2024-09-23 SNIPBOT RomCom Multi-Stage RAT Samples
 |
| Image courtesy of Palo Alto |
2024-09-23 Palo Alto Unit42: Inside SnipBot: The Latest RomCom Malware Variant
This latest version integrates novel obfuscation techniques and exhibits distinct post-infection activities not seen in previous variants (RomCom 3.0 and PEAPOD/RomCom 4.0).
Key Points:
- Capabilities: SnipBot allows attackers to execute commands and download additional modules onto the victim's system. It deploys an initial signed executable downloader, followed by unsigned EXEs or DLLs.
- Infection Vector: Delivered via email containing links that redirect to the SnipBot downloader. The downloader uses anti-sandbox tricks, including checking the file’s original name and verifying at least 100 entries in the
RecentDocsregistry key. It also employs window message-based control flow obfuscation. - Post-Infection Activity:
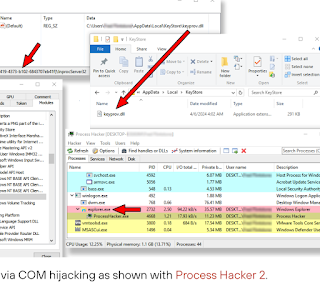
- Downloads additional DLL payloads, injecting them into
explorer.exeusing COM hijacking. Specifically, it registers the malicious DLL (keyprov.dll) as a thumbnail cache library in the registry (HKCU\SOFTWARE\Classes\CLSID). - The primary payload,
single.dll, listens on port 1342 for commands such as deleting registry keys, executing stored DLL payloads, and initiating further updates. - Creates and manages registry keys (
HKCU\SOFTWARE\AppDataSoft\Software) to store encrypted payloads and keep track of updates.
- Downloads additional DLL payloads, injecting them into
- Command & Control: Contacts its C2 domains (e.g.,
xeontime[.]com) to download payloads. Encrypts strings, including the C2 domain and API function names, to evade detection.
File Information
├── 0be3116a3edc063283f3693591c388eec67801cdd140a90c4270679e01677501 atch scan052224 CV.exe- ├── 2c327087b063e89c376fd84d48af7b855e686936765876da2433485d496cb3a4.exe
- ├── 5390ba094cf556f9d7bbb00f90c9ca9e04044847c3293d6e468cb0aaeb688129 Attachment CV June2024.exe
- ├── 57e59b156a3ff2a3333075baef684f49c63069d296b3b036ced9ed781fd42312 Attachment Medical report.exe
- ├── 5b30a5b71ef795e07c91b7a43b3c1113894a82ddffc212a2fa71eebc078f5118 CV for a job.exe
- ├── 5c71601717bed14da74980ad554ad35d751691b2510653223c699e1f006195b8 Atch Data Breach Evidence.pdf Open with Adobe Acrobat.exe
- ├── a2f2e88a5e2a3d81f4b130a2f93fb60b3de34550a7332895a084099d99a3d436 atch List of Available Documents.exe
- ├── b9677c50b20a1ed951962edcb593cce5f1ed9c742bc7bff827a6fc420202b045 webtime-e.exe
- ├── cfb1e3cc05d575b86db6c85267a52d8f1e6785b106797319a72dd6d19b4dc317.exe
- └── f74ebf0506dc3aebc9ba6ca1e7460d9d84543d7dadb5e9912b86b843e8a5b671 резюме.pdf
- Over the past 15 years, as the blog has been around, many hosting providers have dropped support due to stricter no-malware policies. This has led to broken links, especially in older posts. If you find a broken link on contagiodump.blogspot.com (or contagiominidump.blogspot.com), just note the file name from the URL and search for it in the Contagio Malware Storage.