2024-9-27 17:17:5 Author: www.mobile-hacker.com(查看原文) 阅读量:12 收藏
![]()
WiFiPumpkin3 is a powerful framework designed for rogue access point attacks and network security testing. It allows security researchers, and red teamers to create fake Wi-Fi networks, custom captive portals, intercept traffic, and deploy phishing attacks. With its recent integration into the NetHunter arsenal, WiFiPumpkin3 can now be executed directly from an Android smartphone, making it more portable and accessible than ever before.
WifiPumpkin3 replaced MANA Toolkit that was already really difficult to make it work, and the code wasn’t maintained at all. Because of that, this is a very convenient update.
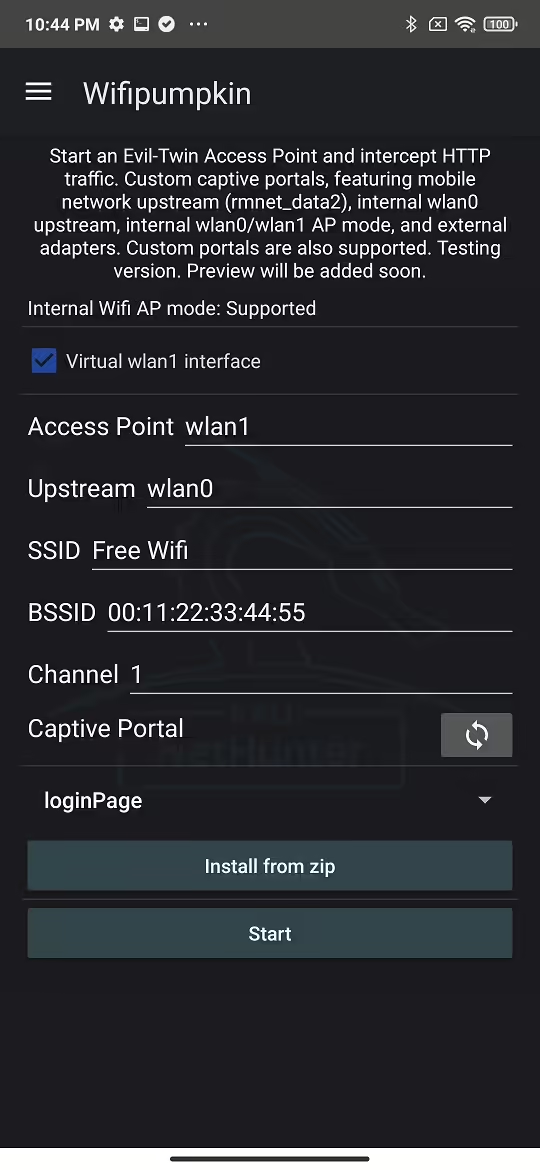
For WifiPumpkin3 to work, you need to have two Wi-Fi interfaces. The first one (e.g wlan1) for creating an access point and the seconds (e.g. wlan0) for upstream, that provides internet connection for devices connected to your access point (wlan1).
WifiPumpkin3 supports virtual interfaces, which means that if your smartphone Wi-Fi chipset (in my case Xiaomi Mi 9T) supports it as well, then you don’t even need external Wi-Fi adapter, which is a huge benefit.
On top of that, cybercriminals can misuse captive portals besides phishing to also distribute malware. By setting up a fake access point, they direct users to a malicious page mimicking a legitimate site like Google Play. Users are then tricked into downloading an APK file disguised as a trusted app, which can steal sensitive information or perform other harmful activities.
WiFiPumpkin3 offers a range of features that make it a versatile tool for network security testing:
- Rogue Access Point: Create an evil twin access point to mimic legitimate Wi-Fi networks and trick users into connecting.
- Traffic Interception: Capture, inspect, modify, and replay web traffic to analyze data flows and identify vulnerabilities. It can’t intercept encrypted HTTPS traffic.
