2024-9-26 19:46:27 Author: cyble.com(查看原文) 阅读量:15 收藏
Executive Summary
Water treatment facilities are critical components of public infrastructure, with over 148,000 public water systems operating in the United States alone. Underscoring their criticality, these facilities are increasingly facing cyberattacks due to the lack of robust cybersecurity measures compared to other industries. In one of the most recent and gruesome hacks in September 2024, hackers attacked the Arkansas City water treatment plant, forcing it to switch to manual operations.
Cyble Research & Intelligence Labs (CRIL) has been emphasizing the critical need to safeguard operational technology (OT) assets and the existing negligence in adhering to basic cybersecurity protocols such as changing the default credentials, ensuring systematic network segmentation of OT assets, and mitigating their exposures over the internet.
Emphasizing the urgency, CISA too recently released a joint fact sheet, highlighting ongoing cyber-attacks conducted by pro-Russia hacktivists specifically targeting operational technology (OT) devices across North America and Europe.
The joint fact sheet states – “authoring organizations are aware of pro-Russia hacktivists targeting and compromising small-scale OT systems in North American and European Water and Wastewater Systems (WWS), Dams, Energy, and Food and Agriculture Sectors. These hacktivists seek to compromise modular, internet-exposed industrial control systems (ICS) through their software components, such as human machine interfaces (HMIs), by exploiting virtual network computing (VNC) remote access software and default passwords”
Water Utilities in the Crosshairs of People’s Cyber Army
Since January this year, the pro-Russian hacktivist group People’s Cyber Army (PCA) has been observed to be targeting critical infrastructures such as Water Utilities across the US and Europe. Amongst their first attack, PCA targeted the water supply control systems in multiple Texan towns and a wastewater facility in a Polish village. According to the US media reports, this resulted in the spilling of tens of thousands of gallons of water onto streets and drainage systems, causing considerable public distress and potential environmental damage.
In March, they disseminated a video on their Telegram channel (later removed) claiming an attack on a French hydroelectric power station.
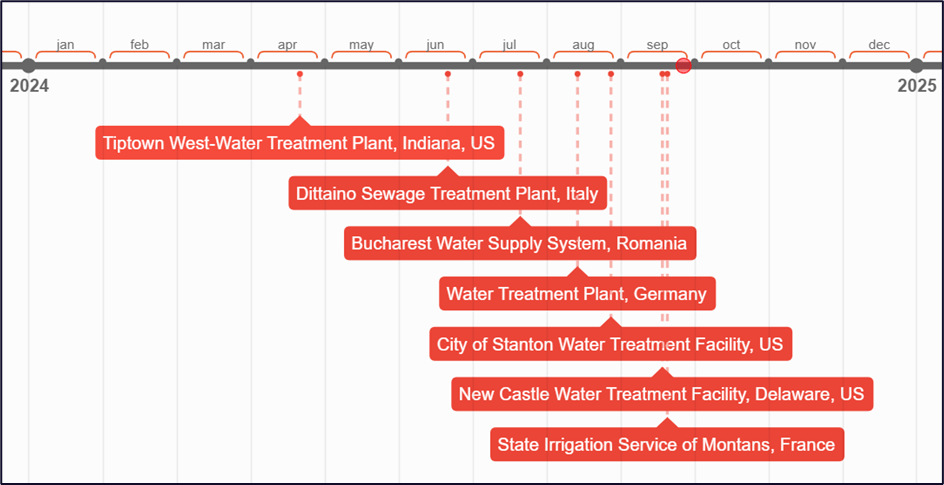
Cyble Research & Intelligence Labs (CRIL) observed that in the last six months, the People’s Cyber Army (PCA) has increased its attacks on Water Treatment facilities across the US and Europe.


Products and Protocols at Risk
Basis the investigation carried out by CRIL researchers, the majority of water treatment facilities in the US are at risk due to:
- Threat Actors Exploiting VNC protocols: Hacktivist groups are leveraging internet-facing and near-obsolete VNC to access HMI systems installed in the environments of organizations dealing with the Wastewater Treatment Sector.
- Internet-facing SCADAView CSX, a SCADA (Supervisory Control and Data Acquisition) software developed by Micro-Comm, Inc., is widely used in Water Utilities across the country. It provides a human-machine interface (HMI) for monitoring and controlling central telemetry units (CTUs). Link
To further highlight the gravity of the situation, the map and statistics below indicate the growing number of internet-exposed water utilities across the United States. Considering the growing attacks on Water utilities, as highlighted in the previous section, such thinly protected assets are susceptible to serious threats from hacktivist groups and state/non-state actors.


Impact
- Disruption of Operations: A cyberattack on the HMI could disrupt critical operations, leading to incorrect control of pumps, valves, and other equipment, potentially causing overflows, spillage, or contamination in the water treatment process.
- Public Health Risks: A compromised HMI could result in the improper treatment of wastewater, leading to the release of untreated or improperly treated water into the environment. This could pose significant public health risks by contaminating drinking water sources or ecosystems.
- Environmental Damage: An attack could cause systems to malfunction or shut down, releasing toxic chemicals or untreated sewage into nearby rivers, lakes, or the ground, causing long-term environmental damage.
- Financial Losses: Downtime and recovery efforts resulting from a cyberattack could lead to significant financial losses for the facility due to halted operations, repair costs, and potential regulatory fines.
