2024-9-27 01:16:24 Author: cyble.com(查看原文) 阅读量:40 收藏
Key takeaways
- Cyble Research and Intelligence Labs (CRIL) recently encountered an ongoing campaign associated with the Patchwork APT group, which is likely aimed at Chinese entities.
- This campaign continues the trend of the Patchwork APT group, which has previously targeted entities in China and Bhutan.
- The threat actors (TAs) have utilized a malicious LNK file, likely originating from a phishing email, as the initial infection vector. This file executes a PowerShell script that downloads two files: a seemingly innocuous PDF intended to lure the user and a malicious Dynamic Link Library (DLL).
- This campaign employs DLL sideloading techniques to execute the downloaded DLL using the legitimate system file “WerFaultSecure.exe,” thereby obfuscating malicious activity.
- The loaded DLL decrypts and executes shellcode that modifies the AMSIscanBuffer and ETWEventWrite APIs. This manipulation aims to evade detection mechanisms, allowing the malware to operate stealthily within the compromised system.
- The shellcode is subsequently used to decrypt and execute the final payload, stealing sensitive information from the victim’s machine.
Overview
Patchwork, also known as Dropping Elephant, is a highly active advanced persistent threat (APT) group that has been engaged in cyber espionage operations since 2009. Believed to be based in India, this group primarily targets high-profile organizations such as government, defense, and diplomatic entities across South and Southeast Asia.
Cyble Research and Intelligence Labs (CRIL) has been closely monitoring the activities of the Patchwork APT group since July 2024. On July 24, 2024, CRIL observed a campaign related to Patchwork APT. By pivoting through the pattern of files, CRIL observed several files associated with two major Patchwork APT campaigns: the first targeting Bhutan and the second targeting Chinese entities.

Campaign Targeting China
This campaign involves a malicious LNK file titled “COMAC_Technology_Innovation.pdf.lnk,” which references the Commercial Aircraft Corporation of China and specifically targets Chinese entities. This lure capitalizes on the 7th COMAC International Science and Technology Innovation Week, with TAs leveraging this event to focus on organizations in the aerospace, technology research, and government sectors, thereby increasing the success rate of their phishing campaign. Researchers from Aliyun have analyzed this campaign and published their findings in a blog post detailing the tactics used by Patchwork.
Campaign targeting Bhutan
Another notable campaign by this group observed in the same month targeted Bhutan with a file named ‘Large_Innovation_Project_for_Bhutan.pdf.lnk.’ This decoy document features a project proposal for Bhutan from the Adaptation Fund Board.
Ongoing Campaign
Among these, a newly identified LNK file, “186523-pdf.lnk”, appears to be linked to an ongoing campaign of the Patchwork group. This same sample was also shared by researcher Ginkgo and StrikeReady Labs on X (formerly Twitter).
When the malicious LNK file gets executed, this file downloads two components: a lure PDF and a malicious DLL containing encrypted shellcode. Additionally, it copies a system file from the victim’s machine, which is then leveraged to sideload the malicious DLL. This DLL then decrypts and executes the final payload directly in memory. The malware collects system information, such as the Process ID, public and private IP addresses, usernames, and more. Then, it transmits this data to the command and control (C&C) server, enabling further malicious activities, as shown in the image below.
This variant seems to be new compared to the payloads observed in previous campaigns. For tracking purposes, we are naming the malware “Nexe” Backdoor, as the string “Nexe” was found hardcoded in the binary used for C&C communication.

Notably, this campaign lacks specific targets, as the lure consists of plain, empty PDF. However, the names of the payload servers used in this campaign, such as shianchi[.]scapematic.info and jihang[.]scapematic.info suggests that Chinese entities are likely being targeted. Typically, the Patchwork group’s payload server names are associated with the country they are focusing on.
Technical Details
The LNK file, disguised as a PDF, contains a PowerShell script that carries out several malicious actions. The image below shows its contents.