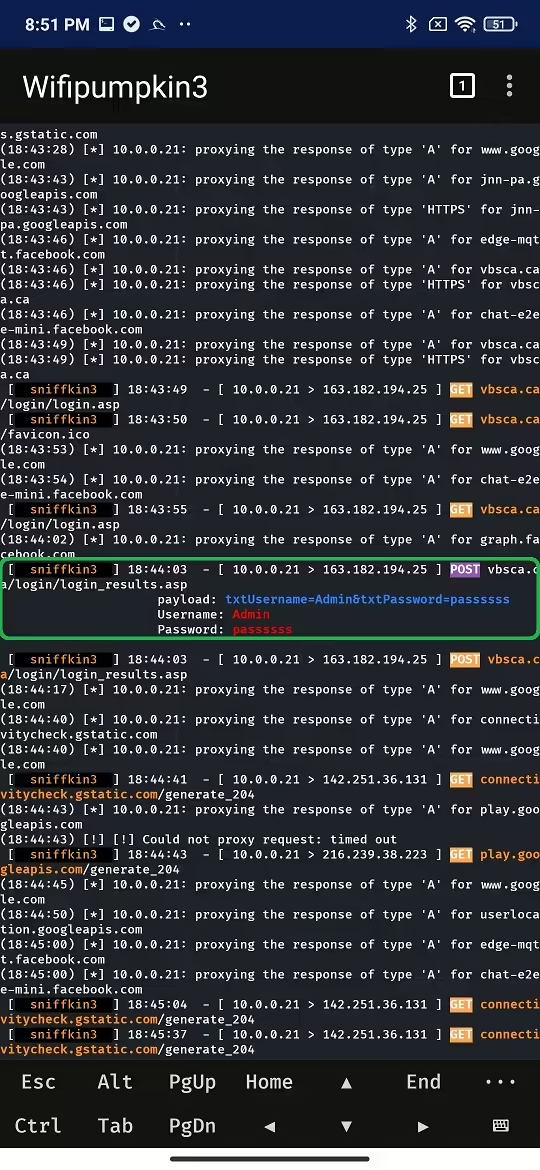
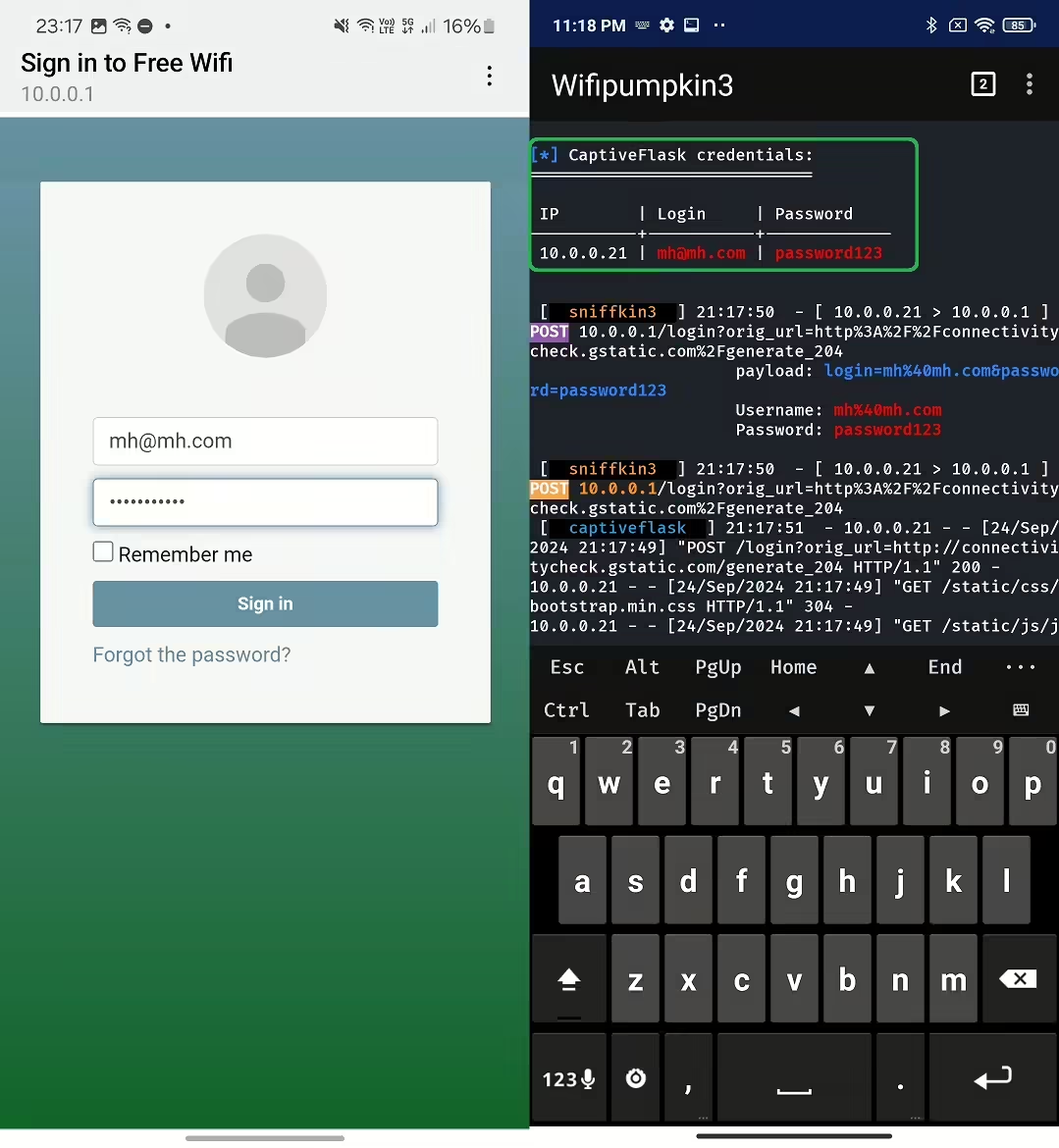
- Captive Portals: Set up web pages that users must interact with before accessing the internet, useful for phishing and credential harvesting.
- DNS Monitoring: Monitor DNS requests to detect and analyze suspicious activities.
- Deauthentication Attacks: Force devices to disconnect from their current network, prompting them to connect to the rogue access point.
- Phishing Attacks: Utilize features like Phishkin3 for MFA phishing and EvilQR3 for QR code phishing attacks.
The most prevalent case of misusing captive portals is phishing for credentials or to obtain Wi-Fi network password. However, cybercriminals can also distribute malware using a captive portal as well. By setting up a fake access point, attackers can setup malicious landing page that impersonates for example a legitimate Google Play website with option to download Wi-Fi manager app. When users connect to the fake network, they are prompted to download an APK file disguised as a trusted app. Once installed, this malware can steal sensitive information or perform other harmful activities.
While WiFiPumpkin3 is a valuable tool for security professionals, it’s essential to be aware of how to protect yourself from its capabilities:
- Verify Network Names: Always double-check the name of the Wi-Fi network before connecting, especially in public places. This helps to avoid connecting to evil twins of Wi-Fi networks.
- Use a VPN: Encrypt your internet traffic to prevent interception and analysis by attackers. This might prevent Attacker-In-The-Middle attack, however not the credentials lure or malware installation via captive portals.
- Look for HTTPS: Ensure websites use HTTPS to secure your data during transmission.
- Be Cautious with Captive Portals: Avoid entering sensitive information on suspicious login pages.
- Use reputable security solution: Anti-malware software can prevent device infiltration if a captive portal distributes malicious software.
The integration of WiFiPumpkin3 into NetHunter marks a significant advancement in mobile network security testing. By leveraging the power of WiFiPumpkin3 on an Android smartphone, security professionals can conduct comprehensive tests with greater ease and flexibility. However, it’s crucial to stay vigilant and implement preventive measures to protect against potential attacks. Stay informed, stay secure, and make the most of these powerful tools to enhance your network’s security.
如有侵权请联系:admin#unsafe.sh