2024-9-26 16:32:9 Author: blog.sekoia.io(查看原文) 阅读量:5 收藏
To read the French version the article, click here.
The European Union (EU) adopted a fundamental directive at the end of 2022 aimed at protecting critical sectors of the European economy from cyber threats. Directive (EU) 2022/2555, better known as NIS2 (Network and Information Security 2), aims to ensure a high common level of cybersecurity for networks and information systems within the EU. This directive outlines the conditions that member states – and the companies located within them – must meet as part of their cybersecurity strategies before October 17, 2024.
Although the theoretical implementation date is set for less than a month from now, the directive is still being transposed by the competent authorities in the member states. Nevertheless, many organizations are already working to test new policies, procedures, and tools to anticipate compliance with the upcoming legislative and regulatory texts. This article, along with our NIS2 white paper, aims to support you in your compliance efforts by detailing the main changes brought about by the directive, clarifying the relationship between NIS2 and the ISO27001 framework, and explaining how Sekoia.io can assist you with these points.
Table of contents
NIS2: why and for whom?
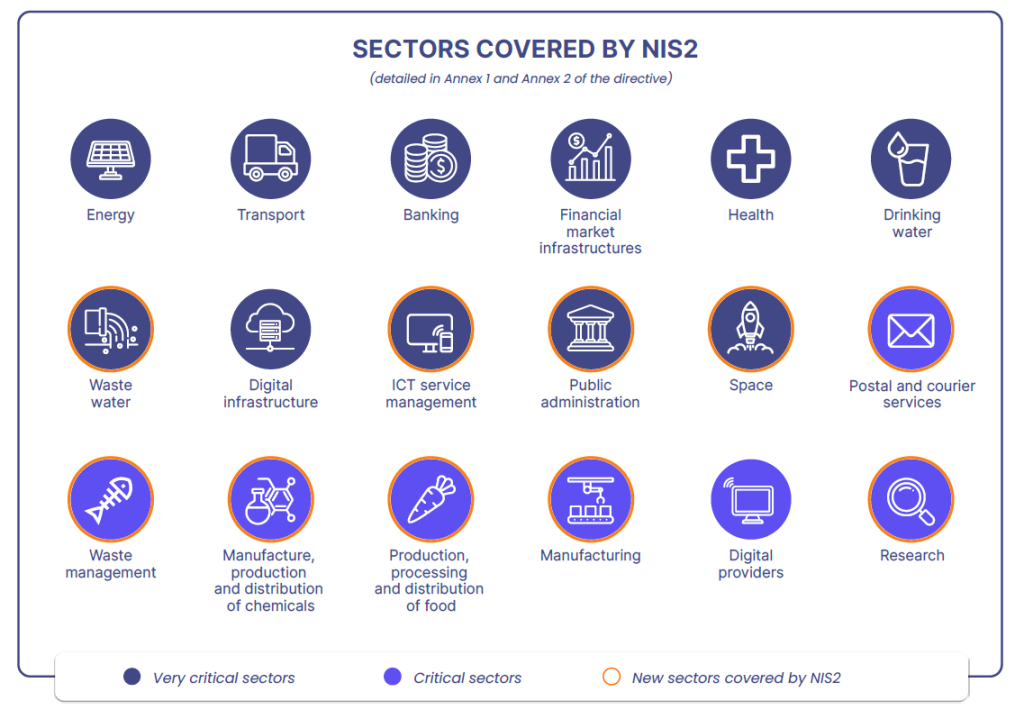
To ensure the continuity of services and the smooth functioning of the European economy, the NIS2 directive expands the list of critical sectors that must be protected from threats to networks and information systems. New sectors, such as wastewater treatment, the food industry, and public administration, are now included.

The NIS2 directive now classifies entities as “essential” or “important” in the above sectors, reflecting the degree of criticality of their services based on their sector, size, and revenue (see specific criteria in our NIS2 White Paper – link below).