- Safety Risks for Personnel: Malfunctioning HMI systems could create unsafe working conditions for operators and maintenance staff, potentially leading to accidents, injuries, or exposure to hazardous substances.
Hacktivism Chronicles
The People’s Cyber Army (PCA) first emerged shortly after the onset of the Russian-Ukrainian War in 2022 and maintains a substantial presence through its Telegram channel, which has 61,000 subscribers, and a network of private Telegram channels, where members set objectives, collaborate, and receive operational commands.
Early in its existence, PCA promoted Distributed Denial of Service (DDoS) attack tools, actively targeting Ukrainian infrastructure while encouraging followers to participate. They also provided training content, including a DDoS tool, through their Telegram channel to enable their subscribers to support them in their activism.
Gradually, PCA expanded its Telegram channel content to include narratives from Russian propaganda outlets, PMC Wagner, and pro-Russian war correspondents and bloggers.
By 2023, PCA expanded its operations beyond Ukraine and began targeting entities, especially Internet Service Providers (ISPs) in the EU and the US.
In 2024, the hacktivist group announced strategic alliances with other hacktivist groups with similar ideologies, such as NoName057(16), Federal Legion, CyberDragon, Phoenix, and 22C, to extend and collaborate in several hacktivist campaigns.
The People’s Cyber Army and Xacknet are likely to interact with or be controlled by the GRU – Russia’s military intelligence agency.
On July 19, 2024, the United States publicly revealed the identities of two members of the Russian-aligned hacktivist group People’s Cyber Army. It imposed sanctions on them for their involvement in cyber operations targeting critical U.S. infrastructure. Yuliya Vladimirovna Pankratova and Denis Olegovich Degtyarenko were identified as key figures within the group, with Pankratova serving as the group’s leader and Degtyarenko as a primary hacker. These sanctions highlight ongoing efforts to counter cyber threats from state-affiliated actors.
Conclusion
The increasing frequency and sophistication of hacktivist attacks on water utilities, particularly those attributed to groups like the People’s Cyber Army of Russia and other pro-Russian entities, underscores the need for promptly safeguarding such critical infrastructures. Recent incidents, such as the cyberattack on the Tipton West Wastewater Treatment Plant, reveal not only the technical capabilities of these groups but also their intent to disrupt essential services that millions rely on daily. The fact that these attacks have targeted municipal systems, often with limited resources for cybersecurity, raises alarms about the potential for more severe disruptions in the future.
Considering the increasing number of internet-exposed Water Utility assets across the United States, continuing use of outdated systems, and inadequate security protocols in such critical facilities, there is an urgent need to implement robust security measures. The Environmental Protection Agency (EPA) too has echoed these concerns, noting that a staggering 70% of inspected water utilities do not meet basic cybersecurity standards.
We see that Russian hacktivist groups leverage cyberattacks not only for operational disruption but also as a tool for propaganda. By publicly exposing vulnerabilities in a high-profile target like the United States Infrastructure, they seek to erode confidence in U.S. cybersecurity defenses. Notably, the People’s Cyber Army has escalated its targeting of critical infrastructure following sanctions on its leadership, signaling a clear intent to persist in these operations despite international pressure.
The potential consequences of inaction are dire, considering the world sits on the brink of kinetic and cyber war; these weaknesses in Water utilities not only pose threats of operational disruptions but also contamination of drinking water supplies, posing significant risks to public health.
Recommendations
- Harden HMI Remote Access: Secure remote access to HMIs using VPNs to encrypt data and require Multi-Factor Authentication (MFA) for user verification. Limit access through whitelisted IP addresses and geo-fencing and regularly audit logs to detect unauthorized activities.
- Strengthen Security Posture: Conduct regular vulnerability assessments and penetration testing to identify weaknesses. Use SIEM tools and Intrusion Detection Systems (IDS) for continuous monitoring and deploy endpoint protection on critical assets. Ensure timely software and firmware updates.
- Network Segmentation: Separate IT and OT networks using firewalls and DMZs to limit exposure. Use VLANs to isolate critical systems and apply strict access controls to minimize unnecessary communication between network segments.
- Asset Visibility: Use automated asset discovery tools to monitor all connected devices and maintain an updated inventory of hardware and software. Network traffic analysis helps detect anomalies, while passive scanning avoids disrupting operations.
- Eliminate Default Passwords & Use MFA: Replace default credentials with strong, unique passwords and enforce regular password changes. Implement MFA for all accounts, especially those with privileged access, and remove unused accounts to reduce the attack surface.
- Incident Response Plan: Prepare and refine an Incident Response Plan that defines roles and actions for cyber incidents. Include steps for containment, eradication, and recovery while ensuring clear communication protocols for internal stakeholders and external parties.
- Enhance Employee Training and Awareness: Conduct ongoing cybersecurity training programs for all employees, particularly those with access to OT systems. This includes educating staff on recognizing phishing attempts, proper use of authentication mechanisms, and the importance of following security protocols to prevent accidental security breaches.
References
https://www.cisa.gov/sites/default/files/2024-05/defending-ot-operations-against-ongoing-pro-russia-hacktivist-activity-508c.pdf
https://www.scadaview.com/Micro-Comm/
https://cyble.com/blog/water-and-wastewater-treatment-facilities-vulnerable-to-cyber-attacks/
Related
如有侵权请联系:admin#unsafe.sh