KELA’s comprehensive cyber intelligence provides detailed insights into how initial access brokers and infostealers operate. This understanding helps security teams develop targeted defenses against these specific threats. For example, KELA’s platform can detect and flag suspicious activities and credentials on the dark web, allowing enterprises to take preemptive action.
-
Real-Time Threat Intelligence Sharing
By leveraging KELA’s threat intelligence, enterprises can gain insights into the latest tactics, techniques, and procedures (TTPs) used by ransomware gangs. KELA’s platform facilitates intelligence sharing within the community, helping create a collective defense that makes it harder for cybercriminals to succeed.
-
Incident Response and Recovery
In the event of a ransomware attack, KELA’s cyber intelligence can expedite incident response. Detailed knowledge of the threat landscape provided by KELA helps incident response teams identify the type of ransomware, understand its propagation methods, and develop effective strategies to contain and eliminate the threat.
Driving ROI Through KELA's Cyber Intelligence
Investing in KELA’s cyber intelligence platform not only enhances security but also drives significant ROI. Here’s how:
-
Reducing Financial Losses
Preventing ransomware attacks directly translates to cost savings. KELA’s platform helps avoid ransom payments, data recovery expenses, and potential regulatory fines for data breaches, saving enterprises millions.
-
Preserving Business Continuity
Ransomware attacks can cripple operations, leading to downtime and lost revenue. KELA ensures that enterprises can maintain business continuity by preventing or quickly mitigating attacks.
-
Protecting Brand Reputation
A successful ransomware attack can severely damage an organization’s reputation, leading to loss of customer trust and future business opportunities. By demonstrating a strong security posture with KELA’s advanced intelligence, enterprises can enhance their brand reputation and customer confidence.
-
Optimizing Security Investments
KELA’s cyber intelligence helps organizations allocate resources more effectively. By understanding the most significant threats and vulnerabilities, enterprises can prioritize investments in the most impactful security measures, ensuring optimal use of their security budgets.
Conclusion
In an era where ransomware poses a constant threat, leveraging KELA’s cyber intelligence platform is essential for enterprise security. By proactively detecting threats, understanding attack vectors, and facilitating intelligence sharing, KELA helps organizations block ransomware attacks before they cause damage. This not only protects valuable assets but also drives substantial ROI, making KELA’s cyber intelligence a critical component of modern cybersecurity strategies.