The main differences between essential and important entities lie in the measures to be implemented and the enforcement of compliance obligations. For essential entities, oversight will be proactive (ex ante). This means that these organizations will be actively supervised to ensure compliance with the legislation. In the case of important entities, supervision happens ex post if warning signs of incidents arise. If, after an incident, it becomes clear that necessary measures were not taken, the organization may also face fines and/or other penalties.
It is important to note that senior executives are now ultimately responsible for managing cybersecurity risks in essential and important entities. As such, management bodies will need to approve risk management measures and oversee their implementation within the entity. Executives (individuals) can be held personally liable for violations of the NIS2 directive by the company and may be temporarily barred from performing their duties. They are also required to undergo cybersecurity training and provide it to their employees.
Key Takeaways
- Scaling Up: Over 300,000 organizations are expected to be covered by NIS2 in Europe – compared to a few thousands with NIS1.
- Supply Chain Targeted: In addition to managed security service providers (MSPs and MSSPs) explicitly included in the “critical” sectors, NIS2 also aims to secure the broader supply chain. Essential and important entities will be able to pass some obligations onto their providers.
- Accountable Executives: The executive may be held responsible in case of failure, facing warnings or penalties.
Risk management measures, incident notification within 24 hours… Focus on key provisions
Incident notification
NIS2 imposes obligations on essential and important entities for phased notification of incidents that have a “significant impact” on the provision of services. These notifications must be sent to the CSIRT or other competent authority.
The main evolution entails the introduction of a mandatory “early warning” within 24 hours of discovering the incident. This alert must be followed by a formal notification within 72 hours, then interim reports upon request from the CSIRT, and finally, a final report within one month.
Entities must inform the recipients of their services about significant incidents. When deemed in the public interest, the CSIRT or the competent authority may also inform the public about the significant incident or require the entity to do so.
Risk management measures
More broadly, NIS2 requires essential and important entities to establish an active cyber protection strategy that includes prevention, detection, monitoring, analysis, and mitigation. Thus, 10 major “risk management measures” are listed in Article 21 of the directive:
- Policies on risk analysis and information system security
- Incident handling
- Business continuity
- Supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers
- Security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure
- Policies and procedures to assess the effectiveness of cybersecurity risk-management measures
- Basic cyber hygiene practices and cybersecurity training
- Policies and procedures for the use of cryptography/encryption
- Human resources security, access control policies and asset management
- Use of multi-factor authentication (MFA) or continuous authentication solutions, secured voice, video and text communications
National transposition
These European measures will be translated into national frameworks and specified via regulations. In France for instance, this translates into “compliance objectives,” which will be further detailed in “acceptable means of compliance,” currently being developed by ANSSI. In Belgium also, the CCB relies on existing frameworks (CyberFundamentals and ISO/IEC) for implementation measures.
The directive specifies that these measures, further detailed at the national level, must be proportional to the risk, cost, impact, and severity of incidents. They must also consider the state of the art and, where relevant, pertinent European and international standards… among them, of course, the ISO standards!
NIS2 vs. ISO: What’s New?
It appears that the ISO27001:2022 standard and the establishment of an ISMS will cover a large part of the compliance requirements introduced by NIS2.
However, we can distinguish specific elements related to NIS2 to be implemented alongside the maintenance of an ISO standard.
Note: This list is not exhaustive and is subject to change.
On “Inventory of Information Systems”
- The entity must identify its Regulated Information Systems (referred to as “SIR,” thus subject to NIS2), as well as those that are out of scope.
On “Digital Governance” and “Incident Response”
- The entity must designate a primary contact person within the company with the CSIRT or competent authority for all matters related to cybersecurity.
- The entity must implement mechanisms to be aware of alerts from the CSIRT or competent authority.
- The now-famous incident notification deadlines must be factored into the incident response processes: mandatory “early warning” within 24 hours of discovering the incident to the competent authority, followed by a more comprehensive notification within 72 hours, interim reports upon CSIRT request, and a final report within one month.
On Securing Access to and Administering SIRs
- The entity must comply with the CSIRT’s or competent authority’s recommendations when choosing encryption and authentication mechanisms.