The script first uses an “Invoke-WebRequest” command to download a file from the URL “hxxps://jihang[.]scapematic[.]info/eqhgrh/uybvjxosg” and saves it as a PDF in the “C:\ProgramData” directory. This PDF file appears to be the lure document, but in this case, it contains no content and is simply a plain, empty PDF.
Next, the script downloads another file from a different URL on the same domain, “hxxps://shianchi[.]scapematic[.]info/jhgfd/jkhxvcf,” saving it initially as “hal” in the “C:\ProgramData” directory. It then renames the file to “wer.dll” in the same location.
The script proceeds to copy the Windows system file “WerFaultSecure.exe” from “C:\Windows\System32” to “C:\ProgramData”, likely to facilitate DLL sideloading. The image below shows the downloaded files on the victim’s machine.

Finally, it creates a scheduled task named “EdgeUpdate” to run “WerFaultSecure.exe” at regular intervals, ensuring persistence on the compromised system. The image below shows the scheduled task created on the system.

DLL Sideloading
Threat actors leveraged the DLL sideloading technique to load the malicious DLL file using the legitimate WerFaultSecure.exe, as shown in the image below.

After the DLL is successfully loaded, it decrypts the encrypted shellcode within it and writes the decrypted content into the memory of the WerFaultSecure process, as shown in the image below.

Bypassing Security Mechanisms via Memory Patching
The injected shellcode is crafted to circumvent AMSI and Microsoft’s event tracking systems by patching specific bytes in the EtwEventWrite, AmsiScanString, and AmsiScanBuffer APIs, as shown in the images below.

Once the shellcode overwrites these APIs, it creates a section object from the previously decrypted content and maps it into the address space of WerFaultSecure. This allows the final VC++ compiled payload to execute without triggering any security alerts.
Final Payload
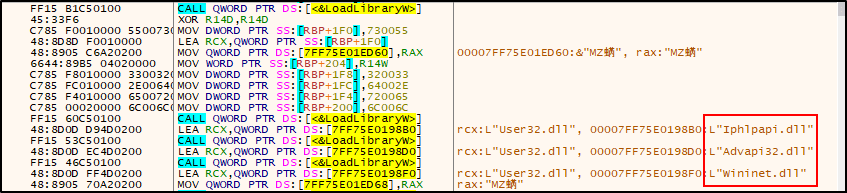
Once the payload is successfully loaded into memory, it utilizes the LoadLibraryW() API to load the necessary modules for execution, as shown in the image below.

After loading the necessary modules, the malware creates a mutex named “dsds” to ensure that only one instance of the malware runs on the victim’s system at a time, as shown in the figure below.

After creating the mutex, the malware retrieves a handle to the console window associated with the calling process. It then hides the console window and continues running in the background.

The malware then utilizes the GetAdaptersInfo() and GetHostName() functions to collect information about the network adapters and the device name on the compromised machine, as shown in the image below.

The malware queries https://myexternalip.com/raw using a specific user agent to obtain the victim’s public IP address, as demonstrated in the image below.

After gathering key system details, including the MAC address, username, and IP address, the malware computes the SHA256 hash for these values before further encryption, as shown in the image below.

After generating the hash, the malware encodes it into Base64 format. The resulting data then enters another encryption loop using the Salsa20 algorithm, which represents a change from the previous encryption method used in prior campaigns. This is followed by an additional round of Base64 encoding. The figure below shows the encryption code with key and nonce.

In addition to the previously mentioned details, including the MAC address, username, and IP address, the malware also retrieves and encrypts the following information using the same sequence: it first converts the data into Base64 format, then applies the Salsa20 encryption algorithm and finally encodes it again in Base64:
- Process ID
- Local IP address
- Windows version
- Username
- Hardcoded user-agent string
Each piece of encrypted system information is concatenated and separated by the “$” symbol. The image below displays the encrypted system information.

The encrypted data corresponds to the following fields:
- MAC address $ username $ public IP address $ private IP address $ Windows version $ username $ Process ID $ Nexe (hardcoded string) $ User-agent string
Using the final generated string, the malware initiates an HTTP request to a hardcoded domain, “iceandfire[.]xyz,” which is embedded in the code, as illustrated in the image below.

After constructing the HTTP request, the malware transmits encrypted data to its C&C server. However, since the C&C was not active during the analysis, we couldn’t fully assess its behavior. Despite this, following the POST request, the malware creates two threads capable of performing various tasks, as shown in the image below.

The thread extracts partial content from the initially generated string, which includes the encrypted MAC address, username, and public IP address of the victim’s machine, and attempts to send this data to the same domain.