- Essential entities are subject to stringent resource segregation requirements dedicated to the administration of SIRs.
On “Mastering the Digital Ecosystem”
- The entity must ensure control over services outsourced as per the NIS2 directive.
On Supervision/Monitoring:
- More stringent requirements than those of the ISO27001 standard concerning logging and detection systems. For example, the retention period for security events for essential entities is expected to be around six months.
How Sekoia.io supports you in achieving NIS2 compliance
Are you classified as an essential or important entity? Sekoia.io enables you to enhance your protection by facilitating the detection and response to cyber threats. More specifically, our solutions Sekoia Intelligence (threat intelligence) and Sekoia Defend (SOC Platform) help address numerous NIS2 requirements, including (see details in the White Paper):
Risk Analysis: Gaining insight into attackers through cyber threat intelligence enables a better understanding of the risks your organization faces, both at strategic and operational levels.
Incident Management: Real-time monitoring of events, detection of security incidents, and automation of responses thanks to the SOC platform. New detection rules will be developed to facilitate the implementation of the directive within an organization.
Notification to Authorities: The reduced “Mean Time to Detect” (MTTD) of the SOC platform provides you with a clear performance indicator to meet the obligation of notifying significant incidents within 24 hours.
Information Sharing: The standardization of information on the Sekoia SOC platform facilitates the reporting of incidents and the sharing of information on cyber threats encouraged by the directive.
Business Continuity: Cyber threat Intelligence helps you develop relevant crisis management exercises, while the SOC platform provides a tool to conduct those exercises. For example, this is the platform used by NATO during cyber exercises such as Crossed Swords.
Sekoia.io and the Resilience of Your Supply Chain
Sekoia.io is already implementing best practices in terms of security assurances (MFA, penetration testing, etc.) and secure engineering of the platform.
Cloud Security: The solution can benefit from SecNumCloud-qualified hosting granted by ANSSI, widely recognized as one of the strictest standards across Europe.
Certifications: Sekoia.io is a SaaS solution certified under the PCI-DSS banking standard in certain cloud regions. Our certification program includes obtaining ISO27001 followed by SOC2.
Internal CERT: Sekoia.io also has its own CERT, which is a recognized member of InterCERT.
What’s Next?
The implementation date set by the directive is October 17, 2024. However, as of the writing of this article (September 2024), the directive is still being transposed in many member states.
Some countries have already clarified that sanctions will not apply immediately – there will for instance be a 3-year grace period in France – to allow entities to achieve compliance.
In this context, we are sharing our NIS2 White paper below, along with resources to assist you in implementing the directive within your organization.
Would you like to discuss further? Contact us here!
Click the button below to download our NIS2 White Paper!
Useful resources for NIS2 compliance
The European Directive:
- The text of the directive : https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=CELEX:32022L2555
- NIS2 Portal of the European Commission: https://digital-strategy.ec.europa.eu/en/policies/nis2-directive
- NIS2 FAQ of the European Commission: https://digital-strategy.ec.europa.eu/en/faqs/directive-measures-high-common-level-cybersecurity-across-union-nis2-directive-faqs
Transposition of NIS2 in EU member states:
- France – The “My NIS2 Space” portal from ANSSI: https://monespacenis2.cyber.gouv.fr/
- Germany – Act implementing the NIS Directive from BSI: https://www.bsi.bund.de/EN/Das-BSI/Auftrag/Gesetze-und-Verordungen/NIS-Richtlinie/nis-richtlinie_node.html
- Belgium – NIS2 Hub from CCB : https://ccb.belgium.be/en/nis2
- EU implementation tracking by Bird&Bird: https://www.twobirds.com/en/trending-topics/cybersecurity/nisd-tracker
Read also:
Chat with our team!
Would you like to know more about our solutions?
Do you want to discover our XDR and CTI products?
Do you have a cybersecurity project in your organization?
Make an appointment and meet us!
如有侵权请联系:admin#unsafe.sh