The threads read the server’s response following the request and then compare the response with the following values:
- upload
- uplexe
- download
- filelist
- screenshot
This comparison helps the thread to determine the actions or commands that it should execute in the system.
Conclusion
The ongoing evolution and enhancement of the Patchwork APT group’s malware capabilities highlight their commitment to remaining at the forefront of espionage and cyber operations. The latest attack exemplifies their ability to evade security alerts and execute malicious files directly in memory, showcasing a sophisticated approach that underscores their adaptability and resourcefulness in the ever-changing landscape of cybersecurity threats. This adaptability not only enables them to bypass traditional defenses but also poses significant challenges for organizations seeking to protect themselves from such advanced tactics.
Recommendations
- The initial breach may occur via spam emails. Therefore, it’s advisable to deploy strong email filtering systems to identify and prevent the dissemination of harmful attachments.
- When handling email attachments or links, particularly those from unknown senders, exercising caution is crucial. Verify the sender’s identity, particularly if an email seems suspicious.
- Consider disabling or limiting the execution of scripting languages on user workstations and servers if they are not essential for legitimate purposes.
- Restrict the execution of WerFaultSecure.exe to its designated location to prevent unauthorized execution from other directories.
- Use a reputed anti-virus and internet security software package on your connected devices, including PC, laptop, and mobile.
- Monitor the beacon on the network level to block data exfiltration by malware or TAs.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
| Initial Access (TA0027) | Phishing (T1660) | Malware distribution via phishing site |
| Execution (TA0002) | User Execution (T1204) | Manual execution by the user |
| Defense Evasion (TA0005) | Masquerading (T1036.008) | LNK file disguised as a legitimate PDF file |
| Privilege Escalation (TA0004) | DLL Side-Loading (T1574.002) | Adversaries may execute their own malicious payloads by side-loading DLLs. |
| Privilege Escalation (TA0004) | Process Injection (T1055) | Injects malicious code into werfaultsecure.exe |
| Discovery (TA0007) | System Information Discovery (T1082) | Queries the system information |
| C&C (TA0011) | Application Layer Protocol (T1071) | Malware exe communicate to C&C server. |
| Exfiltration (TA0010) | Exfiltration Over C2 Channel (T1041) | Exfiltration Over C2 Channel |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| d7b278d20f47203da07c33f646844e74cb690ed802f2ba27a74e216368df7db9 | SHA256 | Malicious LNK file |
| ba262c587f1f5df7c2ab763434ef80785c5b51cac861774bf66d579368b56e31 | SHA256 | Malicious DLL file |
| fe503708d7969e65e9437b56b6559bc9b6bb7f46f3be5022db9406579592670d | SHA256 | Decoy PDF |
| f6d171e79e2fb38b3919011835c8117a1c56788bcf634e69ae67a5e255fb9d58 14bbe421abe496531f4c63b16881eee23fb2c92b2938335dca1668206882201a c3805b8b37eb1ba34057cd6c882dc9bedcebc01ec90a6d4be8d0f6fc82859ecb | SHA256 | Lnk used to target Bhutan |
| c6398b5ca98e0da75c7d1ec937507640037ce3f3c66e074c50a680395ecf5eae | SHA256 | Lnk targeting Chinese entities |
| hxxps://shianchi[.]scapematic[.]info/jhgfd/jkhxvcf hxxps://jihang[.]scapematic[.]info/eqhgrh/uybvjxosg | URL | remote server |
| Iceandfire[.]xyz | Domain | C&C Server |
Yara Rule
rule Nexe_Backdoor
{
meta:
author = “Cyble Research and Intelligence Labs”
description = “Detects Malicious Backdoor used in the latest Patchwork APTcampaign”
date = “2024-09-26”
os = “Windows”
reference_sample = “ba262c587f1f5df7c2ab763434ef80785c5b51cac861774bf66d579368b56e3”
strings:
$a = “WerSysprepCleanup”
$b = “WerpSetReportFlags”
$c = “WriteProcessMemory”
$d = “VirtualAllocEx”
$e = “Release\\AESC.pdb”
condition:
uint16(0) == 0x5A4D and all of them
}
References
Related
如有侵权请联系:admin#unsafe.sh